Authenticate with workspace identity
A Fabric workspace identity is an automatically managed service principal that can be associated with a Fabric workspace. You can use the workspace identity as an authentication method when connecting Fabric items in the workspace to resources that support Microsoft Entra authentication. Workspace identity is a secure authentication method as there is no need to manage keys, secrets, and certificates. When you grant the workspace identity with permissions on target resources such as ADLS gen 2, Fabric can use the identity to obtain Microsoft Entra tokens to access the resource.
Trusted access to Storage accounts and authentication with workspace identity can be combined together. You can use workspace identity as the authentication method to access storage accounts that have public access restricted to selected virtual networks and IP addresses.
This article describes how to use the workspace identity to authenticate when connecting OneLake shortcuts and data pipelines to data sources. The target audience is data engineers and anyone interested in establishing a secure connection between Fabric items and data sources.
Step 1: Create the workspace identity
You must be a workspace admin to be able to create and manage a workspace identity.
Navigate to the workspace and open the workspace settings.
Select the Workspace identity tab.
Select the + Workspace identity button.
When the workspace identity has been created, the tab displays the workspace identity details and the list of authorized users.
Workspace identity can be created and deleted by workspace admins. The workspace identity has the workspace contributor role on the workspace. Admins, members, and contributors in the workspace can configure the identity as the authentication method in Azure Data Lake Storage (ADLS) Gen2 connections that are used in data pipelines and shortcuts.
For more detail, see Create and manage a workspace identity.
Step 2: Grant the identity permissions on the storage account
Sign in to the Azure portal and navigate to the storage account you want to access from OneLake.
Select the Access control (IAM) tab on the left sidebar and select Role assignments.
Select the Add button and select Add role assignment.
Select the role you want to assign to the identity, such as Storage Blob Data Reader or Storage Blob Data Contributor.
Note
The role must be provided at the Storage account level.
Select Assign access to User, group, or service principal.
Select + Select members, and search by name or app ID of the workspace identity. Select the identity associated with your workspace.
Select Review + assign and wait for the role assignment to be completed.
Step 3: Create the Fabric item
OneLake shortcut
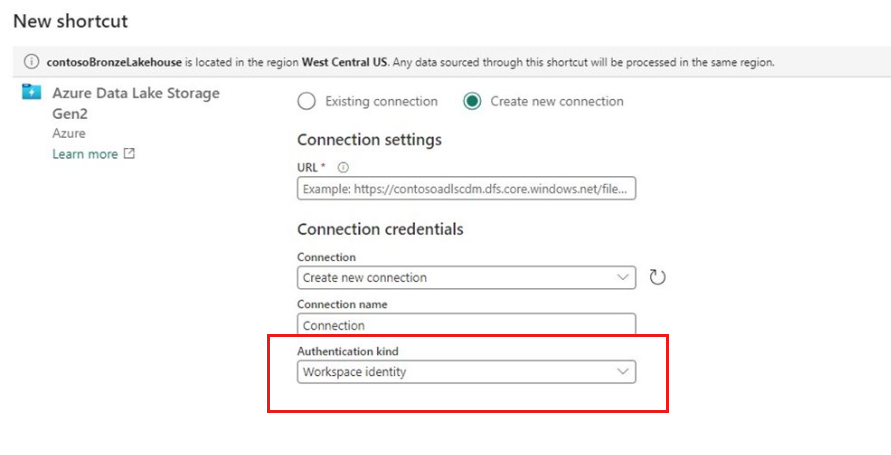
Follow the steps listed in Create an Azure Data Lake Storage Gen2 shortcut. Select workspace identity as the authentication method (supported only for ADLS Gen2).
Data pipelines with Copy, Lookup, and GetMetadata activities
Follow the steps listed in Module 1 - Create a pipeline with Data Factory to create the data pipeline. Select workspace identity as the authentication method (supported only for ADLS Gen2 and for Copy, Lookup, and GetMetadata activities).
Note
The user creating the shortcut with workspace identity must have an admin, member or contributor role in the workspace. Users accessing the shortcuts only need permissions on the lakehouse.
Considerations and limitations
Workspace identity can be created in workspaces associated with any capacity (except for My workspaces).
Workspace identity can be used for authentication in any capacity that supports OneLake shortcuts and data pipelines.
Trusted workspace access to firewall-enabled Storage accounts is supported in any F capacity.
You can create ADLS Gen 2 connections with workspace-identity-based authentication in the Manage Gateways and Connections experience.
Connections with workspace-identity-authentication can only be used in Onelake shortcuts and data pipelines.
Checking the status of a connection that has workspace identity as the authentication method isn't supported.