@Neil Andrews, Adding more information to the above response!
It looks like you're encountering an authorization error when trying to provision a file share using the file.csi.azure.com storage class in Kubernetes. The error message indicates that the client does not have the necessary permissions to perform the action ( Can you please cross verify the permission again and let us know the statsu) Microsoft.Storage/storageAccounts/fileServices/shares/read.
Before you begin( Please cross verify below mentioned prerequisite has been met)
- You need an Azure storage account.
- Make sure you have Azure CLI version 2.0.59 or later installed and configured. Run
az --version to find the version. If you need to install or upgrade, see Install Azure CLI.
- When choosing between standard and premium file shares, it's important you understand the provisioning model and requirements of the expected usage pattern you plan to run on Azure Files. For more information, see Choosing an Azure Files performance tier based on usage patterns.
Here are a few things you can try to resolve this issue:
Check Role Assignments: Ensure that the Kubernetes user has the correct role assignments. The role Microsoft.Storage/storageAccounts/fileServices/fileshares/read should be assigned instead of Microsoft.Storage/storageAccounts/fileServices/shares/read
Update Role Assignments: If the role name has changed, you may need to update the role assignments to reflect the new role name. This can be done through the Azure portal or using Azure CLI commands.
Use Azure Files CSI Driver: The Azure Files Container Storage Interface (CSI) driver is a CSI specification-compliant driver used by Azure Kubernetes Service (AKS) to manage the lifecycle of Azure file shares. Ensure that you are using the latest version of the Azure Files CSI driver
Persistent Volume Configuration: Make sure that your persistent volume (PV) configuration is correct. A PV can be used by one or many pods and can be dynamically or statically provisioned. If multiple pods need concurrent access to the same storage volume, you can use Azure Files to connect by using the Server Message Block (SMB) or NFS protocol
If you have recently granted access, it might take some time for the changes to propagate. You can try refreshing your credentials or re-authenticating to ensure that the new permissions are applied.
Option 2:
Check Scope: Ensure that the scope specified in the error message is correct. The scope should be set to the specific file share or storage account that you are trying to access. You can use the following command to assign the role at the correct scope:
$FileShareContributorRole = Get-AzRoleDefinition "Storage File Data SMB Share Reader"
$scope = "/subscriptions/<subscription-id>/resourceGroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>/fileServices/default/fileshares/<share-name>"
New-AzRoleAssignment -SignInName <user-principal-name> -RoleDefinitionName $FileShareContributorRole.Name -Scope $scope
Use Built-in Roles: Consider using built-in roles such as Storage File Data SMB Share Reader, Storage File Data SMB Share Contributor, or Storage File Data SMB Share Elevated Contributor which provide the necessary permissions for accessing Azure file shares over SMB.
If access was recently granted, it might take some time for the permissions to propagate. You can try refreshing the permissions by re-assigning the role or waiting for a few minutes and then trying again.
References
Use Container Storage Interface (CSI) driver for Azure Files on Azure Kubernetes Service (AKS) - Azure Kubernetes Service | Microsoft Learn
Assign share-level permissions for Azure file shares
Use Azure Files Container Storage Interface (CSI) driver in Azure Kubernetes Service (AKS)
Create and use a volume with Azure Files in Azure Kubernetes Service (AKS)
Update or rotate the credentials for an Azure Kubernetes Service (AKS) cluster
Link: https://github.com/kubernetes-sigs/azurefile-csi-driver/tree/master/deploy/example/nfs#prerequisite
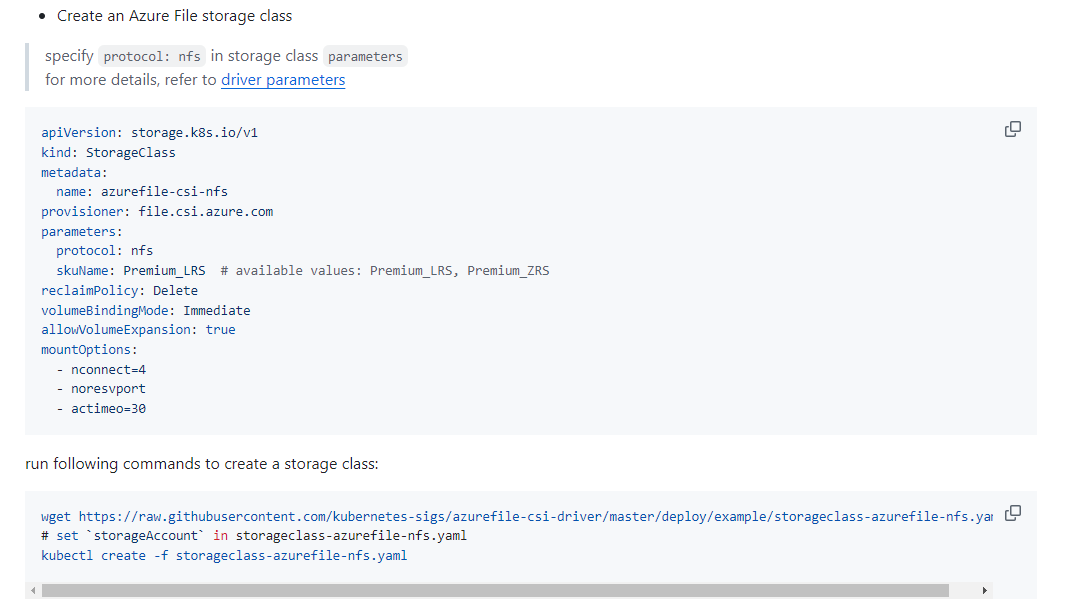
Please let us know if you have any further queries. I’m happy to assist you further.
Please do not forget to "Accept the answer” and “up-vote” wherever the information provided helps you this can be beneficial to other community members.
