Man-In-The-Middle-Attack: Protecting Http Traffic With SSL Might Be Not Enough - Consider Protecting SQL Traffic Too
Think configuring SSL for your web site is enough to protect against prying eyes?
Here is how the sensitive data can be exposed by sniffing your SQL traffic.
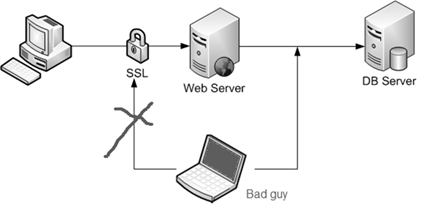
Consider common simple 3 tier web architecture for data driven web site. The Web and DB server (it really does not matter what vendor it is) are physical separate machines as depicted below:
It is common practice to apply SSL for web traffic so that bad guy won't be able to easily see what runs on the wire. It is less common practice to apply network protection to the traffic that goes between the Web and DB server. In some cases it is possible to pretty easily sniff that traffic, or as they call it to launch Man-In-The-Middle-Attack.
One of techniques to sniff the traffic is first launch ARP poisoning attack and then just fire up any network protocol analyzer. For ARP poisoning the tools can be found freely here - www.insecure.org - and I used Cain and Abel. Linux friends will probably use Ettercap (what a nice "how to" they have ) and I used new shiny and freely available Microsoft Network Monitor for protocol analyzing.
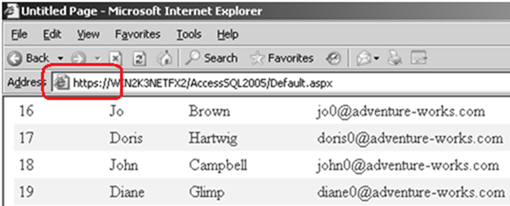
Here is how my web site looks (I just returned some sample data from AdventureWorks database over SSL):
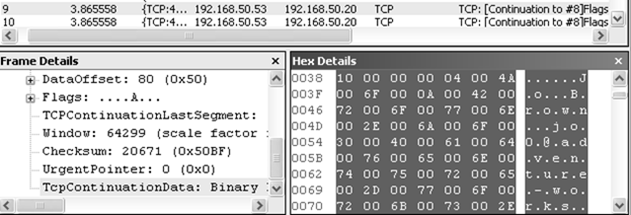
And here is what I fished in my net using MS Netmon while sniffing the traffic between the Web and DB server:
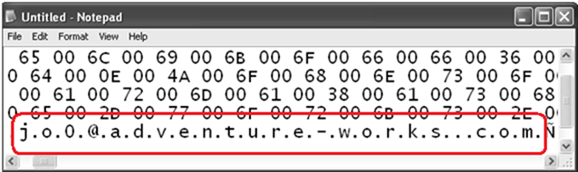
And here is how it looks after pasting it into my favorite tool - Notepad:
Go back to the first image and compare.
This is just email address, now think about a bit more sensitive data like your bank account balance or credentials. Is it secure on its way from the Web server to DB server?
Conclusion and Countermeasures
To build more secure system it is not enough to apply SSL or IPSEC here and there - it is about the holistic approach through the whole development process. Specifically for the case at hand consider the following resources when designing, building, and deploying your next system:
- WSSRA (Windows Server System Reference Architecture) blueprints for Web Application Services
- WSSRA Enterprise Design for Data Services
- How To: Use SSL to Secure Communication with SQL Server 2000
- How To: Use IPSec for Filtering Ports and Authentication
- How To: Use IPSec to Provide Secure Communication Between Two Servers
This post was inspired after watching presentation by Marcus Murray he has given during Microsoft Tech·Ed 2007 in Orlando - Why I Can Hack Your Network in a Day! [A live demonstration of techniques and tools used by hackers to compromise your network].
I am curious (or should I say I am freaked out) who else was inspired to do what after watching it?.....
It is scary presentation - do not watch it before you go to sleep. Especially if you are responsible for your org's IT in some way...
Comments
- Anonymous
August 01, 2007
My answer is "no" . I am working on solution where there is no Windows Active Directory Domain so we