TPM Owner Password
Hello everyone. It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team. Today we will focus on TPM Owner Password – quite misunderstood secret that is usually linked to the Bitlocker.
TPM (Trusted Platform Module) is a small chip on the motherboard (discrete TPM) or part of the CPU implementation (firmware TPM) where we can store secret information (private keys, virtual smartcards, Bitlocker keys etc.). TPM is also responsible for measuring integrity of the platform when used with Bitlocker, Measured Boot or Devide Health Attestation.
To use TPM you need to enable it in the BIOS/UEFI. During this process, special TPM Owner Password gets generated. This password can be later used to reset TPM Lockout state. TPM can go into the lockout state when too many incorrect authorization attempts are made to get access to these secrets. For example, when user enters too many incorrect PINs when prompted by Bitlocker pre-boot authentication or by virtual smartcard.
For older Operating Systems (Windows Vista/Windows 7) TPM had to be manually initialized from the tpm.msc (or from Bitlocker configuration wizard). During that process user had opportunity to save TPM Owner Password to a file.
For never operating systems (Windows 8.1/10) TPM is auto-provisioned – that means TPM is automatically activated after OS installation and in case of failure in repetitive attempts during the OS lifetime (triggered by scheduled task). Windows uses the randomly-generated Lockout Auth to provision the TPM, then destroys the Lockout Auth without ever revealing it to the user. However, depending on the GPO settings shown below, TPM Owner Password can be stored additionally in the registry. This GPO is located under:
Computer Configuration\Administrative Templates\System\Trusted Platform Module Services\
Configure the level of TPM owner authorization information available to the operating system
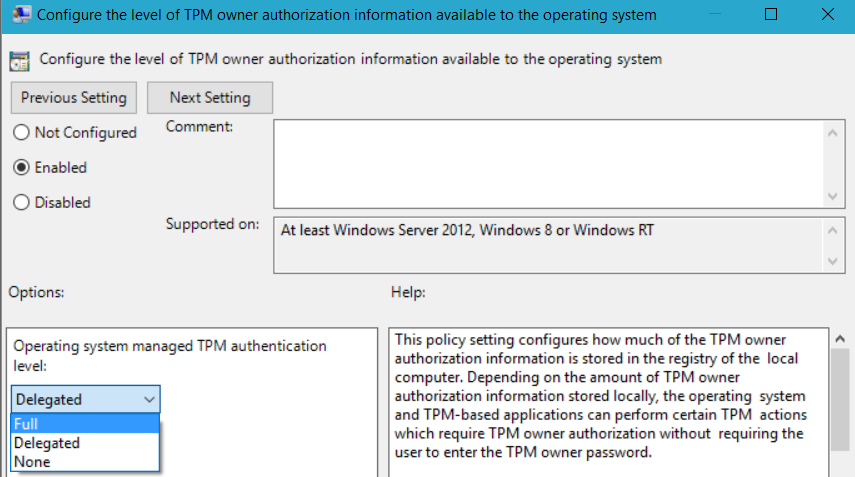
When GPO is configured to store Full authentication data, TPM Owner password will be stored as “OwnerAuthFull” in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TPM\WMI\Admin
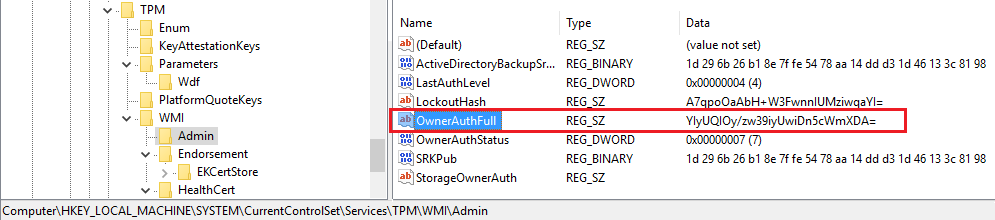
When GPO is configured with option “Delegated” or “None” – TPM Owner Password will not be stored additionally in the registry during (auto)provisioning.
Note: “LockoutHash” value has nothing to do with TPM Owner Password.
As said before, TPM Owner Password can be useful when TPM got locked out and in some scenarios, it is important to store it in central and secure location for your computers.
There are 2 ways of doing this:
1) MBAM Infrastructure – MBAM agent (Microsoft Bitlocker Administration and Monitoring) is capable of saving TPM Owner Password from the registry to the MBAM SQL Database. Of course this is for scenarios where we use Bitlocker on the machine and have MBAM infrastructure set up. This also assumes that:
a. TPM Owner Password is stored as “Full” in the registry
or
b. MBAM agent is responsible for initializing and taking ownership of the TPM
2) Active Directory – Windows Clients are capable of exporting TPM Owner Password to computer attributes in AD. This assumes that:
a. Client has connectivity to AD during export
b. GPO “Turn on TPM backup to Active Directory Domain Services” is enabled
Note: In most cases when you install MBAM agent TPM is already initialized automatically by the system. You can disable this behavior via PowerShell cmdlet Disable-TpmAutoProvisioning, clear TPM and let MBAM take ownership of it. When MBAM agent initializes TPM, it will escrow TPM Owner PWD to the SQL Database and delete it from registry, despite of “OwnerAuthFull” value in the registry.
TPM Owner Password in AD
When you initialize TPM from tpm.msc or via Bitlocker wizard in Control Panel, process called tpminit.exe will communicate with TPM and initialize it. During this time, random TPM Owner Password gets generates by leveraging TPM RNG (Random Number Generator).
Now if the GPO “Turn on TPM backup to Active Directory Domain Services” is enabled, your TPM Owner password will be escrowed to one of the attributes in Active Directory:
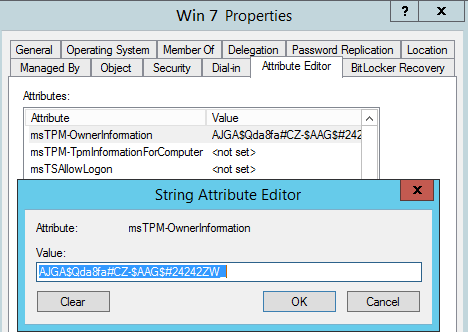
For Windows 7
TPM Owner password is stored in msTPM-OwnerInformation attribute of the Computer object.
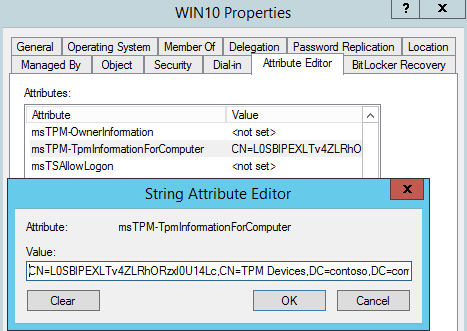
For Windows 8 and above:
TPM Owner Password is stored in the msTPM-OwnerInformation attribute of the TPM object. This object is stored in the TPM Devices container located in the root of your domain.
This attribute is back linked to the Computer object by using msTPM-OwnerInformationForComputer attribute.
For Windows 10 1607 and above:
TPM Owner Password is not stored in the AD at all. Even though you can configure GPO on previous operating system (Windows 8/Windows Server 2012 R2) “Turn on TPM backup to Active Directory Domain Services” or registry keys directly on the client machine:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\TPM\ActiveDirectoryBackup = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\TPM RequireActiveDirectoryBackup = 1
Windows 10 1607 will ignore these values.
Another thing which is worth to mention that GPO
Computer Configuration\Administrative Templates\System\Trusted Platform Module Services\Turn on TPM backup to Active Directory Domain Services
has been removed from ADMX templates in Windows 10 1607 and Windows Server 2016. Thus most of information provided in this article is for pre Windows 10 1607 editions.
TPM object and permissions
TPM Objects is unique for every machine and doesn’t change when you reinstall Operating system. This means when you rebuild/reinstall your machine you might encounter some issues while activating TPM.
For example, very common error is 0x80070005 E_ACCESSDENIED
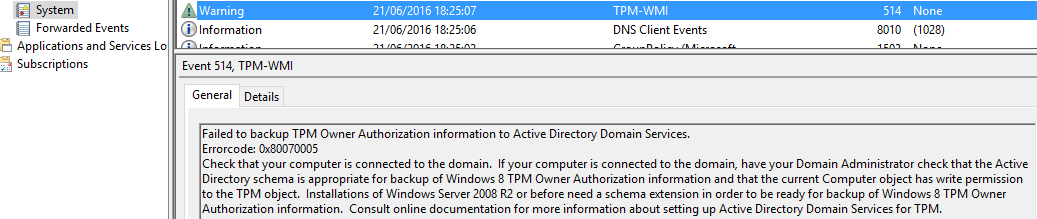
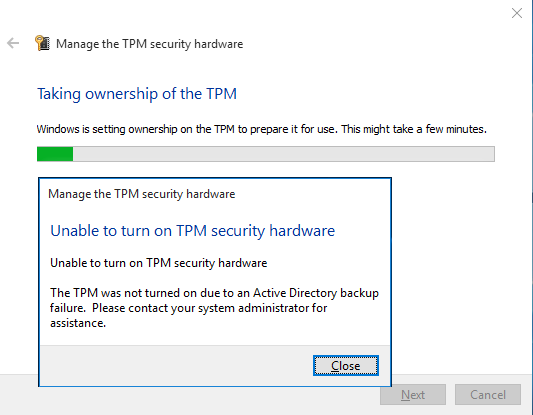
This error occurs because by default new Operating System (after reinstallation) cannot write TPM Owner Password to the old TPM object. Let’s have a look at the default permissions on msTPM-InformationObject:
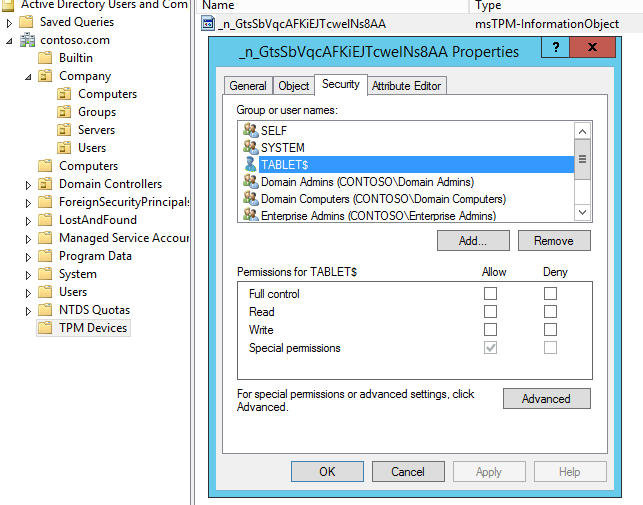
- "Write all properties" for an SID: S-1-3-0 Creator Owner (original computer)
- "Read all properties" for "Domain Computers" (but no write)
We can check this by going to the TPM object in “TPM Devices” container, select original computer (in our case TABLET) and check Special Permissions.
In order to fix this issue, you need to extend the schema by using LDF file published on the TechNet : “TPMSchemaExtensionACLChanges.ldf” which will change default TPM Object’s ACLs. Unfortunately, only new TPM Objects will be affected as we modify the AD schema but not the existing objects.
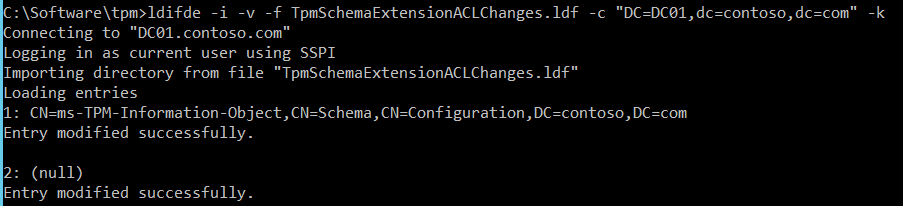
If you want to change ACLs of existing TPM objects you can just add "Write all properties" and "Read all properties" for "Domain Computers" to the specific or all msTPM-InformationObjects.
Using TPM Owner Password
If you want to change TPM Owner Password, you need to retrieve current password from the MBAM database or Active Directory and copy it to the XML file between <ownerAuth> and </ownerAuth> . In example below, my TPM owner password is 7O66EMj9LFFRhwfFsw+gVAIVkR8=
<?xml version="1.0" encoding="UTF-8"?>
<!--
This page is a backup of TPM (Trusted Platform Module) owner authorization information. Upon request, use the authorization information to prove ownership of the computer's TPM. Please keep this file in a secure location away from your computer's local hard drive.
-->
<tpmOwnerData version="1.0" softwareAuthor="Microsoft Windows [Version 6.0.5461]" creationDate="2016-07-09T17:41:00-00:00" creationUser="contoso\user1" machineName="Laptop">
<tpmInfo manufacturerId="112233445566"/>
<ownerAuth> 7O66EMj9LFFRhwfFsw+gVAIVkR8= </ownerAuth>
</tpmOwnerData>
You don’t need to fill out all other details like computer or user name. TPM.msc will only validate password. So, it is fine if you use shorter syntax:
<?xml version="1.0" encoding="UTF-8"?>
<ownerAuth> 7O66EMj9LFFRhwfFsw+gVAIVkR8= </ownerAuth>
Save the file with .tpm extension and then go to the TPM.msc, select “Change Owner Password..”
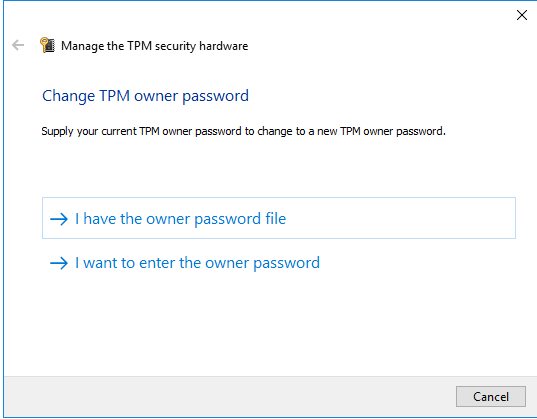
and then “I have the owner password file”.
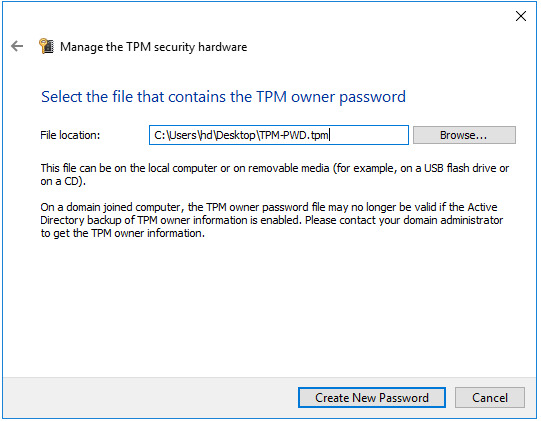
Once TPM.msc validates current password you will be able to generate new one.
Few tips:
If you change TPM Owner password manually from tpm.msc this change will be reflected in AD if export is configured via GPO.
If you apply GPO “Turn on TPM backup to Active Directory Domain Services” after TPM has been initialized, Owner Password will not be exported automatically. You will have to use scripts or manually change the password.
Changing or entering TPM Owner Password have a tolerance of 1 failure. After that, option of using password will be locked for 24 hours. This is not the same as “TPM Lockout” which is part of TPM anti-hammering capability.
Remember: starting from Windows 10 1607 we dropped export of TPM Owner password to AD. This (change) is because TPM Owner Password could be retrieved from the registry in some scenarios and be used in offline attacks against TPM anti-hammering. Additionally, most lockouts of TPM come from Bitlocker thus you don’t even have access to tpm.msc to unlock your TPM. When TPM is completely locked by Bitlocker, you are stuck in preboot phase of Windows. So the workflow was not very convenient for both users and helpdesk people.
As always I hope this was informative.
Rafal
Comments
- Anonymous
February 28, 2017
Really nice article, thank you very much. - Anonymous
March 02, 2017
The comment has been removed - Anonymous
March 06, 2017
Thanks for the article. As C. Schildhorn said in 1.: How is it possible to reset a TPM lockout after e.g. multiple wrong PIN entries by a user? At the moment we have a notebook with a locked out TPM-Chip and we are not able to reset the lockout. - Anonymous
March 06, 2017
@soc234,: Look at my article about TPM Lockout. I explained there how the lockout gets reset in time. - Anonymous
March 06, 2017
@ C. Schildhorn 1) Look at my article about TPM Lockout. TPM gets unlocked in time. 2) you don't have to take ownership. Malicious attempt might look like this: guessing PIN or other authorization data> anti-hammering lockout kicks in > unlock the TPM > repeat 3) you don't have to revert back to 2 but you can - Anonymous
March 07, 2017
@Rafal Sosnowski Sorry I can't find a description in the above article how the TPM lockout is done in 1607. To my knowledge with TPM 2.0 the Lockout reset will be done by the TPM itself after some time, but how we will reset a lockout on a 1607 client that has only TPM 1.2? With TPM 1.2 clients before 1607 changes I was e.g. able to save the TPM owner password to MBAM and enabling the MBAM client to automatically reset the TPM lockout. This setup is no longer supported with the 1607 changes? - Anonymous
March 07, 2017
Or is 1607 able to reset the TPM lockout for 1.2 and 2.0 without the TPM owner password when the TPM authentication level is configured with "delegated"? - Anonymous
March 07, 2017
Windows doesn't do any automatic reset using the owner password. TPM lockout counter expires (in both TPM 1.2 and 2.0) and got reset after some time but this is independent from Owner Password. - Anonymous
March 14, 2017
Amazing article!!!! This really helped me a lot. I have a question which maybe unrelated but just wanted to try my luck here....MBAM 2.5 does not escrow the ownerauth from pre-initialized windows 7 machines as taking the ownership of TPM is required for the same. However this is possible on client machines post windows 8 operating systems. The ownerauth data can be copied over from an AD backup to the MBAM server however this can be done for one machine at a time. Is there any way to carry out this process for multiple machines???? - Anonymous
April 12, 2017
Hi Rafal, my small customer had a couple questions based on this feature being removed from Win 10 and Win Srvr 2016. Is escrowing the keys to MBAM's SQL instance the only way to centralize the backup of the TPM owner password, or is there some other AD feature or Azure AD feature to do so? - Anonymous
April 13, 2017
@ Craig: If machine is AAD joined you can escrow Bitlocker Recovery Password to Azure but not the TPM Owner Password. If its domain joined MBAM is the only choice you have assuming you follow the steps from the article. Cheers - Anonymous
May 09, 2017
Dear Rafa,Hope you re doing well, I appreciate your effort I have a quick query with you I am implementing bitlocker on 200 computers I just want to know to know how to automatic enable TPM remotely on 200 computer if I go one by one it will take several day to enable TPM could you please guide me the best way to do this without MBAM. like any other way GPO or Script please help me out in this regard thank you.Regards,Adeel - Anonymous
May 11, 2017
So with Win 1607 is it possible to backup the TPM owner password to MBAM? All my reading makes it sound like 1607 no longer saves this password. Is the only recovery option to Clear the TPM? - Anonymous
October 04, 2017
Interesting article. Can you give a brief explanation of the conceptual difference between the owner secret, as used by TPM 1.2 and the owner password, as used by TPM 2.0? - Anonymous
October 08, 2017
@Alex please refer to the TPM 2.0 specification: https://trustedcomputinggroup.org/tpm-main-specification/ - Anonymous
October 26, 2017
¡Muy practico! Razonables motivos. Manten este nivel es un post genial. Tengo que leer màs articulos como este.Saludos - Anonymous
December 20, 2017
Hi Rafal, a kind extra remark to your conclusion in the Remember section at the bottom: it is still useful to backup TPM ownership password to AD, or some other storage, when you want to transition between different firmware versions (1.2 / 2.0) w/o prompting the user to press a key at BIOS post messages. To obtain the info from running Windows OS requires some process with elevated privileges to first access and save the information elsewhere before an offline attack can take place. IMHO, that requires really specific targeted users to first load the malicious code, and then gain access to the physical system for offline attack... How real is that scenario? - Anonymous
November 26, 2018
Hi i need to know how to reset TPM pin lockout on Windows 10 1703 and above using MBAM as i can not find any useful info on documentation , i face error when i try to reset "TPM Owner Password file is not found"appreciate your reply