UAG DirectAccess Test Lab Guide CRL Check Update
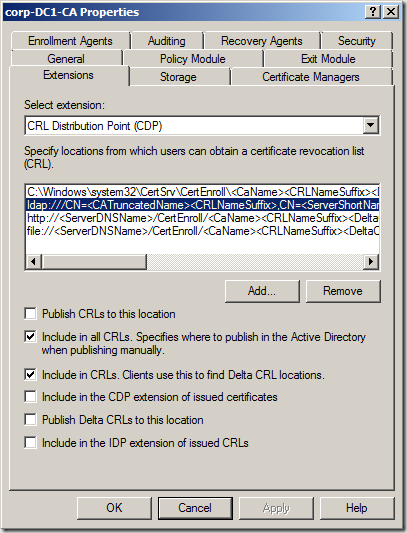
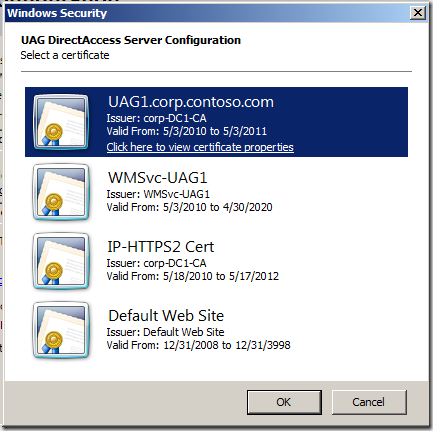
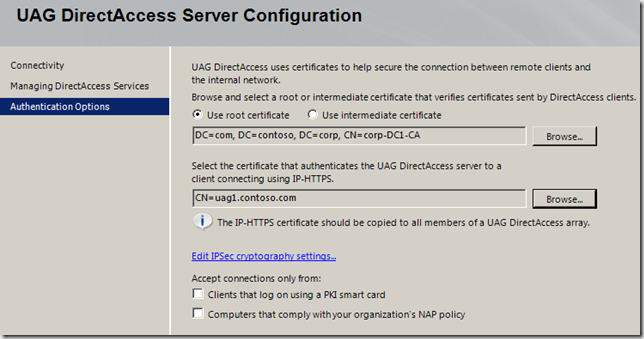
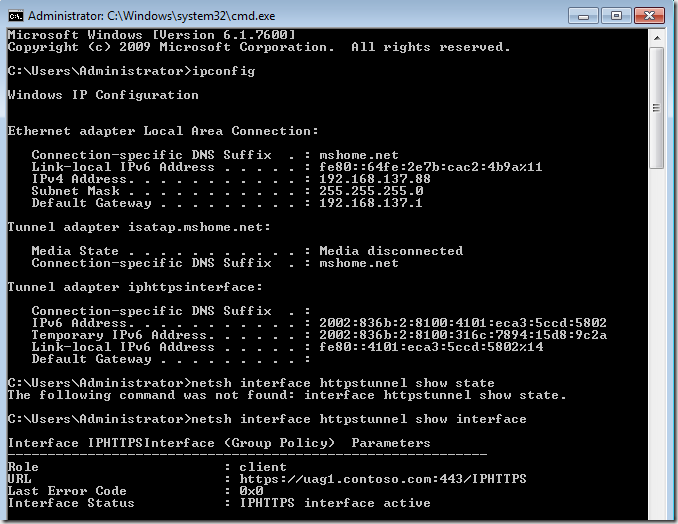
However, back to the “small” problem. Part of the Test Lab Guide walks you through how to install and configure the Microsoft Certificate Server so that Certificate Revocation Checks won’t fail when the DirectAccess client tries to connect to the IP-HTTPS listener on the UAG DirectAccess server. As I point out in the Test Lab Guide, this isn’t something that you would do in a production environment. If you use a commercial certificate for the IP-HTTPS listener, the certificate provider will make sure the CRL is reachable and highly available. If you create your own certificate for the IP-HTTPS listener, then you’ll have to publish your CRL and make sure it’s highly available – a lot of work for some people, not so much for others. The point is, you can do it either way. If you go to https://technet.microsoft.com/en-us/library/ee861152.aspx#BKMK_O you’ll find that you’re in Section O – Remove CRL Distribution Settings on the Certificate Authority on DC1. In step 3, you’ll read the following: “3. Click the Extensions tab. In Specify locations for which users can obtain a certificate revocation list, check all locations of the CRL Distribution Point (CDP) Authority Information Access (AIA) , and verify that Publish CRLs to this location or Publish Delta CRLs to this location is not selected.” The problem with these instructions is that they are incomplete and won’t prevent CRL check failure when the DirectAccess client is later configured to connect to the UAG DirectAccess server using its IP-HTTPS adapter. You’ll know that you’re running into this problem when you run the command netsh interface httpstunnel show interface you’ll see a Last Error Code of 0x80092013. You might also see an error code of 0x274c on the way to the the interface finally failing. The 0x80092013 code indicates that the CRL check failed. In the figure below you can see the Properties dialog box for the Certificate Authority we use in the Test Lab Guide. The problem you’re encounter with the Test Lab Guide is related to the ldap:// URI. When you select that option from the Specify location from which users can obtain a certificate revocation list (CRL) , you have to make sure that you deselect (uncheck) the option Include in the CDP extension of issued certificates. That step is not called out in the Test Lab Guide. I will add that as soon as I can, but until then, make sure you uncheck that option. What if you already configured the Test Lab and everything worked except for the IP-HTTPS connection? What you can do is request a new certificate for the IP-HTTPS listener and run the UAG DirectAccess Wizard again so that the new certificate is bound to the IP-HTTPS listener. Here are the general steps
When you see it work, your output will look something like the figure below Author: Tom Shinder Technical Writer ISD iX – UAG DirectAccess – Anywhere Access Team tomsh@microsoft.com Contributor: Jim Harrison Program Manager |
Comments
- Anonymous
February 24, 2014
Here are the top Microsoft Support solutions for the most common issues experienced when using Forefront