Storage card wipe and encryption - What's the deal?
In Windows Mobile 6 we added the ability to encrypt the storage card of a Windows Mobile device as well as wipe it remotely.
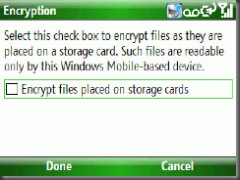
The encryption can either be enabled by the user or enforced through an Exchange 2007 policy.
The encryption of the storage card uses AES 128.
So let me explain more...
Storage Card Encryption
Firstly the encryption does tie the Storage card to the device. The encryption is tied to a unique ID created upon Hard Reset of the device. You cannot move the encrypted card to another device without first decrypting the card.
When the card is encrypted a key is placed on the device itself and the data on the card is encrypted.
This is important as many existing solutions (particularly on other platforms) store the key and data in the same place... so if you have the device you have everything you need to decrypt the data (all you need is time :) )
Storage Card Remote Wipe
Now if you do initiate a remote wipe what happens is that the card is erased and the key removed from the device.
This gets over two major concerns/hurdles.
1) What if someone pulls the storage card quickly from the device stopping it being erased. Well it doesn't matter as the key is removed.
2) What happens if the storage card has the HW write lock disable enabled.. well again the key from the device is removed so the data is useless.
How many times do you overwrite the data on the Storage card?
One question I sometimes get from security teams is how many times we overwrite the data. This is mainly a confusion from PC Hard Drive encryption. There is no need for multiple writes of data on flash drives. The need for multiple writes on hard disks is due to the fact that traditional hard disk heads can skip, and thus jump over sectors, and not wipe them...so multiple overwrites can ensure each sector is hit.
Why don't you encrypt the device?
The #1 followup question I always get is why we don't encrypt the data on the device itself...
Well once the mobile device is accessed via the device-lock or power-on password, all the data on the device is accessible to the user whether it is encrypted at rest or not.
The weakest link is the SD card external memory which, if not encrypted, can be accessed by any device or computer that can read SD cards.
By encrypting the SD card, the weak link is made strong and the data on that card can only be accessed by the paired device after the device-lock PIN or password has been correctly entered.
Comments
Anonymous
March 16, 2007
I'm glad they added this in the new version of WM and Exchange 2007. I remember when MS released the video of that guy in that Taxi and he left phone in the Taxi. They called the system admin to have him remotely wipe the device so everything was safe. I was always thinking that it didn't make much sense because the chances are a large power point would have been stored on the memory card defeating the purpose of the remote wipe :)Anonymous
March 16, 2007
How will recovery work? Is there something like a EFS recovery agent to access an SD card if it is removed from the device and the key on the device is lost? Or a way to prevent the SD card from being wiped and staying encrypted until setup by the user again? In the last week I've had two users wipe their phones after they forgot their PIN 8 times. Associating it with ActiveSync and getting their data back isn't a big deal but if they lost 2 GB worth of an SD card that they wanted secure, I would have more trouble since there isn't a good way to backup an SD card.Anonymous
March 16, 2007
Eagle117 - Unfortunately there isn't a recovery mechanism that I'm aware of.Anonymous
March 16, 2007
The comment has been removedAnonymous
March 17, 2007
The comment has been removedAnonymous
March 17, 2007
The comment has been removedAnonymous
March 17, 2007
In Windows Mobile 6 Microsoft added the ability to encrypt the storage card of a Windows Mobile deviceAnonymous
March 18, 2007
"The encryption is tied to a unique ID created upon Hard Reset of the device." Does this mean a new unique ID is created for every hard reset? Would this mean, if you had a card encrypted before a hard reset, that since a new unique ID was created, the same card could not be read due to the hard reset and creation of a new unique ID? Do you know of any white papers that deal with the storage encryption? -JasperMAnonymous
March 18, 2007
Software / Hardware Loke has a very handy WM5/WM6 feature guide CoolSmartPhone.com is reporting thatAnonymous
March 19, 2007
QUOTE:"This is important as many existing solutions (particularly on other platforms) store the key and data in the same place... so if you have the device you have everything you need to decrypt the data (all you need is time :) )" ... applying that same principal to the way WM stores Exchange credentials on the device for direct push ... doesn't that also suggest that it is only a matter of time before someone can decrypt a user's exchange password on the device? -- I wouldn't want to rely on the device never needing to be hard reset / replaced. In addition to the scenarios given above, I've had several devices lock during the boot phase and the only way out is a hard reset. In this scenario that would be 'goodbye data'.Anonymous
March 19, 2007
Andy - the Exchange password is stored hashed double encrypted on the device using 128-bit RC4 encryption so I think it'd take a VERY long time for someone to decrypt.... if ever....Anonymous
March 19, 2007
The comment has been removedAnonymous
March 19, 2007
@JasperM: A new key is generated after a cold boot, so if you hard reset the device, the files are unreadable. (it has to be like that, we don't want it to be that easy to get into the encrypted storage card of a stolen device+card) @Eagle: One method to migitate the pin recovery risk is to use the OWA password reset feature that's in WM6. Users can log into their OWA account and get a recovery code which is used to reset the password on the device. This will preserve the encrypted files.Anonymous
March 19, 2007
JasperM - love it :) I had been using those numbers in some MEDC presentations last year.... I think most people's device contents will have little value in 149 trillion years ;)Anonymous
March 20, 2007
The comment has been removedAnonymous
March 26, 2007
My colleague Jason Langridge wrote a post about the storage card encryption feature in WM6. This is oneAnonymous
March 26, 2007
My colleague Jason Langridge wrote a post about the storage card encryption feature in WM6. This is oneAnonymous
March 26, 2007
My colleague Jason Langridge wrote a post about the storage card encryption feature in WM6. This is oneAnonymous
March 26, 2007
My colleague Jason Langridge wrote a post about the storage card encryption feature in WM6. This is oneAnonymous
January 30, 2009
A lot of discussions within IT organizations are about security, and how the approved security policiesAnonymous
January 30, 2009
A lot of discussions within IT organizations are about security, and how the approved security policies