Setting up Windows Application Proxy for Exchange 2013
Hello again!
I wanted to try out some of the new Windows Server 2012 R2 functionality that is meant to replace TMG/ISA/UAG. Thanks to Georg Hinterhofer for helping me troubleshooting and getting my lab working!
This post assumes you know how to do basic setup, like DNS, installing Exchange 2013, etc.
You can setup the other protocols/vdirs – but only OWA & ECP support pre-authentication. The others must be set as pass-through. I may try to add those to the lab later, but today we only are doing OWA.
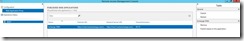
LAB Setup
Server Name |
IP |
Role |
OS |
ADFS1 |
192.168.1.115 |
ADFS Server |
W2k12 R2 |
WAP1 |
192.168.1.114 |
WAP Server, ADFS Proxy |
W2k12 R2 |
DC1 |
192.168.1.5 |
DC, DNS |
W2k8 R2 |
MSX1 |
192.168.1.10 |
Exchange 2013 CAS & MBX (CU3) |
W2k12 |
ADFS |
192.168.1.114 |
A DNS a-record pointing to the WAP server (ADFS proxy) |
- |
192.168.1.114 |
A DNS a-record pointing to the WAP server for mailbox access |
- |
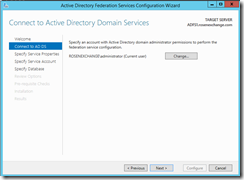
I use the administrator account to setup everything.
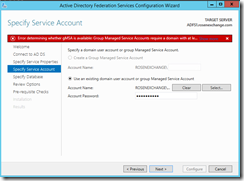
I created one domain account for ADFS – called ADFSSvc. This account was not mailbox enabled.
Setting up ADFS
Goal: Install and configure ADFS server.
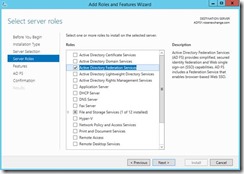
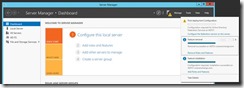
On ADFS1, from server manager add the ADFS server role.
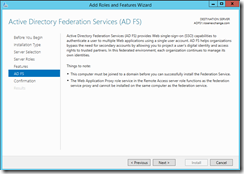
Note the requirements. I *think* you can install this on your DC to save a server, but at the time of this writing Exchange 2013 CU3 does not support a Windows 2012 R2 domain controller. This is why I used a separate ADFS server in my lab.
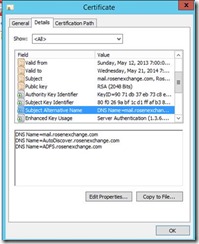
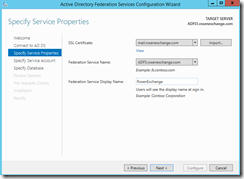
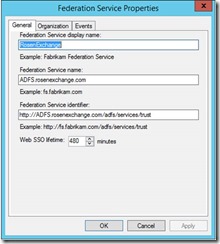
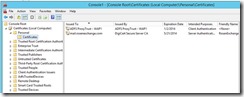
While that installs, import the certificate from MSX1. In this case I have a public certificate from DigiCert. It has 3 names (SAN certificate). Most of the time, you will see STS is the name for your ADFS service. I don't know why, but I picked ADFS. Just make sure you don't name your server ADFS, or you will have issues. You may be better off sticking with STS just to avoid confusion.
You can see the alternate names here:
The install finished, yeah!. Now click on configure
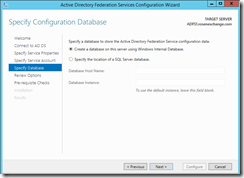
I suppose in a real production setup, you would use SQL.
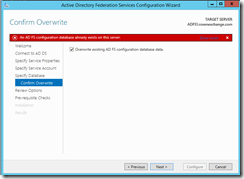
This is what my service looks like.. Since I already had this installed it looks like my settings didn't totally clear out. Note the organization tab is blank.
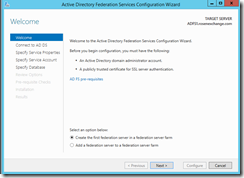
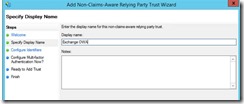
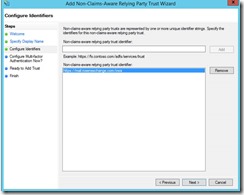
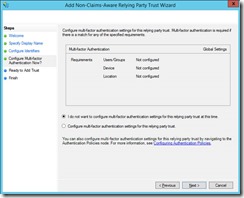
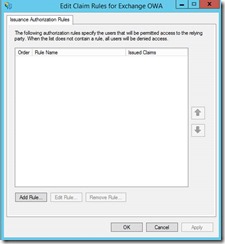
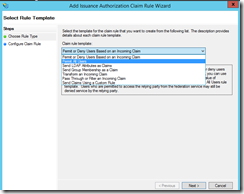
We need to add a non-claims aware relying party trust. Good thing there is a wizard.
If I get ambitious I may try to tackle using an AD group to secure the ECP directory rather than setting up an additional vdir in Exchange to limit Admin access to ECP from outside the company’s network.
To test your ADFS setup is working – you can go to the portal page - https://localhost/adfs/ls/idpinitiatedsignon.aspx
If you see this – continue on!
Setting up Exchange
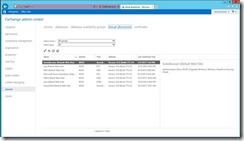
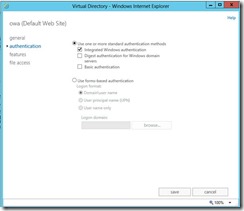
Goal: We need to change the authentication type for the OWA virtual directory to Windows Integrated Auth (from forms) in order for the delegated authentication to work.
On MSX1, open the ECP (https://localhost/ecp or https://msx1/ecp)
Ignore the cert warning.
Change the auth type.
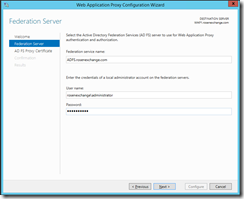
Setting up the WAP server
Goal: Install and configure remote access for OWA.
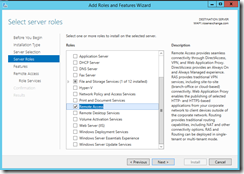
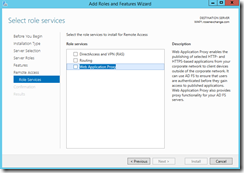
On WAP1, from server manager, we will install the Remote Access role.
Once you click Web Application Proxy, it will ask if you want to automatically add features, go ahead and leave the defaults and continue.
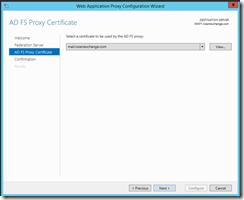
While that installs, import the certificate from the Exchange or ADFS server. I will not show these steps – they are the same as for the ADFS server using the Certificate MMC.
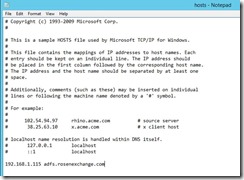
Next, edit the host file on WAP1. While everyone else in DNS gets the WAP server for the ADFS.rosenexchange.com address, the WAP server itself needs to be able to resolve that to the ADFS1 server. Yep, this is the way to do it.
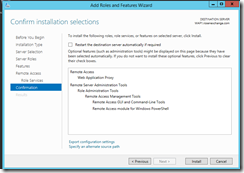
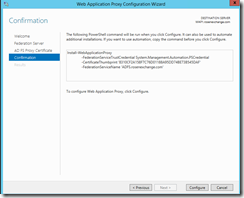
It will sit for a while on ‘configuring ADFS Proxy’
It will then launch the Remote Access Management Console.
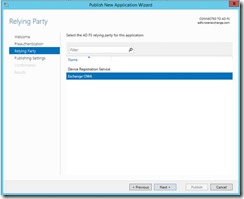
Click publish under General in the Tasks pane
Select Exchange OWA (you will see this since it made its connection back to the ADFS server and we setup the trust)
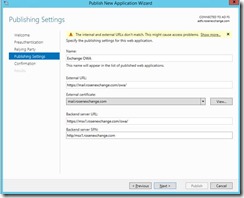
If you forget the trailing “/”, in a few screens you will get this error.
One thing to note, if you look in the certificates store, the server created a self-signed cert with a five days from the date of install expiration. I think this auto-updates itself – but if you turn off your lab machines and this expires – Im not sure what you do J.
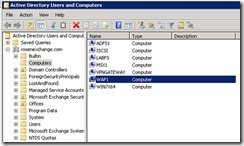
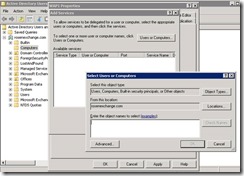
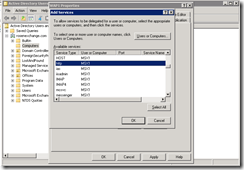
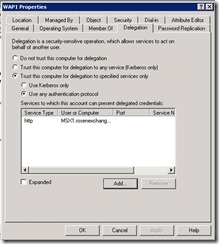
On DC1, we need to configure Kerberos constrained delegation.
Click Add, and it will pop up the ‘Add Services’ dialog box. Press ‘Users or Computer’ and enter MSX1.
Pick HTTP, then OK.
Note, it may show just MSX1, but if you ok and close the window, reopen the properties you should see the FQDN (MSX1.rosenexchange.com).
Finished
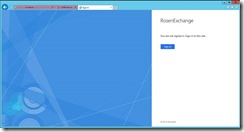
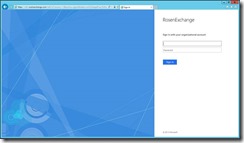
To test, on DC1, open IE and browse to https://mail.rosenexchange.com/OWA.
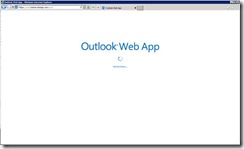
If you are successful, you should get this:
Finally, Yeah!! Im in my mailbox.
If you have issues a few things to check
· Make sure your time is synced (I synced everything to my DC)
· Make sure all the services are running
· The self-signed certs issue mentioned above
· Klist purge will clear out any Kerberos tickets
· Look in the event viewer – in 2012 R2 you have to look in the individual event logs to find the information (stuff is no longer just pushed to the application and system logs)
It my understanding that the WAP server(s) are stateless. So if you wanted to scale out – you could just use DNS RR or something to loadbalance your mail.rosenexchange.com address to all of the WAP servers. For ADFS, you can add servers to the farm. I haven't looked for any scale numbers..Im not sure any have been published yet.
Good luck, and I hope this helps you.
Jeffrey
Comments
- Anonymous
January 01, 2003
assuming your mailbox access via owa is https://owa.domain.com -> WAP server. What is your ADFS service name (not the server name)? Assume its STS (in my example its ADFS..but usually you will see STS.domain.com). STS's record -> Wap server. On the Wap server, edit the host file for STS to point to the ADFS server (ADFS-01.domain.dom's IP address). - Anonymous
January 01, 2003
The comment has been removed - Anonymous
January 01, 2003
Nope, this is correct and its why you need the host entry on the wap server - Anonymous
January 01, 2003
Lol..totally missed it..I fixed it..TY! - Anonymous
January 01, 2003
not sure I understand but ok:)the host file has ADFS>>pointing to some ip(the adfs server named adfs1where the adfs farm is called ADFS "I don't know why, but I picked ADFS."the table with the table at the top shows AFDS instead of ADFS where the host is poiting to.maybe its me:) - Anonymous
January 01, 2003
.Thanks finally the ADFS saga is over:) I am now just struggling with one thing its making this whole thing work with smart card/user certificate authentication seems to hang with these errors on the WAP: Connection to the backend server failed. Error: (0x80072ef1). Details: Transaction ID: {a1f09115-063d-0001-c994-f0a13d06cf01} Session ID: {a1f09115-063d-0001-b894-f0a13d06cf01} Published Application Name: OWA Published Application ID: 287E354F-AC7A-0336-37EA-124313C620CB Published Application External URL: https://mail.test.corp/owa/ Published Backend URL: https://ex1.test.corp/owa/ User: test2@test.corp User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E) Device ID: Token State: NotFound Cookie State: OK Client Request URL: https://mail.test.corp/owa/ev.owa2?ns=PendingRequest&ev=FinishNotificationRequest&UA=0&Fn=1&cid=3317d7b5-7014-4070-a758-b73cba2fa87b Backend Request URL: https://ex1.test.corp/owa/ev.owa2?ns=PendingRequest&ev=FinishNotificationRequest&UA=0&Fn=1&cid=3317d7b5-7014-4070-a758-b73cba2fa87b Preauthentication Flow: PreAuthBrowser Backend Server Authentication Mode: WIA State Machine State: BackendRequestProcessing_sync Response Code to Client: Response Message to Client: Client Certificate Issuer: and after that this: Connection to the backend server failed. Error: (0x80072ef1). Details: Transaction ID: {a1f09115-063d-0002-5197-f0a13d06cf01} Session ID: {a1f09115-063d-0001-b894-f0a13d06cf01} Published Application Name: OWA Published Application ID: 287E354F-AC7A-0336-37EA-124313C620CB Published Application External URL: https://mail.test.corp/owa/ Published Backend URL: https://ex1.test.corp/owa/ User: test2@test.corp User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E) Device ID: Token State: NotFound Cookie State: OK Client Request URL: https://mail.test.corp/owa/ev.owa2?ns=PendingRequest&ev=PendingNotificationRequest&UA=0&cid=3317d7b5-7014-4070-a758-b73cba2fa87b&X-OWA-CANARY=giCP_B9j9U6YZsCg36taEeWTLjxA1tAIzYOK_20dHJuOdXTQoTBGU1_x1Z_K8uPpJMGaNFi0nmg. Backend Request URL: https://ex1.test.corp/owa/ev.owa2?ns=PendingRequest&ev=PendingNotificationRequest&UA=0&cid=3317d7b5-7014-4070-a758-b73cba2fa87b&X-OWA-CANARY=giCP_B9j9U6YZsCg36taEeWTLjxA1tAIzYOK_20dHJuOdXTQoTBGU1_x1Z_K8uPpJMGaNFi0nmg. Preauthentication Flow: PreAuthBrowser Backend Server Authentication Mode: WIA State Machine State: FEBodyWriting Response Code to Client: 200 Response Message to Client: OK Client Certificate Issuer: seems like a problem with the back end reply(Exchange) on OWA virtual directory I have "accept client cert" enabled(not require, since I am testing user/pass also) - Anonymous
January 01, 2003
I think you miss understood me:)I understand the logic of how it worksI meant there is a typo in the table where it says AFDS instead of ADFS:)your setup is fine(I set it up myself too and all is good, except for that typo) - Anonymous
January 01, 2003
The comment has been removed - Anonymous
January 01, 2003
The comment has been removed - Anonymous
January 01, 2003
"> - Anonymous
January 20, 2014
The comment has been removed - Anonymous
March 15, 2014
in exchange 2013 sp1 you can setup claim aware
which means wap doesn't need to be domain member anymore
could you show a setup like that?
Thanks in advance - Anonymous
March 24, 2014
Great article - i would like for my users to type in http://webmail.contoso.com and for WAP to redirect to https://webmail.contoso.com/owa - how do you allow this to happen on the Web Application Proxy server?
I have successfully managed to redirect HTTP to HTTPS.
thanks - Anonymous
May 13, 2014
Pingback from TMG alternatives for Exchange publishing | Christopher Dargel's Exchange and Windows Blog - Anonymous
May 13, 2014
Pingback from TMG alternatives for Exchange publishing | Christopher Dargel's Exchange and Windows Blog - Anonymous
May 15, 2014
Pingback from TMG alternatives for Exchange publishing | Christopher Dargel's Exchange and Windows Blog