Sysinternals Sysmon suspicious activity guide
Sysmon tool from Sysinternals provides a comprehensive monitoring about activities in the operating system level. Sysmon is running in the background all the time, and is writing events to the event log.
You can find the Sysmon events under the Microsoft-Windows-Sysmon/Operational event log.
This guide will help you to investigate and appropriately handle these events.
Let's start with Microsoft Cybersecurity posture
Microsoft Cybersecurity posture consists of three pillars: Protect, Detect, and Respond. While Solid protection and rapid response capability are crucial, detection in depth is equally important. The focus in this blog post is on the last two:
- Detect – Install and configure Sysmon to capture the relevant events
- Respond - Investigate and respond to Sysmon events
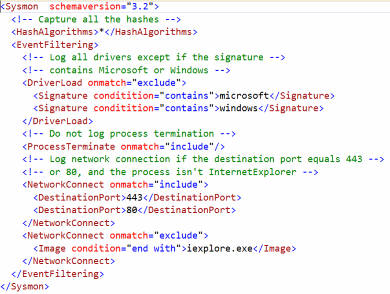
Sysmon Configuration file
A configuration file is used by Sysmon to store information about which events we want to include and which event we wish to exclude.
Configuration files may be specified after the -i (installation) or -c (installation) configuration switches. They make it easier to deploy a preset configuration and to filter captured events.
A sample configuration file with rules to log device drivers that are not related to Microsoft and Windows or only network connections over TCP ports 80 and 443:
A sample configuration file for enterprises based on my research and real-life deployments can be found in My GitHub repository.
How to deploy a Sysmon configuration file in an enterprise?
Sysmon rules and configuration settings are saved in the registry under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\SysmonDrv\Parameters 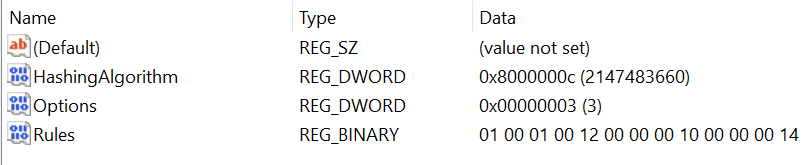
Using Group Policy Preferences (GPP) you can deploy Sysmon filtering rules across the entire organization (once installed, the service will poll its registry key for changes, and will be updated automatically, no restart is needed)
Step-By-Step instructions:
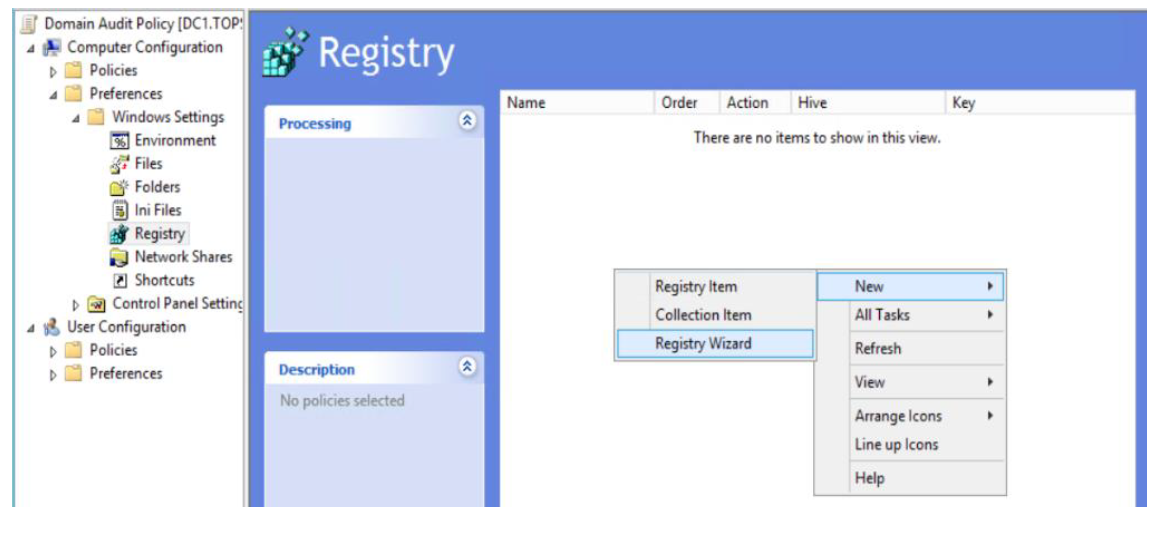
- Open Group Policy Editor, navigate to Computer Configuration, Preferences, Windows Settings and Registry
- Select Registry Wizard and New
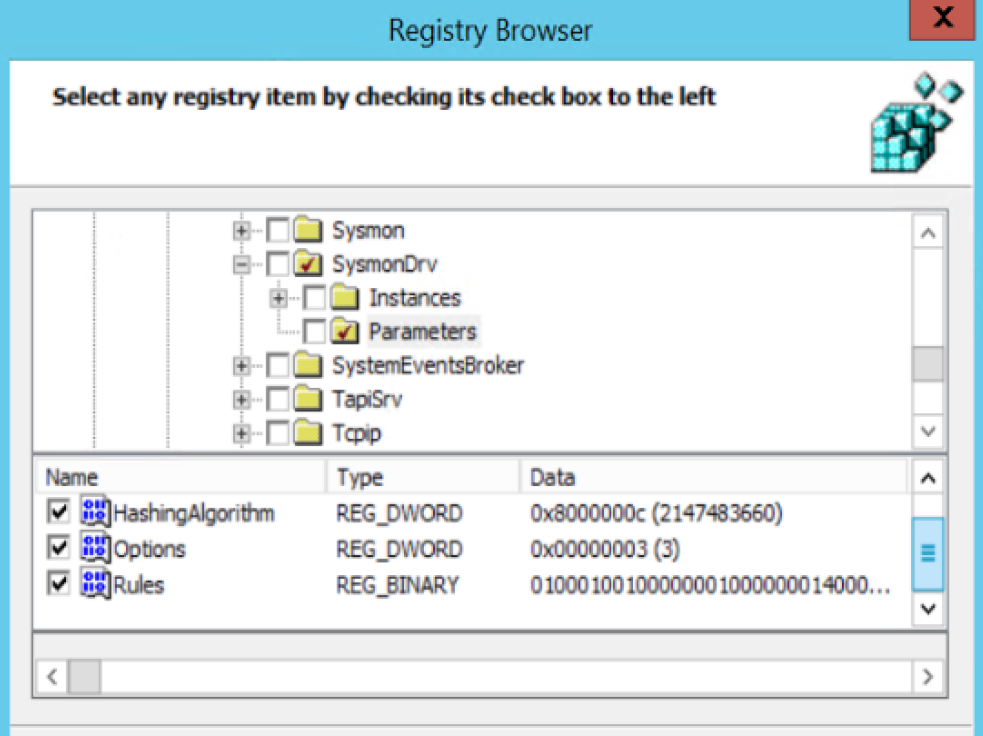
- Navigate to HKLM\SYSTEM\CurrentControlSet\Services\SysmonDrv\Parameters and check the following items: HashingAlgorithm, Options and Rules
 4. Deploy the GPO on the desired computers
4. Deploy the GPO on the desired computers
Prepare for security investigations
- Download and extract Sysinternals Suite file
- You can also download the latest version of specific files from https://live.sysinternals.com
Investigate suspicious process
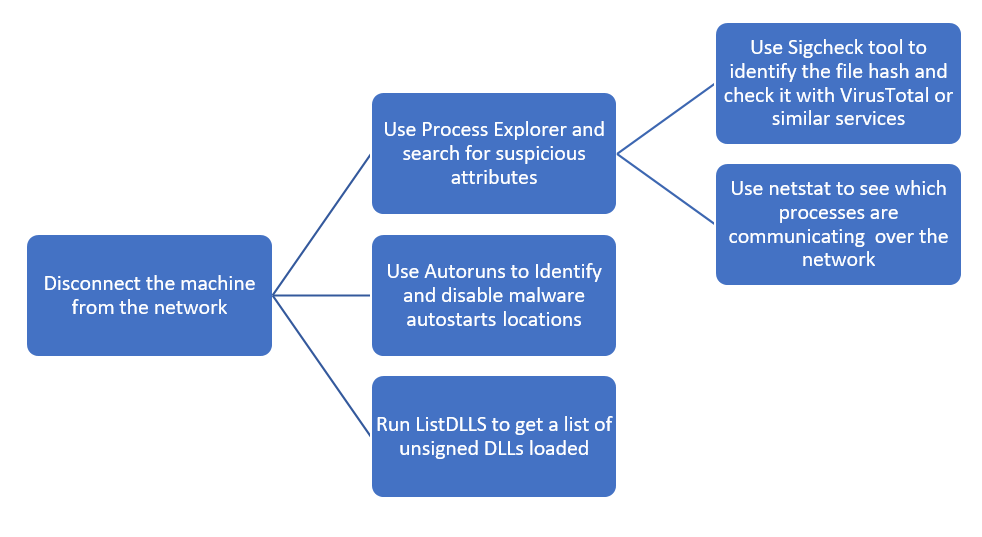
How do you identify processes that are suspicious? Mark Russinovich has told us to look for these suspicious process attributes when hunting malware with Process Explorer
- Have no icon, description or company name
- Run from Windows directory or user profile
- Started with wrong parent
- Misspelled process
- Unsigned executables
- Packed executables
- Host suspicious DLLs or services
- Have open TCP/IP endpoints
- Include strange URLs, strings in the executable
To summarize the most important analysis steps, you can use the accompanying graph:
Useful commands when investigating a suspicious file:
Run Sigcheck and search for any unsigned executables or VirusTotal's flagged executables:
sigcheck -vt -vr -e -u -s c:\
Run streams to detect alternate data streams:
streams -s c:\
Using PowerShell review the content of the Windows directory, and search for files with non-standard date-time:
Get-ChildItem -recurse | Where-Object { !$_.PsIsContainer } | Sort-Object -Descending { $_.CreationTime }
Note: Due to the complexity of modern threats it's recommend to utilize professional/automatic removal process.
Sysmon Events Activity Guide
Event ID 2 - A process changed a file creation time
Description
The change file creation time event is registered when a file creation time is explicitly modified by a process. This event helps tracking the real creation time of a file. Attackers may change the file creation time of a backdoor to make it look like it was installed with the operating system. Note that many processes legitimately change the creation time of a file; it does not necessarily indicate a malicious activity.
Investigation
- Is the source computer running an organization-approved ZIP extractor or web browser? If yes, you may ignore this alert because these applications are known to change file timestamps
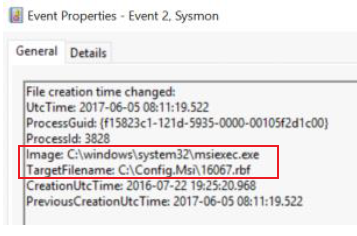
- Extract the following items from the event:
- Image -path is not Windows or ProgramFiles -Use Investigate suspicious processes section above
- TargetFileName -Use Investigate suspicious process table above
Remediation
Exclude an organization-approved application using the configuration file
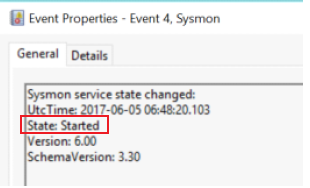
Event ID 4 - Sysmon service state changed
Description
The Sysmon service state change event reports the state of the Sysmon service (started or stopped).
Investigation
- The Sysmon Service state was changed to "Stopped"? If an attacker has privileges, Sysmon monitoring can be disabled by killing the Sysmon service. Investigate why the service had stopped by searching the System event log for events with "Service Control manager" source in the System log
Remediation
None, but it is always recommended to implement a centralized event logging infrastructure
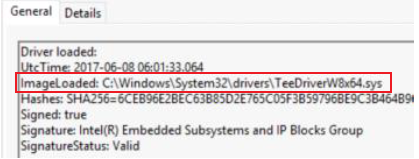
Event ID 6 - Driver loaded
Description
The driver loaded events provides information about a driver being loaded on the system. The configured hashes are provided as well as signature information. The signature is created asynchronously for performance reasons and indicates if the file was removed after loading.
Investigation
An attacker can exploit the Windows kernel by using a vulnerable device driver.
- Is the driver loaded is part of an organization-approved device drivers list? If yes, you may ignore this alert
- Extract the following items from the event:
- ImageLoaded – check if the path is not Windows or Windows\System32\Drivers - Use Investigate suspicious process table above
Remediation
None
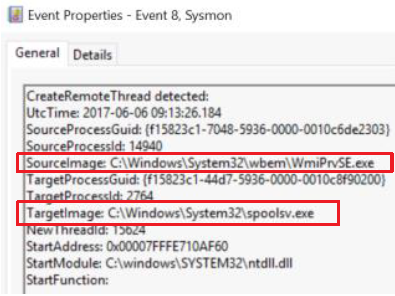
Event ID 8 - CreateRemoteThread
Description
The CreateRemoteThread event detects when a process creates a thread in another process. This technique is used by malware to inject code and hide in other processes. The event indicates the source and target process. It gives information on the code that will be run in the new thread: StartAddress, StartModule and StartFunction. Note that StartModule and StartFunction fields are inferred, they might be empty if the starting address is outside loaded modules or known exported functions.
Investigation
If an attacker has privileges, he can inject a custom DLL into the process's address space by using the CreateRemoteThread function call.
- Extract the following items from the event:
- SourceImage -path is not Windows or ProgramFiles -Use Investigate suspicious processes table above
- TargetImage -image is lsass, password manages, browsers or other sensitive accounts
Remediation
None
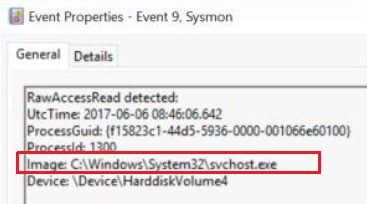
Event ID 9 - RawAccessRead
Description
The RawAccessRead event detects when a process conducts reading operations from the drive using the \\.\ denotation. This technique is often used by malware for data exfiltration of files that are locked for reading, as well as to avoid file access auditing tools. The event indicates the source process and target device.
Investigation
There are tools and PowerShell scripts that are capable of copying NTDS.dit, Registry hives, and any other file sitting on an NTFS volume by obtaining a read handle to the volume and parsing NTFS streams directly.
- Extract the following items from the event:
- Image -path is not Windows or ProgramFiles - Use Investigate suspicious process table above
- Image -path is not Windows or ProgramFiles - Use Investigate suspicious process table above
Remediation
None
Event ID 10 - ProcessAccess
Description
The process accessed event reports when a process opens another process, an operation that's often followed by information queries or reading and writing the address space of the target process. This enables detection of hacking tools that read the memory contents of processes like Local Security Authority (Lsass.exe) in order to steal credentials for use in Pass-the-Hash attacks. Enabling it can generate significant amounts of logging if there are diagnostic utilities active that repeatedly open processes to query their state, so it generally should only be done so with filters that remove expected accesses.
Investigation
- Extract the following items from the event:
- SourceImage -path is not Windows or ProgramFiles -Use Investigate suspicious processes table above
- TargetImage -image is lsass, password manages, browsers or other sensitive accounts
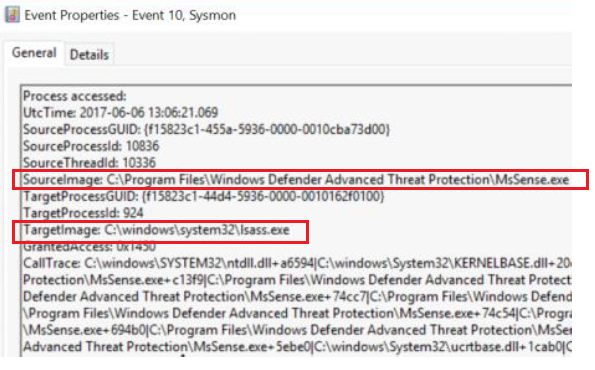
Remediation
In case of sensitive accounts and suspicious processes, assume that the accounts are compromised and replace their passwords
Event ID 15 - FileCreateStreamHash
Description
This event logs when a named file stream is created, and it generates events that log the hash of the contents of the file to which the stream is assigned (the unnamed stream), as well as the contents of the named stream. There are malware variants that drop their executables or configuration settings via browser downloads, and this event is aimed at capturing that based on the browser attaching a Zone.Identifier "mark of the web" stream.
Investigation
- Extract the following items from the event:
SourceImage -path is not Windows or ProgramFiles -Use Investigate suspicious processes table above
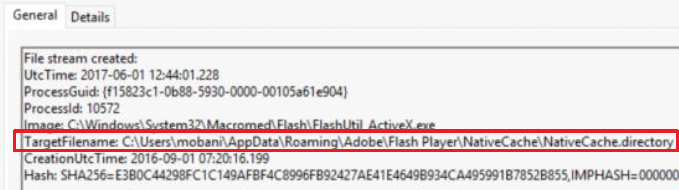
- By using Sysinternals streams we can check which files have alternate data-streams.
Remediation
If the alternate data stream is confirmed to be a malware or data related to a malware you can remove it using the PowerShell Remove-Item command
Comments
- Anonymous
December 08, 2017
Excellent article Moti, thank you! The default config file you shared is helpful - I will see if we can add a package to our monitoring solution EventSentry based on your rules. - Anonymous
December 08, 2017
Thanks. Very helpful. - Anonymous
December 10, 2017
Thanks, very helpful. Great job. - Anonymous
December 10, 2017
This is a must installation on any enterprise or home computer system. Thanks for the article! Looking foward to future blog posts. - Anonymous
December 11, 2017
is this something you just leave on, or is it only after you suspect something?- Anonymous
December 11, 2017
Can you clarify your question ? - Anonymous
December 11, 2017
Hi Nick - something you'd leave on - the link at the top of the articles goes into detail explaining how to install sysmon & registers it as a service.
- Anonymous
- Anonymous
December 11, 2017
Great post Moti!Does sysmon able to log a file that has been deleted by cmd prompt? Say a script calling powershell to delete a file.- Anonymous
December 13, 2017
Not currently, Sysmon is able to log only FileCreate events
- Anonymous
- Anonymous
December 12, 2017
Moti,Thx for the great article. I had a few question re: the install and update of the Sysmon filtering rules.I have an customized XML config file with my Sysmon filtering rules on a few systems and I would like to apply Sysmon and the customized XML Sysmon filtering rules to a large number of other systems. I assume I need to start Group Policy Preferences (GPP) from a system that already has Sysmon installed with the Sysmon filtering rules applied so that when I check the items - HashingAlgorithm, Options and Rules - these will be the Sysmon filtering rules that then get deployed to the other systems when the policy is pushed out?Also, to update the Sysmon filtering rules, once again I assume I'm updating the Sysmon filtering rules on the system that I use GPP so that way it will push the updated Sysmon filtering rules via GP?Thx- Anonymous
December 13, 2017
Hi, you can also connect to Remote Registry using Group Policy Preferences as well.To ease the deployment you can do all on baseline system, and then replicate the configuration to all other computers.- Anonymous
December 13, 2017
Thx MotiDo I need to copy the Sysmon XML file to all of the systems where Sysmon gets deployed, or does the fact the using GPP to create the reg keys apply those filtering rules?Still a little confused on if the XML file is needed on all systems that Sysmon is installed on, and how to update system with updated Sysmon filtering rules.Thx again- Anonymous
December 13, 2017
No need to copy the XML file, the registry (delivered by Group Policy Preferences) will do the work- Anonymous
December 13, 2017
Thx for the clarification! Most appreciated
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
January 13, 2018
Can this be considered a feature request to have Sysmon integrated with Windows moving forward? The value it provides is so great I would think Microsoft would integrate it.- Anonymous
January 14, 2018
It's way above my paygrade ;) But I'm also support this idea
- Anonymous