[Service Fabric] Securing an Azure Service Fabric cluster with Azure Active Directory via the Azure Portal
To make sure appropriate credit is given to a great article on this topic, I did take some of the information for the steps below from this article /en-us/azure/service-fabric/service-fabric-cluster-creation-via-arm. The article found at the link focuses on using an ARM template to do the deployment and secure setup. Using ARM would be the way you would want to set this up in a production environment.
My post is going to be using a more manual approach where you set the cluster up via the portal, for those of you who are just testing this out and want to learn how things are done via the portal. Some of the steps for setting this up in the portal will be short and will point to another article for portal setup of the cluster, but it’s the security setup we want to focus on.
So we will discuss:
- Setup of your cluster certificate
- Setup of Azure AD
- Azure Cluster creation
- Testing your Admin and Read-only user login
Setting up your cluster certificate
My purpose for using Azure Active Directory (AAD) was to setup an admin user and a read-only user so they could access the Service Fabric Explorer with those permissions. You still need to have a cluster certificate to secure the cluster though.
- Open PowerShell ISE as an Administrator.
- In the PowerShell command window, log in to your Azure subscription using 'Login-AzureRMAccount'. When you do this, in the command window you will see the subscriptionID. You need to copy the subscriptionID, because you will need that in the PowerShell script to create the Azure AD application. Also copy the tenantID value.
- Run the following PS script. This script create a new resource group for your key vault, a key vault, a self-signed certificate and a secret key. You will need to record the information that appears in the PS command prompt output window after the successful execution of this script. Fill in the variables with your own values. Note that it is usually best just to save the script code below to a PS file first.
#-----You have to change the variable values-------#
# This script will:
# 1. Create a new resource group for your key vaults
# 2. Create a new key vault
# 3. Create, export and import (to your certificate store) a self-signed certificate
# 4. Create a new secret and put the cert in key vault
# 5. Output the values you will need to supply to your cluster for cluster cert security.
# Make sure you copy these values before closing the PowerShell window
#--------------------------------------------------#
#Name of the Key Vault service
$KeyVaultName = "<your-vault-name>"
#Resource group for the Key-Vault service.
$ResourceGroup = "<vault-resource-group-name>"
#Set the Subscription
$subscriptionId = "<your-Azure-subscription-ID>"
#Azure data center locations (East US", "West US" etc)
$Location = "<region>"
#Password for the certificate
$Password = "<certificate-password>"
#DNS name for the certificate
$CertDNSName = "<name-of-your-certificate>"
#Name of the secret in key vault
$KeyVaultSecretName = "<secret-name-for-cert-in-vault>"
#Path to directory on local disk in which the certificate is stored
$CertFileFullPath = "C:\<local-directory-to-place-your-exported-cert>\$CertDNSName.pfx"
#If more than one under your account
Select-AzureRmSubscription -SubscriptionId $subscriptionId
#Verify Current Subscription
Get-AzureRmSubscription -SubscriptionId $subscriptionId
#Creates the a new resource group and Key-Vault
New-AzureRmResourceGroup -Name $ResourceGroup -Location $Location
New-AzureRmKeyVault -VaultName $KeyVaultName -ResourceGroupName $ResourceGroup -Location $Location -sku standard -EnabledForDeployment
#Converts the plain text password into a secure string
$SecurePassword = ConvertTo-SecureString -String $Password -AsPlainText -Force
#Creates a new selfsigned cert and exports a pfx cert to a directory on disk
$NewCert = New-SelfSignedCertificate -CertStoreLocation Cert:\CurrentUser\My -DnsName $CertDNSName
Export-PfxCertificate -FilePath $CertFileFullPath -Password $SecurePassword -Cert $NewCert
Import-PfxCertificate -FilePath $CertFileFullPath -Password $SecurePassword -CertStoreLocation Cert:\LocalMachine\My
#Reads the content of the certificate and converts it into a json format
$Bytes = [System.IO.File]::ReadAllBytes($CertFileFullPath)
$Base64 = [System.Convert]::ToBase64String($Bytes)
$JSONBlob = @{
data = $Base64
dataType = 'pfx'
password = $Password
} | ConvertTo-Json
$ContentBytes = [System.Text.Encoding]::UTF8.GetBytes($JSONBlob)
$Content = [System.Convert]::ToBase64String($ContentBytes)
#Converts the json content a secure string
$SecretValue = ConvertTo-SecureString -String $Content -AsPlainText -Force
#Creates a new secret in Azure Key Vault
$NewSecret = Set-AzureKeyVaultSecret -VaultName $KeyVaultName -Name $KeyVaultSecretName -SecretValue $SecretValue -Verbose
#Writes out the information you need for creating a secure cluster
Write-Host
Write-Host "Resource Id: "$(Get-AzureRmKeyVault -VaultName $KeyVaultName).ResourceId
Write-Host "Secret URL : "$NewSecret.Id
Write-Host "Thumbprint : "$NewCert.Thumbprint
The information you need to record will appear similar to this:
Resource Id: /subscriptions/<your-subscriptionID>/resourceGroups/<your-resource-group>/providers/Microsoft.KeyVault/vaults/<your-vault-name>
Secret URL : https://<your-vault-name>.vault.azure.net:443/secrets/<secret>/<generated-guid>
Thumbprint : <certificate-thumbprint>
Setting up Azure Active Directory
- To secure the cluster with Azure AD, you will need to decide which AD directory in your subscription you will be using. In this example, we will use the 'default' directory. In step 2 above, you should have recorded the 'tenantID'. This is the ID associated with your default Active directory. NOTE: If you have more than one directory (or tenant) in your subscription, you are going to have to make sure you get the right tenantID from your AAD administrator. The first piece of script you need to save to a file named Common.ps1 is:
<#
.VERSION
1.0.3
.SYNOPSIS
Common script, do not call it directly.
#>
if($headers){
Exit
}
Try
{
$FilePath = Join-Path $PSScriptRoot "Microsoft.IdentityModel.Clients.ActiveDirectory.dll"
Add-Type -Path $FilePath
}
Catch
{
Write-Warning $_.Exception.Message
}
function GetRESTHeaders()
{
# Use common client
$clientId = "1950a258-227b-4e31-a9cf-717495945fc2"
$redirectUrl = "urn:ietf:wg:oauth:2.0:oob"
$authenticationContext = New-Object Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext -ArgumentList $authString, $FALSE
$accessToken = $authenticationContext.AcquireToken($resourceUrl, $clientId, $redirectUrl, [Microsoft.IdentityModel.Clients.ActiveDirectory.PromptBehavior]::RefreshSession).AccessToken
$headers = New-Object "System.Collections.Generic.Dictionary[[String],[String]]"
$headers.Add("Authorization", $accessToken)
return $headers
}
function CallGraphAPI($uri, $headers, $body)
{
$json = $body | ConvertTo-Json -Depth 4 -Compress
return (Invoke-RestMethod $uri -Method Post -Headers $headers -Body $json -ContentType "application/json")
}
function AssertNotNull($obj, $msg){
if($obj -eq $null -or $obj.Length -eq 0){
Write-Warning $msg
Exit
}
}
# Regional settings
switch ($Location)
{
"china"
{
$resourceUrl = "https://graph.chinacloudapi.cn"
$authString = "https://login.partner.microsoftonline.cn/" + $TenantId
}
default
{
$resourceUrl = "https://graph.windows.net"
$authString = "https://login.microsoftonline.com/" + $TenantId
}
}
$headers = GetRESTHeaders
if ($ClusterName)
{
$WebApplicationName = $ClusterName + "_Cluster"
$WebApplicationUri = "https://$ClusterName"
$NativeClientApplicationName = $ClusterName + "_Client"
}
You do not need to execute this script, it will be called by the next script, so make sure you have Common.ps1 in the same folder as the next script.
2. Create a new script file and paste in the code below. Name this file SetupApplications.ps1. Note that you will need to record some of the output from the execute of this script (explained below) for later use.
<#
.VERSION
1.0.3
.SYNOPSIS
Setup applications in a Service Fabric cluster Azure Active Directory tenant.
.PREREQUISITE
1. An Azure Active Directory tenant.
2. A Global Admin user within tenant.
.PARAMETER TenantId
ID of tenant hosting Service Fabric cluster.
.PARAMETER WebApplicationName
Name of web application representing Service Fabric cluster.
.PARAMETER WebApplicationUri
App ID URI of web application.
.PARAMETER WebApplicationReplyUrl
Reply URL of web application. Format: https://<Domain name of cluster>:<Service Fabric Http gateway port>
.PARAMETER NativeClientApplicationName
Name of native client application representing client.
.PARAMETER ClusterName
A friendly Service Fabric cluster name. Application settings generated from cluster name: WebApplicationName = ClusterName + "_Cluster", NativeClientApplicationName = ClusterName + "_Client"
.PARAMETER Location
Used to set metadata for specific region: china. Ignore it in global environment.
.EXAMPLE
. Scripts\SetupApplications.ps1 -TenantId '4f812c74-978b-4b0e-acf5-06ffca635c0e' -ClusterName 'MyCluster' -WebApplicationReplyUrl 'https://mycluster.westus.cloudapp.azure.com:19080'
Setup tenant with default settings generated from a friendly cluster name.
.EXAMPLE
. Scripts\SetupApplications.ps1 -TenantId '4f812c74-978b-4b0e-acf5-06ffca635c0e' -WebApplicationName 'SFWeb' -WebApplicationUri 'https://SFweb' -WebApplicationReplyUrl 'https://mycluster.westus.cloudapp.azure.com:19080' -NativeClientApplicationName 'SFnative'
Setup tenant with explicit application settings.
.EXAMPLE
. $ConfigObj = Scripts\SetupApplications.ps1 -TenantId '4f812c74-978b-4b0e-acf5-06ffca635c0e' -ClusterName 'MyCluster' -WebApplicationReplyUrl 'https://mycluster.westus.cloudapp.azure.com:19080'
Setup and save the setup result into a temporary variable to pass into SetupUser.ps1
#>
Param
(
[Parameter(ParameterSetName='Customize',Mandatory=$true)]
[Parameter(ParameterSetName='Prefix',Mandatory=$true)]
[String]
$TenantId,
[Parameter(ParameterSetName='Customize')]
[String]
$WebApplicationName,
[Parameter(ParameterSetName='Customize')]
[String]
$WebApplicationUri,
[Parameter(ParameterSetName='Customize',Mandatory=$true)]
[Parameter(ParameterSetName='Prefix',Mandatory=$true)]
[String]
$WebApplicationReplyUrl,
[Parameter(ParameterSetName='Customize')]
[String]
$NativeClientApplicationName,
[Parameter(ParameterSetName='Prefix',Mandatory=$true)]
[String]
$ClusterName,
[Parameter(ParameterSetName='Prefix')]
[Parameter(ParameterSetName='Customize')]
[ValidateSet('china')]
[String]
$Location
)
Write-Host 'TenantId = ' $TenantId
. "$PSScriptRoot\Common.ps1"
$graphAPIFormat = $resourceUrl + "/" + $TenantId + "/{0}?api-version=1.5"
$ConfigObj = @{}
$ConfigObj.TenantId = $TenantId
$appRole =
@{
allowedMemberTypes = @("User")
description = "ReadOnly roles have limited query access"
displayName = "ReadOnly"
id = [guid]::NewGuid()
isEnabled = "true"
value = "User"
},
@{
allowedMemberTypes = @("User")
description = "Admins can manage roles and perform all task actions"
displayName = "Admin"
id = [guid]::NewGuid()
isEnabled = "true"
value = "Admin"
}
$requiredResourceAccess =
@(@{
resourceAppId = "00000002-0000-0000-c000-000000000000"
resourceAccess = @(@{
id = "311a71cc-e848-46a1-bdf8-97ff7156d8e6"
type= "Scope"
})
})
if (!$WebApplicationName)
{
$WebApplicationName = "ServiceFabricCluster"
}
if (!$WebApplicationUri)
{
$WebApplicationUri = "https://ServiceFabricCluster"
}
if (!$NativeClientApplicationName)
{
$NativeClientApplicationName = "ServiceFabricClusterNativeClient"
}
#Create Web Application
$uri = [string]::Format($graphAPIFormat, "applications")
$webApp = @{
displayName = $WebApplicationName
identifierUris = @($WebApplicationUri)
homepage = $WebApplicationReplyUrl #Not functionally needed. Set by default to avoid AAD portal UI displaying error
replyUrls = @($WebApplicationReplyUrl)
appRoles = $appRole
}
switch ($Location)
{
"china"
{
$oauth2Permissions = @(@{
adminConsentDescription = "Allow the application to access " + $WebApplicationName + " on behalf of the signed-in user."
adminConsentDisplayName = "Access " + $WebApplicationName
id = [guid]::NewGuid()
isEnabled = $true
type = "User"
userConsentDescription = "Allow the application to access " + $WebApplicationName + " on your behalf."
userConsentDisplayName = "Access " + $WebApplicationName
value = "user_impersonation"
})
$webApp.oauth2Permissions = $oauth2Permissions
}
}
$webApp = CallGraphAPI $uri $headers $webApp
AssertNotNull $webApp 'Web Application Creation Failed'
$ConfigObj.WebAppId = $webApp.appId
Write-Host 'Web Application Created:' $webApp.appId
#Service Principal
$uri = [string]::Format($graphAPIFormat, "servicePrincipals")
$servicePrincipal = @{
accountEnabled = "true"
appId = $webApp.appId
displayName = $webApp.displayName
appRoleAssignmentRequired = "true"
}
$servicePrincipal = CallGraphAPI $uri $headers $servicePrincipal
$ConfigObj.ServicePrincipalId = $servicePrincipal.objectId
#Create Native Client Application
$uri = [string]::Format($graphAPIFormat, "applications")
$nativeAppResourceAccess = $requiredResourceAccess +=
@{
resourceAppId = $webApp.appId
resourceAccess = @(@{
id = $webApp.oauth2Permissions[0].id
type= "Scope"
})
}
$nativeApp = @{
publicClient = "true"
displayName = $NativeClientApplicationName
replyUrls = @("urn:ietf:wg:oauth:2.0:oob")
requiredResourceAccess = $nativeAppResourceAccess
}
$nativeApp = CallGraphAPI $uri $headers $nativeApp
AssertNotNull $nativeApp 'Native Client Application Creation Failed'
Write-Host 'Native Client Application Created:' $nativeApp.appId
$ConfigObj.NativeClientAppId = $nativeApp.appId
#Service Principal
$uri = [string]::Format($graphAPIFormat, "servicePrincipals")
$servicePrincipal = @{
accountEnabled = "true"
appId = $nativeApp.appId
displayName = $nativeApp.displayName
}
$servicePrincipal = CallGraphAPI $uri $headers $servicePrincipal
#OAuth2PermissionGrant
#AAD service principal
$uri = [string]::Format($graphAPIFormat, "servicePrincipals") + '&$filter=appId eq ''00000002-0000-0000-c000-000000000000'''
$AADServicePrincipalId = (Invoke-RestMethod $uri -Headers $headers).value.objectId
$uri = [string]::Format($graphAPIFormat, "oauth2PermissionGrants")
$oauth2PermissionGrants = @{
clientId = $servicePrincipal.objectId
consentType = "AllPrincipals"
resourceId = $AADServicePrincipalId
scope = "User.Read"
startTime = (Get-Date).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ss.fffffff")
expiryTime = (Get-Date).AddYears(1800).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ss.fffffff")
}
CallGraphAPI $uri $headers $oauth2PermissionGrants | Out-Null
$oauth2PermissionGrants = @{
clientId = $servicePrincipal.objectId
consentType = "AllPrincipals"
resourceId = $ConfigObj.ServicePrincipalId
scope = "user_impersonation"
startTime = (Get-Date).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ss.fffffff")
expiryTime = (Get-Date).AddYears(1800).ToUniversalTime().ToString("yyyy-MM-ddTHH:mm:ss.fffffff")
}
CallGraphAPI $uri $headers $oauth2PermissionGrants | Out-Null
$ConfigObj
#ARM template
Write-Host
Write-Host '-----ARM template-----'
Write-Host '"azureActiveDirectory": {'
Write-Host (" `"tenantId`":`"{0}`"," -f $ConfigObj.TenantId)
Write-Host (" `"clusterApplication`":`"{0}`"," -f $ConfigObj.WebAppId)
Write-Host (" `"clientApplication`":`"{0}`"" -f $ConfigObj.NativeClientAppId)
Write-Host "},"
3. Execute the following command from the PS command prompt window:
.\SetupApplications.ps1 -TenantId '<your-tenantID>' -ClusterName '<your-cluster-name>.<region>.cloudapp.azure.com' -WebApplicationReplyUrl 'https://<your-cluster-name>.<region>.cloudapp.azure.com:19080/Explorer/index.html'
The ClusterName is used to prefix the AAD applications created by the script. It does not need to match the actual cluster name exactly as it is only intended to make it easier for you to map AAD artifacts to the Service Fabric cluster that they're being used with. This can be a bit confusing because you haven't created your cluster yet. But, if you know what name you plan to give your cluster, you can use it here.
The WebApplicationReplyUrl is the default endpoint that AAD returns to your users after completing the sign-in process. You should set this to the Service Fabric Explorer endpoint for your cluster, which by default is: https://<cluster_domain>:19080/Explorer
Record the information at the bottom of the command prompt window. You will need this information when you deploy your cluster from the portal. The information will look similar to what you see below.
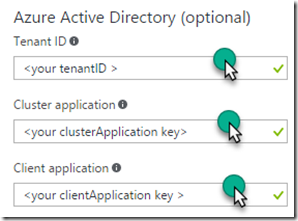
"azureActiveDirectory": {
"tenantId":"<Your-AAD-tenantID>",
"clusterApplication":"1xxxxxxxx-x68e-490a-89c8-2894e4b8686a",
"clientApplication":"xxxxxxx-7825-4e1e-a586-f0ff8d9e679e"
NOTE: You may receive a Warning that you have a missing assembly. You can ignore this warning.
4. After you run the script in step 6, log in to the classic Azure portal at https://manage.windowsazure.com. For now you need to use the classic Azure portal because the production portal Azure Active Directory features are still in preview.
5. Find your Azure Active Directory in the list and click on it.
6. Add 2 new users to your directory. Name them whatever you want just as long as you know which one is Admin and which one would be the read-only user. Make sure to record the password that is initially generated, because the first time you try to log in to the portal as this user, you will be asked to change the password.
7. Within your AAD, click on the Applications menu. In the Show drop-down box, pick Applications My Company Owns and then click on the check button over to the right to do a search.
8. You should see two applications listed. One will be for Native client applications and the other for Web Applications. Click on the application name for the web application type. Since we will be doing our connectivity test connecting to the Service Fabric Explorer web UI, this is the application we need to set the user permissions on.
9. Click on the Users menu.
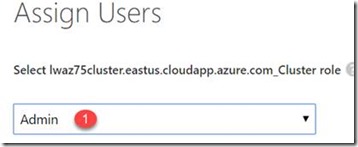
10. Click on the user name that should be the administrator and then select the Assign button at the bottom of the portal Window.
11. In the Assign Users dialog box, pick Admin from the dropdown box and select the check button.
12. Repeat 10 and 11 but this time, for the read-only user select Read-only from the Assign Users drop-down. This step completes what you will need to do in the classic portal, so you can close the classic portal window.
13. You now have all the information you need to create your cluster in the portal. Log in to the Azure Portal at https://portal.azure.com.
Creating your Service Fabric cluster
- Create a new resource group and then within the resource group start the process of adding a new Service Fabric Cluster to the resource group. As you are stepping through creating the cluster, you will find 4 core blades with information you need to provide:
-
- Basic - unique name for the cluster, operating system, username/password for RDP access etc.
- Cluster configuration - node type count, node configuration, diagnostics etc.
- Security - This is where we want to focus in the next step….
NOTE: If you want more details about creating your Service Fabric cluster via the portal, go to /en-us/azure/service-fabric/service-fabric-cluster-creation-via-portal ~ the procedures at this link uses certificates for Admin and Read-only user setup, not AAD.
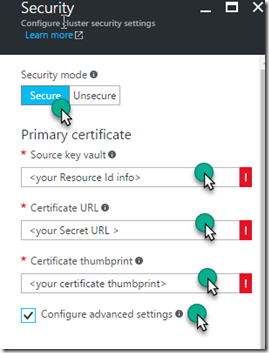
2. In the cluster Security blade, make sure the Security mode is set to Secure. It is by default.
3. The output from the first PS script you executed will contain the information you need for the Primary certificate information. After you enter your recorded information, make sure to select the Configure advanced settings checkbox.
4. By selecting the Configure advanced settings checkbox, the blade will expand (vertically) and you can scroll down in the blade to find the area where you need to enter the Active Directory information. The information you recorded when you executed SetupApplications.ps1 will be used here.
5. Select the Ok button in the Security blade.
6. Complete the Summary blade after the portal validates your settings.
Testing your Admin and Read-only user access
- Once the cluster has completed the creation process, make sure you log out of the Azure portal. This assures that when you attempt to log in as the Admin or Read-only user, you will not accidentally log in to the portal as the subscription administrator.
- Log in to the portal as either the Admin or Read-only user. You will need to change the temporary password you were provided early and then the log in will complete.
- Open up a new browser window and log in to https://<yourfullclustername>:19080/Explorer/. Test the Explorer functionality.
Hope this helps you in your work with Azure Service Fabric!
Comments
- Anonymous
January 09, 2017
thank you, I am so much to learn from this article