Windows 10 1709 Hyper-V Networking Enhancement
Hello All, today I want to share a new feature in Windows 10 1709 client hyper-v. This change is specifically in the Hyper-V networking stack, and is a direct result of a design change request filed by one of our customers. The change centers around how a virtual machines network traffic is routed via the host. In previous versions of client Hyper-V, virtual machines were unable to utilize all of the hosts connected network interfaces - including VPN network interfaces. What this meant was that the VMs could not route through or "use" the hosts VPN connection. There are a number of reasons why you would want a given VM to be able to use the hosts VPN connection, maybe you have a PAW VM that you want to use to administer your corporate network remotely with, or you have a small lab setup on your machine that needs access to corporate resources, or you want your VMs to be able to dynamically access the internet regardless of if the host is using a wired or wireless connection, etc. These are just a few and there are likely more use case scenarios for this, so we've heard customers say that they want this virtualization networking capability and with Windows 10 version 1709 it is here.
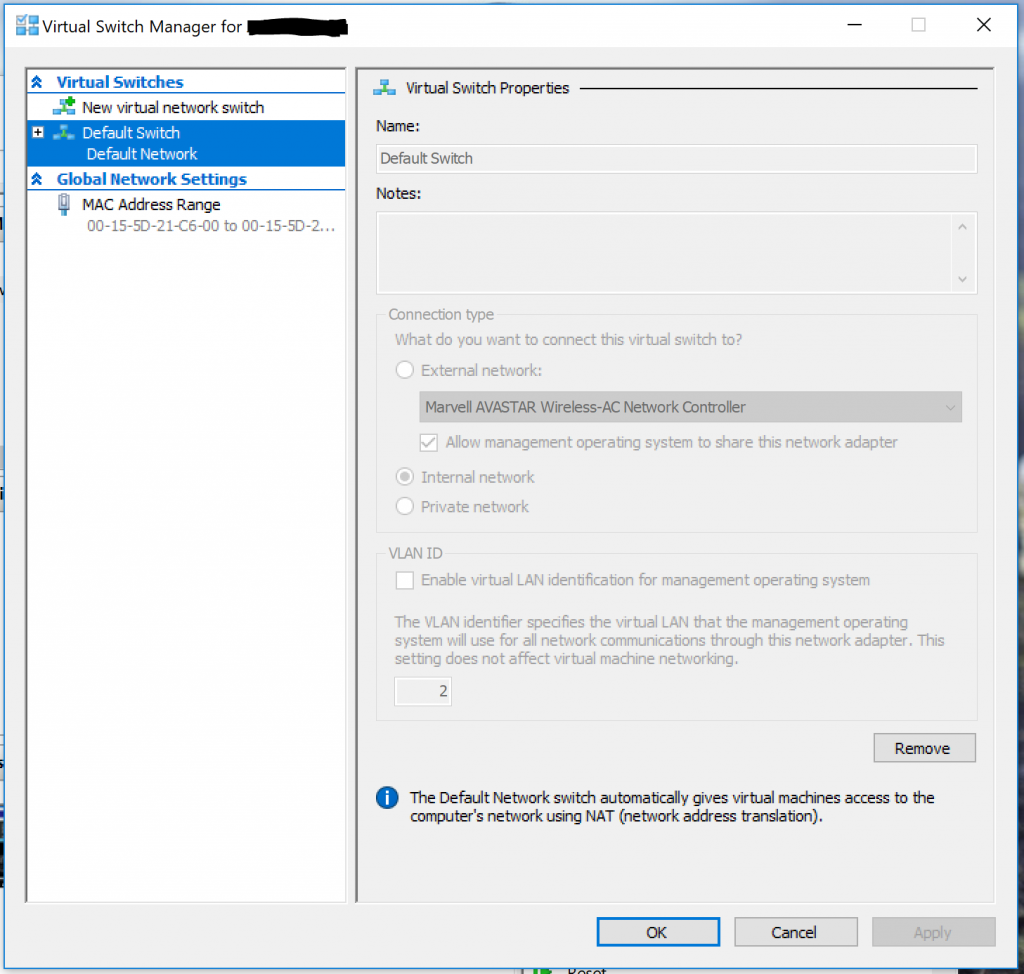
The functionality arrives in the form of a new "Default Switch" in Hyper-V. As you can see, this switch cannot be modified. It also cannot be deleted, it is here to stay! The default switch uses NAT to dynamically assign addresses to the VMs that are connected to it.
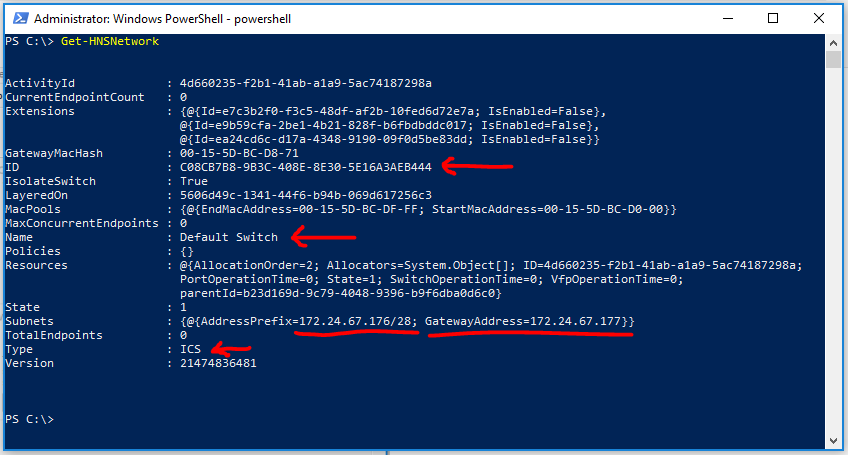
Additional information on the default switch can be obtained by running the Get-HNSNetwork PowerShell cmdlet. Here you can see the Name of the switch, the ID of the switch - which as mentioned in the other post never changes, and the subnet used to dynamically assign addresses to VMs, as well as the type.
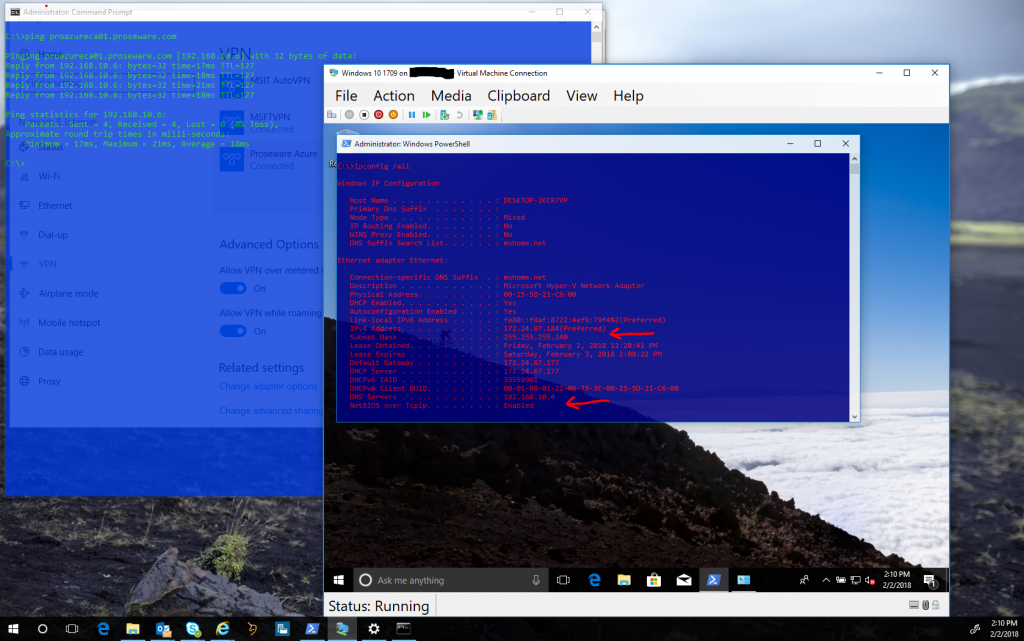
Putting it all together. Of course you'll want to install Hyper-V, create your VM, and install your OS. To demonstrate this capability I've installed and configured an Azure point to site VPN on my host machine for my Azure subscription. I've successfully connected that VPN on my host machine. Now looking at the VM we can see its ip configuration and what its been assigned by the host:
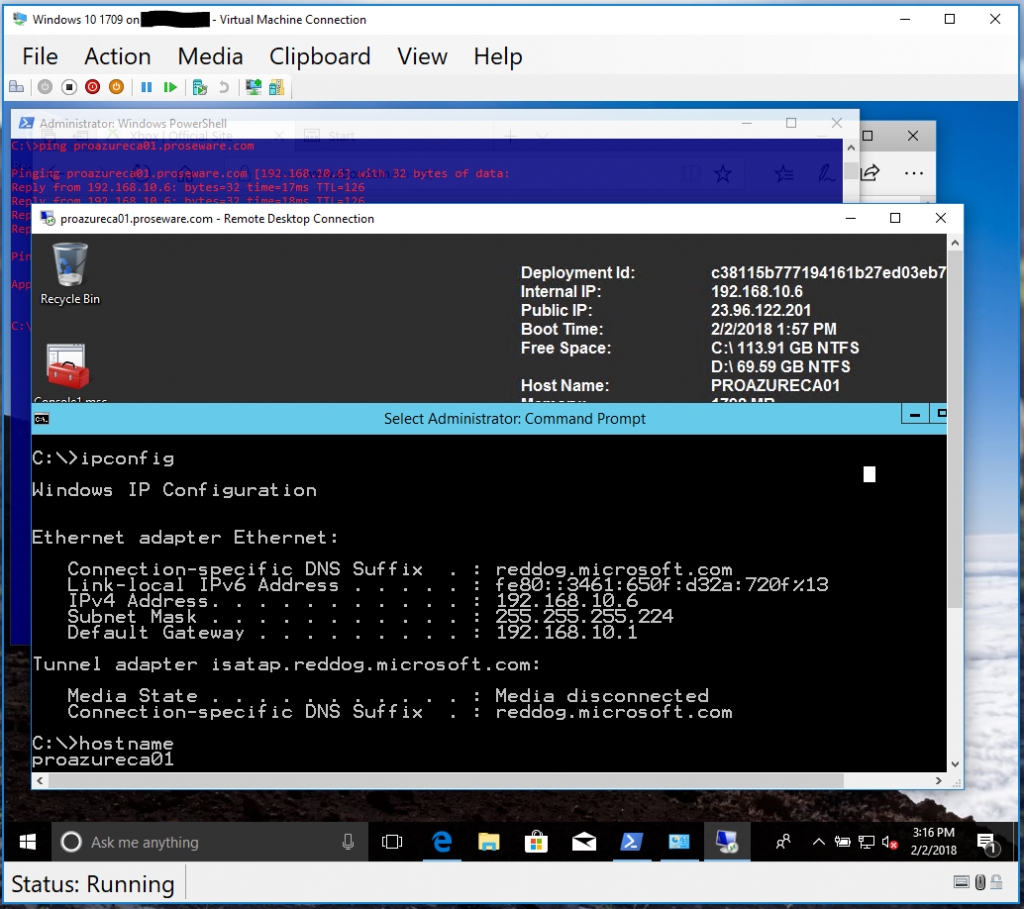
Note we have tcp connectivity to the target Azure VM from both the host AND the VM! So here we can see that the virtual machine is in fact using the Hosts connected VPN tunnel. I've changed the dynamically assigned DNS server on my VM to my Azure DNS server, this allows me to resolve DNS names in my Azure subscription, and DNS names on the internet. With that - on my VM I'm able to route through the hosts VPN tunnel, seen here as I RDP into one of my IaaS VMs in Azure!
This is a nifty feature that I hope you find useful as you move forward with client Hyper-V on Windows 10. I'm curious to see what doors this unlocks for people, I know I have a few ideas of my own for this...
What will you do with this feature, and how will it enable you to be more productive and creative?
Jesse
Comments
- Anonymous
May 16, 2018
Hi Jesse, really interesting topic for me: I switched from Virtualbox to Hyper-v and got lost.In Virtualbox I never had problems in having the VPN connection set up by the host, used by the VM as well (provided I started the VM after the VPN); now with Hyper-v ,I'm unable to make the VMs use my company SSTP based VPN: M?????N .Could you please detail the steps necessary to have that type of VPN being used by the VMs?Maybe another blog post? I've seen other people asking almost the same question (in that case was from VMware Workstation to Hyper-v) and it would be nice if Microsoft (you really :-) could give an answer.Again, thanks for your article.- Anonymous
May 24, 2018
Hi Francesco - what build of Windows 10 are you on? This feature is only present in build 16257 and greater.- Anonymous
May 24, 2018
17134.48 , thanks.
- Anonymous
- Anonymous