UAG SSL Network Tunneling traffic capture
Occasionally, one may need to troubleshoot the UAG Network Tunnling (a.k.a. “the Network Connector”). Normally, traffic capturing is done using tools such as Microsoft’s Network Monitor, or WireShark. If, however, you try to run a capture like that on a UAG client that is connected with the SSL Network Tunneling, you will discover that the client freezes, as the capture driver conflicts with the tunneling components.
There is, however, another way to capture this sort of traffic, using UAG’s built-in TCPDumper. Here is how to do this:
1. On the UAG client, log-off any existing UAG session, and close the browser.
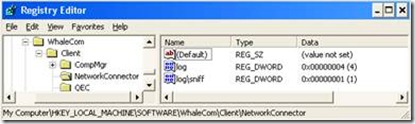
2. Open the registry editor.
3. Navigate to HKLM\SOFTWARE\WhaleCom\Client\NetworkConnector
4. Create a new DWORD value and name it “log”
5. Set the value to 4
6. Create a new DWORD value and name it “log\sniff”
7. Set the value to 1:
8. Exit the registry editor
9. Launch a browser window, and establish your SSL tunnel, and reproduce the issue you need to investigate.
10. When done, log-off the UAG portal, and close the browser, to make sure the SSL-VPN component shuts down gracefully.
11. Re-open the registry editor, and remove the values you have created, or change to “0” and “ - “respectively.
12. Go to the UAG client component folder (c:\program files\Microsoft Forefront UAG\Endpoint Components\3.1.0), where you will find a file called whliocsv.log.lowlevel.dmp. This file is actually a standard CAP file. You can ask Windows to open it with your network capture software, and it will display like any regular capture!
Comments
- Anonymous
September 25, 2013
Hi I followed your guide however the dump file never gets created and I've tried on various machines. One difference I did notice that the reg key is under Wow6432Node. Any help would be appreciated