Windows 10 v1607 - DualScan behavior when "Do not allow update deferral policies to cause scans against Windows Update" is set.
Applies to:
Windows 10 1803 ((tbd))
Windows 10 1709 (Fall Creators update)
Windows 10 1703 (Creators update)
Windows 10 1607 (Anniversary update) / Windows Server 2016
Does not apply to:
Windows 10 1511 (November update)
Windows 10 1507 (RTM)
While I was in Oxnard, California. the following topic came up.
Before you read this, you want to make sure that you go through:
Demystifying “Dual Scan”
https://blogs.technet.microsoft.com/wsus/2017/05/05/demystifying-dual-scan/
Improving Dual Scan on 1607
https://blogs.technet.microsoft.com/wsus/2017/08/04/improving-dual-scan-on-1607/
Using ConfigMgr With Windows 10 WUfB Deferral Policies
Once you have read the 3 blog post above, continue for this particular issue.
[Problem description]
If you have “Windows 10 1607” deployed in Semi-Annual Channel (used to be known as (u.t.b.k.a) Current Branch for Business (CBB)).
And have:
- WSUS set to not deploy “Windows 10 1703” or “Windows 10 1709”.
- According to Improving Dual Scan on 1607, KB4034658 (August 2017 Cumulative update) introduces a new GPO ("Do not allow update deferral policies to cause scans against Windows Update").
https://blogs.technet.microsoft.com/wsus/2017/08/04/improving-dual-scan-on-1607/
And if you have the October 2017 Cumulative update KB4041691 installed.
And these other hotfixes:
KB3186568
KB4013418
KB4023834
KB4033637
KB4035631
KB4038806
KB4051613
- And we have set the "Do not allow update deferral policies to cause scans against Windows Update" in the registry:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"DisableDualScan"=dword:00000001
Expectation:
When going to “Windows Update”
When clicking on “Check online for updates from Microsoft Update”
Result:
To not see “Feature Update to Windows 10, 1703” being offered.
Result:
“Feature Update to Windows 10, 1703” is being offered.
[Cause]
Why?
Windows 10 1607 allows deferment of the feature update for 180 days.
You can only defer up to 180 days prior to version 1703.
You are falling under this below with the manual/adhoc scans against MU:
“Windows updates from WSUS, supplemental updates from WU - the "on-premises" scenario. Here you expect your users to perform ad hoc scans every so often to get updates that are necessary, but have not been deployed by the enterprise admins. You want quality updates, but do not want feature updates offered during these scans. The policy to disable Dual Scan was created for this scenario: you can enable the new policy, along with your deferral policies, and those deferral policies will only take effect when scanning against Windows [or Microsoft] Update.”
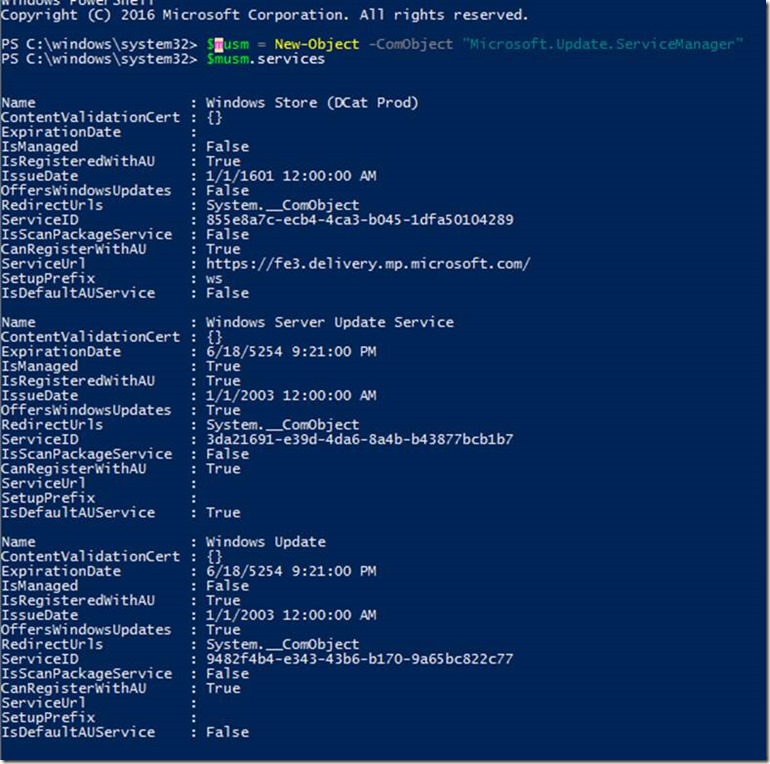
How can you check if DualScan is set?
Powershell (Run As Admin)
$MUSM = New-Object -ComObject “Microsoft.Update.ServiceManager”
$MUSM.Services
IsDefaultAUService
True for "Windows Server Update Service"
False for "Windows Update"
then the following could be causing it:
HKLM\Software\Microsoft\WindowsUpdate\UX\Settings\DeferUpgrade=1
// Was not set.
And/or
HKLM\Software\Microsoft\WindowsUpdate\UX\Settings\BranchReadinessLevel=32
// Was not set.
| How long can you defer? | If you are in SAC-T (u.t.b.k.a CB), what feature update are you going to get? | If you are in SAC (u.t.b.k.a CBB), what feature update are you going to get? | |
| 1803 | 365 days | 1903 | 1809 |
| 1709 | 365 days | 1809 | 1803 |
| 1703 | 365 days | 1803 | 1709 |
| 1607 | 180 days | 1709 | 1703 |
| 1511 | 180 days | Not applicable, Dual Scan was not present. | Not applicable, Dual Scan was not present. |
| 1507 | 180 days | Not applicable, Dual Scan was not present. | Not applicable, Dual Scan was not present. |
Source:
Configure Windows Update for Business
/en-us/windows/deployment/update/waas-configure-wufb
Why this could be a problem?
· If you are using a 3rd party encryption, thus, when this is deployed w/o the ‘/reflecteddrivers’ switch and the ‘compatible’ 3rd party encryption upper filter drivers, it can bricked your system.
· They have in-house apps that are not yet “Windows 10 1703” ‘compatible’, thus need additional time before you upgrade.
[Solution]
Blocking access to “Windows update” via:
-
- Computer Configuration\Administrative Templates\System\Internet Communication Management\Internet Communication settings\Turn off access to all Windows Update features
What do you lose if you disable “Windows Updates”?
· Update drivers (e.g. Print drivers, etc…)
or
-
- User Configuration\Administrative Templates\Start Menu and Taskbar\Remove links and access to Windows Update
What do you lose if you disable “Windows Updates”?
· Update drivers (e.g. Print drivers, etc…)
· Universal apps (Windows Store apps)
Note:
-
- Windows UI
- HKLM\Software\Microsoft\WindowsUpdate\UX\Settings\
- Group Policy
- HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate
- MDM (CSP by SCCM 1706 WUfB policy, Intune, or other MDM Providers)
- HKLM\Software\Microsoft\PolicyManager\current\device\Update
- Windows UI
Thanks.
Yong
Comments
- Anonymous
March 13, 2018
With "Computer Configuration\Administrative Templates\System\Internet Communication Management\Internet Communication settings\Turn off access to all Windows Update features" you do not lose the store apps. With "Do not connect to any Windows Update Internet locations" you will lose the store apps.- Anonymous
March 16, 2018
Thx Andrei. Updated the post. Yong
- Anonymous