Tutorial: Configure Azure Active Directory B2C with Datawiza to provide secure hybrid access
In this tutorial, learn how to integrate Azure Active Directory B2C (Azure AD B2C) with Datawiza Access Proxy (DAP), which enables single sign-on (SSO) and granular access control, helping Azure AD B2C protect on-premises legacy applications. With this solution, enterprises can transition from legacy to Azure AD B2C without rewriting applications.
Prerequisites
To get started, you'll need:
- A Microsoft Entra subscription
- If you don't have one, you can get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
- Docker, an open platform for developing, shipping, and running applications, is required to run DAB
- Your applications can run on platforms such as virtual machine and bare metal
- An on-premises application to transition from a legacy identity system, to Azure AD B2C
- In this tutorial, DAB is deployed on the same server as the application
- The application runs on localhost: 3001 and DAP proxies traffic to applications via localhost: 9772
- The application traffic reaches DAB first and then is proxied to the application
Scenario description
Datawiza integration includes the following components:
- Azure AD B2C: The authorization server to verify user credentials
- Authenticated users access on-premises applications using a local account stored in the Azure AD B2C directory
- Datawiza Access Proxy (DAP): The service that passes identity to applications through HTTP headers
- Datawiza Cloud Management Console (DCMC): A management console for DAB. DCMC UI and RESTful APIs help manage DAB configurations and access control policies
The following architecture diagram shows the implementation.
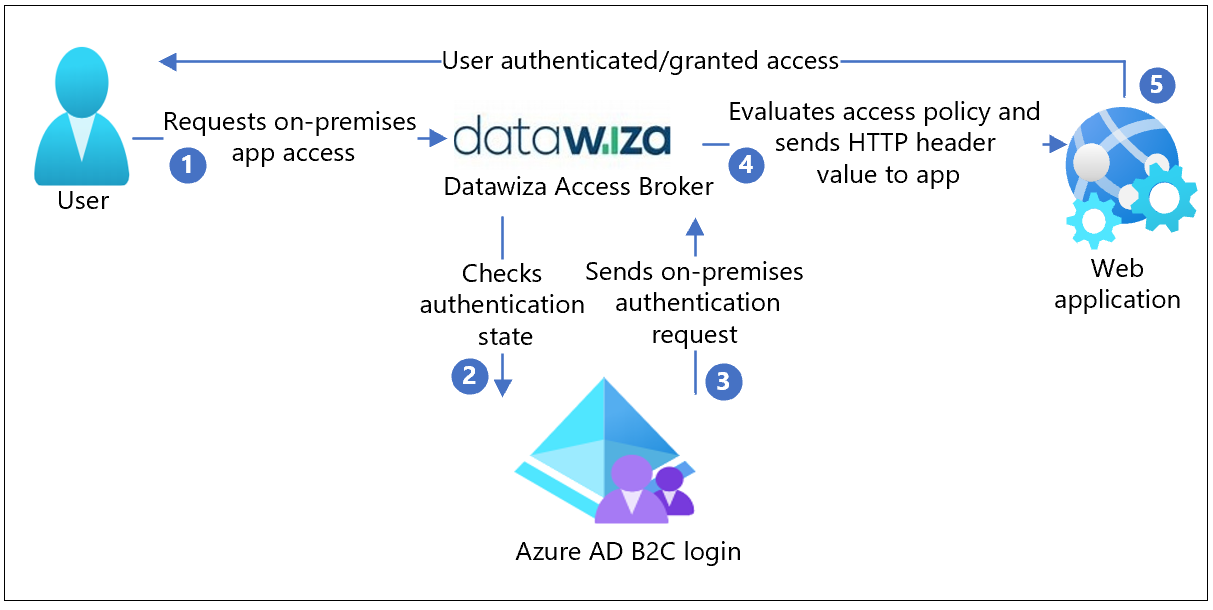
- The user requests access to an on-premises application. DAB proxies the request to the application.
- DAP checks user authentication state. With no session token, or an invalid token, the user goes to Azure AD B2C for authentication.
- Azure AD B2C sends the user request to the endpoint specified during DAP registration in the Azure AD B2C tenant.
- The DAP evaluates access policies and calculates attribute values in HTTP headers forwarded to the application. The DAP might call to the identity provider (IdP) to retrieve information to set the header values. The DAP sets the header values and sends the request to the application.
- The user is authenticated with access to the application.
Onboard with Datawiza
To integrate your legacy on-premises app with Azure AD B2C, contact Datawiza.
Configure your Azure AD B2C tenant
Go to docs.datawiza.com to:
Learn how to register your web application in an Azure AD B2C tenant, and configure a sign up-and sign-in user flow. For more info, see Azure AD B2C.
Configure a user flow in the Azure portal.
Note
When you set up DAB in the DCM, you need the tenant name, user flow name, client ID, and client secret.
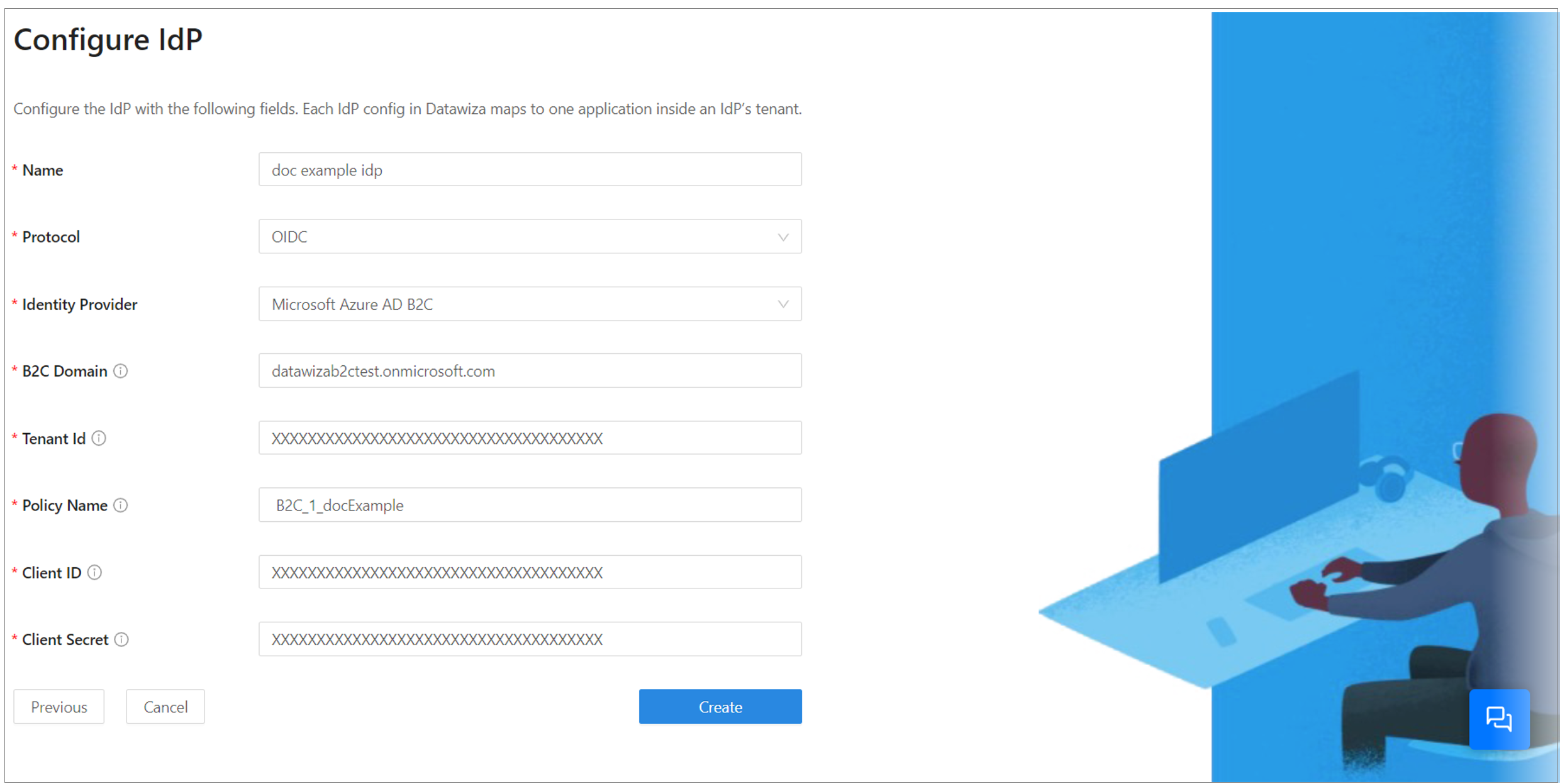
Create an application in DCMC
In DCMC, create an application and generate a key pair of
PROVISIONING_KEYandPROVISIONING_SECRETfor this application. See, Datawiza Cloud Management Console.Configure IdP with Azure AD B2C. See, Part I: Azure AD B2C Configuration.
Run DAB with a header-based application
You can use Docker or Kubernetes to run DAP. Use the Docker image for users to create a sample header-based application.
Learn more: To configure DAP and SSO integration, see Deploy Datawiza Access Proxy With Your App
A sample docker image docker-compose.yml file is provided. Sign in to the container registry to download DAP images and the header-based application.
Deploy Datawiza Access Proxy With Your App.
version: '3' services: datawiza-access-broker: image: registry.gitlab.com/datawiza/access-broker container_name: datawiza-access-broker restart: always ports: - "9772:9772" environment: PROVISIONING_KEY: ############################# PROVISIONING_SECRET: ############################# header-based-app: image: registry.gitlab.com/datawiza/header-based-app container_name: ab-demo-header-app restart: always environment: CONNECTOR: B2C ports: - "3001:3001"The header-based application has SSO enabled with Azure AD B2C.
Open a browser and enter
http://localhost:9772/.An Azure AD B2C sign-in page appears.
Pass user attributes to the header-based application
DAB gets user attributes from IdP and passes them to the application with header or cookie. After you configure user attributes, the green check sign appears for user attributes.
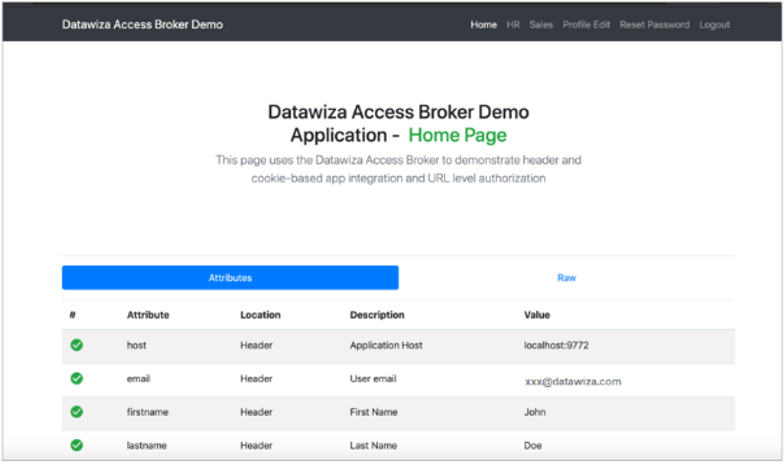
Learn more: Pass User Attributes such as email address, firstname, and lastname to the header-based application.
Test the flow
- Navigate to the on-premises application URL.
- The DAP redirects to the page you configured in your user flow.
- From the list, select the IdP.
- At the prompt, enter your credentials. If necessary, include a Microsoft Entra multifactor authentication token.
- You're redirected to Azure AD B2C, which forwards the application request to the DAP redirect URI.
- The DAB evaluates policies, calculates headers, and sends the user to the upstream application.
- The requested application appears.