Configure TheAccessHub Admin Tool with Azure Active Directory B2C
In this tutorial, learn how to integrate Azure Active Directory B2C (Azure AD B2C) with TheAccessHub Admin Tool from N8 Identity N8ID. The solution addresses customer account migration and customer service request (CSR) administration.
Use this solution for the following scenarios:
- You have a site and want to migrate to Azure AD B2C.
- However, customer-account migration is challenging, including passwords.
- You need a CSR tool to administer Azure AD B2C accounts.
- Delegated CSR administration is a requirement.
- You want to synchronize and merge data from repositories into Azure AD B2C.
Prerequisites
To get started, you need:
An Azure subscription
- If you don't have a one, you can get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
- TheAccessHub Admin Tool environment
- See, N8 Identity/contact for a new environment
- Optional:
- Connection and credential information for databases or Lightweight Directory Access Protocols (LDAPs), from which you want to migrate customer data
- A configured Azure AD B2C environment for custom policies to integrate TheAccessHub Admin Tool into your sign-up policy flow
Scenario description
The TheAccessHub Admin Tool runs in the N8ID Azure subscription or the customer subscription. The following architecture diagram shows the implementation.
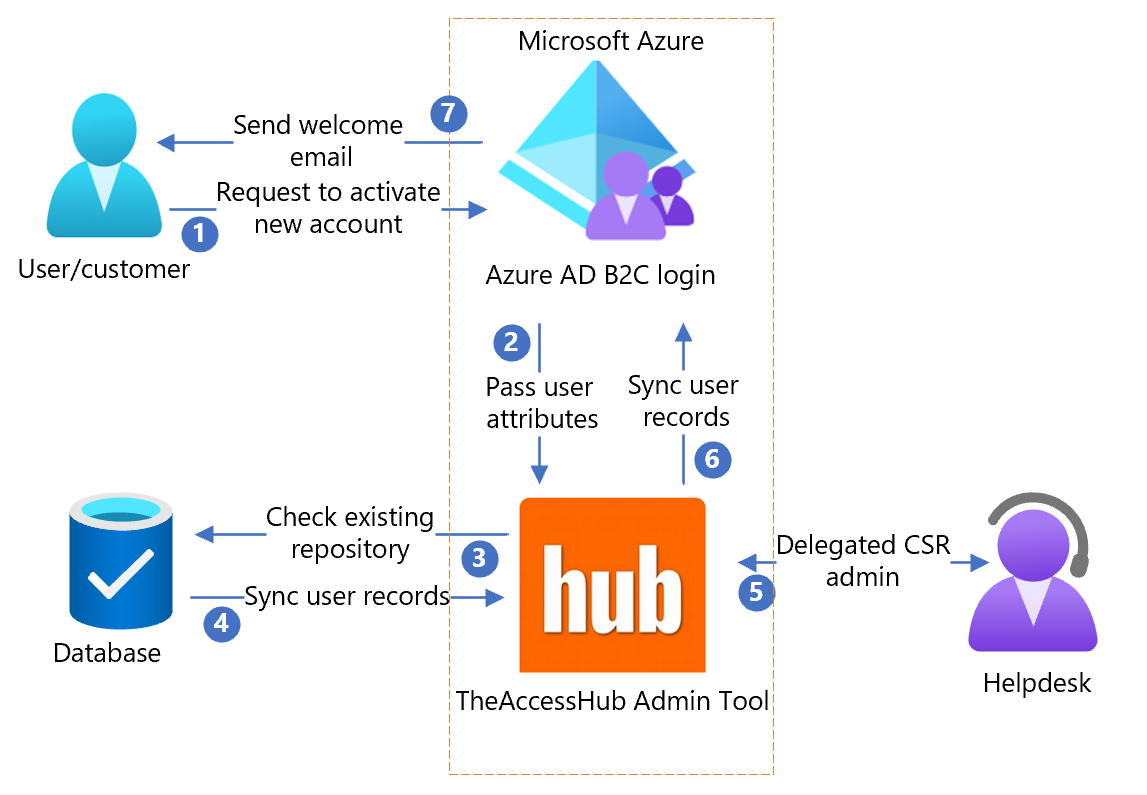
- User arrives on a sign-in page, creates an account, and enters information. Azure AD B2C collects user attributes.
- Azure AD B2C calls the TheAccessHub Admin Tool and passes the user attributes.
- TheAccessHub Admin Tool checks your database for current user information.
- User records synchronize from the database to TheAccessHub Admin Tool.
- TheAccessHub Admin Tool shares the data with the delegated CSR or helpdesk admin.
- TheAccessHub Admin Tool syncs user records with Azure AD B2C.
- Based on TheAccessHub Admin Tool response, Azure AD B2C sends a customized welcome email to users.
Create an External Identity Provider Administrator and B2C User Flow Administrator in your Azure AD B2C tenant
TheAccessHub Admin Tool permissions act on behalf of an External Identity Provider Administrator and B2C User Flow Administrator to read user information and conduct changes in your Azure AD B2C tenant. Changes to your regular administrators don't affect TheAccessHub Admin Tool interaction with the tenant.
To create an External Identity Provider Administrator and B2C User Flow Administrator:
- In the Azure portal, sign in to your Azure AD B2C tenant as an Administrator.
- Go to Microsoft Entra ID > Users.
- Select New User.
- Choose Create User to create a regular directory user and not a customer.
- On the identity information form:
- Enter the username, such as theaccesshub.
- Enter the account name, such as TheAccessHub Service Account.
- Select Show Password.
- Copy and save the initial password.
- To assign the External Identity Provider Administrator and B2C User Flow Administrator role, for User, select the user's current role.
- Select the External Identity Provider Administrator and B2C User Flow Administrator records.
- Select Create.
Connect TheAccessHub Admin Tool to your Azure AD B2C tenant
TheAccessHub Admin Tool uses the Microsoft Graph API to read and make changes to a directory. It acts as an External Identity Provider Administrator and B2C User Flow Administrator in your tenant. Use the following instructions to add needed permissions.
To authorize TheAccessHub Admin Tool to access your directory:
- Use the credentials N8 Identity provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Azure AD B2C Config.
- Select Authorize Connection.
- In the new window, sign in with your External Identity Provider Administrator and B2C User Flow Administrator account. When you sign in for the first time with the new service account, a prompt to reset your password can appear.
- Follow the prompts and select Accept.
Configure a new CSR user with your enterprise identity
Create a CSR or Helpdesk user who accesses TheAccessHub Admin Tool with enterprise Microsoft Entra credentials.
To configure a CSR or Helpdesk user with single sign-on (SSO):
- Use the credentials N8 Identity provided to sign in to TheAccessHub Admin Tool.
- Go to Manager Tools > Manage Colleagues.
- Select Add Colleague.
- For Colleague Type, select Azure Administrator.
- For the profile information, select a home organization to control who has permission to manage this user.
- For Login ID/Azure AD User Name, enter the user principal name from the user Microsoft Entra account.
- On the TheAccessHub Roles tab, select the Helpdesk managed role.
- Select Submit.
Note
The Helpdesk role provides access to the Manage Colleagues view. Place the user into a group or make them an organization owner.
Configure a new CSR user with a new identity
Create a CSR or Helpdesk user to access TheAccessHub Admin Tool with a new local credential. This user is for organizations that don't use Microsoft Entra ID.
See, The AccessHub Admin Tool: Add Colleague Administrator without SSO.
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to Manager Tools > Manage Colleagues.
- Select Add Colleague.
- For Colleague Type, select Local Administrator.
- For the profile information, select a home organization to control who has permission to manage this user.
- On the TheAccessHub Roles tab, select the Helpdesk managed role.
- Copy the Login ID/Email and One Time Password attributes. Provide them to the new user to sign in to TheAccessHub Admin Tool.
- Select Submit.
Note
The Helpdesk role provides access to the Manage Colleagues view. Place the user into a group or make them an organization owner.
Configure partitioned CSR administration
In TheAccessHub Admin Tool, permissions to manage customer and CSR/Helpdesk users are managed through an organization hierarchy. Colleagues and customers have a home organization. You can assign colleagues or colleague groups as organization owners.
Organization owners can manage and change colleagues and customers in organizations or suborganizations they own. For multiple colleagues to manage a set of users, create a group with multiple members. Then, assign the group as an organization owner. All group members can manage colleagues and customers in the organization.
Create a new group
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to Organization > Manage Groups.
- Select Add Group.
- Enter values for Group name, Group description, and Group owner.
- Search for and select the boxes for colleagues to be members of the group.
- Select Add.
- Group members appear at the bottom of the page. Select the X on a row to remove a member.
- Select Submit.
Create a new organization
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to Organization > Manage Organizations.'
- Select Add Organization.
- Enter values for Organization name, Organization owner, and Parent organization
- Select Submit.
Note
Align the organization name with customer data. When loading colleague and customer data, and you enter the organization name in the load, the colleague appears in the organization. The owner manages customers and colleagues in the organization and suborganizations. The parent organization is responsible for the organization.
Modify the hierarchy via the tree view
Use this function to visualize colleague and group management.
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to Manager Tools > Tree View.
- To modify the hierarchy, drag organizations into parent organizations.
- Select Save.
Customize the welcome notification
If you're using TheAccessHub Admin Tool to migrate users from one solution into Azure AD B2C, you can customize the user welcome notification. The notification goes to users during migration and can include a link to set a new password in the Azure AD B2C directory.
To customize the notification:
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Notifications.
- Select the Create Colleague template.
- Select Edit.
- Make needed changes to the Message and Template. The Template field is HTML-aware and can send HTML-formatted notifications.
- Select Save.
Migrate data from external data sources to Azure AD B2C
With TheAccessHub Admin Tool, you can import data from various databases, LDAPs, and .csv files and then push that data to your Azure AD B2C tenant. You load the data to migrate it into the Azure AD B2C user colleague type in TheAccessHub Admin Tool.
Tip
If the data source isn't Azure, the data goes into TheAccessHub Admin Tool and Azure AD B2C. If the external data source isn't a .csv file on your machine, set up a data source before the data load. Use the following steps to create a data source and load the data.
Configure a data source
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Data Sources.
- Select Add Data Source.
- Supply Name and Type values for this data source.
- Enter form data for databases:
- Type: Database
- Database type: select a supported database
- Connection URL: enter a Java Database Connectivity (JDBC) connection string, such as
jdbc:postgresql://myhost.com:5432/databasename - Username: username to access the database
- Password: password to access the database
- Query: the SQL query to extract customer details, such as
SELECT * FROM mytable;' - Select Test Connection. A data sample appears to confirm the connection is working.
- Enter form data for LDAPs:
- Type: LDAP
- Host: host name, or IP address, of the machine on which the LDAP server runs, such as
mysite.com - Port, port number in which the LDAP server is listening
- SSL, select the box for the TheAccessHub Admin Tool to communicate to the LDAP with SSL (recommended)
- Login DN: user account distinguished name (DN) to sign in and do the LDAP search
- Password: user password
- Base DN: DN at the top of the hierarchy in which to do the search
- Filter: LDAP filter string to obtain your customer records
- Attributes: comma-separated attribute list, from your customer records, to pass to TheAccessHub Admin Tool
- Select the Test Connection. A data sample appears to confirm the connection is working.
- Enter data for OneDrive. Type: OneDrive for Business.'
- Select Authorize Connection.
- A new window prompts you to sign in to OneDrive. Sign in with read access to the OneDrive account. TheAccessHub Admin Tool reads .csv load files.
- Follow the prompts and select Accept.
- Select Save.
Synchronize data from your data source into Azure AD B2C
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Data Synchronization.
- Select New Load.
- Colleague Type: Azure AD B2C User.
- Select Source. In the dialog, select your data source. If you created a OneDrive data source, select the file.
- To create new customer accounts, change the first policy, IF colleague not found in TheAccessHub THEN: Do Nothing.
- To update customer accounts, change the second policy, IF source and TheAccessHub data mismatch THEN: Do Nothing.
- Select Next.
- In Search-Mapping configuration, identify load-record correlation with customers in TheAccessHub Admin Tool.
- Select source identifying attributes. Match attributes TheAccessHub Admin Tool attributes with the same values. If there's a match, the record is overridden. Otherwise, a new customer is created.
- Sequence the number of checks. For example, check email first, then first and family name.
- On the left-side menu, select Data Mapping.
- In Data-Mapping configuration, assign the TheAccessHub Admin Tool attributes to be populated from your source attributes. Unmapped attributes remain unchanged for customers. If you map the attribute
org_namewith a current organization value, created customers go in the organization. - Select Next.
- For this load to be recurring, select Daily/Weekly or Monthly. Otherwise, keep the default, Now.
- Select Submit.
- For the Now schedule, a new record is added to Data Synchronizations.
- When validation is 100 percent, select the new record to see the outcome. For scheduled loads, records appear after the scheduled time.
- If there are no errors, select Run. Otherwise, to remove the load, from the More menu, select Remove.
- If there are errors, you can manually update the records. On each record, select Update and make corrections.
- When Data Synchronization is 100 percent, customers appear or receive changes in Azure AD B2C.
Tip
If there are multiple errors, you can continue with errors and resolve them later. In TheAccessHub Admin Tool, use Support Interventions.
Synchronize Azure AD B2C customer data
TheAccessHub Admin Tool can synchronize customer information from Azure AD B2C into TheAccessHub Admin Tool as a one-time, or an ongoing, operation. This operation ensures CSR or Helpdesk administrators see up-to-date customer information.
To synchronize data from Azure AD B2C into TheAccessHub Admin Tool:
- Use the credentials N8ID provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Data Synchronization.
- Select New Load.
- Colleague Type: Azure AD B2C User.
- For Options, leave the defaults.
- Select Next.
- For Data Mapping & Search, leave the defaults. Exception: if you map the attribute
org_nameto a current organization value, created customers appear in the organization. - Select Next.
- For load to be recurring, select a Daily/Weekly or Monthly schedule. Otherwise, leave the Now default. We recommend recurring.
- Select Submit.
- If you selected Now, a new record appears on Data Synchronizations. After validation is 100 percent, select the new record to see the load outcome. For scheduled loads, records appear after the scheduled time.
- If there are no errors, select Run. Otherwise, to remove the load, from the More menu, select Remove.
- If there are errors, manually update each record and select Update.
- When Data Synchronization is 100 percent, the changes are initiated.
Tip
If there are multiple errors, you can continue with errors and resolve them later. In TheAccessHub Admin Tool, use Support Interventions
Configure Azure AD B2C policies
If you occasionally sync TheAccessHub Admin Tool, it might not be up to date with Azure AD B2C. You can use TheAccessHub Admin Tool API and Azure AD B2C policies to inform TheAccessHub Admin Tool of changes. This solution requires technical knowledge of Azure AD B2C custom policies.
Create a secure credential to invoke TheAccessHub Admin Tool API
For your sign-up custom policies, the following steps enable a secure certificate to notify TheAccessHub Admin Tool of new accounts.
- To sign in to TheAccessHub Admin Tool, use the credentials N8ID provided.
- Go to System Admin > Admin Tools > API Security.
- Select Generate.
- Copy the Certificate Password.
- For the client certificate, select Download.
- Use the instruction in HTTPS client certificate authentication to add the client certificate to Azure AD B2C.
Retrieve your custom policy examples
- Use the credentials N8 Identity provided to sign in to TheAccessHub Admin Tool.
- Go to System Admin > Admin Tools > Azure B2C Policies.
- Supply your Azure AD B2C tenant domain and the two Identity Experience Framework IDs from your Identity Experience Framework configuration.
- Select Save.
- Select Download to get a .zip file with basic policies that add customers into TheAccessHub Admin Tool as customers sign up.
- To design custom policies in Azure AD B2C, use the instructions in Create user flows.