Enable vulnerability scanning
The Defender for Servers plan in Microsoft Defender for Cloud provides vulnerability scanning for protected machines.
Integrated vulnerability scanning in Defender for Cloud uses Microsoft Defender Vulnerability Management, and provides both agentless and agent-based scanning.
Vulnerability management is enabled by default when you enable Defender for Servers. Use the instructions in this article if you need to enable vulnerability scanning manually.
Prerequisites
| Requirement | Details |
|---|---|
| Agentless vulnerability scanning | Review agentless scanning requirements. Agentless vulnerability scanning is available and turned on by default when either Defender for Servers Plan 2 or the Defender for Servers Cloud Security Posture Management (CSPM) plan is enabled. |
| Agent-based vulnerability scanning | For agent-based vulnerability scanning Defender Servers Plan 1 or 2 must be enabled. |
| Machine support | Review supported machines. |
| Permissions | You need Owner (resource group level) permissions to deploy the scanner. You need Security Reader to view findings. |
Enable vulnerability scanning on a subscription
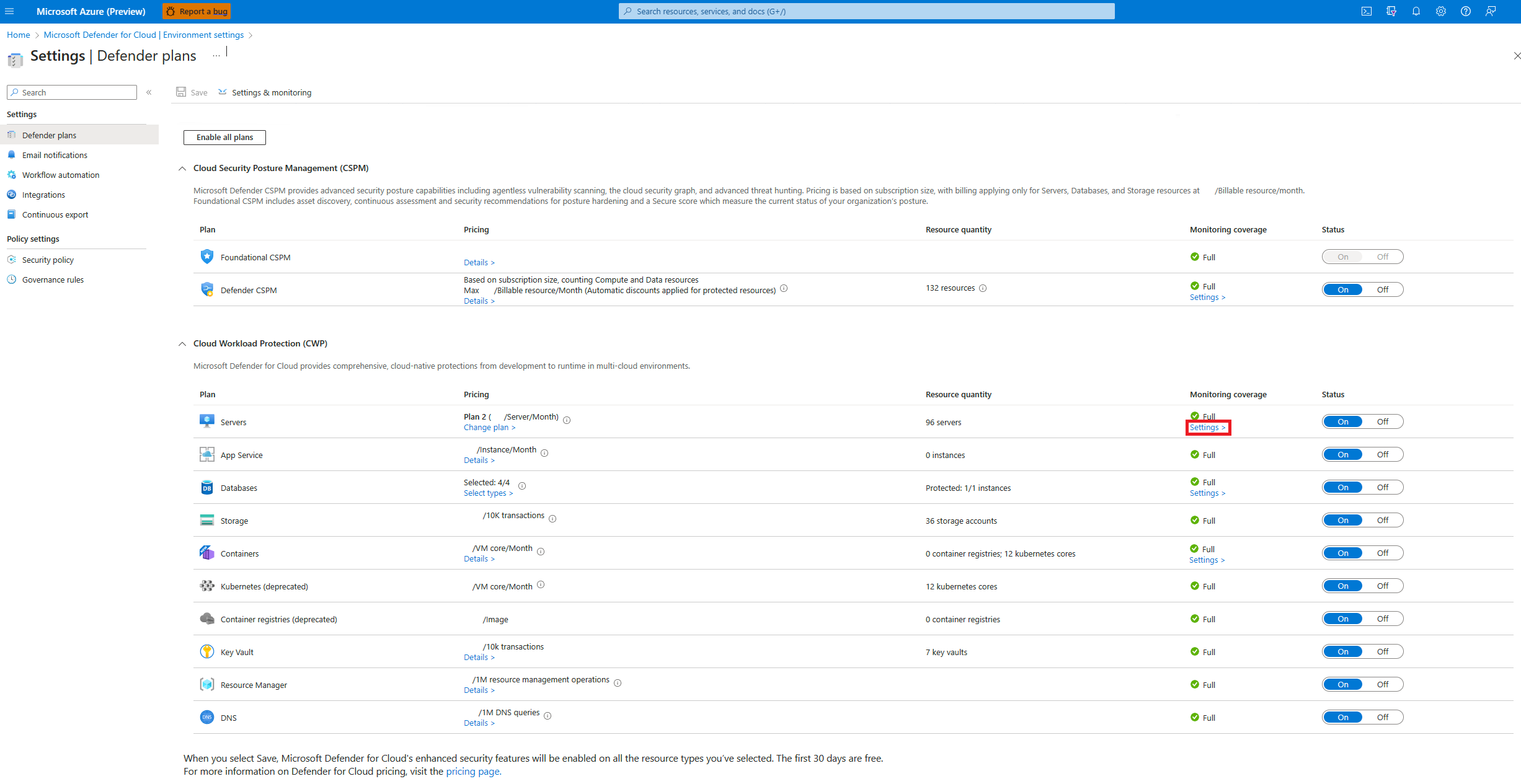
In Defender for Cloud, open Environment settings.
Select the relevant subscription.
In the Monitoring coverage column of the Defender for Servers plan, select Settings.
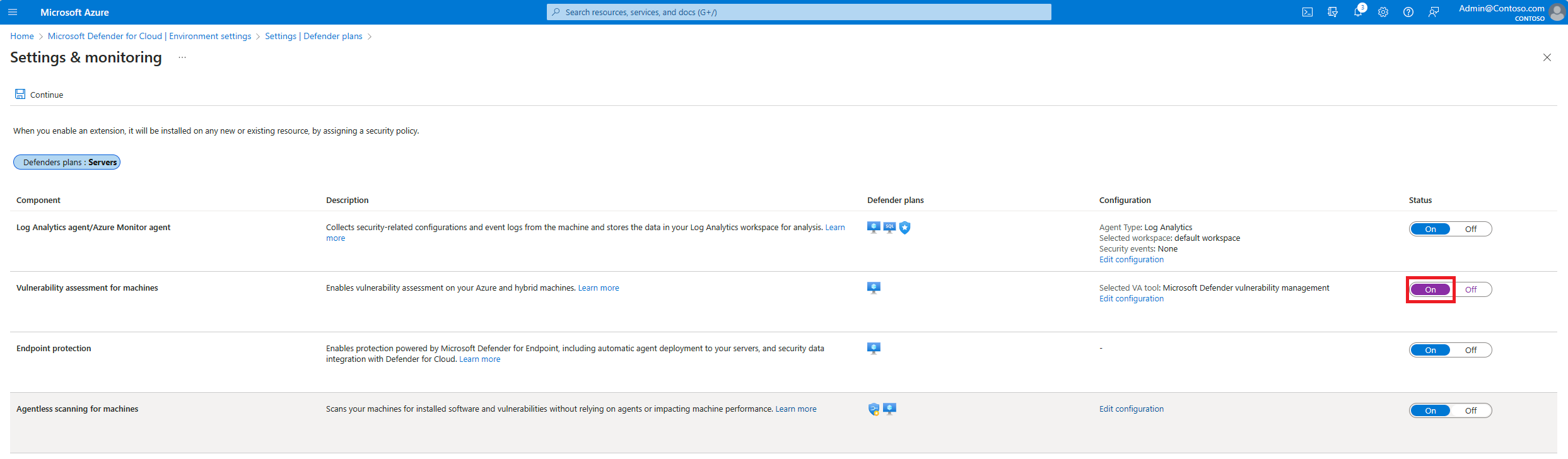
In Settings and monitoring, turn on Vulnerability assessment for machines as needed.
Select Edit configuration to select an assessment solution.
Select Apply > Save.
Configure with the REST API
To configure with the REST API, run PUT/DELETE using this URL:
https://management.azure.com/subscriptions/.../resourceGroups/.../providers/Microsoft.Compute/virtualMachines/.../providers/Microsoft.Security/serverVulnerabilityAssessments/mdetvm?api-version=2015-06-01-preview
Enable vulnerability scanning for a machine
To enable vulnerability scanning for a specific machine, use the recommendation that's issued if Defender for Servers doesn't find a vulnerability assessment solution installed on the machine.
To find all machines without a solution installed, in the Inventory page, select Unhealthy resources. Use the Recommendations filter to search for machines with this recommendation
Machines should have a vulnerability assessment solution.Open the recommendation.
Follow the recommendation remediation steps to fix machines that don't have a vulnerability assessment solution enabled.
Select a vulnerability solution.

After the process completes, it can take up to 24 hours until resources move to the Healthy resources tab.