Enhanced security and workflow efficiency
This sprint brings various improvements focused on boosting security and streamlining workflow efficiency. Among these improvements, the Service Connection Creation Experience in Azure Pipelines. This enables teams to set up service connections utilizing existing managed identities with workload identity federation. It also simplifies configuration and reduces the risk of over-privileged identities.
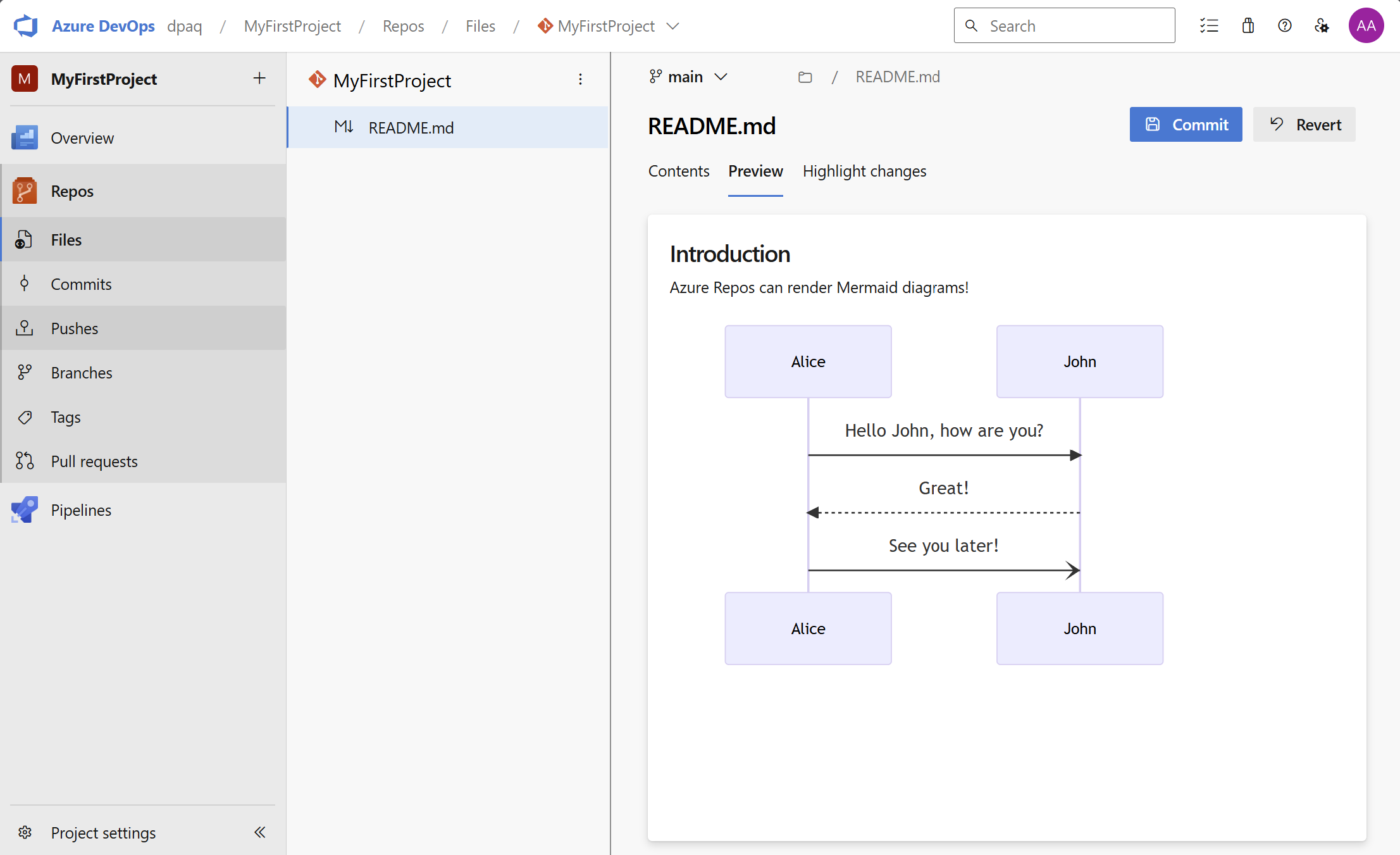
Additionally, we're excited to announce that in Azure Repos, markdown files with mermaid syntax will now render as diagrams in file previews and pull requests, providing clearer visuals for your documentation.
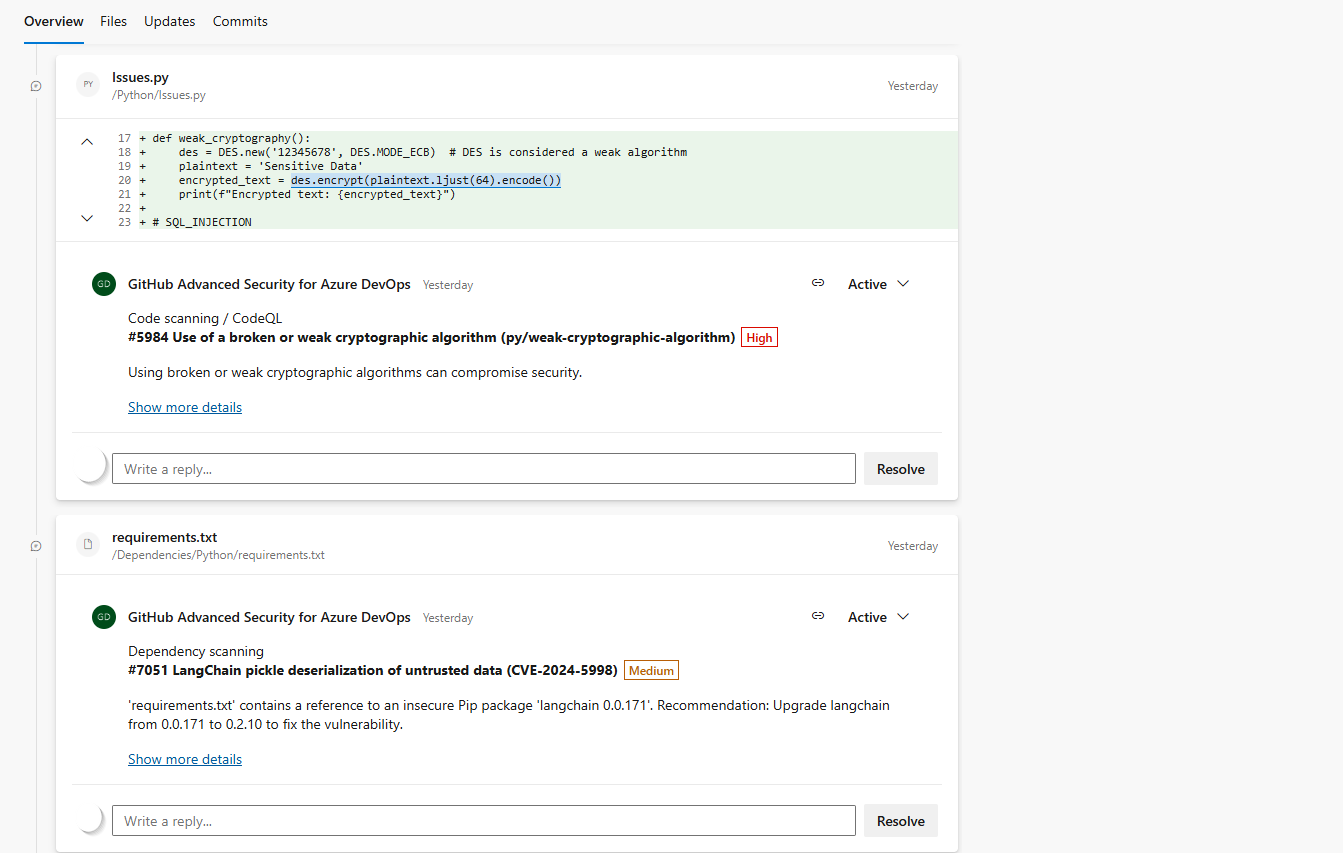
Lastly, in GitHub Advanced Security, pull request annotations now deliver in-line notifications for dependency and code scanning, simplifying the process for teams to detect and address potential problems during code reviews.
Check out the release notes for details.
General
GitHub Advanced Security for Azure DevOps
- Pull request annotations for dependency and code scanning
- New pip detection strategy for dependency scanning
Azure Boards:
- Enhanced tag management on work item form
- Improved image support in work item comments
- GitHub pull request insights
Azure Repos
Azure Pipelines
- Ubuntu 24.04 on Azure Pipelines hosted agents
- Use Workload identity federation in Azure integration tests
- New Azure service connection creation experience with improved Managed identity support
- Run children stages when parent stage fails
Azure Artifacts
Wiki
General
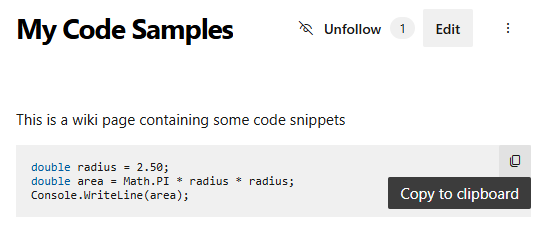
Copy code block to clipboard
In response to your feedback in the developer community, we’ve introduced a "Copy to clipboard" button for all code blocks in rendered markdown. This enhancement is available across Wiki pages, markdown file previews in Repos, pull request discussions and descriptions, and work item discussions.
Microsoft Entra profile information (preview)
We’re excited to introduce the integration of Microsoft Entra profile information in Azure DevOps, removing the need for separate profile updates. To try the preview, enable Microsoft Entra profile information in Preview Features.

Once enabled, your profile settings are read-only and automatically populated from Microsoft Entra. To revert to your previous settings or provide feedback, turn off the preview and share your comments.
GitHub Advanced Security for Azure DevOps
Pull request annotations for dependency and code scanning
As part of the Advanced Security roadmap, pull-request annotations are now available. You'll receive in-line annotations on any pull requests that use a pipeline associated with your build validation policy, which includes dependency and/or code scanning tasks.
No additional opt-in is required beyond creating a build validation policy for the relevant branches.
Clicking on Show more details in the annotation brings you to the alert detail view for the alert in question.
For more information, please see our latest blog post here
New pip detection strategy for dependency scanning
Dependency scanning now uses a new detection strategy for Python: PipReport, based on the pip installation report functionality. This update improves accuracy by respecting environment specifiers to determine the exact versions that a real pip install run would retrieve. By default, the detector uses pypi.org to build the dependency graph. Optionally, you can set a pipeline environment variable, PIP_INDEX_URL to construct the dependency graph instead. If there are authentication issues accessing your feed, you may need the PipAuthenticate@1 pipeline task set up so that your feed can be accessed.
For more information on detection strategy, see Pip Detection documentation.
Azure Boards
Enhanced tag management on work item form
Tag management in Azure Boards has been enhanced to provide a more streamlined experience. Deleted tags no longer appear in the suggested list on work item forms, ensuring that only active tags are displayed.
Improved image support in work item comments
We’ve improved our support for pasting images into work item comments. You can now paste images directly from sources like Microsoft Teams, emails, and Word documents into the discussion section of a work item
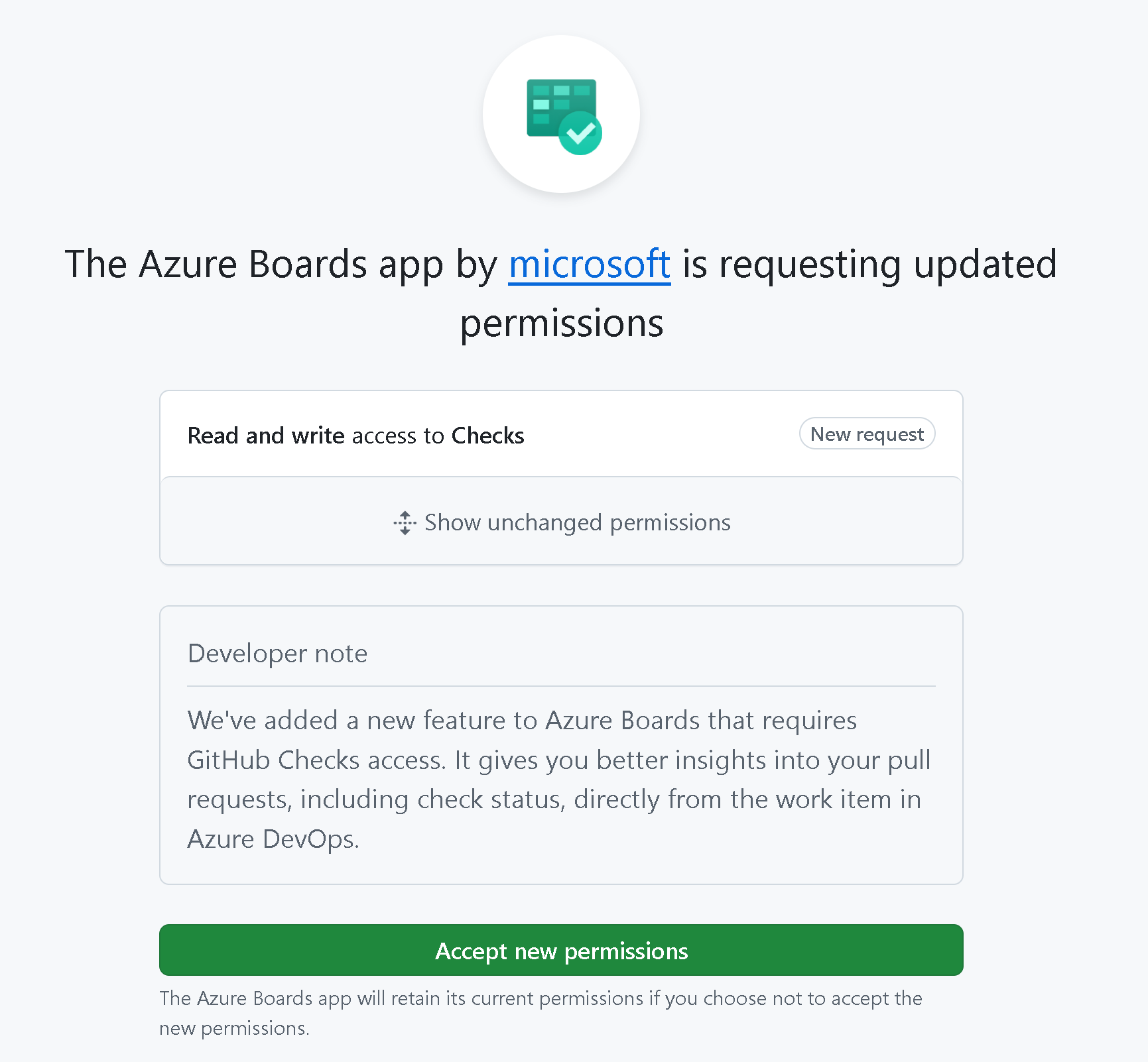
GitHub pull request insights
We've enhanced the integration between GitHub pull requests and Azure Boards. In addition to showing open and closed statuses, you can now see if a pull request is in draft mode, needs review, and Checks status. All without needing to open the pull request.
To enable this feature, make sure you go the Boards App in GitHub to accept the requested updated permissions for read and write access to Checks.
Azure Repos
Configure target branches for pull requests
Managing multiple branches in a repository can be challenging, especially when creating new pull requests. With the new Configure Target Branches for Pull Requests feature, you can now specify a list of preferred target branches, ensuring that pull request suggestions are more accurate and relevant. This helps streamline your workflow and reduces the chances of targeting the wrong branch.
To use this feature, create a .azuredevops/pull_request_targets.yml file in your repository's default branch. This YAML file should contain a list titled pull_request_targets with the branch names or prefixes that match the candidate branches. For example:
pull_request_targets:
- main
- release/*
- feature/*
In this configuration, the main branch is prioritized, but branches starting with release/ or feature/ will also be considered when appropriate. The configuration is applied in the following scenarios:
- Pull Request Suggestions: After pushing a branch to Azure DevOps, the Repos page may suggest creating a pull request from that branch, dynamically choosing the target branch.
- Pull Request URL: When navigating directly to the pull request creation page using a sourceRef parameter but omitting the targetRef parameter, Azure DevOps selects a target branch based on this dynamic choice.
It’s recommended to include only branches protected by pull request policies to ensure consistency in the first-parent history of the tip commit.
Support mermaid diagrams in markdown file preview
Markdown files containing mermaid syntax will now render as diagrams inside file previews in repos file browser and in pull requests. This can help you add richer documentation to your repositories.
Azure Pipelines
Ubuntu 24.04 on Azure Pipelines hosted agents
The Ubuntu 24.04 image is now available for Azure Pipelines hosted agents. To use this image, update your YAML file to include vmImage:'ubuntu-24.04':
- job: ubuntu2404
pool:
vmImage: 'ubuntu-24.04'
steps:
- bash: |
echo Hello from Ubuntu 24.04
lsb_release -d
Note
The ubuntu-latest image label will continue to point to ubuntu-22.04 until later this year.
See the Ubuntu 24.04 image readme for installed software.
Use Workload identity federation in Azure integration tests
In June, the Azure Identity libraries for.NET, C++, Go, Java, JavaScript, and Python added support for workload identity federation. This added the ability for code executed from the AzureCLI@2 and AzurePowerShell@5 tasks to authenticate with Microsoft Entra (for example, to access Azure) with the AzurePipelinesCredential class.
Many customers are using the Azure Identity libraries in integration tests invoked from other tasks. We've now added support for AzurePipelinesCredential to the DotNetCoreCLI@2, Maven@4 and VSTest@3 tasks.
You can set the connectedService property to an Azure service connection configured with workload identity federation. The AzurePipelinesCredential requires SYSTEM_ACCESSTOKEN to be set.
- task: DotNetCoreCLI@2
inputs:
command: 'run'
connectedService: <Azure service connection configured with workload identity federation>
env:
SYSTEM_ACCESSTOKEN: $(System.AccessToken)
For more information on AzurePipelinesCredential, see this blog post.
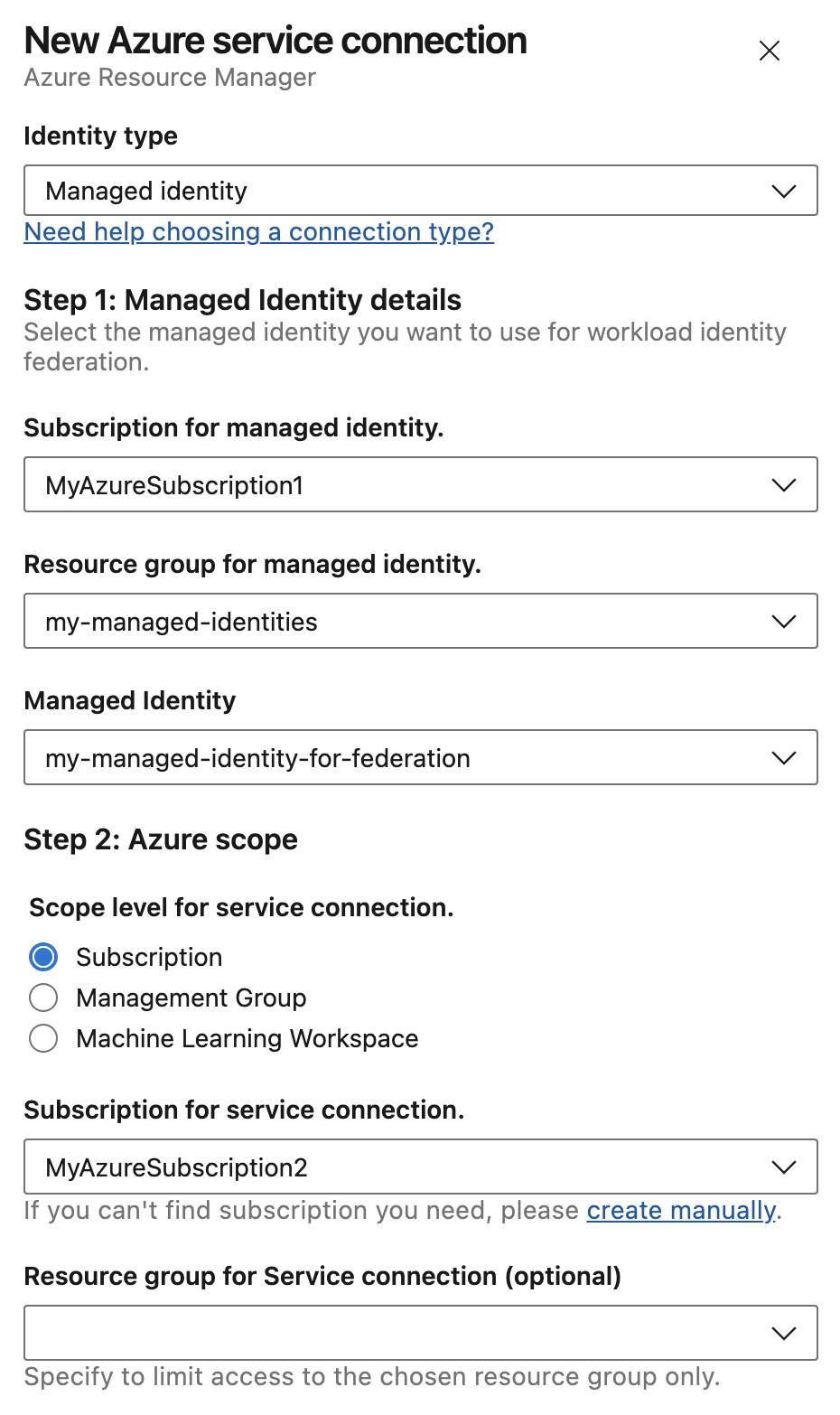
New Azure service connection creation experience with improved Managed identity support
The new Azure service connection creation experience provides increased flexibility and secure defaults. It also aligns terminology with Microsoft Entra ID, so that users who create Microsoft Entra ID objects manually have a better understanding when navigating different portals.
When creating a new Azure Resource Manager service connection, the various options to configure identity are now available in a single unified dialog that replaces the distinct top level items used previously:
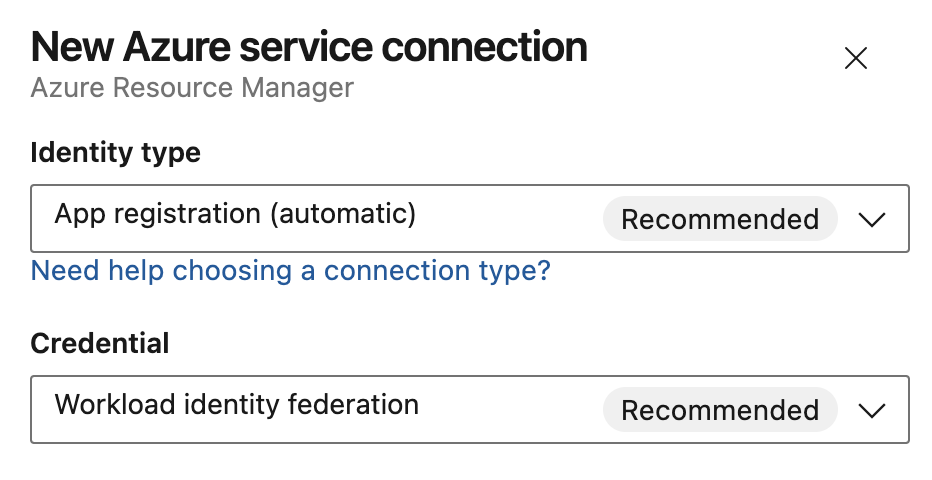
Identity type lists all authentication schemes the Azure service connection supports:
For app registrations, you can independently select Credential to be workload identity federation or a secret.
Azure Service Connection Managed Identity support
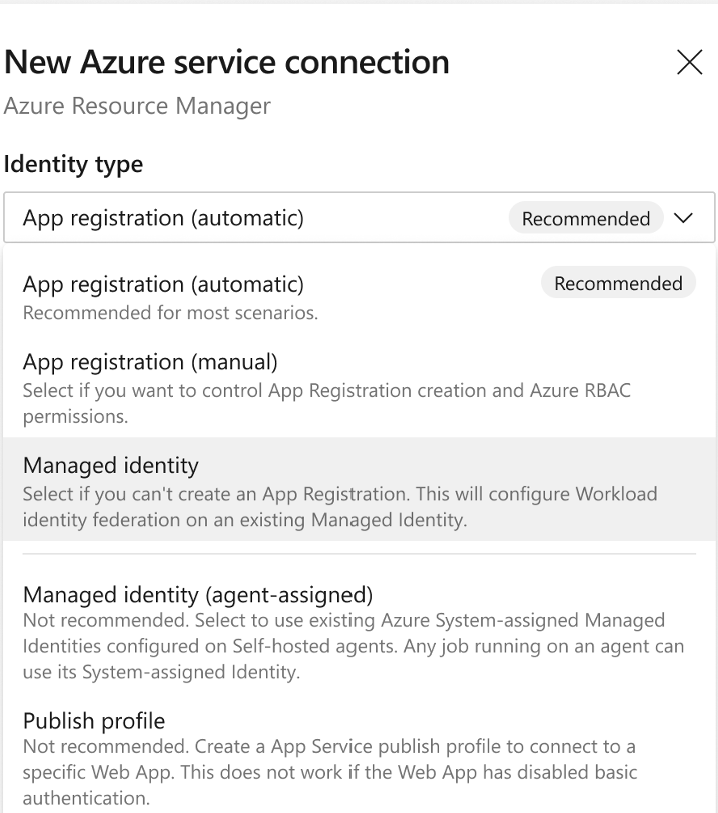
You can now select a pre-existing managed identity and use it to configure a service connection that uses workload identity federation. First, create a User-assigned Managed Identity.
Then, create an Azure service connection and select the Managed identity Identity Type. This configures federated identity credentials on the managed identity.
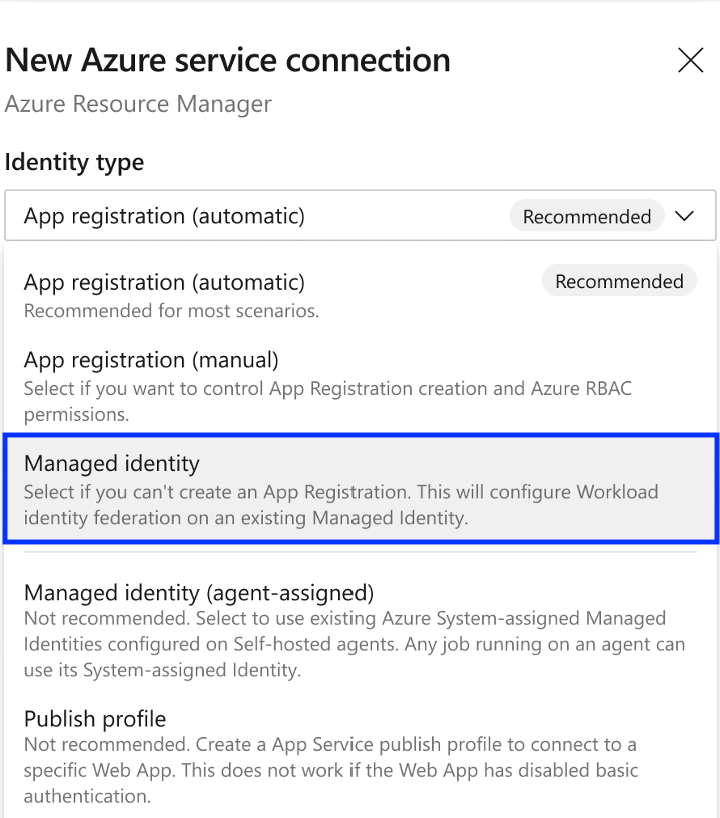
The option to use a managed identity assigned to an agent (pool) has been renamed Managed identity (agent-assigned). To prevent sharing over-privileged managed identities, it's recommended to use a managed identity with workload identity federation instead of managed identities assigned to agent pools.
Managed identity is also the recommended option for users who can't create an App registration if that is disabled in Microsoft Entra ID.
To use a managed identity with workload identity federation, first select the subscription and resource group that holds your managed identity. This can be different from the subscription the service connection accesses in pipeline jobs. Pick the managed identity that is configured for workload identity federation. The user needs the Managed Identity Contributor role or equivalent permissions on the managed identity to create federated identity credentials on it.
Continue to select the subscription that will be used as the deployment scope for the service connection.
Service Management Reference field
Some organizations require the Service Management Reference of an App registration to be populated with relevant context information from an ITSM database. If necessary to do so, users can specify this reference at service connection creation time.
More information
The new Azure service connection creation experience is rolling out over the next month. For more information, see:
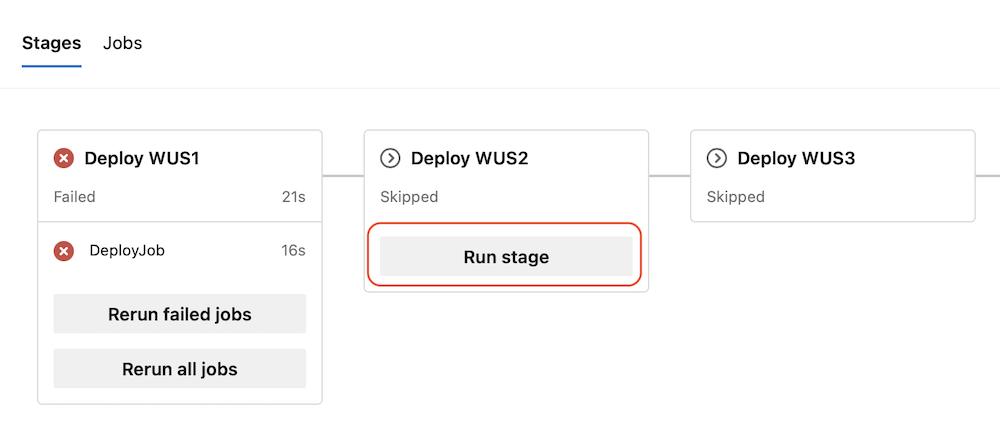
Run children stages when parent stage fails
We made it easier to continue deployments using Azure Pipelines. This is useful, for example, when you use Pipelines to deploy new versions of your application across multiple Azure regions.
Say you need to deploy to five consecutive Azure regions. Assume your pipeline has a stage for each region, and each stage has a job that runs an AzureResourceManagerTemplateDeployment task, and then it logs some telemetry. The latter is nice to have, but not critical. Imagine there's an issue logging the telemetry. Now, the stage fails and the deployment stops.
Starting with this sprint, when a stage fails, you can resume running its children stages.
Azure Artifacts
Authentication to Azure Artifacts using a public feed and Cargo
Due to a limitation with the Cargo client, authentication was all-or-nothing. For private feeds, authentication would be sent, but for public feeds, which need to allow for anonymous users, no authentication would be sent, even if it was available or needed.
Now, authenticated users can connect to a public Azure Artifacts feed, just as they would a private feed. If you or your pipeline agent have permission to save packages from upstream sources, you can access packages from crates.io through the feed. This change gives control of what packages can come into a feed back in the hands of feed administrators. Once packages are brought into the feed from an upstream source, anonymous users will have access to them.
To ensure authentication, append ~force-auth to the feed name in your registry URL. You can find out more details through our public documentation.
Wiki
Improve pasting of HTML based content into Wikis
We’ve made it easier to paste HTML-based content into Wikis. Now, HTML elements like links, lists, tables, images, Excel sheets, Microsoft Teams messages, emails, and Azure Data Explorer queries are automatically converted to Markdown syntax for smoother editing.
Next steps
Note
These features will roll out over the next two to three weeks.
Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.
Thanks,
Dan Hellem