Use Git Credential Manager to authenticate to Azure Repos
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
Visual Studio 2019 | Visual Studio 2022
Git Credential Manager simplifies authentication with your Azure Repos Git repositories. Credential managers let you use the same credentials that you use for the Azure DevOps Services web portal. Credential managers support multifactor authentication through Microsoft account or Microsoft Entra ID. Besides supporting multifactor authentication with Azure Repos, credential managers also support two-factor authentication with GitHub repositories.
Azure Repos provides IDE support for Microsoft account and Microsoft Entra authentication through the following clients:
If your environment doesn't have an integration available, configure your IDE with a Personal Access Token or SSH to connect to your repositories.
Install Git Credential Manager
Windows
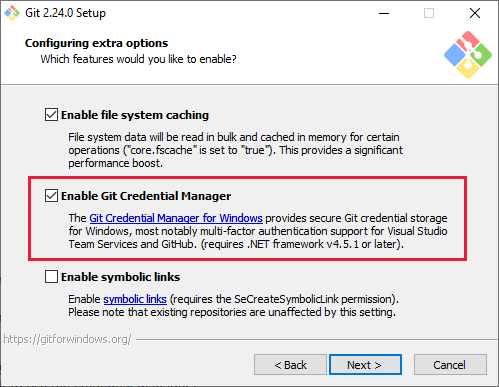
Download and run the latest Git for Windows installer, which includes Git Credential Manager. Make sure to enable the Git Credential Manager installation option.
macOS and Linux
You may use SSH keys to authenticate to Azure Repos, or you may use Git Credential Manager.
Installation instructions are included in the GitHub repository for GCM. On Mac, we recommend using Homebrew. On Linux, you can install from a .deb or a tarball.
Using the Git Credential Manager
When you connect to a Git repository from your Git client for the first time, the credential manager prompts for credentials. Provide your Microsoft account or Microsoft Entra credentials. If your account has multi-factor authentication enabled, the credential manager prompts you to go through that process as well.
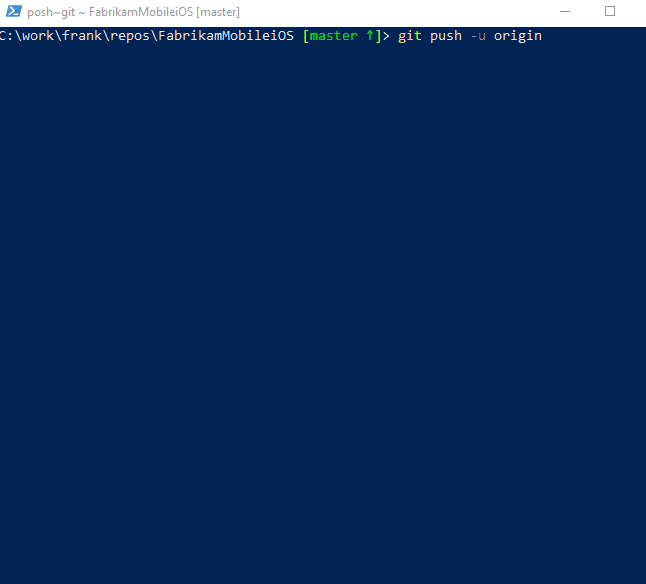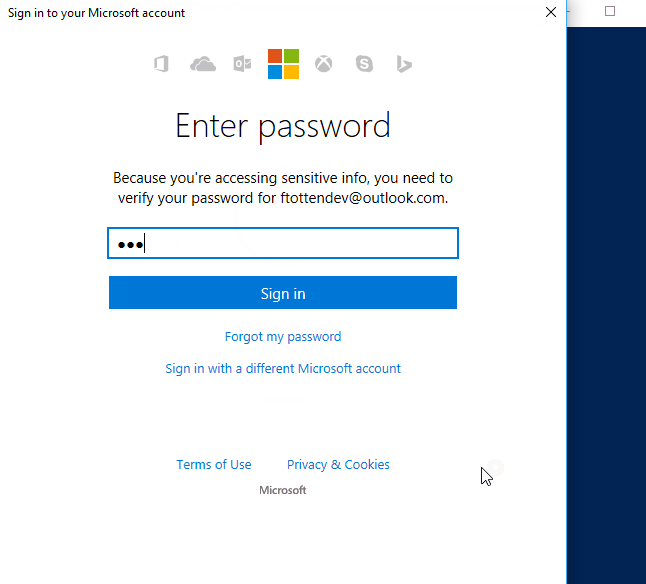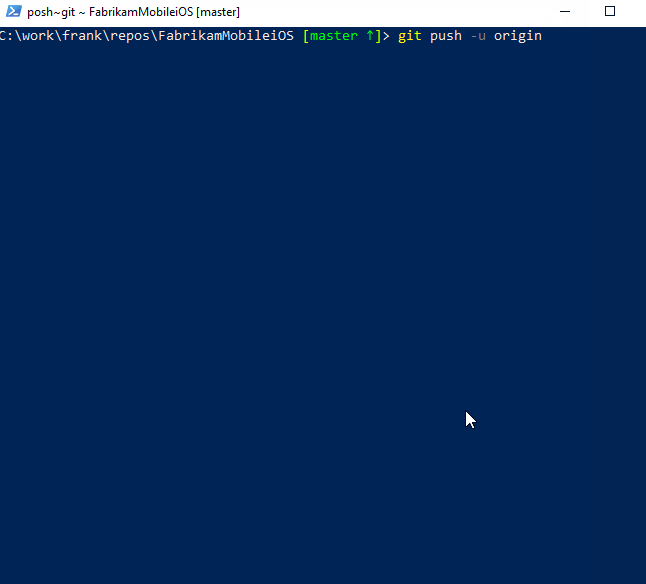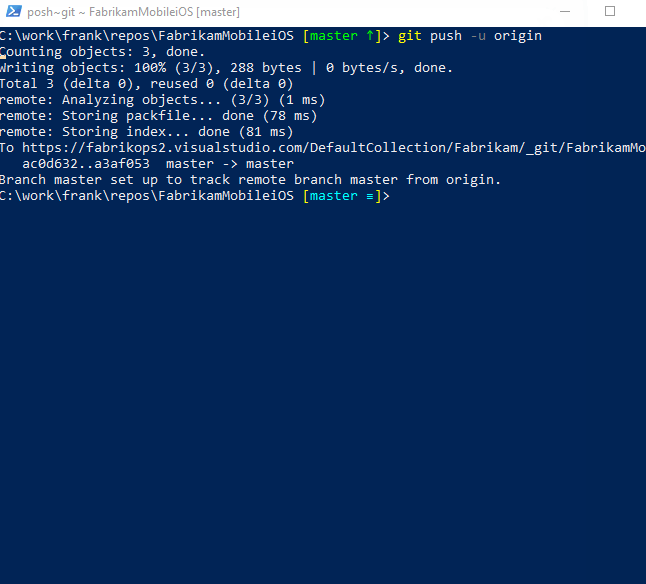
Once authenticated, the credential manager creates and caches a token for future connections to the repo. Git commands that connect to this account won't prompt for user credentials until the token expires. A token can be revoked through Azure Repos.
Set default credential type as OAuth
By default, GCM will request a personal access token from Azure Repos. However, you can change the default token type to a Microsoft Entra token for Git authentication instead. We recommend this approach since the latter token has a one-hour expiration compared to the 7-day PATs minted by GCM. All PATs created by GCM can be revoked in the User Settings page.
To set your default credential type to Microsoft Entra tokens, set the credential.azreposCredentialType configuration entry (or GCM_AZREPOS_CREDENTIALTYPE environment variable) to oauth. Learn more about using GCM with Azure Repos.
Use service principal as authentication
You can also provide a service principal for authentication with GCM. Specify the client and tenant IDs of a service principal in this format: {tenantId}/{clientId}.
git config --global credential.azreposServicePrincipal "11111111-1111-1111-1111-111111111111/22222222-2222-2222-2222-222222222222"
You must also set at least one authentication mechanism if you set this value:
- credential.azreposServicePrincipalSecret
- credential.azreposServicePrincipalCertificateThumbprint
- credential.azreposServicePrincipalCertificateSendX5C
Getting help
You can open and report issues with Git Credential Manager on the project GitHub.