Configure multiple authentications in a single instance
Many organizations might want to support multiple authentication options to be available for their learners. Microsoft Community Training now supports adding more than one authentication option for a single platform instance.
To be able to configure multiple authentications to your instance you need to first create AD B2C tenant and register an application. If your instance is already setup to use social login via ADB2C then you can proceed configuring your tenant to add phone login and work email login support to your instance.
Note
We would strongly recommend that an MFA (Multi Factor Authentication) or a 2FA (2 Factor Authentication) be implemented, if your instance is using ADB2C based authentication, especially for the Admin accounts.
Add Phone-based login to existing Social Account login Instance
If your instance is already setup to accept social login via AD B2C, below are the steps to configure your AD B2C tenant to be able to support MCT platform's Phone authentication along side your social account login.
Prerequisites
Create a MCT support ticket requesting for creation of new ClientID and ClientSecret in your Key-Vault to be used while configuring New OpenID connect provider.
Also mention your AD B2C Tenant name in description while creating support ticket.
After receiving confirmation (typical wait time is around 2 business days) from our support team you can proceed to next steps adding phone based login.
Steps to support Phone Auth along side your social account Login
Login to your Azure portal
Switch to the directory which contains your ADB2C Tenant.
In search bar type ‘Azure ADB2C’ and Navigate to your application from ‘App Registration’.
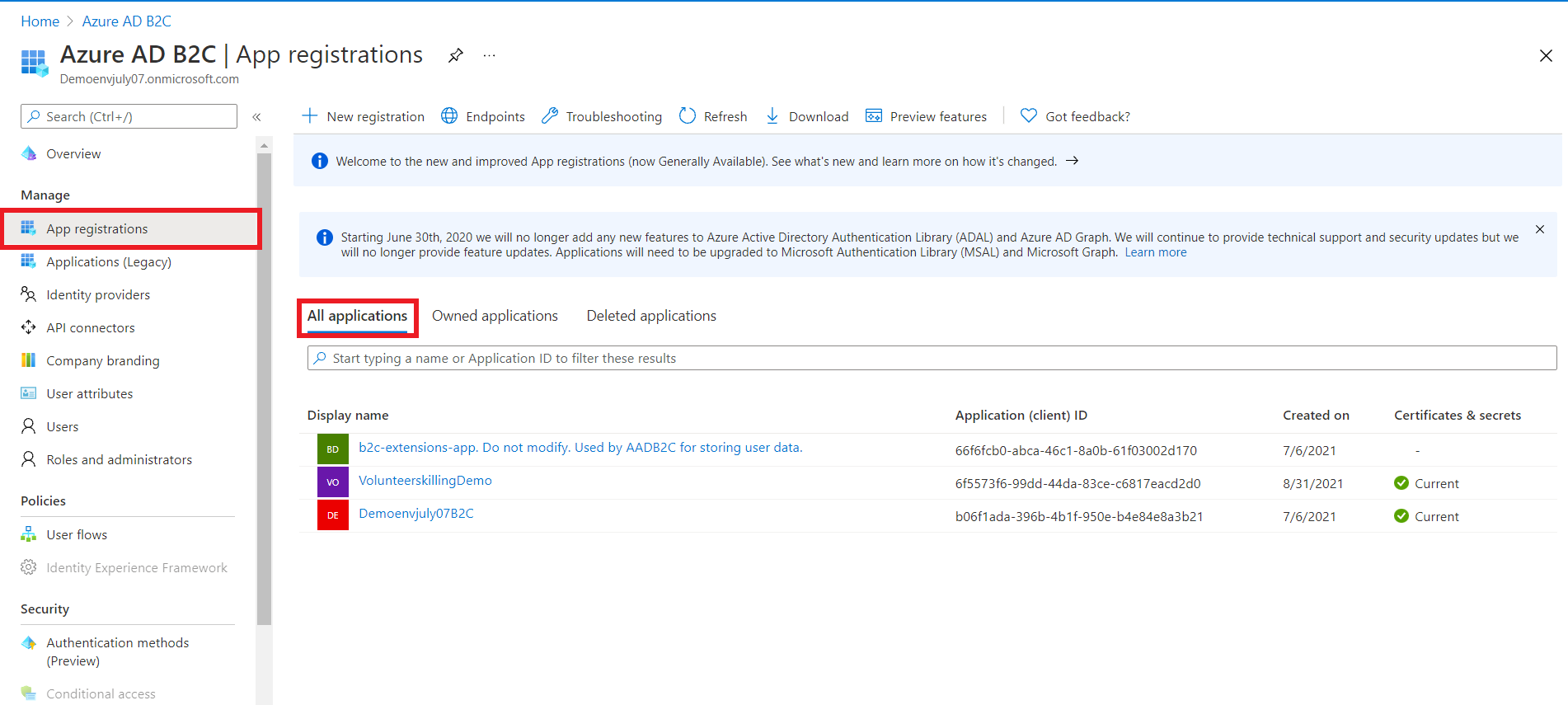
Inside your application, navigate to ‘Authentication’ and make sure you have “Access tokens (used for implicit flows)” checked under Implicit grant and hybrid flows.
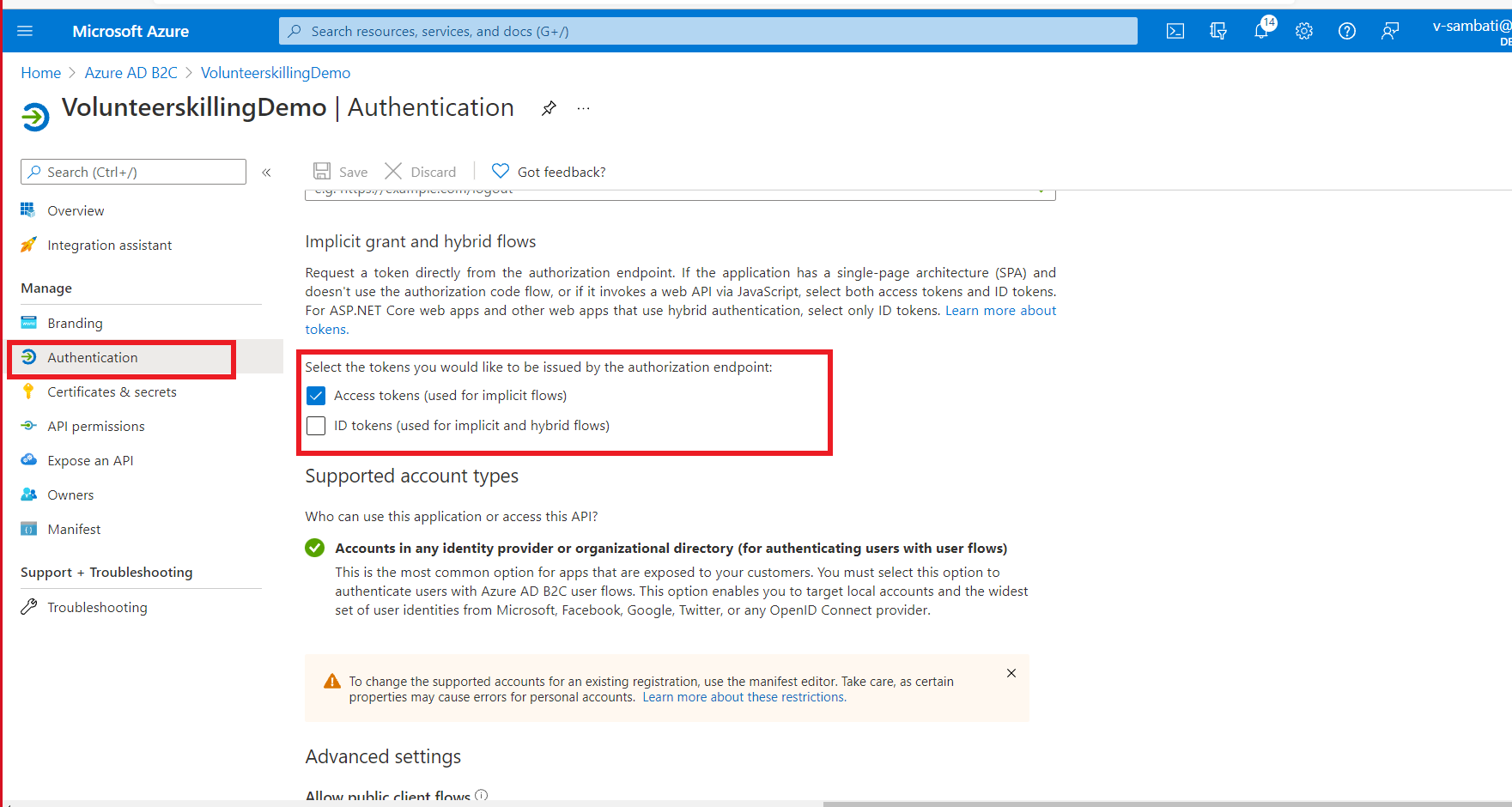
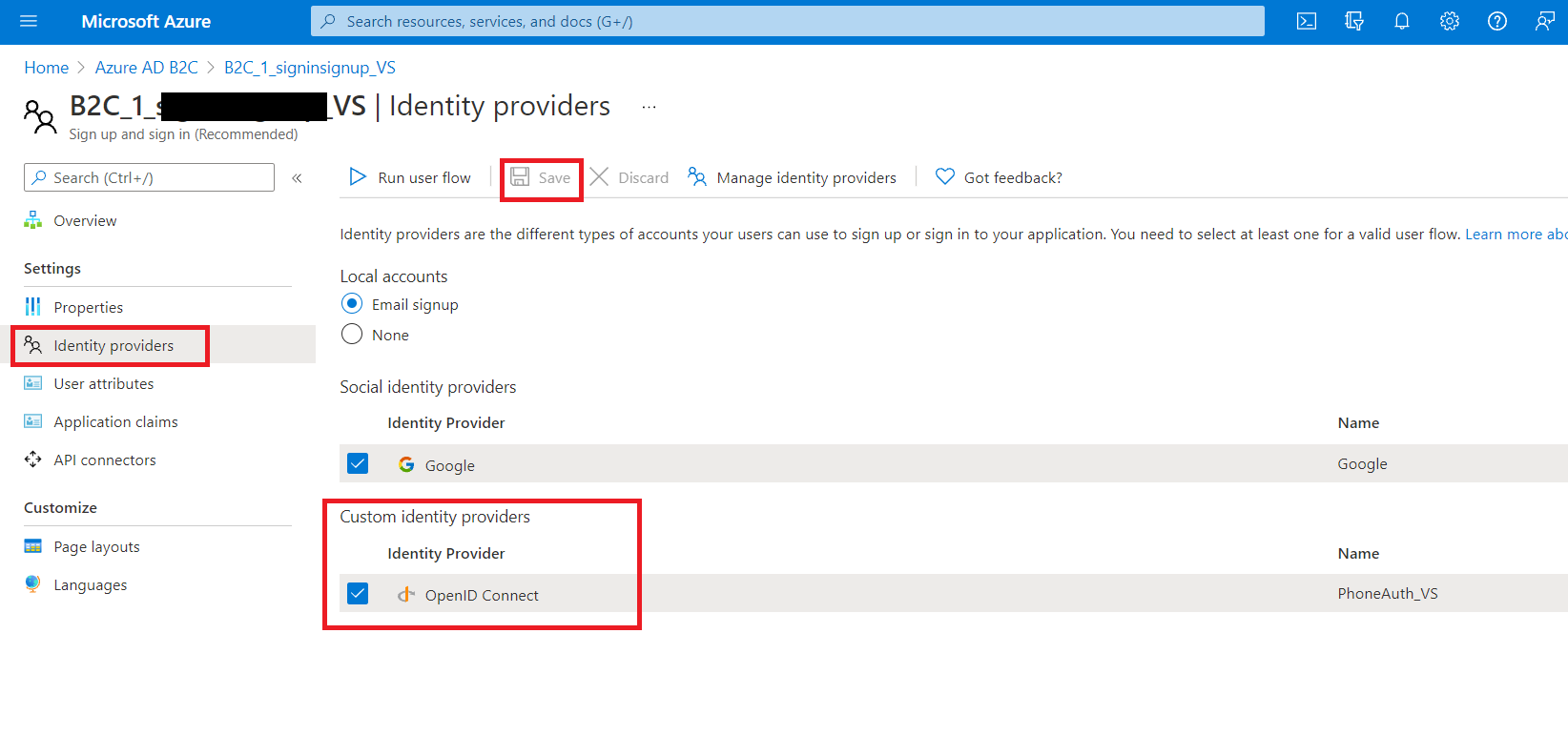
Navigate back to your ADB2C resource, under Manage section, in ‘Identity Providers’ click on ‘New Open ID Connect Provider’ and provide following values in Configure custom IDP window and click save.
Value Description Name This name will appear in login page, provide user friendly name, example: Phone Auth Metadata URL https://phoneverification.azurefd.net/.well-known/openid-configurationClient ID Copy ‘PhoneExternalAuthClientID’ value from Key-Vault and paste it here. Client Secret Copy ‘PhoneExternalAuthClientSecret’ value from Key-Vault and paste it here Scope Enter openid offline_accessResponse Type From dropdown select codeResponse mode From dropdown select form_postDomain hint Optional, leave blank User ID Enter subDisplay Name Enter subGiven Name Enter given_nameSurname Enter family_nameEmail Enter email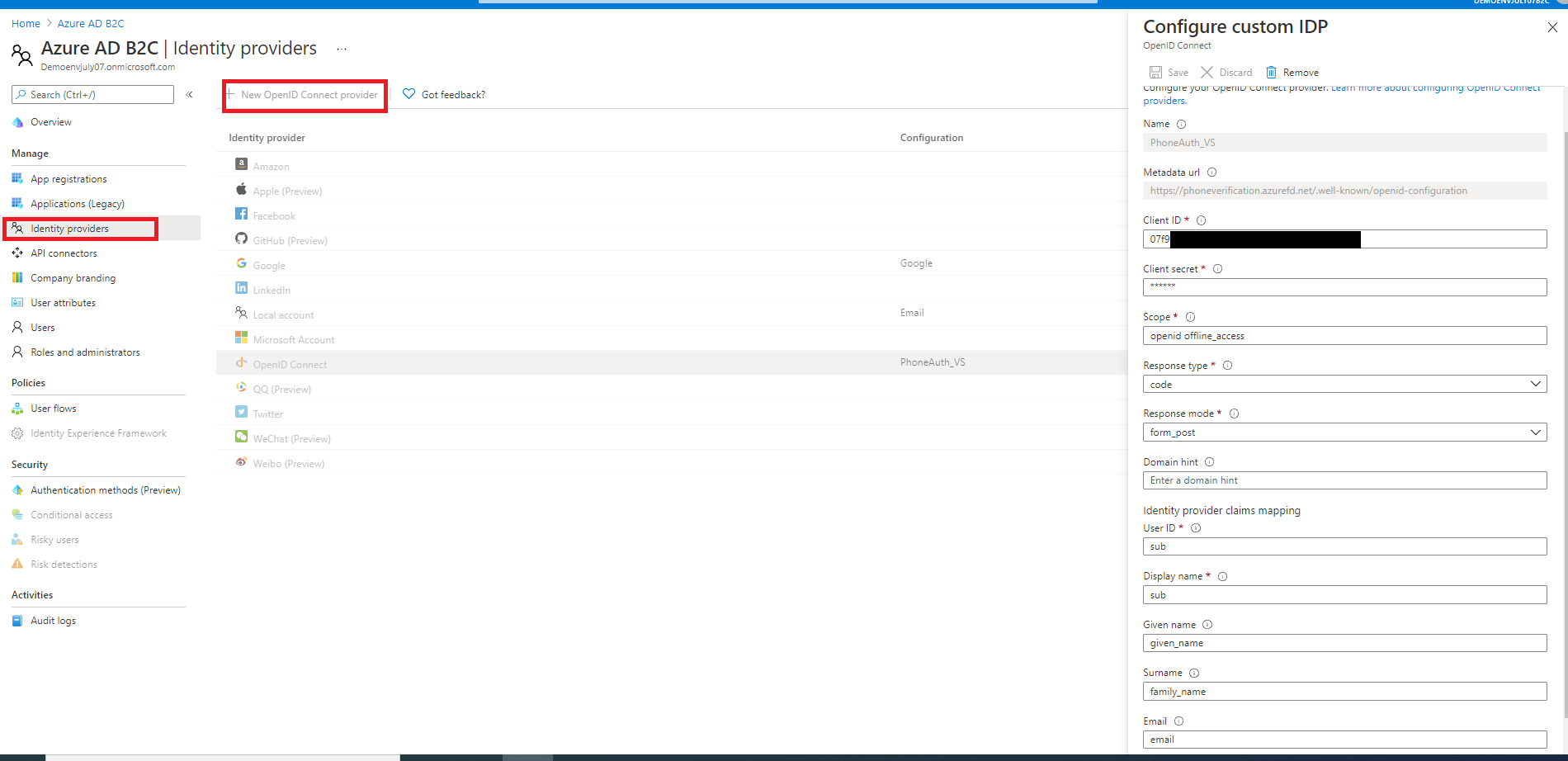
Navigate back to your ADB2C resource, under Policies, click on User Flows and click on your instance's “Sign up and Sign in” User flow.
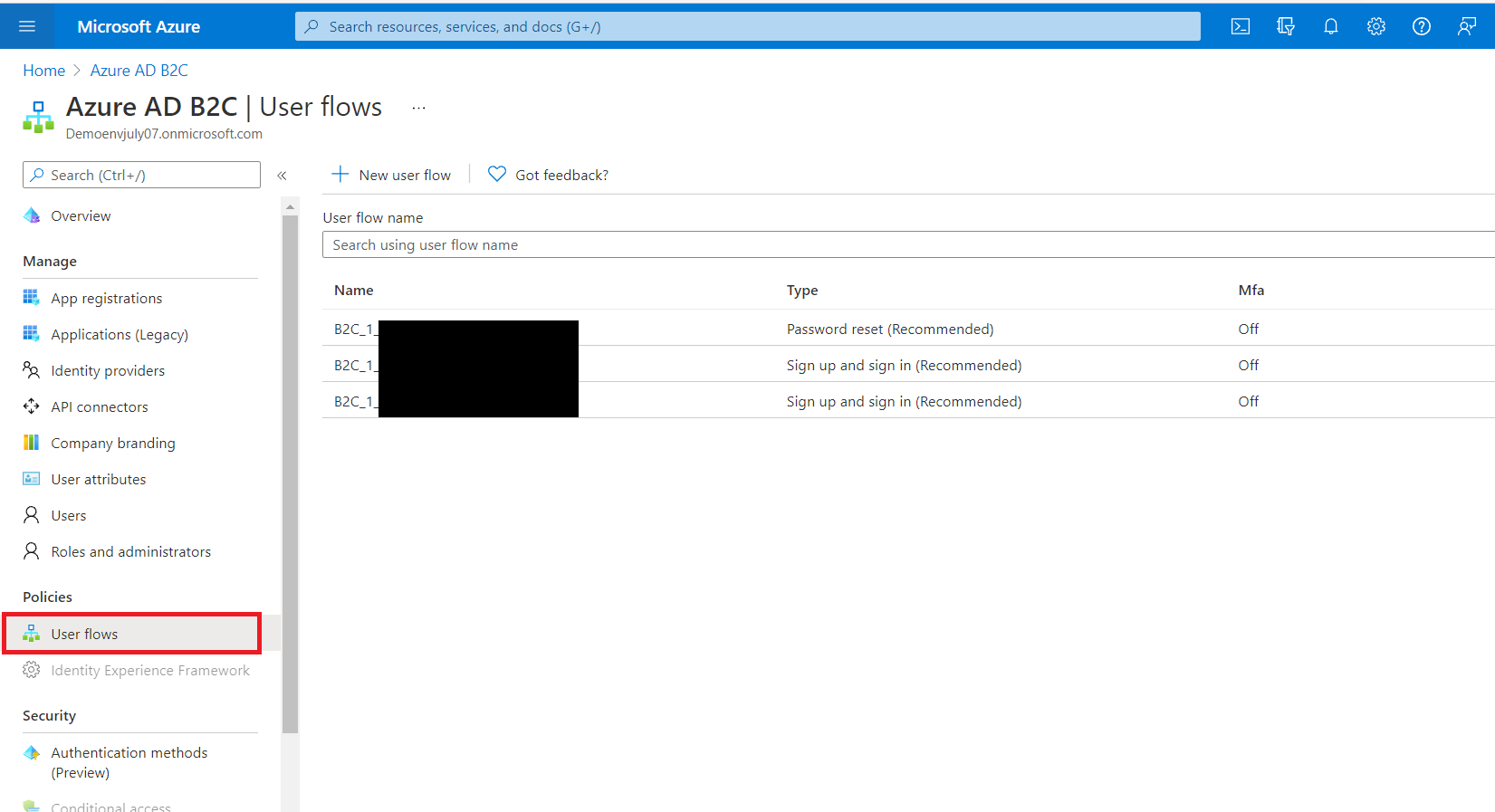
Inside your instance’s Sign-up and Sign-in user flow, click on ‘Application Claims’ and ensure you have ‘Display Name’, ‘Email Address’, ‘User’s Object ID’ selected and saved.
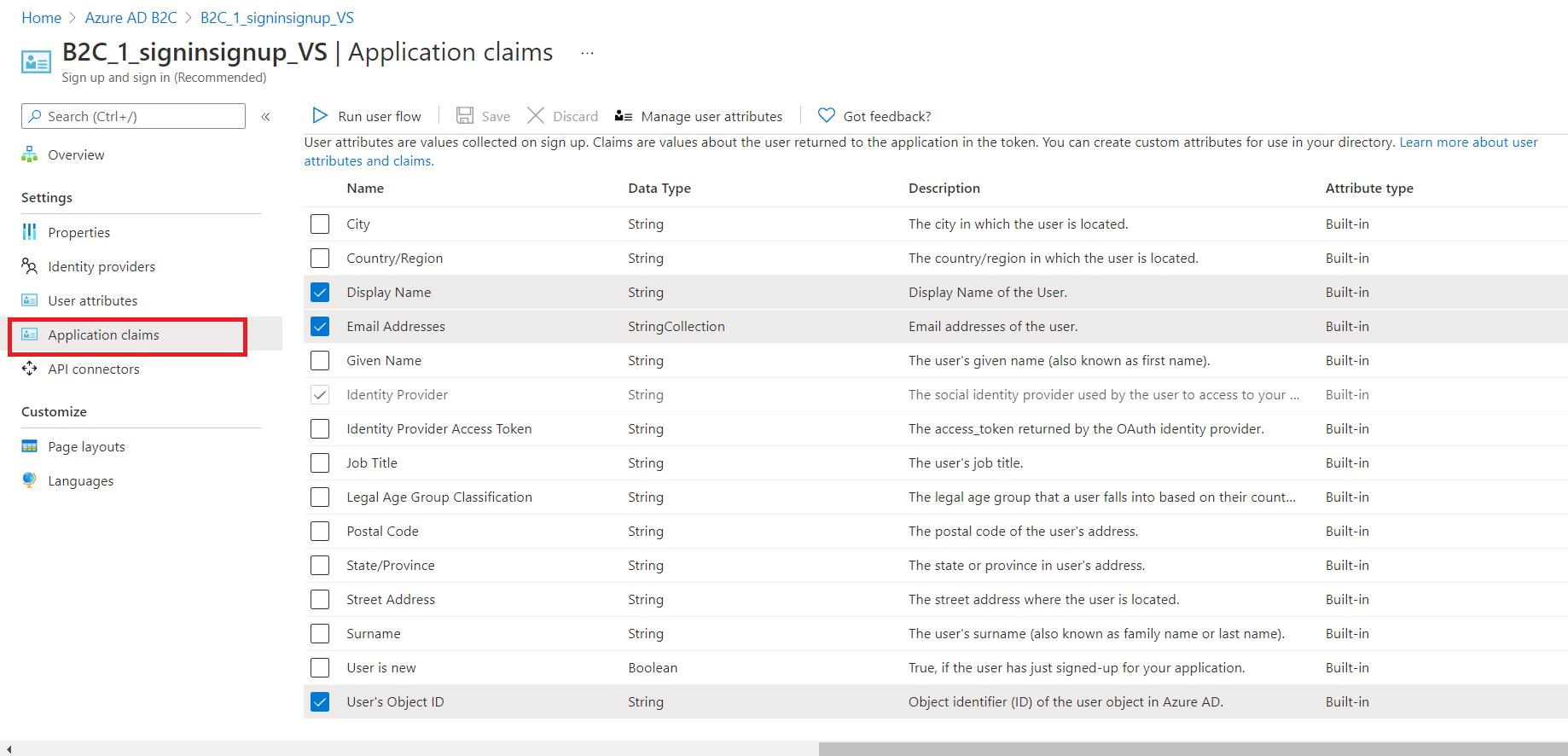
While in your Sign-up Sign-in user flow, navigate to ‘Identity Providers’ and select on newly configured OpenID Connect under Custom Identity Providers and click save.
Now in the login page of your instance, you should see an option that enables users to login through their Phone number alongside option to login via social account. Users can now choose any one of the login methods for registering.
Add Work email based Authentication to existing Social Account login instance
If your instance is already setup to accept social login via AD B2C, below are the steps to add Azure Active Directory/Work email based authentication along side social account login by configuring your existing Azure ADB2C tenant.
Login to your Azure portal
Note down your AD B2C tenant’s name i.e., for example, if the default domain for your Azure AD B2C tenant is contoso.onmicrosoft.com, then contoso is your tenant’s name.
Create an Azure Active Directory App (can be from different tenant) configure login identity for the platform by creating Azure AD application, copy your Client ID, Client Secret and Tenant ID.
While in your AAD app, Click on ‘Authentication’ to add your Reply URL
https://<adb2c_tenant_name>.b2clogin.com/<adb2c_tenant_name>.onmicrosoft.com/oauth2/authrespreplace <adb2c_tenant_name> with your AD B2C tenant name from Step 2.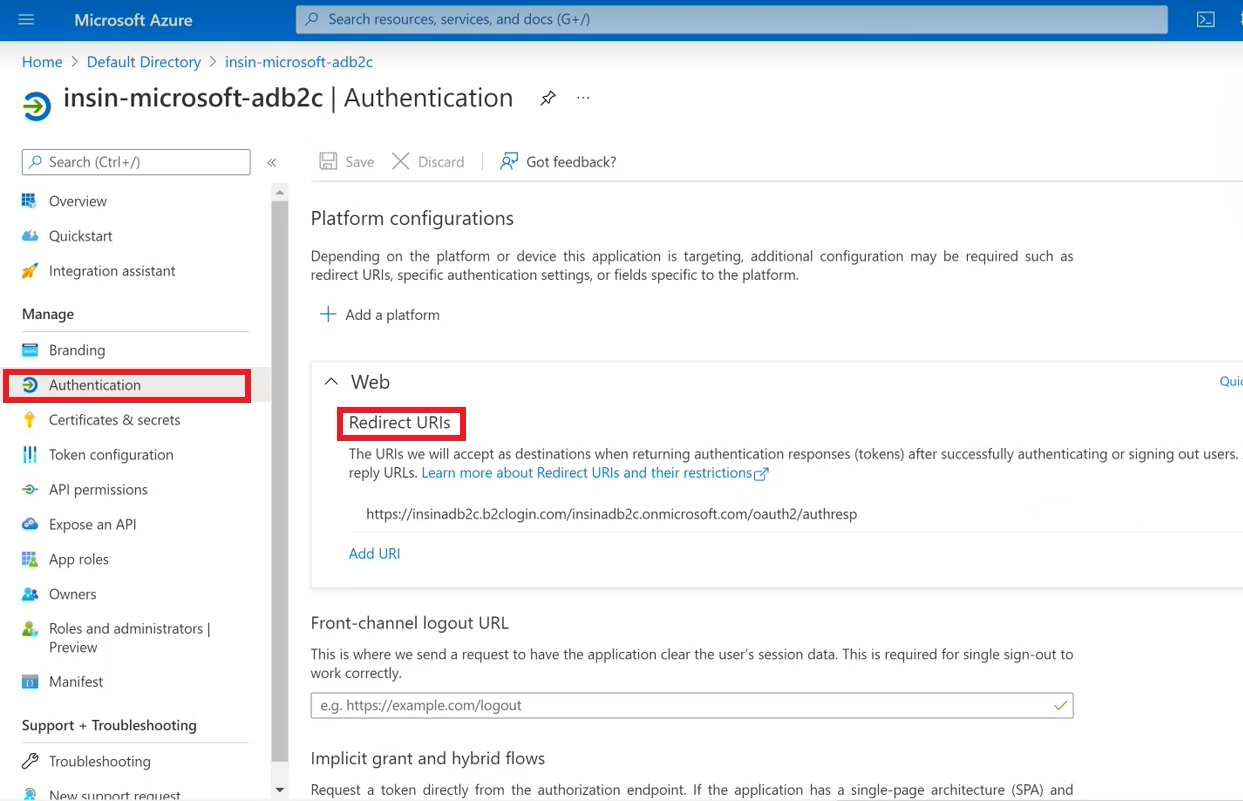
Now switch to your AD B2C tenant, under Manage section, in ‘Identity Providers’ click on ‘New Open ID Connect Provider’ and provide following values in Configure custom IDP window and click save.
Value Description Name This name will appear in UI on login page, provide user friendly name example: Active Directory Login Metadata URL https://login.microsoftonline.com/<tenant_id>/v2.0/.well-known/openid-configurationReplace <tenant_id> with Tenant ID of AAD from Step3 (for AAD application)Client ID Paste the ClientId that you copied from Step3 (for AAD application) Client Secret Paste the ClientSecret that you copied from Step3 (for AAD application) Scope Enter email openid profile User.ReadResponse Type From dropdown select codeResponse mode From dropdown select form_postDomain hint Optional, leave blank. User ID Enter subDisplay Name Enter nameGiven Name Enter given_nameSurname Enter family_nameEmail Enter email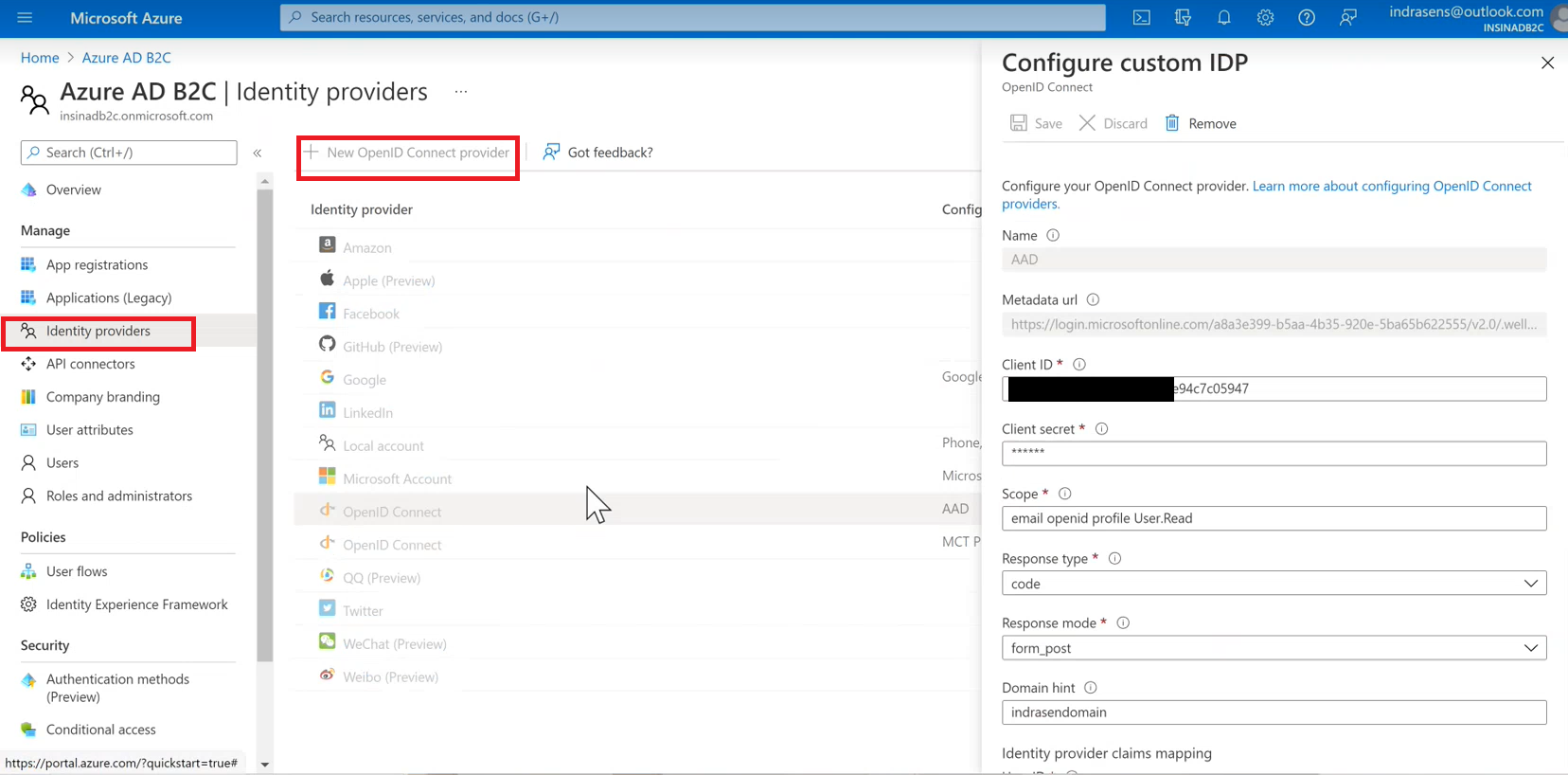
Navigate back to your ADB2C resource, under Policies, click on User Flows and click on your instance's “Sign up and Sign in” User flow.

Inside your instance’s Sign-up and Sign-in user flow, click on ‘Application Claims’ and ensure you have ‘Display Name’, ‘Email Address’, ‘User’s Object ID’ selected and saved.

While in your Sign-up Sign-in user flow, navigate to ‘Identity Providers’ and select on newly configured OpenID Connect under Custom Identity Providers and click save.

Now in the login page of your instance, you should see an option that enables users to login through their work email (Azure AD email) alongside Social Account login.
Add Work/Social Account login to Phone-based login instance
As multiple modes of authentication in MCT can only be achieved via AD B2C, you need to first create an Azure AD B2C tenant to support social login and then configure your B2C tenant to support MCT's phone authentication and work email login. Below are the detailed steps
Configure login identity for the platform by creating an Azure AD B2C tenant. In the document skip point 7 in Step2 as you are not deploying new instance, proceed to Step3 if you need to add local account login support to your instance.
Copy and note ClientID, ClientSecret, TenantName, sign-up and sign-in user flow name while configuring ADB2C tenant.
Navigate to your Application’s Key-Vault:
Click on “AzureADB2CExternalAuthClientSecret” in Secrets under settings
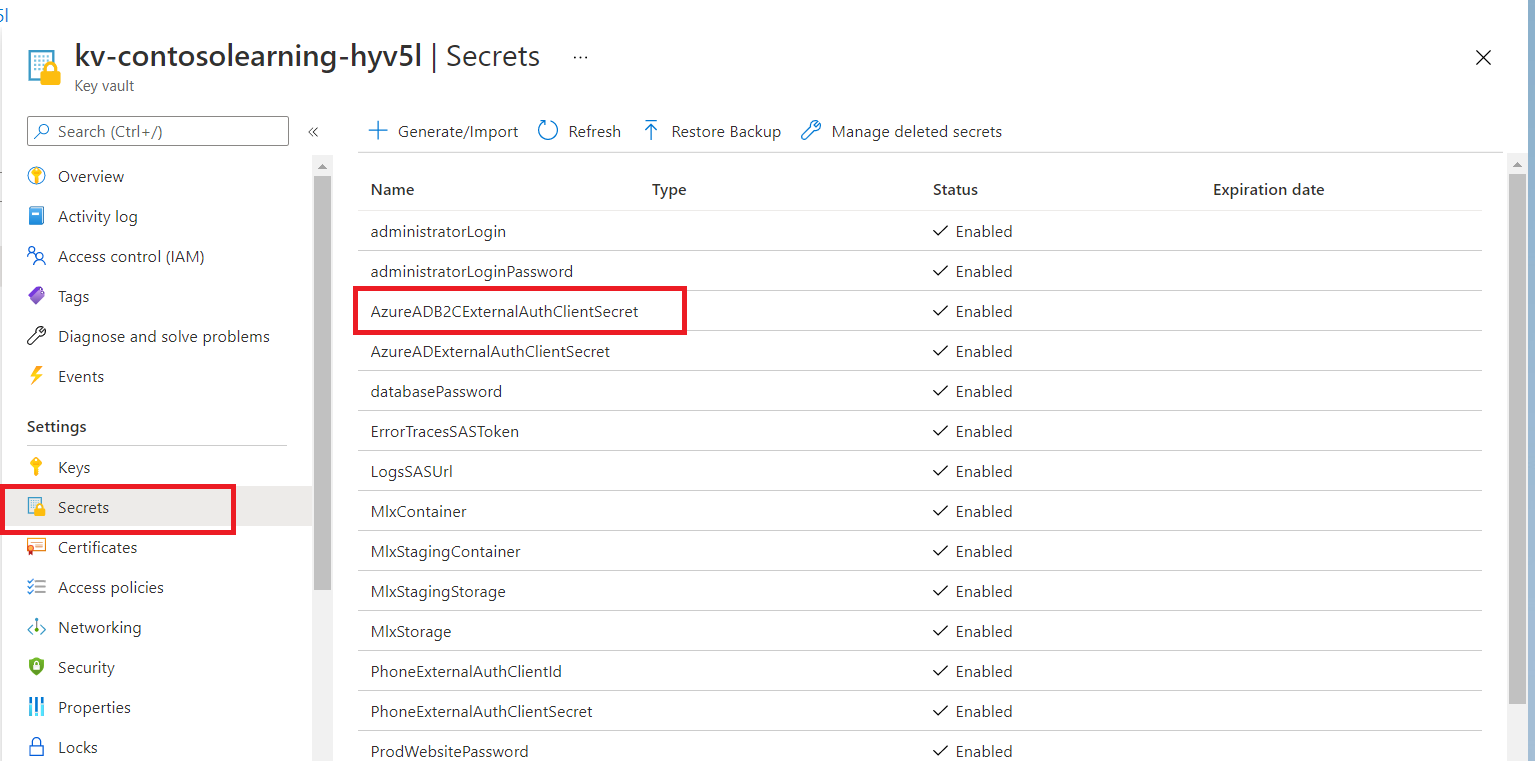
Create a new secret version
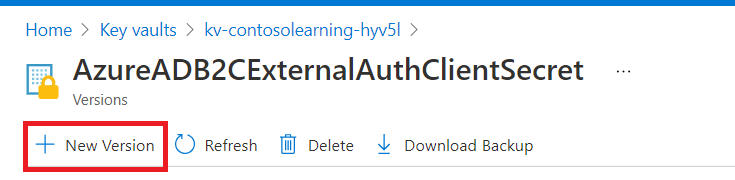
Paste the ADB2C application ClientSecret that you previously copied as Value and click save.
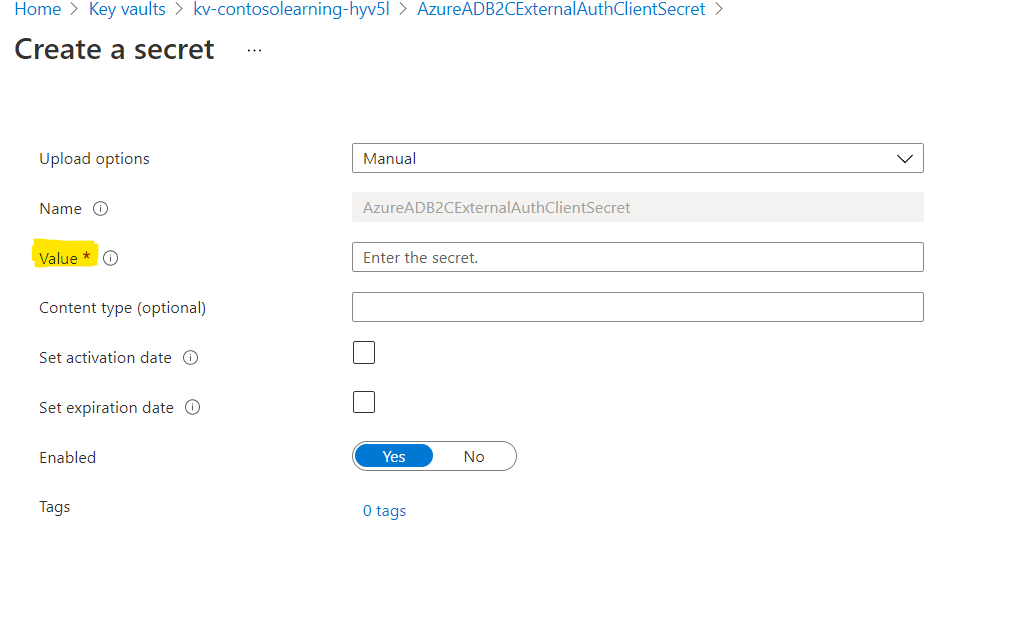
Now, with in AzureADB2CExternalAuthClientSecret, click on newly created secret version and copy Secret Identifier
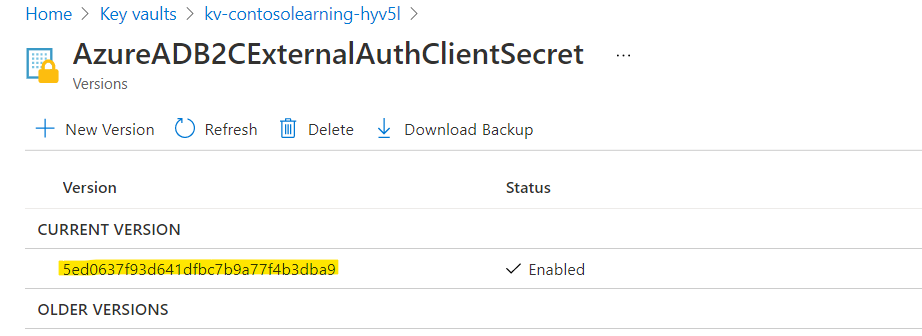
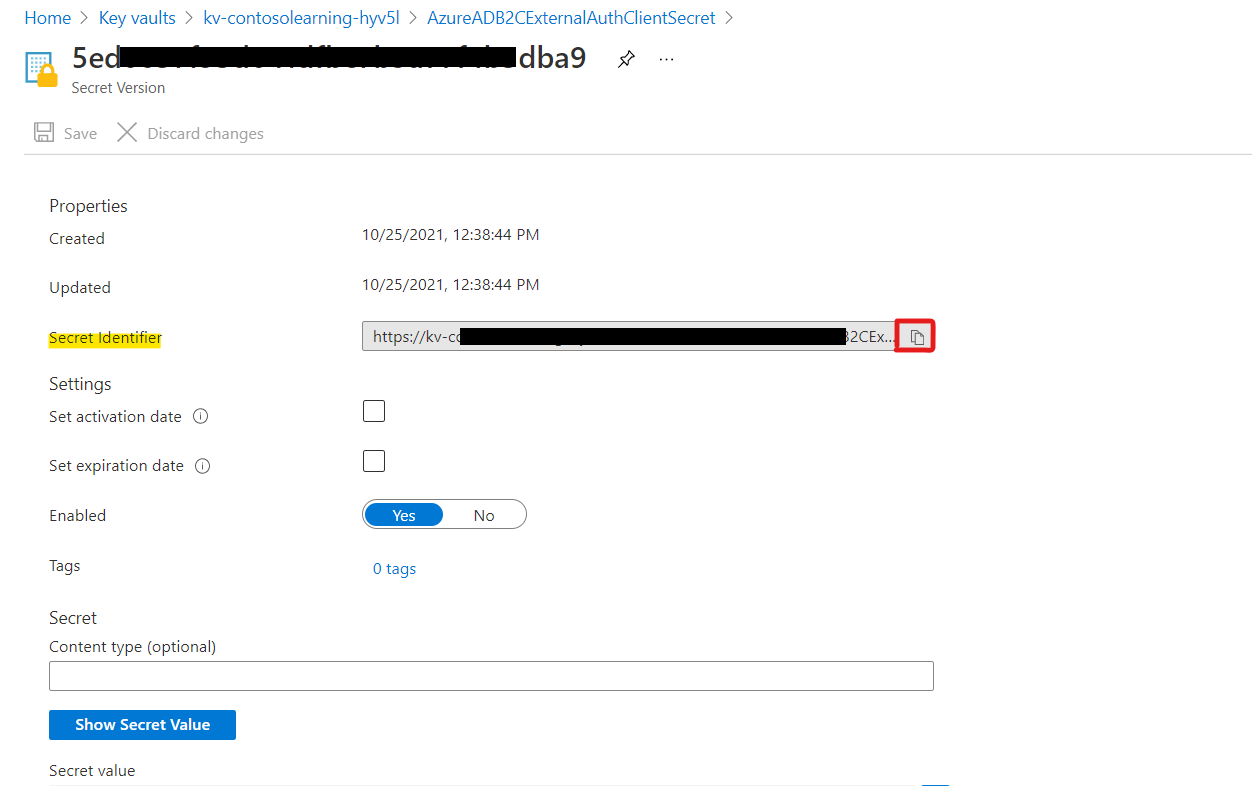
Navigate to configurations on the Training Platform, search and update the following app settings (create new application settings if not already present)
Application Setting Value idp:AzureADB2CExternalAuthClientId Paste the ClientID of ADB2C application idp:AzureADB2CExternalAuthClientSecret Paste the Secret Identifier from Key vault idp:AzureADB2CExternalAuthTenant ADB2C Tenant Name idp:AzureADB2CExternalAuthPolicy Sign-up ans Sign-in User flow name idpSelection 1 Add Phone-based login to existing Social Account login Instance
Add Work email based Authentication to existing Social Account login instance
Add Phone-based login to Azure AD (work email) based authentication instance
To be able to support multi mode authentication you should create AD B2C tenant to support social login and later configure the AD B2C application to add Phone and work email based login.
Configure login identity for the platform by creating an Azure AD B2C Tenant. In the document skip point 7 in Step2 as you are not deploying new instance, proceed to Step3 if you need to add local account login support to your instance.
Add Phone-based login to existing Social Account login Instance
Add Work email based Authentication to existing Social Account login instance
Note
- Please note that learner should use only one mode of authentication (phone, social email, work email) for registering. If a learner uses multiple modes of authentication for registration, the accounts will be treated as different users.
- If you have an existing mobile application and you made changes to login type on your instance, to have them reflected in your mobile app, you need to update your existing mobile application.