Quickstart: Update and secure container image dependencies with Dependabot and Copacetic
In this quickstart, you'll be introduced to the steps necessary to configure Dependabot and Copacetic, which will help you automate software dependency updates and bolster the security of container images in a secure supply chain environment. By using these tools, you can ensure that your container images are always current and secure.
In this quickstart, you learn how to:
- Update container image dependencies and security using Dependabot.
- Dependabot automates the process of keeping your container images dependencies up to date, reducing the risk of vulnerabilities.
- Continuously monitor, scan, and patch container images using Copacetic.
- Copacetic provides ongoing monitoring and scanning of your container images, ensuring they are secure and patched against known vulnerabilities.
Prerequisites
- An Azure subscription. If you don't have an Azure subscription, create a free account before you begin.
- The latest version of the Azure CLI installed and configured for your subscription.
- An existing Azure Container Registry (ACR) in your subscription.
Update container image dependencies and security using Dependabot
Dependabot is a tool that automates the process of keeping software dependencies up-to-date. It works by scanning your repository for outdated dependencies and creating pull requests to update them to the latest version. It checks for updates to your dependencies on a daily basis and creates pull requests to update them. You can configure Dependabot to create pull requests for all types of dependencies, including Docker images. We recommend using dependabot to automatically bump dependencies in your Dockerfiles, Kubernetes yaml files, and Helm chart values yaml files to get the latest security patches and reduce security risks.
Use Dependabot with GitHub
Follow the guidance and recommendations for effectively managing pull requests raised by Dependabot, using GitHub Actions to enhance Dependabot's performance, and troubleshooting common Dependabot errors.
- Set up Dependabot with GitHub here.
Use Dependabot with Azure DevOps
Follow the instructions to configure Dependabot with Azure DevOps, ensuring your container image dependencies remain current with the latest versions and security enhancements.
- Grant Permissions: Create a service account with the name
YOUR-PROJECT-NAME Build Service (YOUR-ORGANIZATION-NAME)and grant it the following permissions:
- Force Push
- Contribute to pull requests
- Create branch
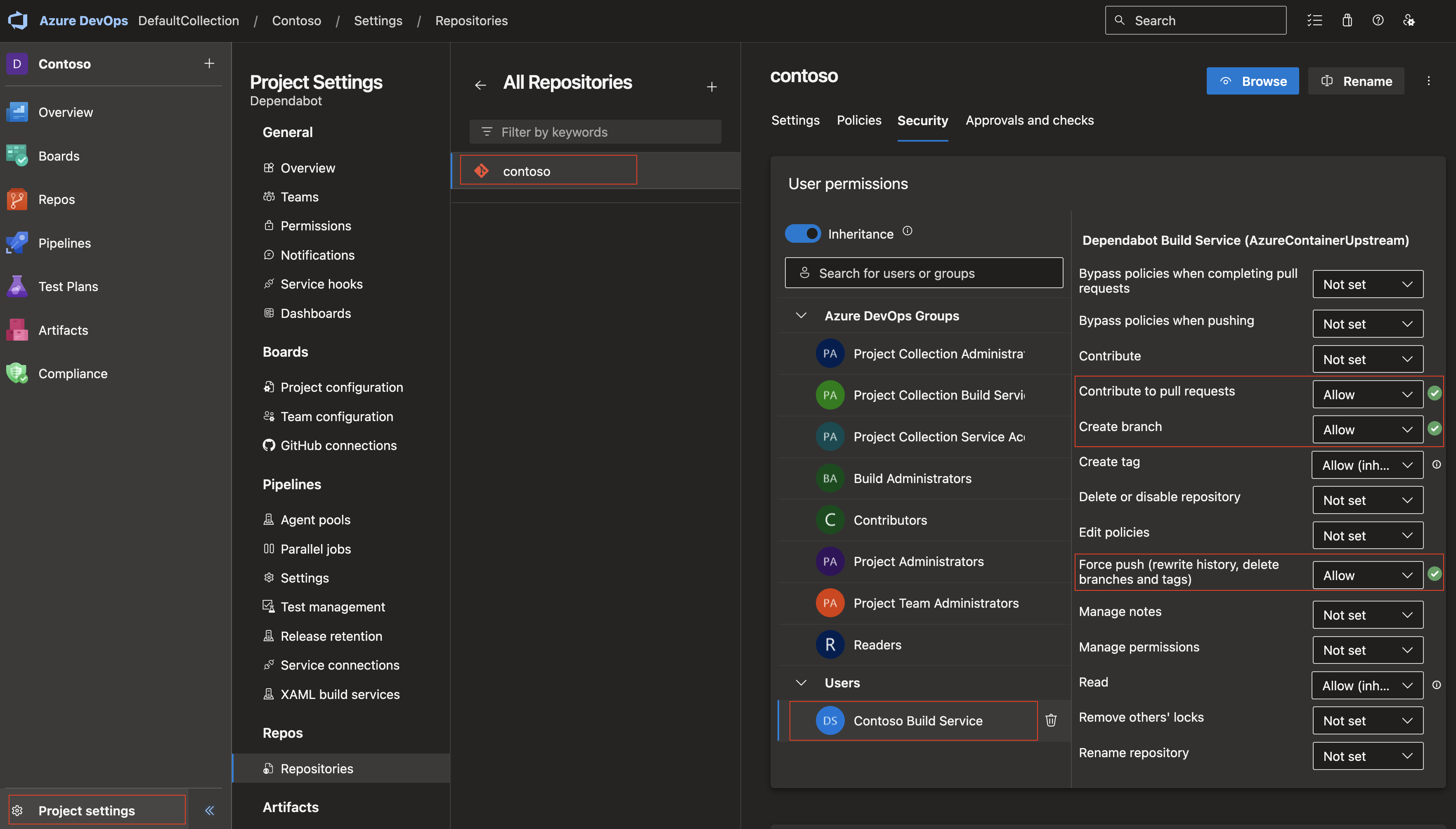
Make sure to replace YOUR-PROJECT-NAME and YOUR-ORGANIZATION-NAME with the actual names of your project and organization.
Configure Dependabot: To configure Dependabot, add a
dependabot.ymlconfiguration file to your repository. Here's an example of what your configuration file might look like:version: 2 updates: - package-ecosystem: "docker" directory: "/" assignees: - "dependabot"
This configuration sets up Dependabot for a project that uses Docker, specifying that the root directory ("/") is where the Docker files are located and assigning Dependabot to handle the updates. You can customize the configuration to suit your project's needs.
Create an Azure DevOps Pipeline: To create an Azure DevOps Pipeline, add an
azure-pipeline.ymlfile to your repository with the following content:schedules: - cron: '0 14 * * *' displayName: 'Every day at 7am PST' branches: include: [main] always: true trigger: none jobs: - job: steps: - script: | git clone https://github.com/dependabot/dependabot-core.git cd dependabot-core DOCKER_BUILDKIT=1 docker build \ --build-arg "USER_UID=$(id -u)" \ --build-arg "USER_GID=$(id -g)" \ -t "dependabot/dependabot-core" . cd .. displayName: build dependabot-core Docker image - script: | git clone https://github.com/dependabot/dependabot-script.git cd dependabot-script docker run -v "$(pwd):/home/dependabot/dependabot-script" -w /home/dependabot/dependabot-script dependabot/dependabot-core bundle install -j 3 --path vendor displayName: install dependencies - script: | #!/bin/bash SYSTEM_COLLECTIONURI_TRIM=`echo "${SYSTEM_COLLECTIONURI:22}"` PROJECT_PATH="$SYSTEM_COLLECTIONURI_TRIM$SYSTEM_TEAMPROJECT/_git/$BUILD_REPOSITORY_NAME" echo "path: $PROJECT_PATH" docker run -v "$(pwd)/dependabot-script:/home/dependabot/dependabot-script" \ -w '/home/dependabot/dependabot-script' \ -e AZURE_ACCESS_TOKEN=$(System.AccessToken) \ -e PACKAGE_MANAGER=docker \ -e PROJECT_PATH=$PROJECT_PATH \ -e DIRECTORY_PATH=/ \ -e OPTIONS="$OPTIONS" \ dependabot/dependabot-core bundle exec ruby ./generic-update-script.rb displayName: "run dependabot" env: OPTIONS: | { "kubernetes_updates": true }
Run the pipeline: Create and verify new ADO pipeline from above
azure-pipelines.yamlfile.
Dependabot can update container image dependencies in various scenarios, such as:
- Dockerfile
- Kubernetes YAML
- Helm values.yaml
Note
The syntax allows Dependabot to identify and update container image dependencies within your configuration files, ensuring that you stay up-to-date with the latest versions and security patches.
When specifying images in your configuration files, use the following syntax:
# Dockerfile
foo:
image:
repository: sql/sql
tag: 1.2.3
registry: docker.io
# Helm values.yaml
foo:
image:
repository: sql/sql
tag: 1.2.3
registry: docker.io
Alternatively, for Helm values.yaml, you can use the version field to specify the image version:
foo:
image:
repository: sql/sql
version: 1.2.3
Continuously monitor, scan, and patch container images using Copacetic
Copacetic (copa) is a Microsoft-backed CNCF open-source project that directly patches Linux OS package vulnerabilities in container images given the vulnerability scanning results from popular scanner tools. Copacetic allows to patch containers quickly without going upstream for a full rebuild. This will help the container images to quickly redeploy into production. Copacetic is only for Linux OS vulnerabilities. For app-level vulnerabilities, patches must be done before the image is built.
Use Copacetic
Follow the quick start guide for Copacetic provides instructions to patch container images by utilizing vulnerability scanning results.
Review the Sample ADO Pipeline for a sample Azure DevOps pipeline configuration file for using Copacetic. The pipeline is designed to integrate Copacetic into your CI/CD workflow, allowing for continuous monitoring, scanning, and patching of container images for vulnerabilities.
Copacetic can also be integrated into Github Actions workflows to patch image vulnerabilities using the Copacetic Action. This action patches a set of designated images for a repository using their associated vulnerability reports.