Microsoft's Security Service Edge Solution Deployment Guide for Microsoft Entra Private Access Proof of Concept
Microsoft's identity-centric Security Service Edge solution converges network, identity, and endpoint access controls so that you can secure access to any app or resource, from any location, device, or identity. It enables and orchestrates access policy management for employees, business partners, and digital workloads. You can continuously monitor and adjust user access in real time if permissions or risk level changes to your private apps, SaaS apps, and Microsoft endpoints.
This guidance helps you deploy Microsoft Entra Private Access as a Proof of Concept in your production or test environment, including Conditional Access policies and application assignments. You can scope your configuration to specific test users and groups. See Microsoft's Security Service Edge Solution Deployment Guide Introduction for prerequisites.
Deploy and test Microsoft Entra Private Access
Complete the Configure initial product steps. This includes enabling the Microsoft Entra Private Access traffic forwarding profile and installing the Global Secure Access Client on a test device. Use this guidance to set up your connector server and publish your application to Microsoft Entra Private Access.
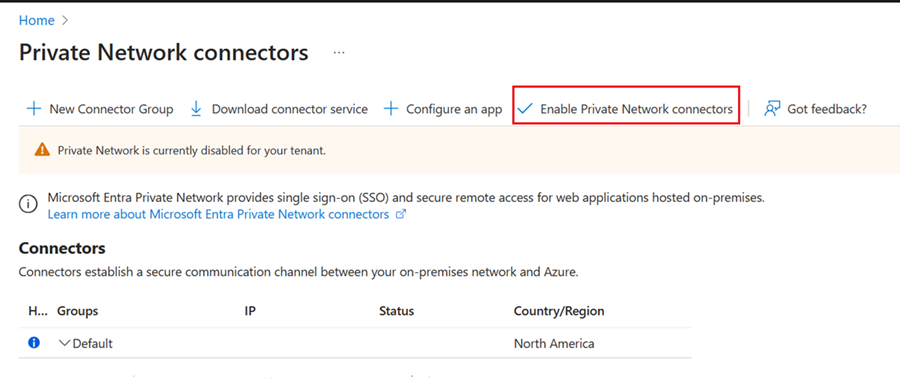
Set up connector server
The connector server communicates with Microsoft's Security Service Edge Solution as the gateway to your corporate network. It uses outbound connections through 80 and 443 and doesn't require inbound ports. Learn How to configure connectors for Microsoft Entra Private Access.
On the connector server, open the Microsoft Entra admin center. Go to Global Secure Access > Connect > Connectors and then click Enable Private Network connectors. Click Download connector service.
Create a new connector group for your Private Network Connector.
Follow the installation wizard to install the connector service on your connector server. When prompted, enter your tenant credentials to complete installation.
Confirm that the connector server is installed in your new connector group by ensuring that it appears in the Connectors list.
In this guide, we use a new connector group with one connector server. In a production environment, you should create connector groups with multiple connector servers. See detailed guidance for publishing apps on separate networks by using connector groups.
Publish application
Microsoft Entra Private Access supports transmission control protocol (TCP) applications using any ports. To connect to the application server using RDP (TCP port 3389) over the internet, complete the following steps:
From the connector server, verify that you can remote desktop into the application server.
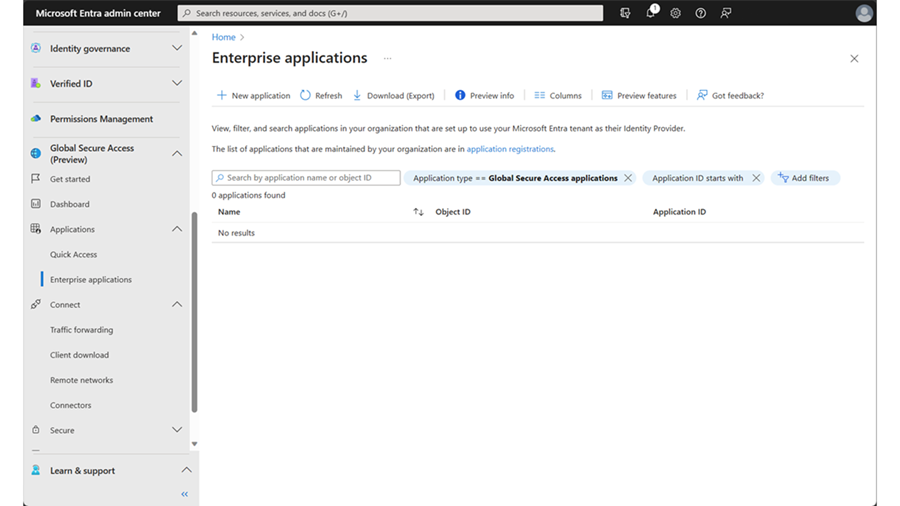
Open the Microsoft Entra admin center and then go to Global Secure Access > Applications > Enterprise applications > + New Application.
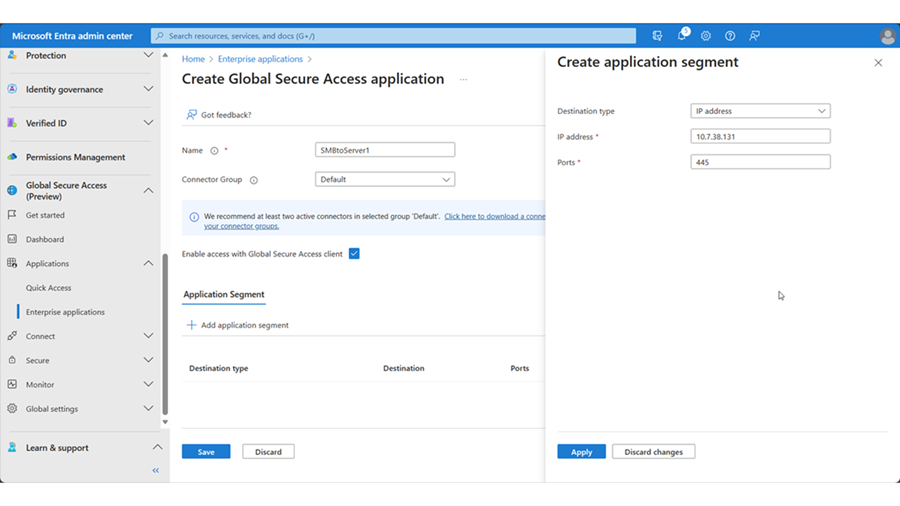
Enter a Name (such as Server1) and select the new connector group. Click +Add application segment. Enter the IP address of the application server and port 3389.
Click Apply > Save. Verify that the application is added to the Enterprise applications list.
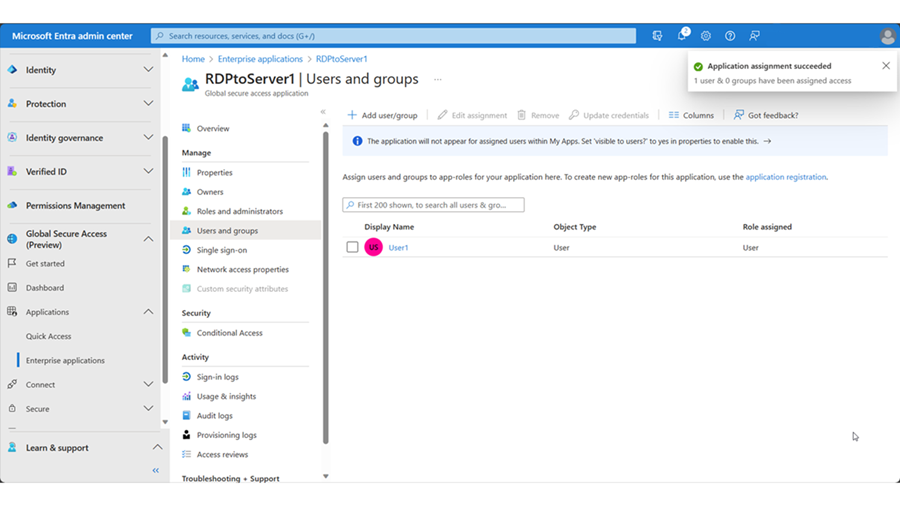
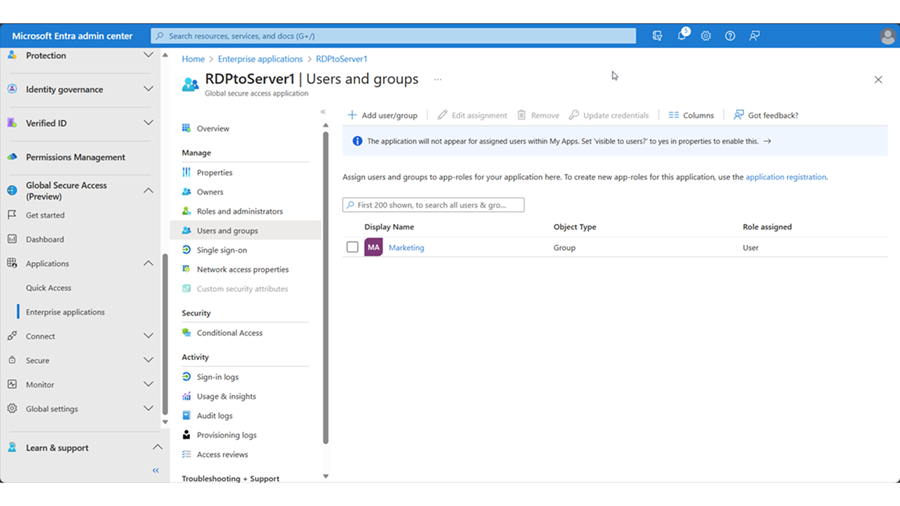
Go to Identity > Applications > Enterprise applications and click the newly created application.
Click Users and groups. Add your test user that that will access this application from the internet.
Sign in to your test client device and open a remote desktop connection to the application server.
Sample PoC scenario: apply Conditional Access
You can apply Conditional Access policies to applications published with Microsoft Entra Private Access. Use this guidance to enforce phone sign-in (Microsoft Authenticator) for users that remote desktop to the application server.
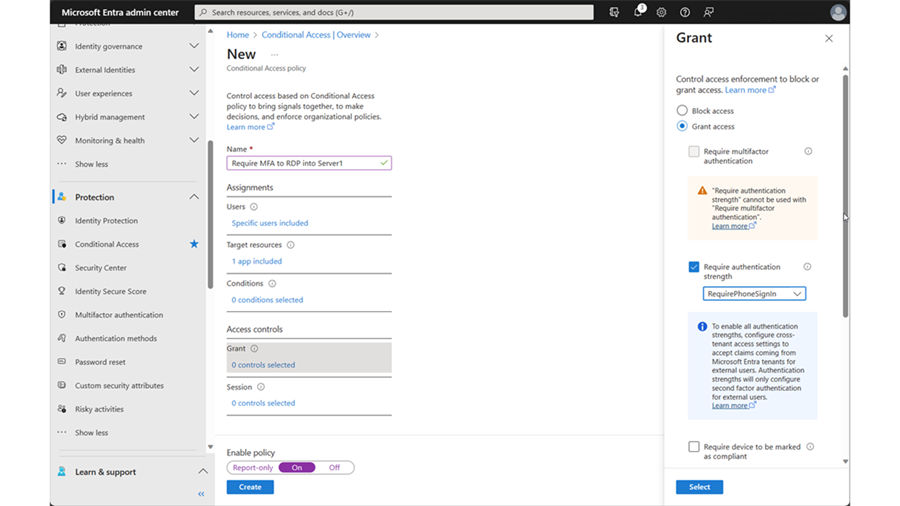
Open the Microsoft Entra admin center. Go to Identity > Protection > Conditional Access > Authentication strengths. Select +New authentication strength.
Create New authentication strength to require Microsoft Authenticator (Phone Sign-in).
Go to Policies.
Create a new Conditional Access Policy as follows:
- Users: select a specific user
- Target resources: select a specific published app
- Grant > Grant Access -- Require Authentication Strengths (choose authentication strength created above)
To accelerate the enforcement of Conditional Access policies, right-click the Global Secure Access client in the Windows taskbar. Select Switch user. Wait for several seconds until prompted for authentication.
Open a remote desktop connection to the application server. Verify enforcement of Conditional Access by checking sign-in logs or confirming that expected authentication strength is prompted.
Sample PoC scenario: control access by multiple users to multiple apps
In the earlier section, we applied Conditional Access to one application for a single user. In production, you need access control for multiple applications and users.
In this scenario, a Marketing department user needs to use RDP to open a remote desktop session to Server1. Additionally, a user in the Developer department needs to access a file share on Server using SMB protocol. Permissions to each application are configured so that users in the Marketing department can remote desktop into Server1 but can't access the file share on Server1. For additional access control, we enforce MFA to users in the Marketing department and require users in the Developer department to agree on the Terms of Use to access their resources.
Open the Microsoft Entra admin center and create two test users, such as FirstUser and SecondUser.
Create a group each for Marketing and Developers. Add FirstUser to the Marketing group and add SecondUser to the Developers group.
Go to Global Secure Access > Applications > Enterprise applications. Select your test application from the Publish application section. Remove your earlier test user from Users and groups and replace it with the Marketing group.
Create a second application to connect to your application server using SMB protocol over port 445.
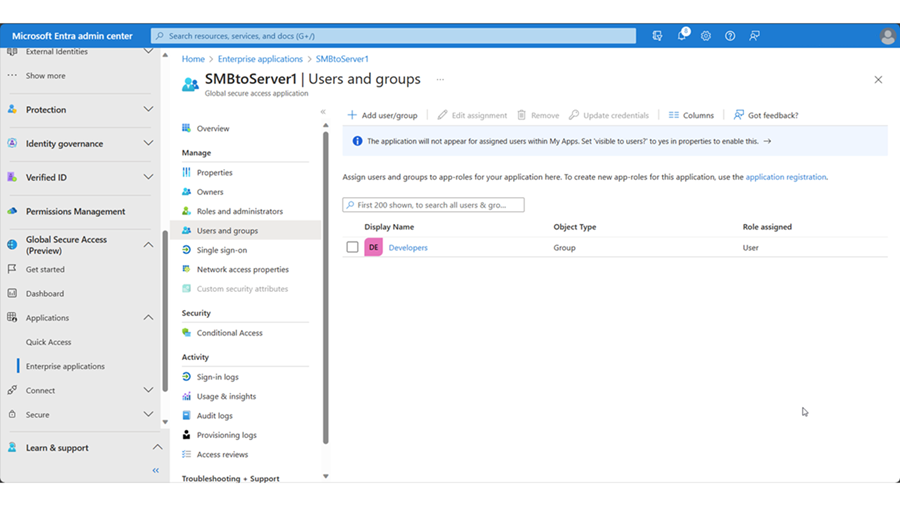
In Users and groups of the new SMB application, add the Developers group.
Sign in to your test client device with the Marketing user identity FirstUser. Verify that FirstUser can successfully open a remote desktop connection to Server1 and that Developer group user SecondUser is blocked from opening a remote desktop connection to Server1.
Sign in to your test client device with the Developers user SecondUser and confirm that you can successfully connect to file shares on Server1. Confirm that Marketing user FirstUser can't connect to the same file share.
Create Conditional Access policies to add additional controls.
- Conditional Access Policy 1
- Name: MarketingToServer1
- Users: Marketing group
- Target Resource: RDPToServer1
- Grant: Grant access, require multifactor authentication
- Session: Sign-in frequency 1 hour
- Conditional Access Policy 2
- Name: DevelopersToServer1
- Users: Developers group
- Target Resource: SMBToServer1
- Grant: Grant access, require Terms of Use
- Session: Sign-in frequency 1 hour
- Conditional Access Policy 1
Sign in with the respective users and verify Conditional Access policies.
Sample PoC scenario: verify application access from traffic logs
You can monitor applications accessed via Microsoft Entra Private Access via the traffic logs.
Open the Microsoft Entra admin center. Go to Global Secure Access > Monitor > Traffic logs.
Select Private Access to apply filter.
Select each log to view activity details with specific information about users and accessed applications.
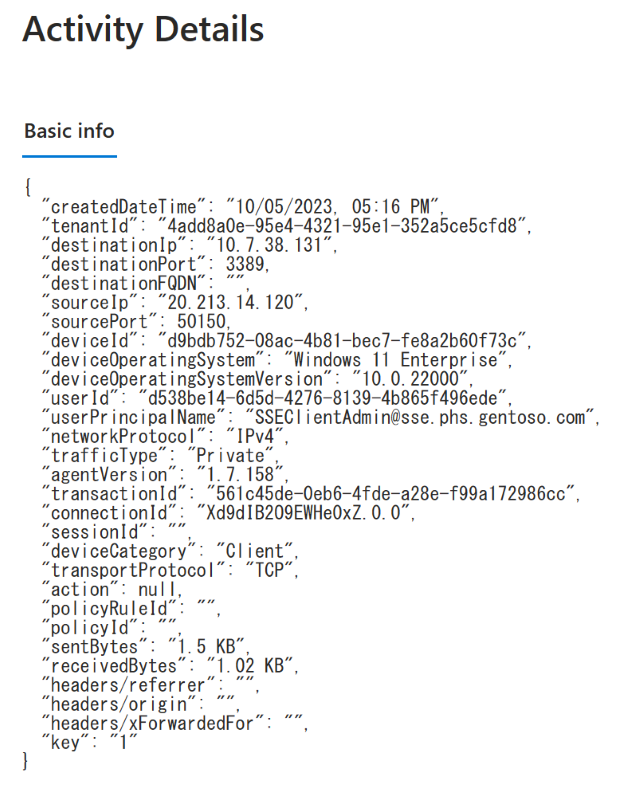
Select Add Filter to find the information of interest (for example, User Principal Name contains UserA).
Note
The IP Address listed in the sourceIp section is the public IP address of the client and not the IP Address of the Microsoft's Security Service Edge Solution Network.
Next steps
Deploy and verify Microsoft Entra Internet Access for Microsoft Traffic Deploy and verify Microsoft Entra Internet Access