Universal Conditional Access through Global Secure Access
In addition to sending traffic to Global Secure Access, administrators can use Conditional Access policies to secure traffic profiles. They can mix and match controls as needed like requiring multifactor authentication, requiring a compliant device, or defining an acceptable sign-in risk. Applying these controls to network traffic not just cloud applications allows for what we call universal Conditional Access.
Conditional Access on traffic profiles provides administrators with enormous control over their security posture. Administrators can enforce Zero Trust principles using policy to manage access to the network. Using traffic profiles allows consistent application of policy. For example, applications that don't support modern authentication can now be protected behind a traffic profile.
This functionality allows administrators to consistently enforce Conditional Access policy based on traffic profiles, not just applications or actions. Administrators can target specific traffic profiles - the Microsoft traffic profile, private resources, and internet access with these policies. Users can access these configured endpoints or traffic profiles only when they satisfy the configured Conditional Access policies.
Prerequisites
- Administrators who interact with Global Secure Access features must have one or more of the following role assignments depending on the tasks they're performing.
- The Global Secure Access Administrator role role to manage the Global Secure Access features.
- The Conditional Access Administrator to create and interact with Conditional Access policies.
- The product requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
- To use the Microsoft traffic forwarding profile, a Microsoft 365 E3 license is recommended.
Known tunnel authorization limitations
Both the Microsoft and Internet access forwarding profiles use Microsoft Entra ID Conditional Access policies to authorize access to their tunnels in the Global Secure Access Client. This means that you can Grant or Block access to the Microsoft traffic and Internet access forwarding profiles in Conditional Access. In some cases when authorization to a tunnel isn't granted, the recovery path to regain access to resources requires accessing destinations on either the Microsoft traffic or Internet access forwarding profile, locking a user out from accessing anything on their machine.
One example is if you block access to the Internet access target resource on noncompliant devices, you leave Microsoft Entra Internet Access users unable to bring their devices back to compliance. The way to mitigate this issue is bypassing Network endpoints for Microsoft Intune and any other destinations accessed in Custom compliance discovery scripts for Microsoft Intune. You can perform this operation as part of custom bypass in the Internet access forwarding profile.
Other known limitations
- Continuous access evaluation isn't currently supported for Universal Conditional Access for Microsoft traffic.
- Applying Conditional Access policies to Private Access traffic isn't currently supported. To model this behavior, you can apply a Conditional Access policy at the application level for Quick Access and Global Secure Access apps. For more information, see Apply Conditional Access to Private Access apps.
- Microsoft traffic can be accessed through remote network connectivity without the Global Secure Access Client; however the Conditional Access policy isn't enforced. In other words, Conditional Access policies for the Global Secure Access Microsoft traffic are only enforced when a user has the Global Secure Access Client.
Conditional Access policies
With Conditional Access, you can enable access controls and security policies for the network traffic acquired by Microsoft Entra Internet Access and Microsoft Entra Private Access.
- Create a policy that targets all Microsoft traffic.
- Apply Conditional Access policies to your Private Access apps, such as Quick Access.
- Enable Global Secure Access signaling in Conditional Access so the source IP address is visible in the appropriate logs and reports.
Internet Access – Universal Conditional Access
The following example demonstrates how Microsoft Entra Internet Access works when you apply Universal Conditional Access policies to network traffic.
Note
Microsoft's Security Service Edge solution comprises three tunnels: Microsoft traffic, Internet Access, and Private Access. Universal Conditional Access applies to the Internet Access and Microsoft traffic tunnels. There isn't support to target the Private Access tunnel. You must individually target Private Access Enterprise Applications.
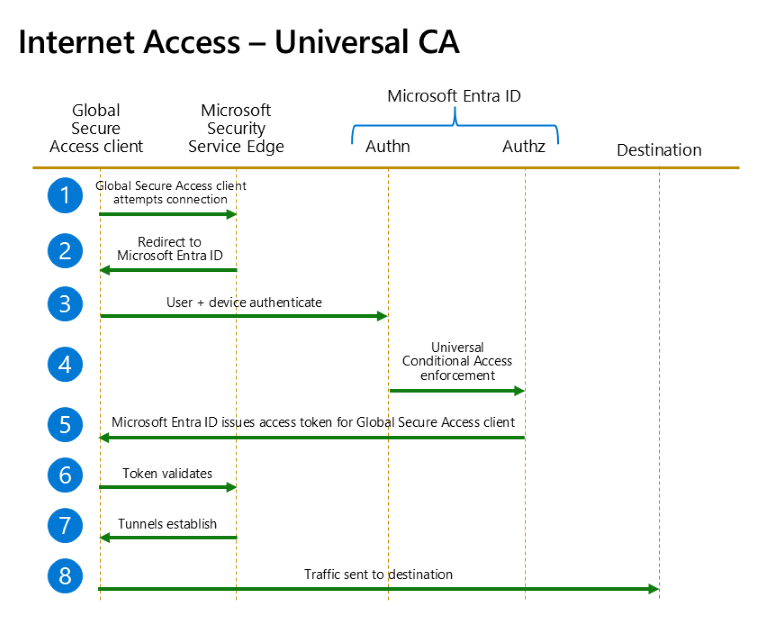
The following flow diagram illustrates Universal Conditional Access targeting internet resources and Microsoft apps with Global Secure Access.
| Step | Description |
|---|---|
| 1 | The Global Secure Access client attempts to connect to Microsoft's Security Service Edge solution. |
| 2 | The client redirects to Microsoft Entra ID for authentication and authorization. |
| 3 | The user and the device authenticate. Authentication happens seamlessly when the user has a valid Primary Refresh Token. |
| 4 | After the user and device authenticate, Universal Conditional Access policy enforcement occurs. Universal Conditional Access policies target the established Microsoft and internet tunnels between the Global Secure Access client and Microsoft Security Service Edge. |
| 5 | Microsoft Entra ID issues the access token for the Global Secure Access client. |
| 6 | The Global Secure Access client presents the access token to Microsoft Security Service Edge. The token validates. |
| 7 | Tunnels establish between the Global Secure Access client and Microsoft Security Service Edge. |
| 8 | Traffic starts being acquired and tunneled to the destination via the Microsoft and Internet Access tunnels. |
Note
Target Microsoft apps with Global Secure Access to protect the connection between the Microsoft Security Service Edge and the Global Secure Access client. To ensure that users can't bypass the Microsoft Security Service Edge service, create a Conditional Access policy that requires compliant network for your Microsoft 365 Enterprise applications.
User experience
When users sign in to a machine with the Global Secure Access Client installed, configured, and running for the first time they're prompted to sign in. When users attempt to access a resource protected by a policy. Like the previous example, the policy is enforced and they're prompted to sign in if they haven't already. Looking at the system tray icon for the Global Secure Access Client you see a red circle indicating it's signed out or not running.
When a user signs in the Global Secure Access Client has a green circle that you're signed in, and the client is running.