Quickstart: Configure per-app access to private resources
This quickstart shows you the steps needed to configure per-app access to private resources. To learn more about Global Secure Access, see What is Global Secure Access?
Prerequisites
Administrators who interact with Global Secure Access features must have the Global Secure Access Administrator role. Some features might also require other roles.
To follow the Zero Trust principle of least privilege, consider using Privileged Identity Management (PIM) to activate just-in-time privileged role assignments.
The product requires licensing. For details, see the licensing section of What is Global Secure Access?. If needed, you can purchase licenses or get trial licenses. To use the Microsoft traffic forwarding profile, a Microsoft 365 E3 license is recommended.
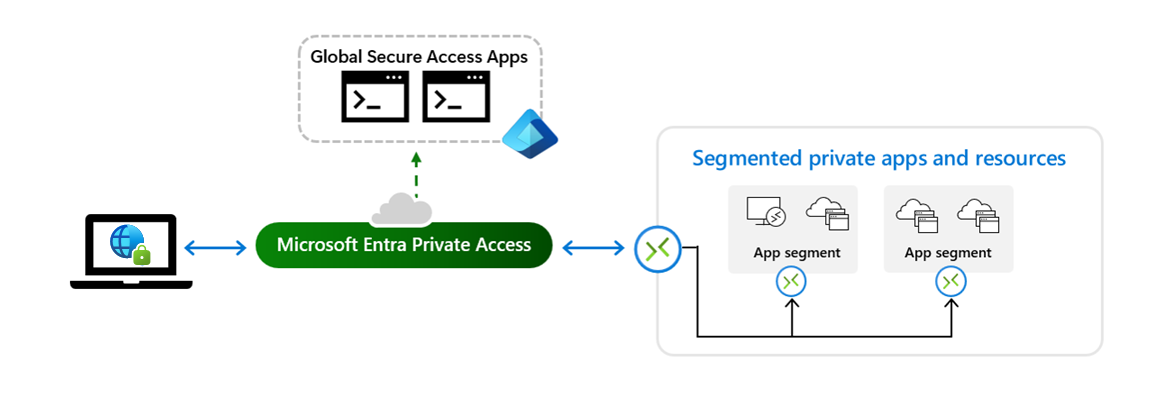
Configure per-app access to private resources
Create specific private apps for granular segmented access to private access resources using Microsoft Entra Private Access.
- Configure a private network connector and connector group.
- Create a private Global Secure Access application.
- Enable the Private Access traffic forwarding profile.
- Install and configure the Global Secure Access Client on end-user devices.
After you complete these steps, users with the Global Secure Access client installed on a Windows device can connect to your private resources through a Global Secure Access app and private network connector.
Optionally:
- Secure Quick Access applications with Conditional Access policies.
- Review the Global Secure Access logs.