Security in Manufacturing data solutions (preview)
Important
Some or all of this functionality is available as part of a preview release. The content and the functionality are subject to change.
Manufacturing data solutions in Microsoft Fabric (preview) is designed to help you meet your security and compliance needs. This article gives you an overview of the security features and capabilities of Manufacturing data solutions that you can configure when secure access is mandatory to protect sensitive data and resources from unauthorized access, data breaches, and cyberattacks.
Set up private links
Azure Private Link provides private connectivity from a virtual network to Azure platform as a service (PaaS). It simplifies the network architecture and secures the connection between Azure endpoints by eliminating data exposure to the public internet.
Azure Private Link lets you connect to a Manufacturing data solutions service from your virtual network via a private endpoint. Resources associated with this virtual network would be able to communicate with Manufacturing data solutions APIs privately through this private endpoint.
A private endpoint is a set of private IP addresses in a subnet within the virtual network. You can then limit access to your Manufacturing data solutions instance over these private IP addresses. Private endpoints for Manufacturing data solutions can be provisioned post the deployment of the Manufacturing data solution instance.
Prerequisites
Create a virtual network in the same subscription as the Manufacturing data solutions instance. This virtual network allows automatic approval of the Private Link endpoint.
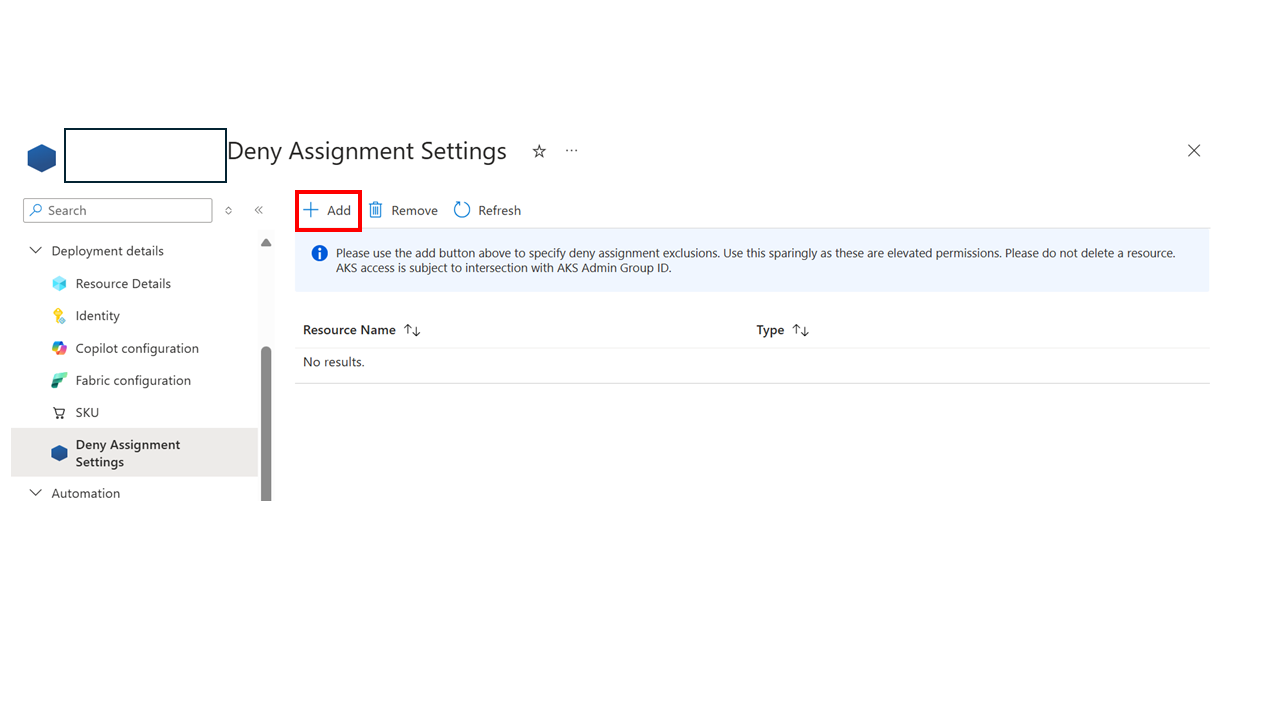
Update the Manufacturing data solutions by configuring the Deny Assignment Group ID in the Deny Assignment Settings of the Manufacturing data solutions resource. The identity responsible for setting up the private link must be added to the Deny Assignment Group, which was configured in the Manufacturing data solutions, to access the Application Gateway resource.
Create private endpoints for Manufacturing data solutions by using the Azure portal
Perform the following steps to create a private endpoint for an existing Manufacturing data solutions instance.
From the All resources pane, select Manufacturing data solutions.
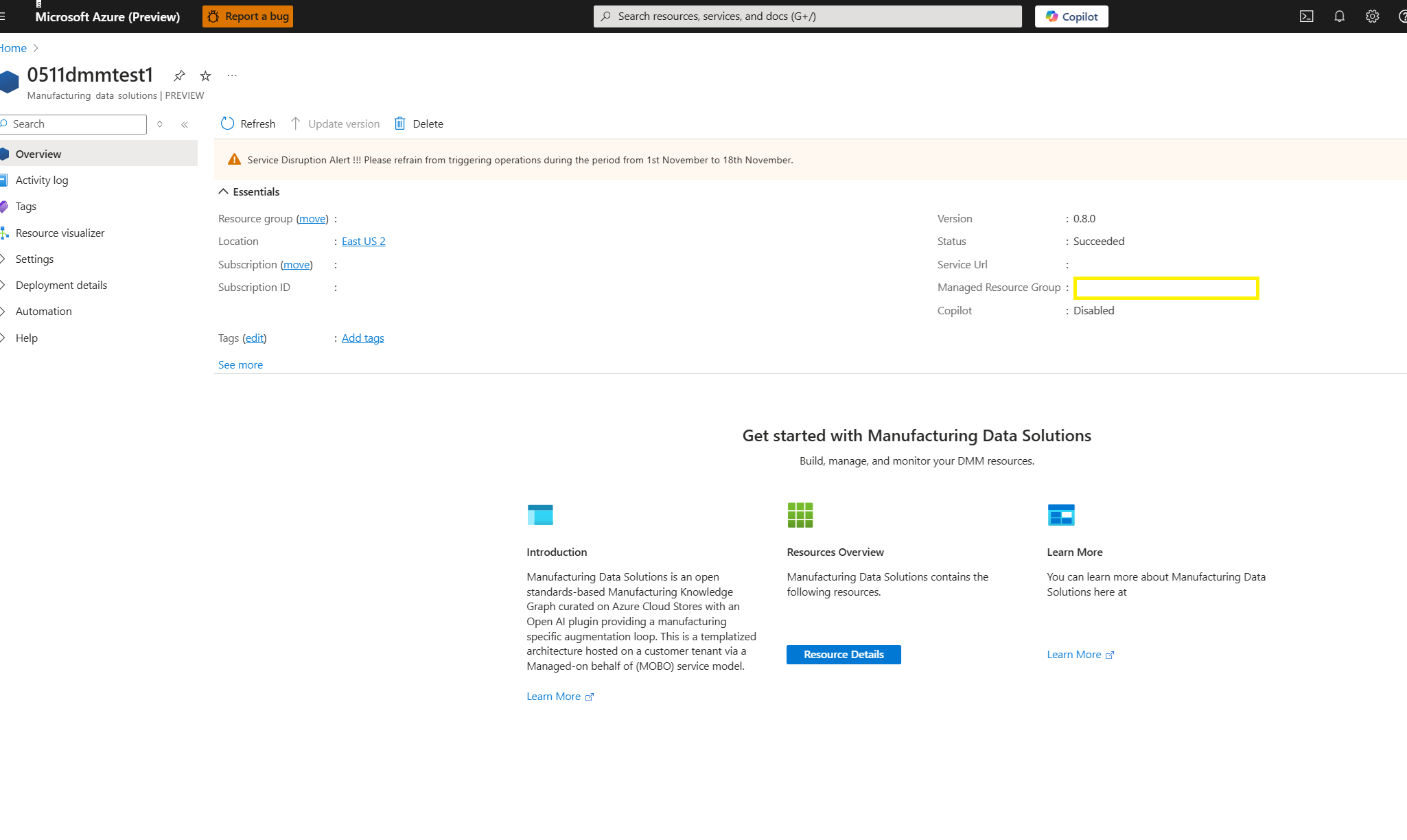
In the Overview page, copy the Managed Resource Group name.
Navigate to Search bar at the top and search for the Managed Resource Group.
From the search result, select the Managed Resource Group associated with your Manufacturing data solutions instance.
In the Overview page, go to Resources tab and filter for Application gateway resource from the Type filter.
Select the Azure Application Gateway resource from the list of resources and navigate to Settings > Private link.
Select the Private endpoint connections tab, and then select +Private endpoint .
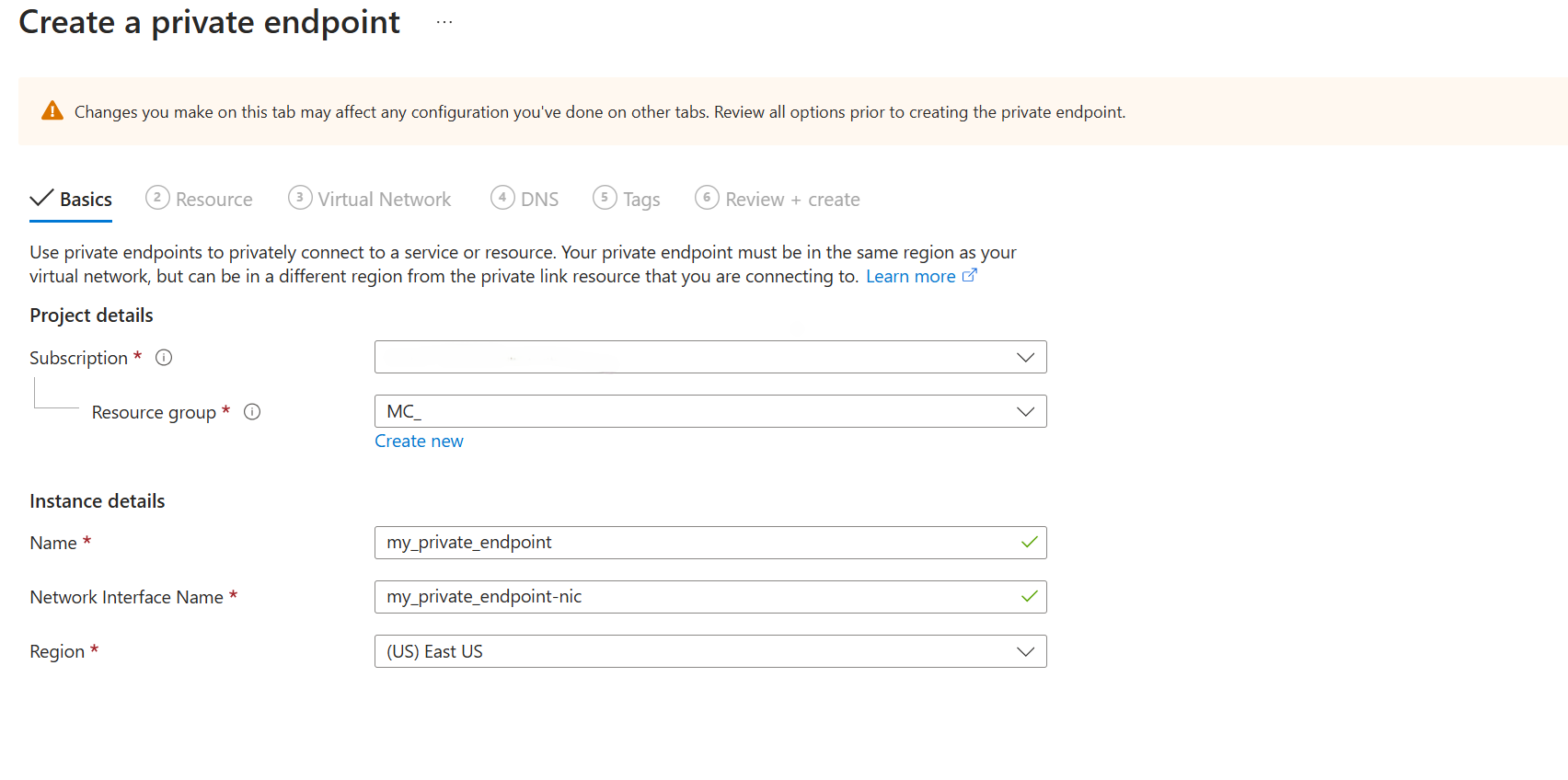
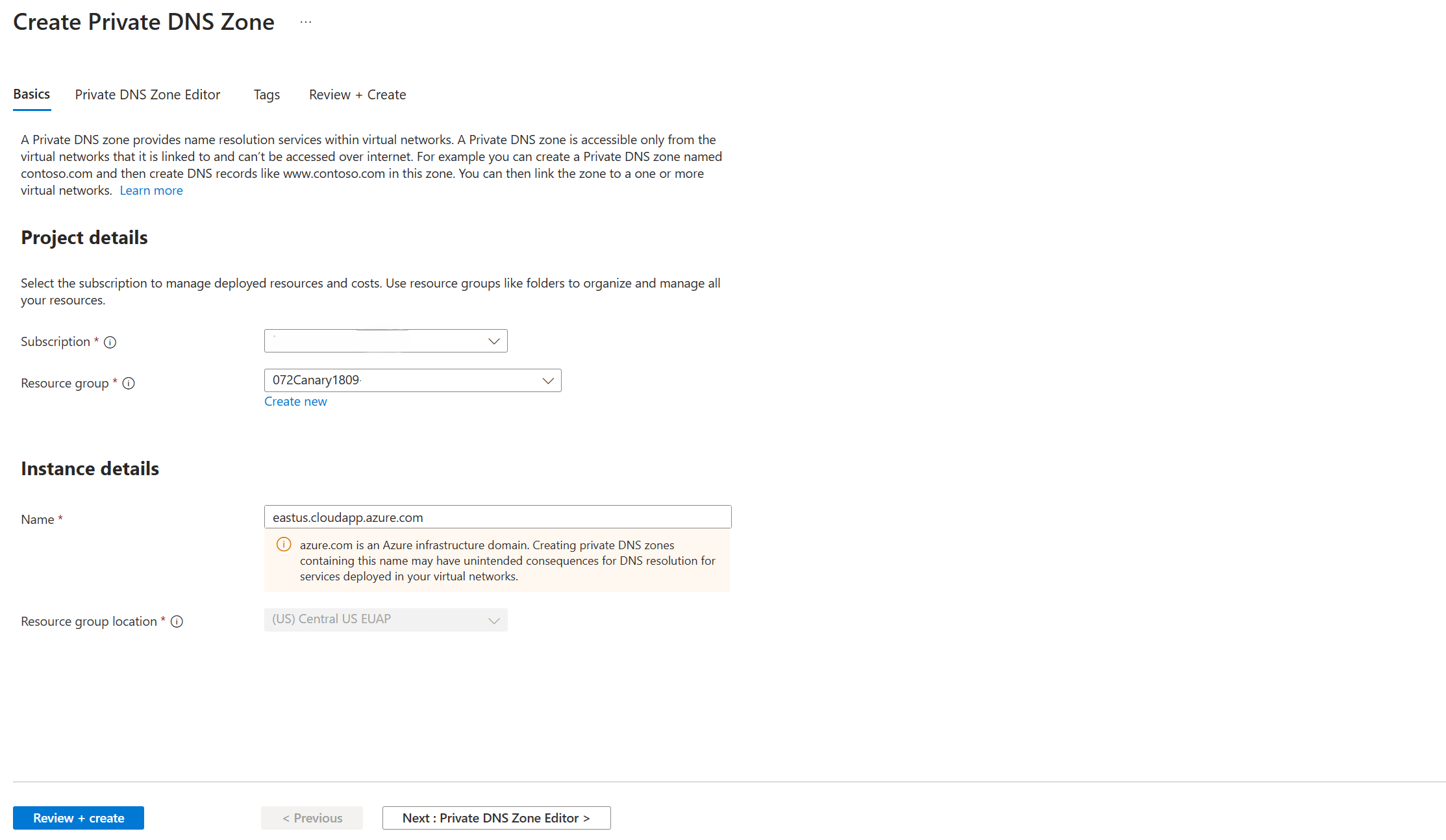
In the Create a private endpoint wizard, on the Basics page, enter or select the following details.
Setting Value Subscription Select your subscription for the resource. Resource group Select a resource group for the resource. Name Enter a name for your private endpoint. The name must be unique. Region Select the region where you want to deploy the Private end point. Select Resource and confirm the following information:
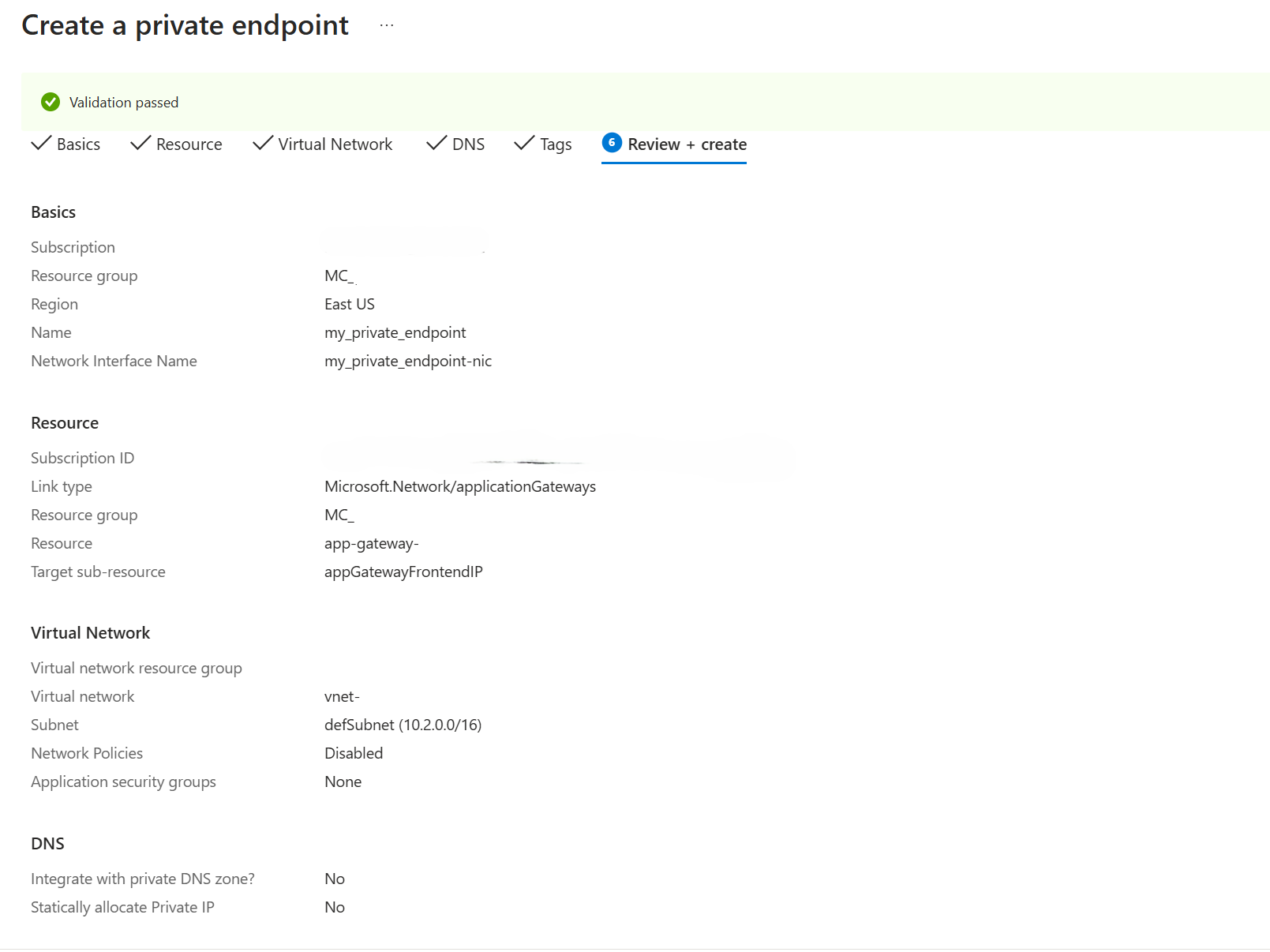
Setting Value Resource type Microsoft.Network/applicationGateways Resource Application Gateway resource name listed in the Resource Details section of the Manufacturing data solutions Target sub-resource appGatewayFrontendIP Select Virtual Network, select the virtual network, and subnet where the private endpoint network interface should be provisioned to. This virtual network and subnet should be the same from where Manufacturing data solutions APIs are being accessed and created as a prerequisite.
Select DNS and retain the default settings or configure private DNS integration.
Select Tags and add tags to categorize resources.
Select Review + create. where Azure validates your configuration. When you see Validation passed, select Create.
After the private endpoint is created, navigate to the Network interface of this private endpoint and note the Private IPv4 address associated with it. This value would be required for the next task, Configure Private DNS routing.
Configure Private DNS routing for Manufacturing data solutions
After the private endpoint is created, to configure the DNS routing for Manufacturing data solutions, follow these steps:
Navigate to Search bar at the top and search for Private DNS zones.
Select +Create.
On the Basics tab, enter the following details:
Setting Value Subscription Select your subscription for the resource. Resource group Select a resource group for the resource. Name <region>.cloudapp.azure.com Region Select the region where you want to deploy Private Link. Select Review + create.
After the Private DNS Zone is created, go to the Private DNZ Zone Overview page and select the Virtual network links from the list of DNS Management.
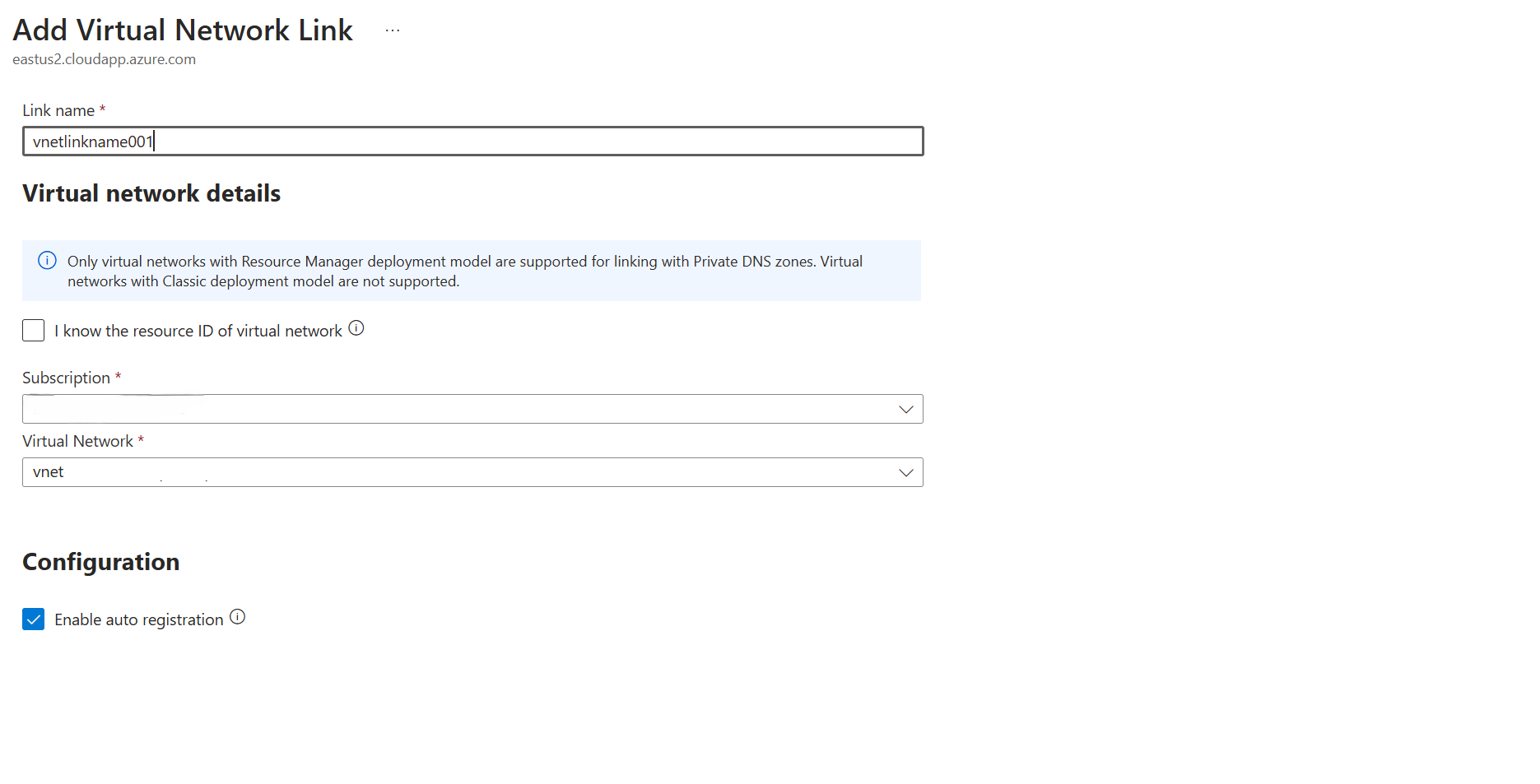
Select + Add to create a new virtual network link.
On the Add virtual network link wizard, enter or select the following details:
Setting Value Link name Virtual network link name Subscription Subscription for the resource Virtual network Select the Virtual Network where the private endpoint network interface was provisioned to. Enable auto registration Select the checkbox to enable auto registration Select Create.
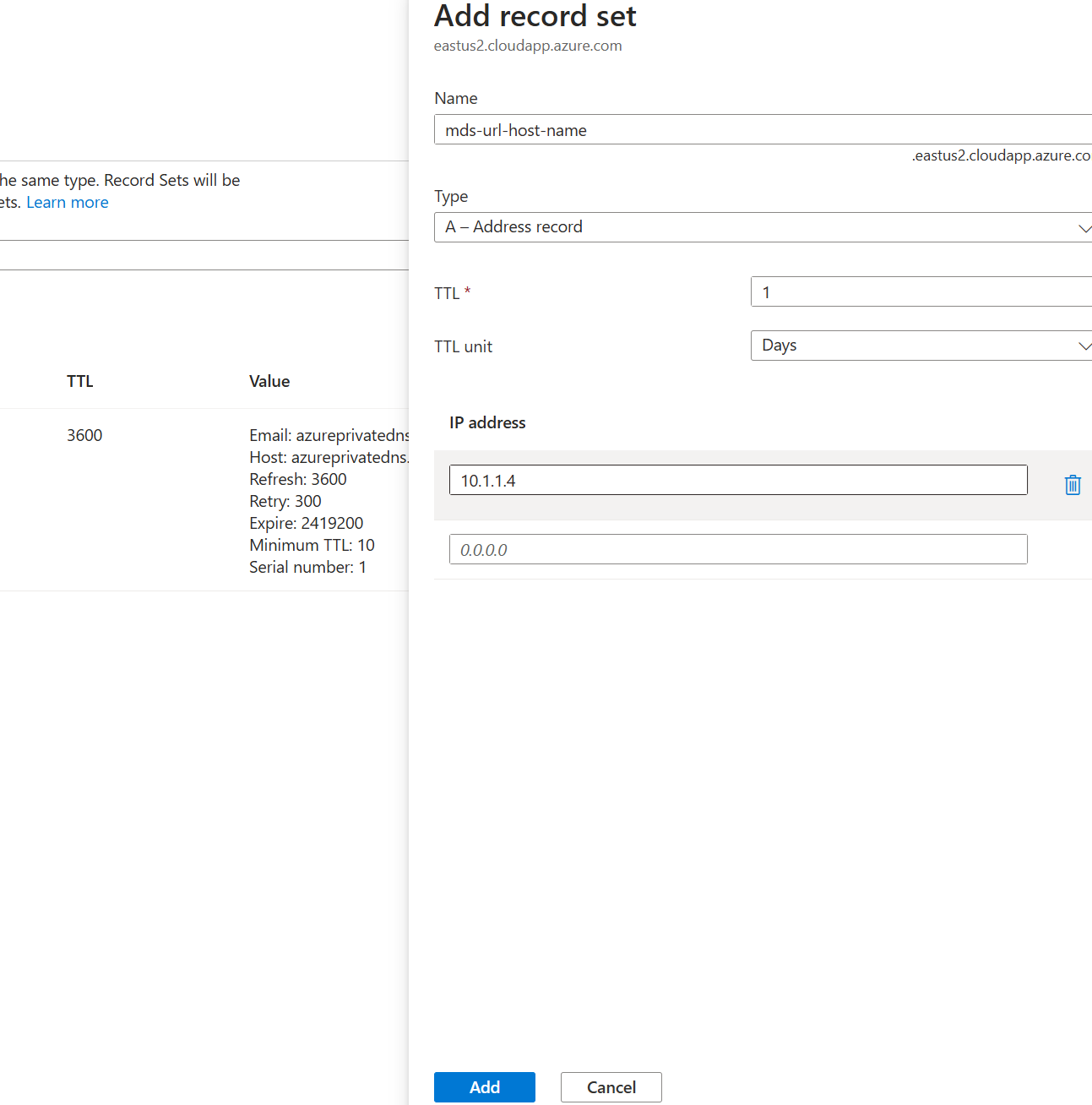
Go to the overview page of the Private DNS Zone and select + Record set.
On the Record set blade, select Add, and enter or select the following values.
Settings Value Name Enter the MDS Service URL Host Name without <region>.cloudapp.azure.com suffix. Type A - Address record TTL/TTL unit Select the duration and unit of TTL IP address Enter the private IP address of the private endpoint network interface created in the above steps
After the Private DNS routing is enabled, you would be able to connect the Manufacturing data solutions seamlessly using the same service URL which resolves to the private IP associated with the virtual network. The entire communication to Manufacturing data solutions APIs now happens over the Microsoft Backbone network instead of the internet.
Set up managed identity (Associate managed identity in Manufacturing data solutions to access other Azure services)
A managed identity from Microsoft Entra ID lets any application access other Microsoft Entra protected resources. Azure platform manages this identity for you. You don't have to create or rotate any secrets. Manufacturing data solutions uses managed identities with specific Azure roles assigned. This way, you can enable role-based access to other Azure services.
To learn more about managed identities, see What are managed identities for Azure resources?
Currently, Manufacturing data solutions don't support system-assigned managed identities. You can associate User managed Identities to Manufacturing data solutions while resource provisioning.
Data encryption
Manufacturing data solutions uses Platform-managed keys (PMKs), with encryption keys generated, stored, and managed entirely by Azure.
PMKs can help organizations implement encryption with little operational overhead. Customers don't interact with PMKs. By default, the keys used for Azure Data Encryption at Rest in Manufacturing data solutions are PMKs.
For more information, see Security in Microsoft Cloud for Manufacturing.
Compliance
For more information, see Governance and compliance in Microsoft Fabric and Compliance in Microsoft Cloud for Manufacturing.
Limitations
The IP allocation method for the private endpoint network interface is fixed to Dynamic. Once IP allocated is released, the DNS record set needs to be updated with the new IP address in the Private DNS Zone.
Private Link Configuration for Application Gateway has an idle timeout of ~5 minutes (300 seconds). To avoid hitting this limit, applications connecting to Manufacturing data solutions endpoints through private endpoint must use TCP keepalive intervals of less than 300 seconds.