Passwordless for Students
With the rise of security threats, it's critical that schools start to think about ways to use security features typically avoided for students.
This article describes a way to use passwordless credentials in schools.
Requirements:
- A license or bundle that includes Entra P1.
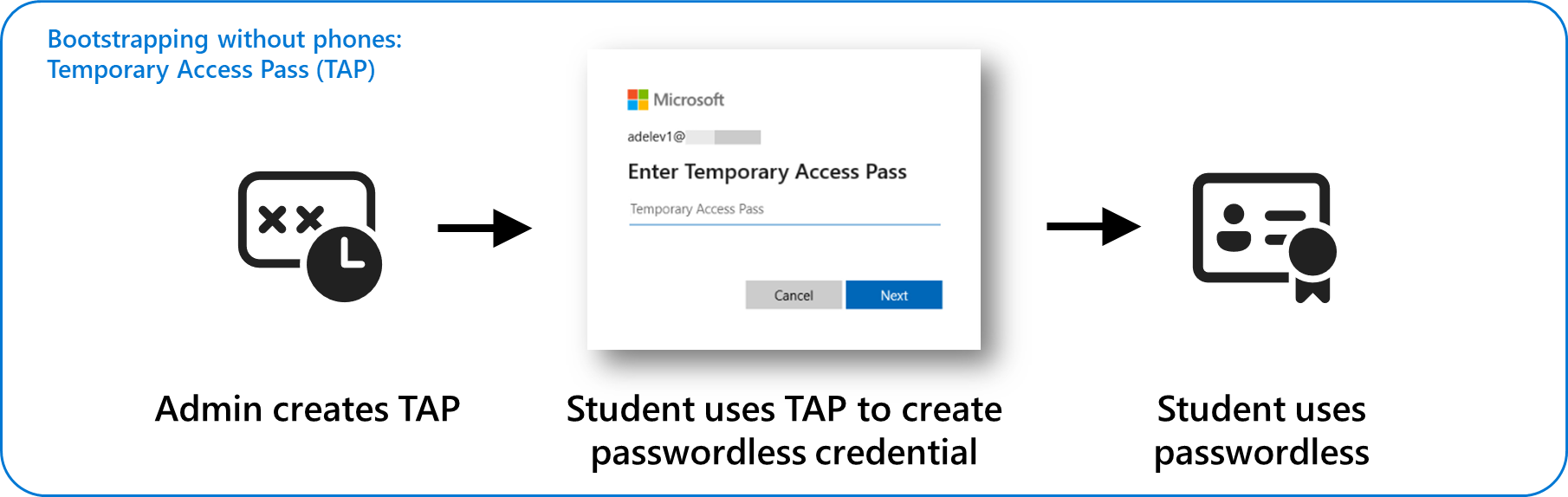
Distributing passwordless phishing resistant credentials to students has been challenging due to the multifactor authentication (MFA) requirement for setup (sometimes referred to as bootstrapping). Temporary Access Pass (TAP) provides a phone free option for users to set up credentials, including device-bound passwordless credentials.
A Temporary Access Pass is a time-limited passcode that can be configured for single or multiple use. Users can sign in with a TAP to onboard other passwordless authentication methods, such as Microsoft Authenticator, FIDO2, Windows Hello for Business, Platform single sign-on (SSO) with Secure Enclave, and Passkeys.
Administrators can create a TAP and distribute to students. Students can use the TAP to create the passwordless credential. Students can then use the passworldess credential to sign in to the device.
Each operating system has a different implementation for device-bound passwordless credentials:
| Operating system | Hardware bound key technology | Suitable for | Hardware requirement | Biometric information |
|---|---|---|---|---|
| Windows | Windows Hello for Business | 1:1 devices | Trusted Platform Module (TPM) | Windows Hello |
| macOS | Platform SSO with Secure Enclave (preview) | 1:1 devices | Secure Enclave | TouchID |
| iOS | Passkeys with Microsoft Authenticator (preview) | 1:1 devices | iOS 16+ | FaceID |
| Android | Passkeys with Microsoft Authenticator (preview) | 1:1 devices | Android 14+ | OEM-specific |
| Windows, macOS | FIDO2 Security Keys | 1:1 or shared devices | FIDO2 Security Key | Various |
| Passkeys (syncable) - coming later in 2024 | n/a | Not hardware bound – protection varies by passkey provider vendor | n/a | Various |
These technologies provide Phishing-resistant authentication strength because they use a combination of a hardware bound private key, the user's physical possession of that device. The local device PIN or password used to unlock or "release" the device specific private key. The private key never leaves the device or is transmitted over the network. Microsoft Entra ID only possesses a corresponding public key used to validate data signed by the hardware bound private key. The PIN or local password is device specific and can't be used to log into services or other devices (unless the user uses the same PIN).
Tip
For the best passwordless experience on 1:1 devices for K-12 Students and Devices, Microsoft recommends TAP + Windows Hello (or other platform specific hardware bound key technology). For shared devices, Microsoft recommends FIDO2 Security Keys.
For more information about Passwordless and Microsoft Entra ID, see Microsoft Entra passwordless sign-in.
Passwordless user experience
These steps demonstrate the user experience during Autopilot in the following conditions:
- The user has a temporary access pass.
- Windows Hello for Business is enabled for this device.
If the device is already provisioned, the experience is the same from step 2 when the user logs in to a device with Windows Hello for Business enabled.
- Sign in with a work or school account and use the temporary access pass to start Autopilot.
- After provisioning is complete, the user is prompted to configure Windows Hello for Business.
- The user is prompted to enter their temporary access pass.
- The user creates a PIN and sets up biometric credentials if supported by the device.
- The user can now sign in with their PIN or biometrics.
User experience when a user doesn't have a TAP or the TAP is expired
If the user doesn't have a temporary access pass when going through Autopilot, they are prompted to register for multifactor authentication:
If you assign a temporary access pass to a user and ask them to try again or restart the computer, users are prompted to use the temporary access pass instead.
Planning for Passwordless
The main challenge of provisioning passwordless credentials to students is distributing the TAP.
Options include:
- Generating TAP when passwords are provided to students for the first time or providing only a TAP and no password to enforce passwordless.
- Generating and distributing a TAP when students receive new devices.
- Enabling the passwordless authentication options and asking students to configure them and call IT support to request a TAP when setting it up.
- Delegating access to create TAP to local IT or teachers.
You can use Authentication Methods in Entra to control which users can use specific types of authentication methods. For example, you could allow teachers and staff to use Microsoft Authenticator but only allow students to use Temporary Access Pass.
| Target user attributes | Typical users | Authentication Methods |
|---|---|---|
| Can use iOS or Android devices in addition to their main device | Staff, university students, students in schools where mobile devices are allowed | ✔️ Microsoft Authenticator ✔️ Temporary Access Pass ✔️ FIDO2 Security Key ✔️ Passkeys |
| No mobile device access | K-12 students | ✔️ Temporary Access Pass ✔️ FIDO2 Security Key ✔️ Passkeys |
For more information about the authentication methods available in Entra, see Authentication Methods.
Configure Authentication Methods
Configure Entra to use Authentication Methods policies
Authentication methods can be configured after multifactor authentication and self-service password reset policy settings are migrated to the Authentication Methods functionality. For more information, see How to migrate MFA and Self Service Password Reset policy settings to the Authentication methods policy for Microsoft Entra ID.
Configure the authentication methods based on your requirements
Use Authentication Methods to target the required configuration at groups of users. For more information, see Authentication Methods. For example:
- Change the target groups for Phone, SMS, Microsoft Authenticator methods to include staff and exclude students.
- Change the target group of Temporary Access Pass to include students.
Issue Temporary Access Pass
Administrators can issue Temporary access passes and distribute them to users. For more information, see Create a temporary access pass.
Configure Devices
Configure the passwordless sign in method for each operating system to meet your requirements.
For Intune-managed devices, there are two methods for configuring Windows Hello for Business:
- Tenant-wide. The tenant wide Windows Hello for Business policies in Devices > Windows > Windows Enrollment > Windows Hello for Business. It's typical for schools to disable Windows Hello for Business to avoid students being asked to set up multifactor authentication during sign in.
- Targeted using policies. Targeted policies take precedence over the tenant-wide policy, allowing settings to be targeted at groups or to stage the rollout.
For more information, see Configure Windows Hello for Business.
Additional steps are required to configure single sign-on access to on premises resources with Windows Hello for Business credentials. For more information, see Configure single sign-on for Microsoft Entra joined devices.
Customize the Windows Hello for Business experience
These settings are optional but can be used to customize the Windows Hello for Business experience.
DisablePostLogonProvisioning – By default Windows Hello for Business requires provisioning during sign-in. With this setting enabled, the sign-in prompt is disabled. Users can configure Windows Hello for Business in the settings app.
Configuration Value OMA-URI: ./Device/Vendor/MSFT/PassportForWork/**Microsoft Entra ID Tenant ID**/Policies/DisablePostLogonProvisioningData type: Boolean Value: True EnablePasswordlessExperience - When the policy is enabled on Windows 11, certain Windows authentication scenarios don't offer users the option to use a password, helping organizations and preparing users to gradually move away from passwords. For more information, see Windows passwordless experience.
Configuration Value OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Authentication/EnablePasswordlessExperienceData type: Integer Value: 1
For steps on creating a custom policy, see Add custom settings for Windows 10/11 devices in Microsoft Intune.
Monitor Passworldess Authentication
Entra includes reports for monitoring authentication methods. For more information, see Authentication Methods Activity.
Use the reports to see your rollout progress and identify when users are using paswordless credentials.
Enforce Authentication Strength with Conditional Access
Access to services that use Microsoft Entra ID for authentication can be restricted based on authentication method strength, among other conditions, using Conditional Access.
For example, to require students access services using Microsoft Entra ID for authentication use a managed device with passwordless credentials, configure a Conditional Access policy with these settings:
| Configuration | Value |
|---|---|
| Name | Students |
| Target | All students |
| Grant | Complaint device: yes Authentication strength: Phishing-resistant |
For more information on authentication strength in conditional access policies, see Overview of Microsoft Entra authentication strength.
For instructions on configuring Conditional Access policies, see What is Conditional Access in Microsoft Entra ID?.
Tip
In scenarios where devices are shared among multiple users, an alternative passwordless authentication option is FIDO 2 security keys. Shared devices could be excluded from conditional access policies based on location however this isn't recommended.
Manage Passwordless Credentials
Passwordless credentials are unaffected by password changes, resets, or policies. If a device is compromised or stolen, you should follow procedures required by your security team. Some examples of actions could include:
- Taking no action until a compromise is investigated.
- Triggering a remote wipe of the compromised device.
- Disabling the credential or user account.
If a device is compromised, you may choose to delete the associated passwordless credential from Microsoft Entra ID to prevent unauthorized use.
To remove an authentication method associated with a user account, delete the key from the user's authentication method. You can identify the associated device in the Detail column.
- Sign in to the Microsoft Entra admin center and search for the user whose passkey needs to be removed.
- Select Authentication methods > next to the relevant authentication method, select the "…" menu and then select Delete.
Next Steps
For more information about enrolling your devices into Intune, go to: