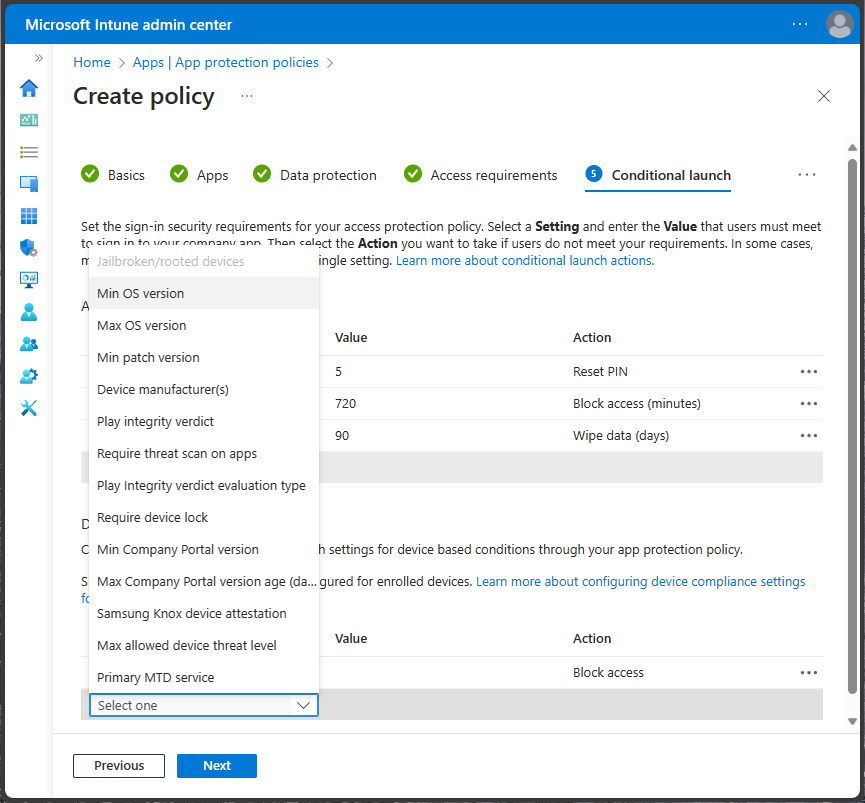
Understand app protection conditional launch
The Conditional launch settings allow you to select the sign-in security requirements for your access protection policy. App protection policies offer both app and device conditions.
You must select a setting and enter the value that users must meet to sign in to your company app. Then select the Action you want to take if users don't meet your requirements. In some cases, multiple actions can be configured for a single setting. Learn more about conditional launch actions.
Conditional launch settings offer similarities between iOS/iPadOS and Android.
Conditional launch for iOS/iPadOS and Android app protection policy
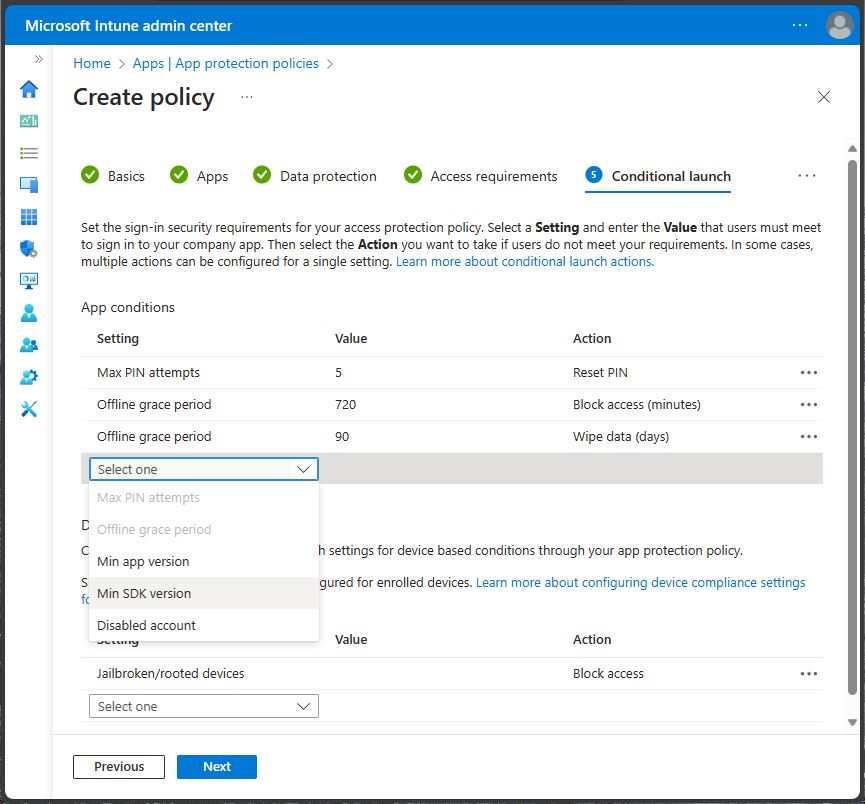
iOS/iPadOS app conditional settings allow the similar settings configuration as Android, however you can also set a Min SDK version for iOS/iPadOS.
| App condition setting | iOS/iPadOS | Android |
|---|---|---|
| Max PIN attempts | ✔ | ✔ |
| Office grace period | ✔ | ✔ |
| Min app version | ✔ | ✔ |
| Max SDK version | ✔ | ✖ |
| Disabled account | ✔ | ✔ |
In addition, Android device condition settings offer several more setting configuration options compared to iOS/iPadOS.
| Device condition setting | iOS/iPadOS | Android |
|---|---|---|
| Jailbroken/rooted devices | ✔ | ✔ |
| Min OS version | ✔ | ✔ |
| Max OS version | ✔ | ✔ |
| Min patch version | ✔ | ✔ |
| Device model(s) | ✔ | ✖ |
| Device manufacturer(s) | ✖ | ✔ |
| SafetyNet device attestation | ✖ | ✔ |
| Require threat scan on apps | ✖ | ✔ |
| Required SafetyNet evaluation type | ✖ | ✔ |
| Require device lock | ✖ | ✔ |
| Min Company Portal version | ✖ | ✔ |
| Max Company Portal version age (days) | ✖ | ✔ |
| Samsung Knox device attestation | ✖ | ✔ |
| Max allowed device threat level | ✔ | ✔ |
| Primary MTD service | ✔ | ✔ |