3.2.4.1 Activate Operation
During the Activate request, the server MAY<34> act as a proxy between the version 1.0 client and the RMS Machine Activation cloud service. The request from the client to the server and the request from the server to the cloud service are identical. Likewise, the response from the cloud service to the server and the response from the server to the client are identical.
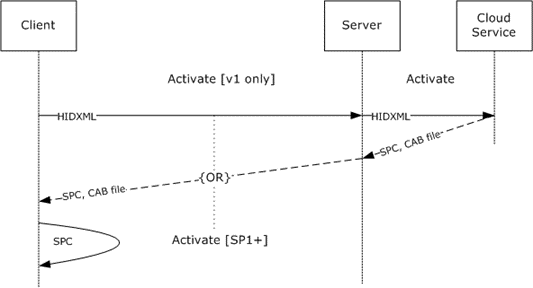
Figure 6: Activation message sequence
-
<wsdl:operation name="Activate"> <wsdl:input message="tns:ActivateSoapIn" /> <wsdl:output message="tns:ActivateSoapOut" /> </wsdl:operation>
The Activate web method response also includes binary data that the server returns verbatim as a DIME attachment to the SOAP response.
In the Activate operation, the client submits an HID hash (section 3.2.4.1.2.3) and requests a security processor software component, signature, and SPC chain. A properly formed Activate request MUST contain a HID hash. The server treats this HID hash as an opaque BLOB and forwards it to the RMS Machine Activation cloud service.
In addition to returning an ActivateResponse element, the response method SHOULD also return a binary attachment using DIME, as specified in [WSDLExt]). The DIME attachment is treated as an opaque BLOB by the server and forwarded from the RMS Machine Activation cloud service back to the client.
The server's role in the Activate request is to act only as a proxy to the RMS Machine Activation cloud service. This functionality exists to enable clients that do not have connectivity to the Internet beyond the corporate environment. The Activate protocol between the server and the RMS Machine Activation cloud service is identical to the Activate protocol between the client and the server.
Upon receiving an Activate request, the server SHOULD service the request. To service the request, the server MUST make an Activate request to the RMS Machine Activation cloud service using the same Activate protocol and the same request data. When the cloud service responds, the server MUST respond to the client with the same response data. The server MUST treat the request and response data as opaque BLOBs and pass the response data through to the client. A successful response includes an SPC chain, a security processor binary file containing the security processor private key, and a signature of the binary file.
After the activation step is complete, the client has a security processor with its own key pair and SPC chain.
For a successful request, the server MUST return exactly what it receives from the RMS Machine Activation cloud service. For an unsuccessful request, the server SHOULD return the same fault as the cloud service.