Use Kerberos for single sign-on (SSO) to SAP BW using gx64krb5
This article describes how to configure your SAP Business Warehouse (BW) data source to enable single sign-on (SSO) from the Power BI service by using gx64krb5.
Important
Microsoft will allow you to create connections using Secure Network Communications (SNC) libraries (like gx64krb5) but will not provide support for these configurations. Additionally SAP no longer supports the gx64krb5 for on-premises data gateways in Power BI and the steps required to configure it for the gateway are significantly more complex compared to CommonCryptoLib. As a result, Microsoft recommends using CommonCryptoLib instead. For more information, see SAP Note 352295. Note that gx64krb5 doesn't allow for SSO connections from the data gateway to SAP BW Message Servers; only connections to SAP BW Application Servers are possible. This restriction doesn't exist if you use CommonCryptoLib as your SNC library. For information about how to configure SSO by using CommonCryptoLib, see Configure SAP BW for SSO using CommonCryptoLib. Use CommonCryptoLib or gx64krb5 as your SNC library, but not both. Do not complete the configuration steps for both libraries.
Note
Configuring both libraries(sapcrypto and gx64krb5) on the same gateway server is an unsupported scenario. It’s not recommended to configure both libraries on the same gateway server as it’ll lead to a mix of libraries. If you want to use both libraries, please fully separate the gateway server. For example, configure gx64krb5 for server A then sapcrypto for server B. Please remember that any failure on server A which uses gx64krb5 is not supported, as gx64krb5 is no longer supported by SAP and Microsoft.
This guide is comprehensive; if you've already completed some of the described steps, you can skip them. For example, you might have already configured your SAP BW server for SSO using gx64krb5.
Set up gx64krb5 on the gateway machine and the SAP BW server
The gx64krb5 library must be used by both the client and server to complete an SSO connection through the gateway. That is, both the client and server must be using the same SNC library.
Download gx64krb5.dll from SAP Note 2115486 (SAP s-user required). Ensure you have at least version 1.0.11.x. Also, download gsskrb5.dll (the 32-bit version of the library) if you want to test the SSO connection in SAP GUI before you attempt the SSO connection through the gateway (recommended). The 32-bit version is required to test with SAP GUI because SAP GUI is 32-bit only.
Put gx64krb5.dll in a location on your gateway machine that's accessible by your gateway service user. If you want to test the SSO connection with SAP GUI, also put a copy of gsskrb5.dll on your machine and set the SNC_LIB environment variable to point to it. Both the gateway service user and the Active Directory (AD) users that the service user will impersonate need read and execute permissions for the copy of gx64krb5.dll. We recommend granting permissions on the .dll to the Authenticated Users group. For testing purposes, you can also explicitly grant these permissions to both the gateway service user and the AD user you use to test.
If your BW server hasn't already been configured for SSO using gx64krb5.dll, put another copy of the .dll on your SAP BW server machine in a location accessible by the SAP BW server.
For more information on configuring gx64krb5.dll for use with an SAP BW server, see SAP documentation (SAP s-user required).
On the client and server machines, set the SNC_LIB and SNC_LIB_64 environment variables:
- If you use gsskrb5.dll, set the SNC_LIB variable to its absolute path.
- If you use gx64krb5.dll, set the SNC_LIB_64 variable to its absolute path.
Configure an SAP BW service user and enable SNC communication on the BW server
Complete this section if you haven't already configured your SAP BW server for SNC communication (for example, SSO) by using gx64krb5.
Note
This section assumes that you've already created a service user for BW and bound a suitable SPN to it (that is, a name that begins with SAP/).
Give the service user access to your SAP BW Application Server:
On the SAP BW server machine, add the service user to the Local Admin group. Open the Computer Management program and identify the Local Admin group for your server.
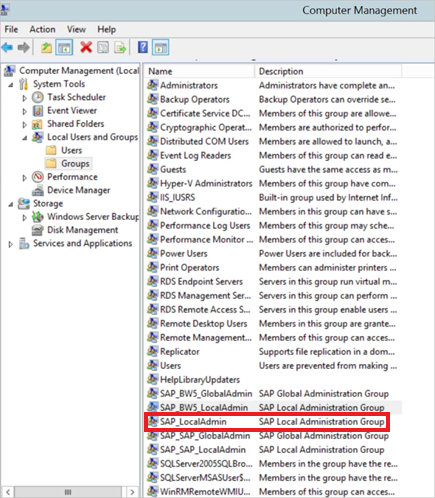
Double-click the Local Admin group, then select Add to add your service user to the group.
Select Check Names to ensure you've entered the name correctly, and then select OK.
Set the SAP BW server's service user as the user that starts the SAP BW server service on the SAP BW server machine:
Open Run, and then enter Services.msc.
Find the service corresponding to your SAP BW Application Server instance, right-click it, and then select Properties.
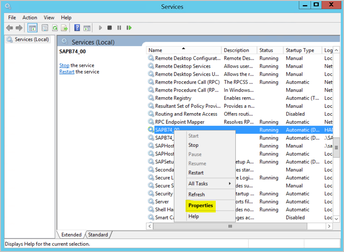
Switch to the Log on tab and change the user to your SAP BW service user.
Enter the user's password, then select OK.
In SAP Logon, sign in to your server and set the following profile parameters by using the RZ10 transaction:
Set the snc/identity/as profile parameter to p:<SAP BW service user you created>. For example, p:BWServiceUser@MYDOMAIN.COM. Note that p: precedes the service user's user principal name (UPN), as opposed to p:CN=, which precedes the UPN when you use CommonCryptoLib as the SNC library.
Set the snc/gssapi_lib profile parameter to <path to gx64krb5.dll on the BW server>. Place the library in a location that the SAP BW Application Server can access.
Set the following additional profile parameters, changing the values as required to fit your needs. The last five options enable clients to connect to the SAP BW server by using SAP Logon without having SNC configured.
Setting Value snc/data_protection/max 3 snc/data_protection/min 1 snc/data_protection/use 9 snc/accept_insecure_cpic 1 snc/accept_insecure_gui 1 snc/accept_insecure_r3int_rfc 1 snc/accept_insecure_rfc 1 snc/permit_insecure_start 1 Set the snc/enable property to 1.
After you set these profile parameters, open the SAP Management Console on the server machine and restart the SAP BW instance.
If the server won't start, confirm that you've set the profile parameters correctly. For more information on profile parameter settings, see the SAP documentation. You can also consult the Troubleshooting section in this article.
Map an SAP BW user to an Active Directory user
If you haven't done so already, map an AD user to an SAP BW Application Server user and test the SSO connection in SAP Logon.
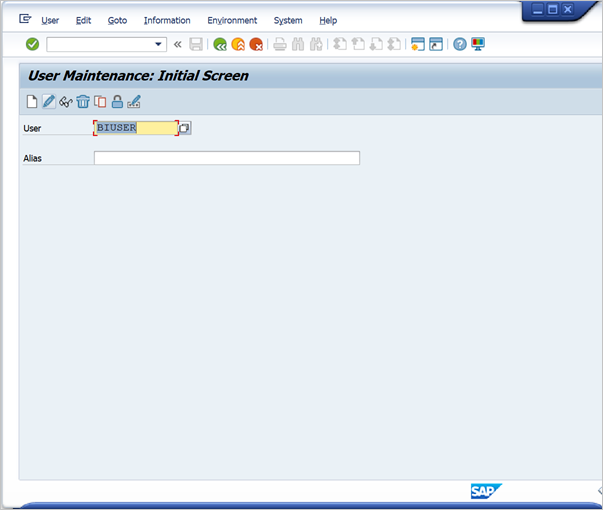
Sign in to your SAP BW server with SAP Logon. Run transaction SU01.
For User, enter the SAP BW user for which you want to enable SSO connection. Select the Edit icon (pen icon) near the top left of the SAP Logon window.
Select the SNC tab. In the SNC name input box, enter p:<your Active Directory user>@<your domain>. For the SNC name, p: must precede the AD user's UPN. Note that the UPN is case-sensitive.
The AD user you specify should belong to the person or organization for whom you want to enable SSO access to the SAP BW Application Server. For example, if you want to enable SSO access for the user testuser@TESTDOMAIN.COM, enter p:testuser@TESTDOMAIN.COM.
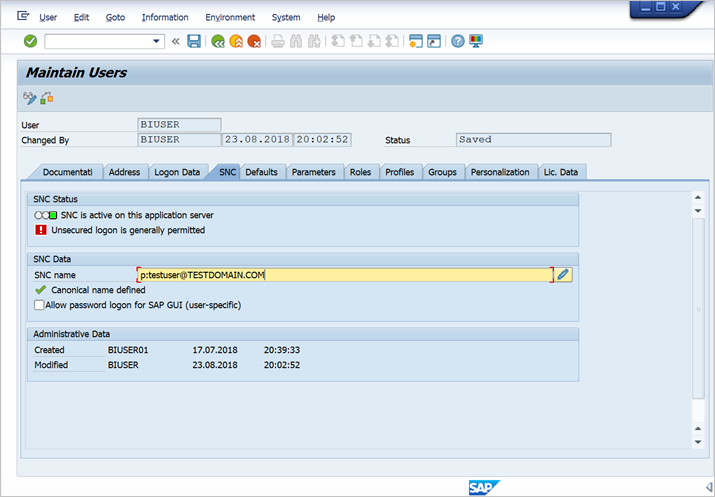
Select the Save icon (floppy disk image) near the top left of the screen.
Test sign in via SSO
Verify that you can sign in to the server by using SAP Logon through SSO as the AD user for whom you've enabled SSO access:
As the AD user for which you've just enabled SSO access, sign in to a machine in your domain on which SAP Logon is installed. Launch SAP Logon, and create a new connection.
Copy the gsskrb5.dll file you downloaded earlier to a location on the machine you signed in to. Set the SNC_LIB environment variable to the absolute path of this location.
Launch SAP Logon and create a new connection.
In the Create New System Entry screen, select User Specified System, then select Next.
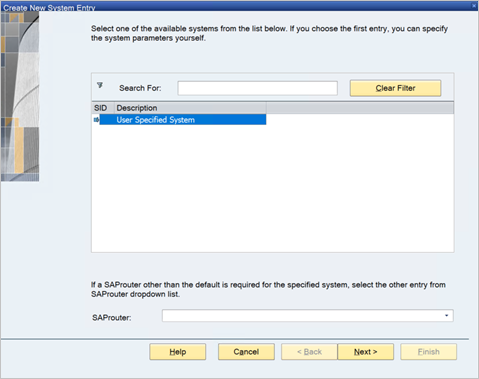
Fill in the appropriate details on the next screen, including the application server, instance number, and system ID. Then, select Finish.
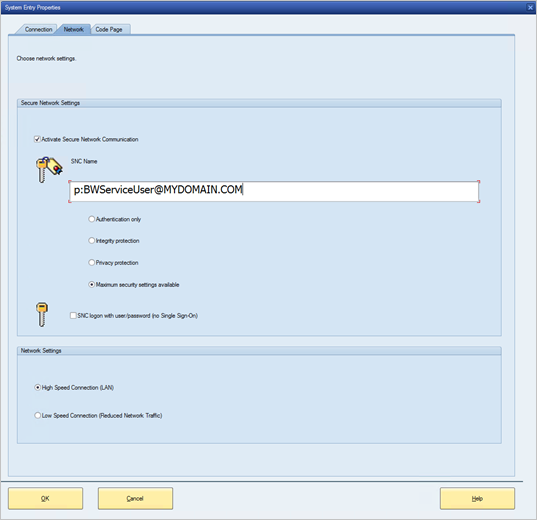
Right-click the new connection, select Properties, and then select the Network tab.
In the SNC Name box, enter p:<SAP BW service user's UPN>. For example, p:BWServiceUser@MYDOMAIN.COM. Select OK.
Double-click the connection you just created to attempt an SSO connection to your SAP BW server.
If this connection succeeds, continue to the next section. Otherwise, review the earlier steps in this document to make sure they've been completed correctly, or review the Troubleshooting section. If you can't connect to the SAP BW server via SSO in this context, you won't be able to connect to the SAP BW server by using SSO in the gateway context.
Add registry entries to the gateway machine
Add required registry entries to the registry of the machine that the gateway is installed on, and to machines intended to connect from Power BI Desktop. To add these registry entries, run the following commands:
REG ADD HKLM\SOFTWARE\Wow6432Node\SAP\gsskrb5 /v ForceIniCredOK /t REG_DWORD /d 1 /fREG ADD HKLM\SOFTWARE\SAP\gsskrb5 /v ForceIniCredOK /t REG_DWORD /d 1 /f
Add a new SAP BW Application Server data source to the Power BI service, or edit an existing one
In the data source configuration window, enter the SAP BW Application Server's Hostname, System Number, and client ID, as you would to sign in to your SAP BW server from Power BI Desktop.
In the SNC Partner Name field, enter p:<SPN you mapped to your SAP BW service user>. For example, if the SPN is SAP/BWServiceUser@MYDOMAIN.COM, enter p:SAP/BWServiceUser@MYDOMAIN.COM in the SNC Partner Name field.
For the SNC Library, select the Custom option and provide the absolute path for GX64KRB5.DLL or GSSKRB5.DLL on the gateway machine.
Select Use SSO via Kerberos for DirectQuery queries, and then select Apply. If the test connection is not successful, verify that the previous setup and configuration steps were completed correctly.
Troubleshooting
Troubleshoot gx64krb5 configuration
If you encounter any of the following problems, follow these steps to troubleshoot the gx64krb5 installation and SSO connections:
You encounter errors when you complete the gx64krb5 setup steps. For example, the SAP BW server won't start after you've changed the profile parameters. View the server logs (…work\dev_w0 on the server machine) to troubleshoot these errors.
You can't start the SAP BW service due to a sign-on failure. You might have provided the wrong password when you set the SAP BW start-as user. Verify the password by signing in as the SAP BW service user on a machine in your AD environment.
You get errors about underlying data source credentials (for example, SQL Server), which prevent the server from starting. Verify that you've granted the service user access to the SAP BW database.
You get the following message: (GSS-API) specified target is unknown or unreachable. This error usually means you have the wrong SNC name specified. Make sure to use p: only, not p:CN=, to precede the service user's UPN in the client application.
You get the following message: (GSS-API) An invalid name was supplied. Make sure p: is the value of the server's SNC identity profile parameter.
You get the following message: (SNC error) the specified module could not be found. This error is often caused by placing gx64krb5.dll in a location that requires elevated privileges (../administrator rights) to access.
Troubleshoot gateway connectivity issues
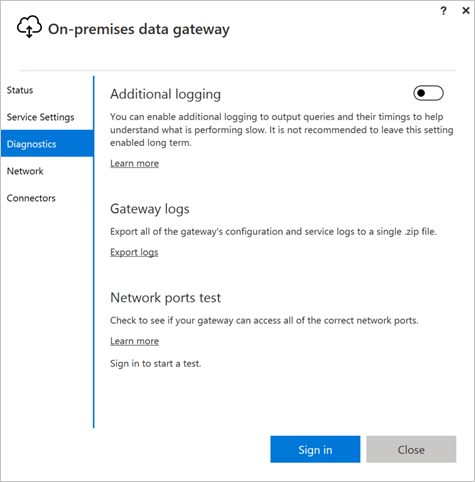
Check the gateway logs. Open the gateway configuration application and select Diagnostics, then Export logs. The most recent errors are at the end of any log files you examine.
Turn on SAP BW tracing and review the generated log files. There are several different types of SAP BW tracing available (for example, CPIC tracing):
a. To enable CPIC tracing, set two environment variables: CPIC_TRACE and CPIC_TRACE_DIR.
The first variable sets the trace level and the second variable sets the trace file directory. The directory must be a location that members of the Authenticated Users group can write to.
b. Set CPIC_TRACE to 3 and CPIC_TRACE_DIR to whichever directory you want the trace files written to. For example:

c. Reproduce the issue and ensure that CPIC_TRACE_DIR contains trace files.
d. Examine the contents of the trace files to determine the blocking issue. For example, you might find that gx64krb5.dll wasn't loaded properly, or that an AD user different than the one you were expecting initiated the SSO connection attempt.
Related content
For more information about the on-premises data gateway and DirectQuery, see the following resources: