Plan for directory synchronization using Microsoft Entra Connect Sync
While Microsoft Entra Connect Sync requires a greater investment to deploy and support than Microsoft Entra Cloud Sync, it's still easy to implement. That being said, organizations must still thoroughly plan their Microsoft Entra Connect Sync implementation. This requirement is especially true if an organization has a complex on-premises Active Directory implementation or special requirements, such as partial attribute synchronization. To start planning, an organization should collect answers to the following questions:
- On what server do you want to install Microsoft Entra Connect Sync?
- Do you require a Microsoft Entra Connect Sync failover scenario?
- Do you want to synchronize one or more Active Directories (or multiple forests)?
- Do you want to synchronize all or only part of your Active Directory?
- Do you want to synchronize all object attributes, or use specific filters?
- Do you want to use advanced configuration features such as password hash synchronization, password writeback, or device writeback?
An organization's decision whether to implement password hash synchronization will affect its next steps. Be mindful of the following considerations:
- Implementing password hash synchronization. Password hash synchronization enables users to authenticate using the same username and password as on-premises. Microsoft Entra Connect Sync synchronizes a user's password hash (a cryptographic hash of the password hash) and stores it in the respective user object in Microsoft Entra ID. Since the password can't be reverse-engineered, organizations can consider it as securely stored.
- Not implementing password hash synchronization. If a company doesn't want its Active Directory password hashes stored outside the company, it must implement either Active Directory Federation Services (AD FS) or Microsoft Entra pass-through authentication to provide single-sign on. Alternatively, organizations can have each user provide with a separate password for their Microsoft Entra account.
Before you install Microsoft Entra Connect Sync
Before an organization installs Microsoft Entra Connect Sync, there are a few preparation tasks that it must complete. The following sections outline these tasks, which validate the hardware and connectivity requirements of Microsoft Entra Connect Sync.
Microsoft Entra ID
To run Microsoft Entra Connect Sync, an organization needs a Microsoft Entra tenant. You can get one with an Azure free trial. You can use either the Microsoft Entra admin portal or the Office portal.to manage Microsoft Entra Connect Sync.
An organization should then add and verify the domain it plans to use in Microsoft Entra ID. For example, if you plan to use contoso.com for your users, ensure you verify this domain and that you're not using just the contoso.onmicrosoft.com default domain.
A Microsoft Entra tenant allows, by default, 50,000 objects. When an organization verifies its domain, the limit increases to 300,000 objects. If it needs even more objects in Microsoft Entra ID, it must open a support case to have the limit increased even further. If it needs more than 500,000 objects, it needs a license, such as Microsoft 365, Microsoft Entra Premium, or Enterprise Mobility + Security.
Prepare your on-premises data
Organizations should consider the following requirements when preparing their on-premises data:
- An organization should use IdFix to identify errors in its on-premises data before it synchronizes to Microsoft Entra ID and Microsoft 365. Typical errors include things such as duplicates and formatting problems in its directory.
- The organization should then review optional sync features it can enable in Microsoft Entra ID, and evaluate which features it should enable.
On-premises Active Directory
Organizations should consider the following requirements when planning their on-premises Active Directory:
- The Active Directory schema version and forest functional level must be Windows Server 2003 or later. The domain controllers can run any version as long as it satisfies the schema version and forest-level requirements. An organization might require a paid support program if it requires support for domain controllers running Windows Server 2016 or older.
- The domain controller used by Microsoft Entra ID must be writable. Microsoft Entra Connect Sync doesn't support a read-only domain controller (RODC), nor does it follow any write redirects.
- Microsoft Entra Connect Sync doesn't support using on-premises forests or domains by using "dotted" NetBIOS names, which are names containings a period.
- Microsoft recommends that organizations enable the Active Directory recycle bin.
PowerShell execution policy
Microsoft Entra Connect Sync runs signed PowerShell scripts as part of the installation. You must ensure the PowerShell execution policy allows running of scripts. The recommended execution policy during installation is "RemoteSigned."
Additional reading. For more information on setting the PowerShell execution policy, see Set-ExecutionPolicy.
Microsoft Entra Connect Sync server
The Microsoft Entra Connect Sync server contains critical identity data. Therefore, it's important that organizations properly secure administrative access to this server. Follow the guidelines in Securing privileged access.
Organizations should treat the Microsoft Entra Connect Sync server as a Tier 0 component as documented in the Active Directory administrative tier model. Microsoft recommends that organizations harden the Microsoft Entra Connect Sync server as a Control Plane asset by following the guidance provided in Secure Privileged Access.
Additional reading. To read more about securing your Active Directory environment, see Best practices for securing Active Directory.
SQL Server used by Microsoft Entra Connect Sync
Microsoft Entra Connect Sync requires a SQL Server database to store identity data. By default, Microsoft Entra Connect Sync installs a SQL Server 2019 Express LocalDB, which is a light version of SQL Server Express.
SQL Server Express has a 10-GB size limit that enables organizations to manage approximately 100,000 objects. If an organization must manage a higher volume of directory objects, it must point the installation wizard to a different installation of SQL Server. The type of SQL Server installation can impact the performance of Microsoft Entra Connect Sync.
If an organization uses a different installation of SQL Server, the following requirements apply:
- Microsoft Entra Connect Sync supports all mainstream supported SQL Server versions up to SQL Server 2019. Refer to the SQL Server lifecycle article to verify the support status of your SQL Server version. Microsoft Entra Connect Sync doesn't support Azure SQL Database and Azure SQL Managed Instance.
- You must use a case-insensitive SQL collation. These collations are identified with a _CI_ in their name. Microsoft Entra Connect doesn't support a case-sensitive collation identified by _CS_ in their name.
- You can have only one sync engine per SQL instance. Microsoft Entra Connect Sync doesn't support sharing a SQL instance with FIM/MIM Sync, DirSync, or Microsoft Entra Sync.
Accounts
An organization must have a Microsoft Entra Global Administrator account or a Hybrid Identity Administrator account for the Microsoft Entra tenant that it wants to integrate with. This account must be a school or organization account. It can't be a Microsoft account.
If an organization uses express settings or upgrades from DirSync, it must have an Enterprise Administrator account for its on-premises Active Directory.
An organization has more options if it uses the custom settings installation path. For more information, see Custom installation settings.
Connectivity
Organizations should consider the following requirements when planning their network connectivity with the Microsoft Entra Connect Sync server:
- The Microsoft Entra Connect Sync server needs DNS resolution for both intranet and internet. The DNS server must be able to resolve names both to your on-premises Active Directory and the Microsoft Entra endpoints.
- Microsoft Entra Connect Sync requires network connectivity to all configured domains.
- Microsoft Entra Connect Sync requires network connectivity to the root domain of all configured forest.
- If an organization limits the URLs its proxy or firewall can access, it must open the URLs documented in Office 365 URLs and IP address ranges. Also see Safelist the Azure portal URLs on your firewall or proxy server.
- Microsoft Entra Connect Sync (version 1.1.614.0 and after) by default uses TLS 1.2 for encrypting communication between the sync engine and Microsoft Entra ID. If TLS 1.2 isn't available on the underlying operating system, Microsoft Entra Connect Sync incrementally falls back to older protocols (TLS 1.1 and TLS 1.0). From Microsoft Entra Connect Sync version 2.0 onwards. Microsoft Entra Connect Sync doesn't support TLS 1.0 and 1.1. A Microsoft Entra Connect Sync installation fails if TLS 1.2 isn't enabled.
- Prior to version 1.1.614.0, Microsoft Entra Connect Sync by default uses TLS 1.0 for encrypting communication between the sync engine and Microsoft Entra. To change to TLS 1.2, follow the steps in Enable TLS 1.2 for Microsoft Entra Connect Sync.
Additional reading. For more information, see Microsoft Entra Connect Sync ports if you have firewalls on your intranet and you need to open ports between the Microsoft Entra Connect Sync servers and your domain controllers. If you're using the Microsoft cloud in Germany or the Microsoft Azure Government cloud, see Microsoft Entra Connect Sync sync service instances considerations for URLs.
Outbound proxy server requirements
This section only applies when an organization uses an outbound proxy for connecting to the internet.
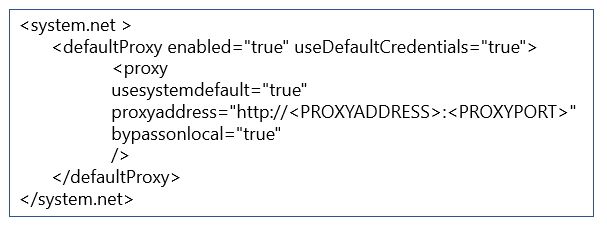
In this scenario, the organization must add the following setting in the C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\machine.config file. The installation wizard and Microsoft Entra Connect Sync requires this setting to connect to the internet and Microsoft Entra ID. The organization must enter this text at the bottom of the file. In this code, <PROXYADDRESS> represents the actual proxy IP address or host name.

If an organization's proxy server requires authentication, its domain must include the service account. To specify a custom service account, an organization must use the customized settings installation path.
The organization also needs a different change to the machine.config file so that the installation wizard and sync engine respond to authentication requests from the proxy server. All installation wizard pages, excluding the Configure page, use the signed-in user's credentials. On the Configure page at the end of the installation wizard, the context switches to the service account that you created. The machine.config section should look like this:
If an existing setup is performing the proxy configuration, you must restart the Microsoft Entra Sync service for Microsoft Entra Connect Sync to read the proxy configuration and update the behavior.
Warning
When Microsoft Entra Connect Sync sends a web request to Microsoft Entra ID as part of directory synchronization, Microsoft Entra ID can take up to 5 minutes to respond. It's common for proxy servers to have a connection idle timeout configuration. As such, it's important that you verify the configuration, and if necessary, adjust the connection idle timeout setting to at least 6 minutes or more. Administrators typically become aware of a connection idle timeout issue through the observation of symptoms such as failed or delayed directory synchronization. They may notice that the synchronization process takes longer than expected or encounters errors during the sync operation. To investigate and identify the cause of such issues, administrators would typically review logs and monitoring tools related to Microsoft Entra Connect Sync, the proxy server, or any associated network infrastructure. These logs might indicate connection timeouts or failures that could point to a connection idle timeout problem.
Additional reading. For more information, see MSDN about the default proxy element. For more information when you have problems with connectivity, see Troubleshoot connectivity problems.
Hardware requirements for Microsoft Entra Connect Sync
The following table shows the minimum requirements for the Microsoft Entra Connect Sync server.
| Number of objects in Active Directory | CPU | Memory | Hard drive size |
|---|---|---|---|
| Fewer than 10,000 | 1.6 GHz | 4 GB | 70 GB |
| 10,000–50,000 | 1.6 GHz | 4 GB | 70 GB |
| 50,000–100,000 | 1.6 GHz | 16 GB | 100 GB |
| For 100,000 or more objects, the full version of SQL Server is required. For performance reasons, installing locally is preferred. | |||
| 100,000–300,000 | 1.6 GHz | 32 GB | 300 GB |
| 300,000–600,000 | 1.6 GHz | 32 GB | 450 GB |
| More than 600,000 | 1.6 GHz | 32 GB | 500 GB |
The minimum requirements for computers running AD FS or Web Application Proxy servers are:
- CPU. Dual core 1.6 GHz or higher.
- Memory. 2 GB or higher.
- Azure VM. A2 configuration or higher.
Knowledge check
Choose the best response for the following question.