Encrypt existing VM disks
Suppose your company decides to implement Azure Disk Encryption (ADE) across all virtual machines. You need to evaluate how to roll out encryption to existing virtual machine (VM) volumes. Here, we look at the requirements for ADE, and the steps involved in encrypting disks on existing Linux and Windows VMs. In the next unit, you work through the process of encrypting existing VM disks.
Azure Disk Encryption prerequisites
Before you can encrypt your VM disks, you need to:
- Create a key vault.
- Set the key vault access policy to support disk encryption.
- Use the key vault to store the encryption keys for ADE.
Azure Key Vault
The encryption keys ADE uses can be stored in Azure Key Vault. Azure Key Vault is a tool for securely storing and accessing secrets. A secret is anything to which you want to tightly control access, such as API keys, passwords, or certificates. Azure Key Vault provides highly available and scalable secure storage, as defined in Federal Information Processing Standards (FIPS) 140-2 Level 2 validated Hardware Security Modules (HSMs). Using Key Vault, you keep full control of the keys used to encrypt your data, and you can manage and audit your key usage.
Note
Azure Disk Encryption requires that your key vault and your VMs are in the same Azure region; this ensures that encryption secrets do not cross regional boundaries.
You can configure and manage your key vault with:
PowerShell
New-AzKeyVault -Location <location> `
-ResourceGroupName <resource-group> `
-VaultName "myKeyVault" `
-EnabledForDiskEncryption
Azure CLI
az keyvault create \
--name "myKeyVault" \
--resource-group <resource-group> \
--location <location> \
--enabled-for-disk-encryption True
Azure portal
An Azure Key Vault is a resource that you can create in the Azure portal using the normal resource creation process.
On the Azure portal menu or from the Home page, select Create a resource.
In the search box, search for and select Key Vault. The Key Vault pane appears.
Select Create. The Create a key vault pane appears.
On the Basics tab, enter the following values for each setting.
Setting Value Project details Subscription Select the subscription in which to place the key vault (defaults to your current subscription). Resource group Select an existing resource group or create a new one. Instance details Key vault name Enter a name for your key vault. Region Select the region in which your VM resides. Pricing tier Standard. You can select either Standard or Premium for the pricing tier. The main difference is that the Premium tier allows for hardware encryption-backed keys. 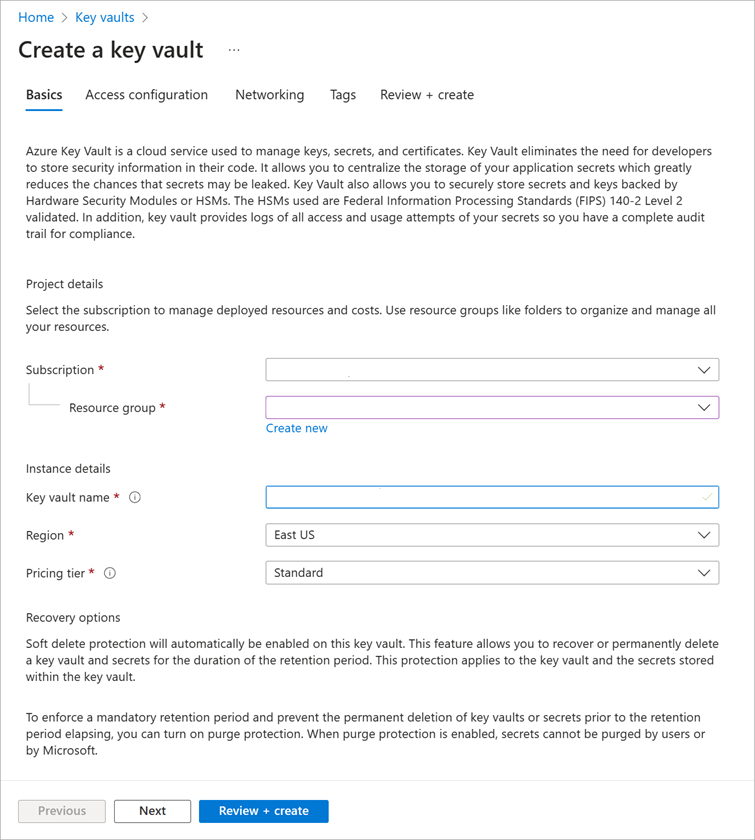
Select Next to move to the Access configuration tab. You must change the Access policies to support Disk Encryption. By default, it adds your account to the policy.
On the Access configuration tab, enter the following value for the setting.
Setting Value Resource access Check the box for Azure Disk Encryption for volume encryption. You can remove your account if you like, as it's not necessary if you only intend to use the key vault for disk encryption. Select Review + create.
After validation passes, to create the new Key Vault, select Create.
Enable access policies in the key vault
Azure needs access to the encryption keys or secrets in your key vault to make them available to the VM for booting and decrypting the volumes. You enabled this access in the preceding steps when you changed the Access policy.
There are three policies you can enable:
- Disk encryption: Required for Azure Disk encryption.
- Deployment: (Optional) Enables the
Microsoft.Computeresource provider to retrieve secrets from this key vault when this key vault is referenced in resource creation. For example, when creating a VM. - Template deployment: (Optional) Enables Azure Resource Manager to get secrets from this key vault when this key vault is referenced in a template deployment.
Here's how to enable the disk encryption policy. The other two policies are similar but use different flags.
Set-AzKeyVaultAccessPolicy -VaultName <keyvault-name> -ResourceGroupName <resource-group> -EnabledForDiskEncryption
az keyvault update --name <keyvault-name> --resource-group <resource-group> --enabled-for-disk-encryption true
Encrypt an existing VM disk
After you have the key vault set up, you can encrypt the VM using either Azure CLI or Azure PowerShell. The first time you encrypt a Windows VM, you can choose to encrypt either all disks or the OS disk only. On some Linux distributions, only the data disks can be encrypted. To be eligible for encryption, your Windows disks must be formatted as New Technology File System (NTFS) volumes.
Warning
Before you can turn on encryption, you must take a snapshot or a backup of managed disks. The following SkipVmBackup flag informs the tool that the backup is complete on managed disks. Without the backup, you're unable to recover the VM if the encryption fails for some reason.
To enable encryption by using PowerShell, run the Set-AzVmDiskEncryptionExtension cmdlet.
Set-AzVmDiskEncryptionExtension `
-ResourceGroupName <resource-group> `
-VMName <vm-name> `
-VolumeType [All | OS | Data]
-DiskEncryptionKeyVaultId <keyVault.ResourceId> `
-DiskEncryptionKeyVaultUrl <keyVault.VaultUri> `
-SkipVmBackup
To enable encryption by using the Azure CLI, run the az vm encryption enable command and specify the volume you want to encrypt using the --volume-type [all | os | data] parameter. Here's an example of encrypting all volumes for a virtual machine:
az vm encryption enable \
--resource-group <resource-group> \
--name <vm-name> \
--disk-encryption-keyvault <keyvault-name> \
--volume-type all
View status of disk
You can check whether specific disks are encrypted.
Get-AzVmDiskEncryptionStatus -ResourceGroupName <resource-group> -VMName <vm-name>
az vm encryption show --resource-group <resource-group> --name <vm-name>
Both of these commands return the status of each disk attached to the specified VM.
Decrypt drives
To reverse the encryption through PowerShell, run the Disable-AzVMDiskEncryption cmdlet.
Disable-AzVMDiskEncryption -ResourceGroupName <resource-group> -VMName <vm-name>
For the Azure CLI, run the vm encryption disable command.
az vm encryption disable --resource-group <resource-group> --name <vm-name>
These commands disable encryption for volumes of type all for the specified VM. Just like the encryption version, to decide what disks to decrypt, you can specify a -VolumeType parameter [All | OS | Data]. It defaults to All if not supplied.
Warning
Disabling data disk encryption on Windows VM when both OS and data disks have been encrypted doesn't work as expected. You must disable encryption on all disks instead.
In the next exercise, you try some of these commands out on a new VM.