Azure network connection domain credential life cycle
When you create an Azure network connection (ANC) using a Microsoft Entra hybrid join type, you must include on-premises domain credential information. This requirement makes it possible for the ANC to communicate with your on-premises resources.
This article describes how Windows 365 protects and manages the on-premises domain credentials during the whole Microsoft Entra hybrid join ANC life cycle:
- Providing credentials
- Encrypting credentials
- Updating credentials
- Removing credentials
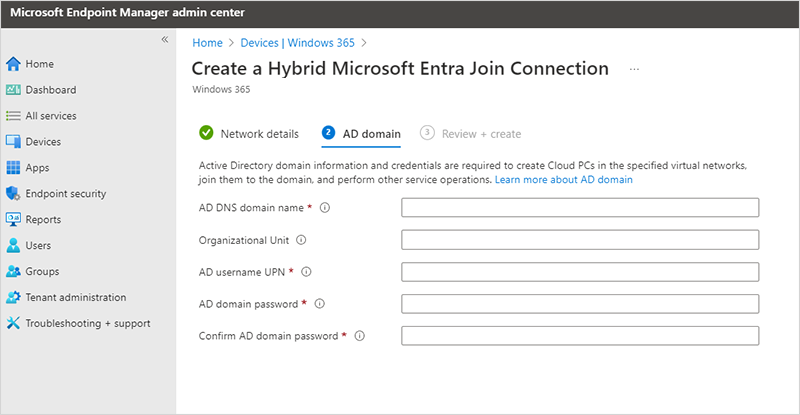
Provide Microsoft Entra domain credentials
When you create an ANC, you must provide credentials of an on-premises Active Directory user account that will be used to domain join Cloud PCs. You provide this information, including the on-premises user account's username and domain password, on the AD domain page:
Encryption of domain password information
When an ANC is created, information associated with it is stored in the Windows 365 service. The Windows 365 service encrypts the domain password information with a well-protected key before saving it. Encryption details include:
- Encryption type: Azure Key Vault certificate
- Key type: RSA-HSM
- Algorithm: RSAOAEP256
The automated encryption steps proceed as follows:
- The Windows 365 service checks the service for an existing symmetric key specific to that tenant.
- If a key isn't present or has expired, Windows 365 generates a new symmetric key for this tenant using a random number generator. Keys are created per tenant.
- If a key already exists for this tenant, it's used in the following steps.
- After getting the (new or existing) tenant key, Windows 365 decrypts the key with the Windows 365 dedicated Enterprise CA issued certificate.
- This certificate is stored in the Azure Key Vault instance managed by Microsoft.
- Windows 365 service encrypts the password with the decrypted tenant key.
- The encrypted password is saved to the Windows 365 service.
Windows 365 Enterprise certificates
Windows 365 service enterprise certificates are generated and renewed automatically by the Azure Key Vault. This certificate expires after one year. The Windows 365 service regularly checks the status of the certificate. Three months before the expiration date, the Windows 365 service automatically regenerates a new certificate. After the new certificate is generated, it's used by the Windows 365 service to re-encrypt the tenant keys.
Password encryption/decryption algorithm
Windows 365 uses an encrypt-then-MAC approach to encrypt the domain credential with the per tenant key as described in RFC 7366. The same key is used for both encrypting and decrypting the data.
Encryption algorithm details include:
- Encrypt algorithm: Advanced Encryption Standard symmetric-key
- Cipher mode: Cipher-Block-Chaining
- Key length: 256 bit
- Key valid period: 12 months
- Authentication algorithm: HMACSHA256
Updating credential information
Credentials often change and need updating. Windows 365 doesn’t proactively detect credential changes of the on-premises Active Directory user account associated with ANC. Instead, Windows 365 relies on customers to manually update the ANC with the updated credential information.
When there’s a change to the domain credential of the user account associated with an ANC, the new credential should be manually updated by the Windows 365 administrator. The new credential is then automatically re-encrypted and updated in the Windows 365 service.
Note
If the domain credential is changed in your on-premises Active Directory environment, but you don’t manually update the ANC, Windows 365 will still use the old credential for ANC health checks. Therefore, these health checks will fail because the credentials on record are no longer valid. To make sure such failures don’t happen, update the Azure network connection configuration with the new credentials immediately.
Removing credential information
After you delete an ANC, all the data related to the ANC is immediately and permanently removed from the Windows 365 service.
If the tenant account is deactivated without deleting the ANC, the credential information is retained for 29 days. If the tenant is reactivated within 29 days, the ANC and domain credentials are restored. If the tenant isn't reactivated in 29 days, all ANCs and related information, including credentials, are permanently removed.