Protecting you from malware
One of the things we talk quite a bit about with Windows 8 is making sure Windows is a safe, secure, and reliable computing environment. We have always provided a broad range of solutions for achieving these goals and work closely with a broad range of industry partners. We continue to enhance these capabilities with Windows 8 while making sure you always have choice and control over how to protect and manage your PC. With Windows 8 we are extending the protections provided by Defender to address a broader range of potential threats. Jason Garms, the group program manager of our reliability and security team authored this post that represents work across several teams. --Steven
I’m excited to share with you some investments we are making in Windows 8 to better protect you against the constantly changing landscape of malicious software (“malware”). In this blog I will talk about enhancements to mitigation features that help protect you against exploits used by malware, improvements to Windows Defender to provide you with real-time protection from all categories of malware, and the use of URL and application reputation to help protect you against social engineering attacks.
A view of the current landscape
Criminal attacks continue to evolve and malware has become their standard weapon against anyone who uses the Internet—on traditional form-factor devices, as well as on mobile devices like tablets and phones. Malware targets all operating systems and browsers, and in recent years, criminal attacks against applications have increased substantially.
Criminals also use social engineering to trick you into performing actions that put you at risk. An increasingly common social engineering strategy uses online advertising campaigns to lure you to a site that installs malware on your computer.
An economy has developed around building reliable vulnerability exploits, which criminals buy to help distribute their malware. Criminals make money from their malware, so they invest in ways to keep it alive such as producing a higher quantity of malware, updating it more frequently—e.g. multiples times each day—and increasing its size and complexity. Some malware is as complex as commercial applications.
Secure by design
We use the Security Development Lifecycle (SDL) to build Windows with the best security design, development and testing practices available. Some highlights include:
- Threat modeling and security design reviews. During the design process we consider how criminals might seek to attack features and scenarios, and incorporate this analysis into our designs.
- Writing secure code. Training and code quality tools help to prevent common coding issues from entering the Windows source code.
- Penetration testing. Security engineers take an attacker’s perspective when reviewing a completed set of features that make up a scenario.
- Security code reviews. Security engineers provide additional security-oriented code reviews for highly sensitive components.
- Security tools. Tools continuously updated with the latest state of the art in finding and exploiting software provide a scalable solution to improve existing code.
Making it harder to create an exploit on Windows 8
With Windows XP SP2, we began creating defenses called mitigations that make it difficult to develop reliable exploits for security vulnerabilities. Each subsequent version of Windows has continued to expand and improve on these mitigations, because a single mitigation feature can break an entire class of exploits. Windows 8 includes mitigation enhancements that further reduce the likelihood of common attacks. Some of these improvements include:
- Address Space Layout Randomization (ASLR). ASLR was first introduced in Windows Vista and works by randomly shuffling the location of most code and data in memory to block assumptions that the code and data are at same address on all PCs. In Windows 8, we extended ASLR’s protection to more parts of Windows and introduced enhancements such as increased randomization that will break many known techniques for circumventing ASLR.
- Windows kernel. In Windows 8, we bring many of the mitigations to the Windows kernel that previously only applied to user-mode applications. These will help improve protection against some of the most common type of threats. For example, we now prevent user-mode processes from allocating the low 64K of process memory, which prevents a whole class of kernel-mode NULL dereference vulnerabilities from being exploited. We also added integrity checks to the kernel pool memory allocator to mitigate kernel pool corruption attacks.
- Windows heap. Applications get dynamically allocated memory from the Windows user-mode heap. Major redesign of the Windows 8 heap adds significant protection in the form of new integrity checks to help defend against many exploit techniques. In addition, the Windows heap now randomizes the order of allocations so that exploits cannot depend on the predictable placement of objects—the same principle that makes ASLR successful. We also added guard pages to certain types of heap allocations, which helps prevent exploits that rely on overrunning the heap.
- Internet Explorer. “Use-after-free” vulnerabilities represented nearly 75% of the vulnerabilities reported in Internet Explorer over the last two years. For Windows 8, we implemented guards in Internet Explorer to prevent an attacker from crafting an invalid virtual function table, making these attacks more difficult. Internet Explorer will also take full advantage of the ASLR improvements provided by Windows 8.
Keeping malware off your PC
Having effective malware protection is important for any device connected to the Internet and almost all Windows PCs sold today include a traditional antimalware solution, though it is often a time-limited or trial version.
Shortly after Windows 7 general availability in October 2009, our telemetry data showed nearly all Windows 7 PCs had up-to-date antimalware software. However, a few months later the trend started to decline month-to-month, likely reflecting antimalware trial subscriptions expiring. A year later, at least 24% of Windows 7 PCs did not have current antimalware protection. Our data also shows that PCs that become unprotected tend to stay in this unprotected state for long periods of time. And when antimalware software is even one week out of date, its ability to protect against new malware drops significantly.
We believe that all Windows 8 users should be protected by traditional antimalware software that provides an effective, industry-recognized level of protection. There are a lot of great antimalware solutions available that we expect will be updated to protect Windows 8 PCs and we believe most PC makers will continue to ship Windows PCs with these solutions installed.
Windows Defender
If you don’t have another solution installed, Windows 8 will provide you protection with a significantly improved version of Windows Defender.
Improved protection for all types of malware. The improvements to Windows Defender will help protect you from all types of malware, including viruses, worms, bots and rootkits by using the complete set of malware signatures from the Microsoft Malware Protection Center, which Windows Update will deliver regularly along with the latest Microsoft antimalware engine. This expanded set of signatures is a significant improvement over previous versions, which only included signatures for spyware, adware, and potentially unwanted software.
In addition, Windows Defender will now provide you with real-time detection and protection from malware threats using a file system filter, and will interface with Windows secured boot, another new Window 8 protection feature.
When you use a PC that supports UEFI-based Secure Boot (defined in the UEFI 2.3.1 specification), Windows secured boot will help ensure that all firmware and firmware updates are secure, and that the entire Windows boot path up to the antimalware driver has not been tampered with. It does this by loading only properly signed and validated code in the boot path. This helps ensure that malicious code can’t load during boot or resume, and helps to protect you against boot sector and boot loader viruses, as well as bootkit and rootkit malware that try to load as drivers.
The same interfaces for secured boot used by Windows Defender, as well as all APIs used by Windows Defender, are available for use by our antimalware partners to deliver additional protection to Windows customers.
- Improved user experience. We have designed Windows Defender to be unobtrusive for most daily usage, and will notify you only when you need to perform an action, or critical information demands your attention. Windows Defender will also use the new Windows 8 maintenance scheduler to limit interruptions.
- Improved performance. Traditionalantimalware technologies are well known for impacting system performance. It’s not uncommon that running antimalware software doubles the amount of time required for core scenarios like file copy and boot. As you read in last week’s blog entry, we have a lot of people working on system performance and Windows Defender dramatically improves performance on all key scenarios compared to common antimalware solutions on Windows 7, while maintaining strong protection. For example, Windows Defender with its full protection functionality enabled adds only 4% to boot time, while dramatically reducing CPU time during boot by 75%, disk I/O by around 50MB, and peak working set by around 100MB.
These same improvements benefit energy efficiency, meaning Windows Defender consumes less power, and gives you longer battery life.
We’re continuing to work with antimalware partners during the Windows 8 development process so you have the best possible Windows PC experience no matter what antimalware solution you choose. We provide them with resources, such as the technical details of how we architected the performance improvements for Windows Defender, so they have the opportunity to make similar improvements to their products.
Microsoft SmartScreen for Internet Explorer and now for Windows too
Traditional antimalware software plays a critical role in defending and remediating attacks. However, reputation-based technologies can help provide effective protection against social engineering attacks before traditional antimalware signatures are available, especially against malware that pretends to be legitimate software programs.
Windows 8 will help protect you with reputation-based technologies when launching applications as well as browsing with Internet Explorer.
Since its release, the SmartScreen filter has used URL reputation to help protect Internet Explorer customers from more than 1.5 billion attempted malware attacks and over 150 million attempted phishing attacks. Application reputation, a new feature added to SmartScreen in Internet Explorer 9, provides an additional layer of defense to help you make a safer decision when URL reputation and traditional antimalware aren’t enough to catch the attack. Telemetry data shows 95% of Internet Explorer 9 users are choosing to delete or not run malware when they receive a SmartScreen application reputation warning.
We understand that Internet Explorer isn’t the only way you download applications from the Internet, so Windows now uses SmartScreen to perform an application reputation check the first time you launch applications that come from the Internet.
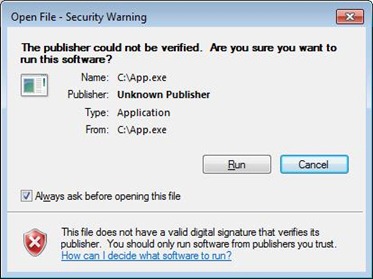
In Windows 7 when launching these downloaded applications, you get the following notification:
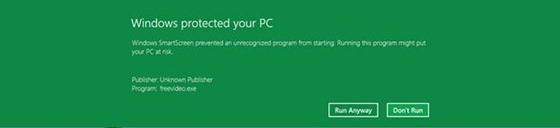
In Windows 8, SmartScreen will only notify you when you run an application that has not yet established a reputation and therefore is a higher risk:
The user experience for applications with an established reputation is simple and clean: you just click and run, removing the prompt you would have seen in Windows 7.
SmartScreen uses a marker placed on files at download time to trigger a reputation check. All major web browsers and many mail clients, and IM services already add this marker, known as the “mark of the web,” to downloaded files.
We expect average users to see a SmartScreen prompt less than twice per year and when they do see it, it will signify a higher risk scenario. Telemetry data shows 92% of applications downloaded via Internet Explorer 9 already have an established reputation and show no warnings. The same data shows that when an application reputation warning is shown, the risk of getting a malware infection by running it is 25-70%. And SmartScreen gives you administrative controls to prevent your non-techie friends or children from ignoring these warnings.
We’ve seen dramatic results with this approach in Internet Explorer and we’re happy to bring it to a broader set of Windows scenarios.
Here’s a video that shows you Windows Defender and SmartScreen URL and application reputation in action:
Download this video to view it in your favorite media player:
High quality MP4 | Lower quality MP4
In conclusion, we’ve taken a very broad approach to improving the level of protection you’ll get from malware in Windows 8, including the use of SDL processes to be secure by design, the implementation and upgrading of mitigations to help protect you against exploits used by malware, improvements to Windows Defender to provide you with real-time protection against all categories of malware, and the use of URL and application reputation to help protect you against social engineering attacks.
Thanks,
--Jason Garms
Comments
Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The biggest thing a user can do is to not run their user account as administrator. I hope that Windows 8 adds controls for preventing executables from running which haven't been installed behind an elevated protected directory. That would make it very hard for a user to download an untrusted executable an then run it, harming themselves.Anonymous
September 15, 2011
And what about Windows Security Essentials? Any changes on that front as well?Anonymous
September 15, 2011
You are very vague. Explain clearly: Is Windows Defender now the same as Security Essentials or is Essentials still a superset of Defender? You talk about realtime protection. I thought Defender already includes a realtime protection. What has changed? Again vague and unclear. I Defender in Windows 8 a true antivirus product then or not? What feature are still missing for example? Be clear. You are ivasive. Microsoft is always vague like this especially in your documentation. Say it clearly, we are implementing this and not implementing the other thing. Be clear please.Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The best malware protection is only one: Mac OS X. Period.Anonymous
September 15, 2011
Also vague is the statement. "Improved protection for all types of malware.Anonymous
September 15, 2011
Microsoft is always vague everywhere. In their documentation, MSDn everywhere. Compare this to Google's cristal clear posts and developer documentation. Anyway: What does "Interfacing with secure boot" mean exactly? It can mean one hundred things. What do you do exactly? And why do you separate realtime protection from other types of protection. You say you provide enhanced protection against most malware and yet below you talk about realtime protection. Why? Is realtime separate. When I buy an antivirus realtime protection is understood to be part of the "protection" not extra. And you mean to say the Defender did not have realtime protection before? Again be clear like Google.Anonymous
September 15, 2011
Microsoft is always vague everywhere. In their documentation, MSDn everywhere. Compare this to Google's cristal clear posts and developer documentation. Anyway: What does "Interfacing with secure boot" mean exactly? It can mean one hundred things. What do you do exactly? And why do you separate realtime protection from other types of protection. You say you provide enhanced protection against most malware and yet below you talk about realtime protection. Why? Is realtime separate. When I buy an antivirus realtime protection is understood to be part of the "protection" not extra. And you mean to say the Defender did not have realtime protection before? Again be clear like Google. This commenting system is broken.Anonymous
September 15, 2011
I'm going to have to disagree with you Anon. I find MSDN documentation to be way better than any other documentation library I've used. Is it perfect? no. But it is really good.Anonymous
September 15, 2011
Wouldn't it be better to exclude the "run anyway" button in the Windows SmartScreen promt and change the color to a bright red, instead of green?Anonymous
September 15, 2011
@James Tiberius Kirk. right... because osx doesn't have malware /s.. stop being idiot with those statements . anyway, the only security system people need is common sense. but if you are the ones that think OSX is better for that? omg... i better dont say more. anyway, i would rather play too many videogames, even free to play mmos in my windows machine, work with my designs in 3dsmax, and do all the stuff i do... than limiting myself to use OSXAnonymous
September 15, 2011
@Anon I think it's probably best to be a vague as possible when it comes to security.Anonymous
September 15, 2011
Does this mean the end fo Securiy Essentials for Windows 8 or will we as consumers still need this?Anonymous
September 15, 2011
So, what happens to Microsoft Security Essentials? @Fake Kirk: Troll.Anonymous
September 15, 2011
Why not make software can be run in sandbox/real time mode, this will get rid all the problems. Windows defender can really waste system resources and delay boot-up time.Anonymous
September 15, 2011
I'm not idiot (thanks for the comment) or troll, it's reality. Windows should be rewritten from scratch to change its vulnerable roots. They must abandon NT and create a truly new SECURE base. Until that day, Windows will ALWAYS remain what it is... Mac OS X and Linux are more secure at their base level, that's the big difference. Windows is a paper boat over the sea. It will be Windows NT 6.2, it's absurd, still NT inside, nooooo!Anonymous
September 15, 2011
Nice to hear that the default security suite will be more robust and enabled by default. I also hope that you have fixed some start-up issues with MSE like:
Microsoft Antimalware Real-Time Protection feature has encountered an error and failed. Feature: Behavior Monitoring Error Code: 0x80004005 Error description: Unspecified error Reason: The filter driver requires an up-to-date engine in order to function. You must install the latest definition updates in order to enable real-time protection.
when the computer is online all the time and so it should have up-to-date definitions and starting the engine late in the Windows login cycle (I often see a red cross for a while after login to Windows 7 just after the computer starts up).
Anonymous
September 15, 2011
It's amazing how one can write so much and manage to create way more questions than answers. Here's the word I'd use to describe Microsoft's communication with users and developers: confusion. Pure, unadulterated confusion. Seriously guys, I don't think you'd be able to create more confusion about Windows 8 even if you tried.Anonymous
September 15, 2011
Very Very nice concept.
- Pls let us know what is the future of Microsoft Security Essentials. I think its better to merge the windows defender and essentials in one package. Less confusion for end users.
- Also ppl need to know the time limit for the security package. Will this be on trial or permanent.
- Pls make sure that real time protection does not result in system performance issues.
Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
Will someone explain the relationship between Defender and Security Essentials, which we know is the best thing ever?Anonymous
September 15, 2011
"Windows Defender with its full protection functionality enabled adds only 4% to boot time, while dramatically reducing CPU time during boot by 75%, disk I/O by around 50MB, and peak working set by around 100MB." Excellent work. Compare to these figures: thepcspy.com/.../what_really_slows_windows_down I've never heard of UEFI Secure Boot - are you going to do a seperate post on that subject? As a matter of comparison, what would be the most secure system, of:Windows 8 running Defender
Windows 8 with Defender disabled but this Group Policy setting enabled: Security SettingsLocal PoliciesSecurity Options: ValidateAdminCodeSignatures Ref: technet.microsoft.com/.../dd835564(WS.10).aspx
Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
I think the explorer Smart Screen Filter might be too annoying like UAC under Vista. I'm running the Developer Preview and noticed that dragging a photo from a webpage into an explorer folder triggers "do you want to allow this website to copy files to your computer. you should only allow files you trust." And it does that for every... single... file I drag & drop, even after I've allowed a website to copy files to my computer.Anonymous
September 15, 2011
@jimbrowski That sounds more like a bug, images aren't covered by IE's reputation, I don't see why they'd be covered by Windows reputation. I'd wager it has nothing to do with SmartScreen at all.Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
The worst malware I ever had was all the pre-installed bloatware. Also, any Adobe product.Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
Has Microsoft done a serious study of how often folks just click through the warning? "Run anyway" or "Are you sure?" "Yes" Yes, I realize the prompts serve a purpose and represent a substantial protection mechanism. But has Microsoft taken a study of, how often the "average user" takes advantage of this mechanism?Anonymous
September 15, 2011
What will happen to Microsoft Security Essentials in Windows 8? Which to choose? Windows Defender, or Essential?Anonymous
September 15, 2011
Does Defender have the firewall integration that Security Essentials has? It looks like it is missing many options from the latest version of SE, so is Defender expected to be upgraded to SE for more comprehensive security, like in Vista and 7?Anonymous
September 15, 2011
@James Tiberius Kirk Macs are for people who are computer illiterate. You pay double the price for a computer that has half the functionality and specs of it's competitors because you don't have any common sense.Anonymous
September 15, 2011
@TPM Bob If this is implemented, I guarantee you that I and many others who sell Windows software will require it to be turned off. Heck, my installer is a .exe so it won't even run. As for why I do not use MSI: Cannot install MSI from inside MSI indirectly. Therefore, cannot decide on the fly whether or not to install SQL Express unless my installer does not use MSI.Anonymous
September 15, 2011
Let me give you some examples why MSDN and your blog postings are vague and contain lots of mistakes, or your naming is illogical:
- Is it Windows Live or simply Live? On MSDN you call the new sdk as the Live Connect SDK and not the Windows Live sdk. But the services are still called Windows Live. Decide please. Is it Live or Windows Live? Live Hotmail or Windows Live Hotmail? Remember Windows Live Search, afterwards renamed to Live Search, etc.
- From Windows Defender help in Windows 7: "Real-time spyware protection alerts you when spyware and other potentially unwanted software attempts to install itself or run on your computer." So there is realtime protection after all? So, what are you adding in Windows 8?
- From the same help topic: "Real-time protection agent Purpose Downloaded files and attachments Monitors files and programs that are designed to work with web browsers. These files can be downloaded, installed, or run by the browser itself. Spyware and other potentially unwanted software can be included with these files and installed without your knowledge." Hehehe. Downloaded files and attachments are certainly not files and programs that are designed to work with web browsers. So, what did you mean? Browser pluggins perhaps? And which browsers anyway are you talking about? Vague vague vague. And wrong. Perhaps you mean e-mail attachments and IE downloads? Then why would you say "programs that work with web browsers". Frustration!
- At the top of all the MSDN pages describing the new Live Connect SDK: "This page describes features that are scheduled to be updated. For information about upcoming programming interfaces to Live Connect, see the Live SDK preview documentation at the Microsoft Connect website for Live Connect." What do you mean? Honestly. Does the above make sense to anyone? "features that are scheduled to be updated" means what? Do you mean to say that this is a pre-release version of the documentation? "see the Live SDK preview documentation at the Microsoft Connect website" means what? The documentation is on the MSDN page I am currently reading and which contains this notice. Why should I go to MS Connect to read the same things there? OK, let me go to MS Connect. You click the link and it takes you to a Live ID sign-in page. Still and after so many years and even though it is used by 500 million users, the Windows Live ID (or is it Live ID) sign-in page is slow sooo sloooow to load. Compare this to Google's sign-in page which appears instantly. OK, I don't want to sign-in, I decide to press back. Oh, look, back does not work! You can't go back. The log-in page loads and re-loads when you press back. You see, errors, mistakes, broken experiences everywhere.
- OK, I manage to go back to MSDN after trying and re-trying. But look, if I click the Documentation link at the top of the Live Connect SDK it takes me to an API reference! Honestly now, when somebody tells you they want to read the DOCUMENTATION of a new technology, like the Live Connect SDK in this case, the first thing any intelligent person would show them is a reference? Ask yourselves. I would show an overview, a programmers introduction, a developers Guide, etc. Certainly not switch to the Reference section right away. Compare this to Android's documentation. You click on something and the page you expect comes up. Not something illogical. By the way, that MSDN section includes things that I think are not even distributed with current versions of Windows Live Messenger for example, like the Activities SDK. Again, another problem is that your documentation is updated slowly and sometimes never. Win32 API MSDN section for example which contains things from the 90s and even samples which do not compile.
- OK, let me go back to dev.live.com, perhaps there I will find what I want. Oh, look some graphics which I have to click on to get to the information I want not links? And some vague promises like: Skydrive enables you to work with users' photos and documents. Photos? Documents? Why not they say simply users' files? Oh, perhaps they only restrict Skydrive to specific file types, such as JPG. Who knows. Let me read on. Later down of course it appears that photos = both photos an videos. I guess for Microsoft videos are simply large photos, so we'll call everything photos. It makes sense doesn't it? But wait a moment, perhaps documents now equals all files too. Because how can you tell if something is a "document" or not. Again confusing. Oh, I am fet up. Unclear as always. I guess I will not use Live Connect after all.
Anonymous
September 15, 2011
Do a Bing search on the recent malware attacks to OS X. Then say that OS X is more secure. Windows has more attackers specifically because it has 90% marketshare. Why even target something with 3% when you're getting paid for the number of computers either taken over or infected? And yes, as indicated in the article above, Microsoft has done studies on how often the user clicks "yes" continue and has a problem and when the click "yes" and don't. Please read the article before commenting. I also agree with the guy who said that "how security prevents attacks should be kept vague", and you should too, unless you're a hacker, that is.Anonymous
September 15, 2011
@Anon Defender will pick up all the capabilities of MSE and will take advantage of windows 8 specific security features. Wasn't that vague was it ?Anonymous
September 15, 2011
Wanna know a great way to protect everyone from malware?????? Move onto a UNIX like Kernel ;)Anonymous
September 15, 2011
@BumbleBritches75, Windows is FAR more secure than UNIX and Linux will ever be.Anonymous
September 15, 2011
@BumbleBritches75, Windows is FAR more secure than UNIX and Linux will ever be.Anonymous
September 15, 2011
"The same data shows that when an application reputation warning is shown, the risk of getting a malware infection by running it is 25-70%." Thats quite a broad percentage range. Would be interesting what makes it 25% risk and what 70%.Anonymous
September 15, 2011
windows 8 preview is slower than windows 7.Anonymous
September 15, 2011
no screen resolution on windows 8 preview? bring back aero themAnonymous
September 15, 2011
what happen to themes on windows 8? y the blurry look. bring the glassy interfaceAnonymous
September 15, 2011
what happen to themes on windows 8? y the blurry look. bring the glassy interfaceAnonymous
September 15, 2011
MORE WORK FOR WINDOWS 8. WAY BEHIND THAN WINDOWS 7Anonymous
September 15, 2011
MORE WORK FOR WINDOWS 8. WAY BEHIND THAN WINDOWS 7Anonymous
September 15, 2011
MORE WORK FOR WINDOWS 8. WAY BEHIND THAN WINDOWS 7Anonymous
September 15, 2011
MORE WORK FOR WINDOWS 8. WAY BEHIND THAN WINDOWS 7Anonymous
September 15, 2011
Hi, it's great to see that Windows now gets an anitmalware solution built-in but as an ITPRO I do have a lot of questions on how this will behave in an enterprise environment. We all use solutions like FEP,McAfee or Symantic, ... How will they be able to deactivate Windows Defender? if it a feature which you can remove? or is it like in Windows 7 that you can disable it but that the shortcuts and so on remain visible causing confusion and helpdesk calls. Are you guys thinking about this? Do you talk with the systems management team about this? Forgive me but sometimes I get the feeling that the teams are not always working close togheter which has a negative impact on the products being released. Do you have some comments on that? Thx, KrisAnonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
If don't want Windows 8 to be banned in EU or even in the US, you better reconsider it...Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
I didn't understand why everyone wants to know every minute details at this time? Just hold for some time, details will emerge, there will be beta releases and more with more functionality showing in Win8. There is still 5-9 months at least before it will go to RTM..Anonymous
September 15, 2011
*nix is nothing but a crapOS for cheap orphan servers, or for some retarted kids, that no one (from the real hacker's community) deems to attack! Hackers have more interest in widespread/pervasive OS like windows.Anonymous
September 15, 2011
The comment has been removedAnonymous
September 15, 2011
@ali
- Currently, it looks similar as MSE.
- Check this support.microsoft.com/.../923159
Anonymous
September 15, 2011
Yes, the posts are quite cryptic. Not only this one, but also about Hyper-V, the "reflecting" ones etc. Some of them have more marketing buzz words than facts and from the others is really hard to dig and guess what is really new in Win8.Anonymous
September 15, 2011
@MCCZ what is cryptic?Anonymous
September 15, 2011
The comment has been removedAnonymous
September 16, 2011
@Steven Sinofski: For example, at blogs.msdn.com/.../bringing-hyper-v-to-windows-8.aspx I have almost no clue what is "old" and what features and characteristics are "new" in Windows 8. The section "An introduction to Hyper-V" seems to talk about Hyper-V as a general, non Windows version specific, but then you have a video about how it works in Windows 8 (which is version specific). Being not keen in the current version of Hyper-V I do not see what is new to Windows 8 and is already in the market, or whether there are no changes in Windows 8 and you are just mentioning the current state and the video is just mispositioned - if this is the case, I do not understand why the section exists in the first place, instead of providing a link to an appropriate part of the existing documentation and introducing just the smallest part needed to understand the new things. In this post, my understanding and parsing was much better in general than in the Hyper-V, but I was lost a little bit in the place what malvares are new in Windows 8 in contrast to the Defender + MSE combo in Windows 7 and whether they are really consolidated in one product (there is no word about MSE at all). From a part of the post I have a suspision that you use SDL to build Windows in general, not only with this version, but from the conclusion it seems like that you have just started using SDL in Windows 8.Anonymous
September 16, 2011
I am maybe a bit off topic, but I am interested to learn how developers are going to protect their games and apps code from being stolen and also getting cracked. I have already explored js code of all built-in apps came with Windows 8 preview. .net apps are also easy to decompile. Why is MS recommended to protect the apps? // chall3ng3r //Anonymous
September 16, 2011
@MCCZ - it is a safe bet to assume we're not blogging about old features of Windows :-) I am not sure how you would conclude that about SDL, but you initial assumpion is correct.Anonymous
September 16, 2011
Please, enhance your UAC/SmartScreen/etc. to reach the process-control functionality like in the modern firewalls, with rules, program groups etc. For example: www7.pcmag.com/.../235706-comodo-antivirus-5-0-defense-rules.jpg , www.computersecure.org/comodo-bg_cpf_alert.gif (but it can be made much better, of course). That's not what firewalls must do, proccess controlling is the system work.Anonymous
September 16, 2011
@Steven Sinfosky: Every single other item in the list is a "new" feature, so the SDL should also logically be one of them. And as you stated you do not blog about the old ones :)Anonymous
September 16, 2011
@Steven Sinfosky: Every single other item in the list is a "new" feature, so the SDL should also logically be one of them. And as you stated you do not blog about the old ones :)Anonymous
September 16, 2011
During the developer preivew (clean) setup, I have explicitly turned off the SmartScreen. What a suprise when I tried to run a network driver installer and was presented with a "Windows SmartScreen can't be reached right now. Check your internet connection..." message. So, great, but make sure the user can switch it off and respect their wishes! :-)Anonymous
September 16, 2011
Excuse me if it's not the right theme to report a bug, but my Win 8 dev preview spontaneously changed the color style: rghost.ru/.../image.png .Anonymous
September 16, 2011
I dont quite understand how this will work in enterprise scenerios.. will FEP still be there ? will windows defender will still be controllable via registry / group policies.. And, while writing technet/msdn help files, divide them into average and advanced user scenerios. Its like i know 4 things, get there to clear 2 things and lost previous 4 things in confusion....Anonymous
September 16, 2011
The comment has been removedAnonymous
September 16, 2011
The comment has been removedAnonymous
September 16, 2011
The comment has been removedAnonymous
September 16, 2011
The comment has been removedAnonymous
September 16, 2011
@Steven Sinfosky: Dear Mr. Steven Sinfosky, I am reaching out to you as we would like your valuable input, insight and thoughts on our discussions on HTML5.com. I have signed an NDA with MS through Ziad Ismail and he told me to get ahold of others at MS as I need but won't provide contact details. So here I am... We've have temporarily pointed HTML5.com to BeautyOfTheWeb.com. As we all know, HTML5 is the one standard that allows for purchase once and use on Desktop, Tablet and Mobile, while over coming the limits of other ECO systems. I cannot go into any further details, so please contact me directly at HTML5.com ((at)) Gmail.com. Kindest regards.Anonymous
September 16, 2011
It's so simple: Windows 7 Win Defender: Antimalware Engine MSE: Antimalware Engine + Antivirus Engine + Network extra Protection Windows 8 Windows Defender: Antimalware Engine + Antivirus + Network Extra Protection Engine ( ex-MSE ) Perfect move the integration of the great MSE into Windows 8. Along with ISO support, better tools such as Defragment and Cleaning etc. We're not gonna need may 3rd party software. Even less, at least.Anonymous
September 16, 2011
The comment has been removedAnonymous
September 16, 2011
@Steven Sinfosky: And in the Hyper-V artice. From the title "An introduction to Hyper-V" I understood that you are going to explain us what the Hyper-V technology is about. That technology is already in the market for several years, so I expect that the text is just for those of use who are not experienced in it, so they can understand the rest of the article (the new things). So I do not expect that the text introduce something new unless that part is clearly tagged as "new in Windows 8". After several paragraphs of "an introduction" there is a video how it works in Windows 8 as that the (old) Hyper-V is about something new in Windows 8. Quite unexpected, confusing and requiring to ask mysql "Have I missed something? Was there something new in the previous text? Should I sit down and compare the existing documantation with the previous text to localize the new parts?" Quite a lot of work for (almost) no benefit.Anonymous
September 16, 2011
clearly, because only EVERYONE except Microsoft uses some form of Unix Kernel... so logic dictates that it has to be insecure. :Facepalm:Anonymous
September 16, 2011
HyperV was for server environments and now it’s supported for all versions of Windows 8. That’s the new thing.. that we, the average user, can experience bare metal virtualization on our home PC. P.S. if you are just a hater, please mention in the post-script, rather than making it complicated for us.Anonymous
September 16, 2011
You are a lowlife troll and you are not welcome here. Live with this.Anonymous
September 16, 2011
The blue screen page when Windows 8 crashes suggests to find the solution to that problem over the Internet, but.... if that's the only PC I've got and it keeps crashing, how can I find the solution? Here we have the usual stupid Microsoft defective by design thing.... ;)Anonymous
September 16, 2011
@Mohit: Microsoft Security Essentials will not be needed on Windows 8. We remain committed to providing strong protection of Windows 7 and earlier Windows users with Microsoft Security Essentials. Both are based on the same core technology (engine, signatures, filter driver), but Windows Defender on Windows 8 also provides additional functionality, such as integration with Windows 8 secured boot, as described in the blog. There is nothing time limited about Windows Defender's protection in Windows 8. @fjpoblam: Yes, we’ve done quite a bit of research and refinement on the SmartScreen user experiences in Internet Explorer over the years and we’re carrying that learning forward to the Windows SmartScreen experience. In the linked blog you can read more about the Internet Explorer 9 application reputation results. The top level result is that 95% of users make a safe choice when presented with the equivalent Internet Explorer 9 warning. @FZB: 25-70% is a day-over-day risk range depending on the attack landscape, but is influenced by a number of factors including the daily volume of attacks and the zero hour protection rate of upstream detection mechanisms.Anonymous
September 16, 2011
@Anon - you have my respect dude. And some people are just to dumb and ignorant to understand simplest things and for that they will call you a troll. I totally agree with Anon that the MSDN and these blog postings are very unclear and somewhat misleading. If you want to do something, do it right or don't do it at all.Anonymous
September 16, 2011
@magistarx You and Anon should learn how to read then.Anonymous
September 17, 2011
The comment has been removedAnonymous
September 17, 2011
The comment has been removedAnonymous
September 17, 2011
The comment has been removedAnonymous
September 17, 2011
@avon, @arnold: The people who develop and those who document an API or product are strictly different at Microsoft. Have you tried to read Open XML MSDN documentation and update a column range for a particular existing conditional formatting in XLSX file based on that documentation?Anonymous
September 17, 2011
The comment has been removedAnonymous
September 17, 2011
"Windows is FAR more secure than UNIX and Linux will ever be."
- Linux - opensource -> trustworthy. Windows - FAIL
- Linux - central repo -> secure, Windows - FAIL
- Linux - unstable kernel ABI -> unstable to infect, Windows - FAIL
- Linux - ACL+SeLinux RT protection -> complete rights lock, Windows - FAIL(Cacls -> mix of garbage )
- Linux - Kernel Address Space Randomization since June 2005. Windows - FAIL
- Linux - FREE and OPEN. Windows FAIL!
- Linux - never spreading FUD or sabotaging companies. WINDOWS FAIL! You guys serious? Maybe Microsoft should openup the OS and stop charging for doing NOTHING? Or maybe they should die because Google does the right thing and eventually overthrowns it? Windows 90% market FAIL! Windows 99,9% preinstalled on Desktop machines via illegal hidden agreements with OEMs (either preinstall or pay full price). Means every 10 desktop machine gets its preinstalled windows REPLACED by Linux or Hackintosh straight. Microsoft, please, continue bribing graphics cards companies to develop your MS-Only DirectX driver support instead of crossplatform graphics! Please! Because, else, you already dead and lost. And whats about that new interface in 8? I think you copy-pasted it from "Idiocracy" the movie. No, seriously :)
Anonymous
September 17, 2011
I never understood why the user has to search for anti-malware software, install it, maybe even pay for it and so on. If a product isn't secure by default additions that make it secure should be built-in and free. They should work by default. So: Because Windows isn't secure against viruses and other malware by default it should be clear that Windows needs a built-in malware-protection without using any additional software. Or make Windows secure against malware by default without any additional software.Anonymous
September 17, 2011
The comment has been removedAnonymous
September 17, 2011
The comment has been removedAnonymous
September 18, 2011
@ktyle: Well said. Very well said indeed! @James Tiberius Kirk: What is it with Mac users that hang out in Windows-specific blogs just to troll? Can't you find something else to do on your Mac?Anonymous
September 18, 2011
Why not sandbox each application for itself. It's ridiculous that i have to give an installer FULL admin rights, including ability to modify windows system files, just so that it can create a folder and copy some files into %PROGRAMFILES% You have really thought your users to ignore UAC warnings, some applications (spotify for example) require elevation upon almost every startup just for auto update to work. People get used to it and just click past.Anonymous
September 18, 2011
its still 'boy that cried wolf' scenario. needs a built in sandbox.... i agree with ChenAnonymous
September 18, 2011
The comment has been removedAnonymous
September 18, 2011
is this remove all viruses is with this antivirus i did not have to download any other antivirus like nortonAnonymous
September 18, 2011
Nice post. I just hope that if I want to live without Defender, Windows would allow it and just let me be. Cheers!Anonymous
September 19, 2011
We wanna see a sandbox architecture like qubeos in windows 8. I definitively will love microsoft if the guys behind this make it a reality.Anonymous
September 19, 2011
The comment has been removedAnonymous
September 20, 2011
Wow the security enhancements are really exciting and comprehensive. Doesn't randomizing the heap lead to heap defragmentation? I just have one request for this area. I cannot stress how important it is for me to be able to optionally disable the reputation based download feature without disabling the SmartScreen filter for browsing. I am an experienced/power user and I only wish to enable SmartScreen. Please give us this choice through IE settings and a Group Policy. There is already an option for disabling SmartScreen which also disables the reputation based download warning feature but disabling SmartScreen entirely for browsing is dangerous. Please allow individual controls for disabling SmartScreen and disabling the application reputation based download feature. I know what I am downloading and do not wish to receive additional and obtrusive warnings.Anonymous
September 20, 2011
The comment has been removedAnonymous
September 21, 2011
Windows 8 run better. but I can install Kasspersky Internet security 2011 (KIS 2011) on Windows 8. How to run it?Anonymous
September 22, 2011
Hey that little green prompt is great for untrusted apps except for one little thing... most apps ARE untrusted anyway! Including most MS downloads direct from your site!Anonymous
September 25, 2011
The comment has been removedAnonymous
September 26, 2011
It is called Windows Developer Preview for a reason, is under development.. Wait for the Beta release to make comments and sugestions/changes. OS X, linux, unix, ubuntu, users please stop wasting time.Anonymous
September 27, 2011
@xpclient: You can separately enable the protection SmartScreen provides through Internet Explorer from the protection it provides at app launch time.Anonymous
September 27, 2011
@prthrokz: Windows Defender will get out of the way when you chose to use a different solution.Anonymous
September 29, 2011
@Jonathan Thu, Sep 15 2011 11:49 PM # "I was very glad to see MSE rebranded as Windows Defender and bundled with Windows 8" MSE is NOT Windows Defender and is NOT bundled with Windows 8. Windows Defender is the same with older Windows Defender bundled with Vista or 7, just improved. You can succesfully install MSE in Windows 8 Developer preview however. @Jason - it seems to be quite annoying to include SmartScreen in Windows. Norton Products uses something similar also. But if a file is new, there is no reputation for it. Your telemetry statistics may be accurate, but not for some wich uses to keep his software up to date. I got warnings in IE 9 even for Microsoft Software or Codeplex downloads. There is almost no week to not receive warnings, wich of course I decide to ignore. So if you don't find a way to update more frequently SmartScreen database, better get rid off.Anonymous
October 04, 2011
The comment has been removedAnonymous
October 10, 2011
There exists some issue with MSE and AutoHotkey compiler. See www.autohotkey.com/.../viewtopic.php. Just tested it, it exists in Windows Developer Preview too. Please fix this for the beta. When you start compiling an AHK script into an EXE, CPU usage increases if MSE is running, everything stops responding and sometimes script compilation fails.Anonymous
October 10, 2011
The comment has been removedAnonymous
October 11, 2011
The comment has been removedAnonymous
October 11, 2011
The comment has been removedAnonymous
October 11, 2011
The comment has been removedAnonymous
October 13, 2011
The comment has been removed