Active Directory PowerShell Script to Report on Users with SPNs
A peer of mine Chris Nadler, reached out and said “Hey we really don’t have any good ways to scan for a particular type of account in Active Directory that could be a prime target for malicious activity what do you think this would take.” So here it is, this script goes out and pulls every Active Directory User object with ServicePrincipalName’s (SPN) defined and gathers important information about that account. After I was done writing it, I also realized it was a way to potentially get rid of unknown accounts by validating if the computer’s they should be performing authentications for are still online. Disclaimer I would use it as one of many steps to determine if an account is still used or valid.
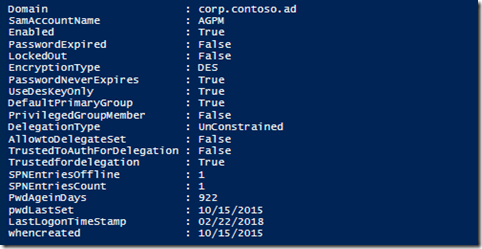
Here are things the script looks for:
- Is the SPN’s computer that is defined currently online.
- Is the User Account set up with Kerberos Constrained vs UnConstrained Delegation.
- What kind of encryption is being used for the accounts password. (msds-supportedencryptiontypes)
- Checks to see if the Account is a member of a Domain Privileged Group.
- Also checks so see if the primary Group Membership has changed.
- The password age.
Our Recommendations:
- No Accounts should be set up with Unconstrained Kerberos Delegation.
- Same goes for Protocol Transitioning Constrained Delegation.
- None of these accounts should be in a privileged group. Example – Domain Admins or Enterprise Admins
- Passwords should be changed regularly with a a minimum 15, preferred 25 character password.
- Only Valid SPN’s should be defined.
- DES Encryption should not be used.
I provide the script below along with a sample of the output that gets displayed in PowerShell. The script will also exports the results to a csv file for easy searching and filtering in Excel.
Here is an example of the output:
Here is the source code which can be found on Github: Link
And that is all for now.
-Chad
Recommend Reading:
- Kerberoasting
- What should I know about security? The massive list of links post.
- Detecting Kerberoasting activity using Azure Security Center
- Get rid of accounts that use Kerberos Unconstrained Delegation
- Security Focus: Report on Unconstrained Delegation
- Security Focus: Report on Protocol Transition