Video Screencast: Complete setup details for federated identity access from on-premise AD to Office 365.
How to set up IIS, ADFS 2.0, the Federation Config Tool and Office 365 Dirsync. The video starts with federated access and its setup. Shows how an existing user can use their AD credentials to log in to Office 365 entirely seamlessly; they hit CTRL-ALT-DEL and login to the machine, then when they go to Office 365 they are not prompted for the password because they have already logged in.
Then in Dirsync I do the setup so that you can create users and modify their attributes in AD and they automagically appear in Office 365 as federated accounts that you can use your AD credentials to log in to.
I’ll do a whiteboard flow of the protocols and how they work very soon, I just wanted to get the demo-video in place because so many folks have asked for it. I use the “magic of video editing” to avoid the confusion of error messages and to shorten the install-times of various components.
Complete setup details for federated identity access from on-premise AD to Office 365. from Steve Plank on Vimeo.
Video Screencast: AD to Office 365 setup
If you are going to do this yourself – here are a couple of notes worth mentioning:
Federated Identity:
The “Admin” account you need to use for the powershell commands that set up the ADFS server and the Microsoft Federation Gateway up in the cloud is not just any admin account. It needs to be the first admin account on the Office 365 system when the subscription is created.
There is a typo in the help files on the Microsoft Online portal (https://onlinehelp.microsoft.com/en-us/office365-enterprises/ff652560.aspx). The 3rd powershell command says:
“Convert-MSOLDomainToconverFederated –DomainName <domain>”.
The part I’ve highlighted in red should be missed out completely – so the command becomes:
“Convert-MSOLDomainToFederated –DomainName <domain>”.
DirSync:
Can only run on a 32-bit Server. I used Windows Server 2008 SP2. You can’t install it on a Domain Controller. Which means if you are going to set up a test-lab, you need a minimum of 2 machines: a DC (you could use for ADFS 2.0) and a member server for the Dirsync tool.
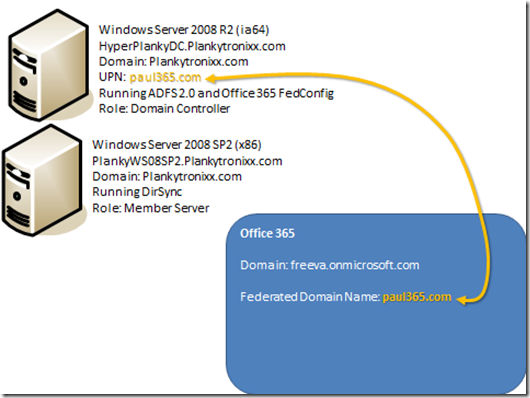
In my test environment I had:
Planky – GBR-257
Comments
Anonymous
January 25, 2011
Very useful, thanks a lot! One question: Can the synchronization be done from the on-premise AD by means of groups or other claim rules as is possible with native ADFS 2.0?Anonymous
January 26, 2011
Under the covers, Dirsync is using a heavily doctored version of MIIS 2003 (for example it doesn't install SQL) and the MIIS client is part of the installation. The trouble with MIIS 2003 is that provisioning rules are code-only. They give you the assemblies but not the source code. To provision an entry based on group membership you'd need access to that assembly's source code. Plus - an even bigger problem, if you fiddle with anything in the MIIS set up then it will become an unsupported configuration. It's intersting to have a look and see what's going on, but you shouldn't change anything.Anonymous
March 22, 2011
Great and very useful work! I have some questions: 1 - Is it possible to get a better video quality because characters are difficult to read. 2 - What is the format of tokens exchanged between ADFS and O365? Is the SAML V2.0 or V1.1? Where can I find a description of the messages exchanged between MFG -> ADFS and ADFS-> MFG (SAML Assertion + HTTP method used)?Anonymous
June 07, 2011
very useful info. I was wondering if (how) we can setup a federation relationship between Office 365 (as a Relying Party) and a 3rd party Identity Provider for non-microsoft enterprise ? Does O365 use Microsoft Federation gateway (hosted online) ? Where can I find all the URL endpoints to exchange ws-fed metadata and stup trust ? ThanksAnonymous
July 24, 2011
It was very useful, thanks a lot and i have a 1 question tAnonymous
July 24, 2011
Hi Raj, I'm glad you liked it, but your question got truncated. Try again! PlankyAnonymous
September 26, 2011
Thanks for this useful video. I have a couple questions:
- Is there any reason that DirSync can not or should not be installed on the federation server, assuming that it isn't a DC?
- Unless I missed it, I don't think that you mentioned anything about setting up an internet proxy. Is that out of scope of this video?
Anonymous
September 26, 2011
The comment has been removedAnonymous
September 29, 2011
Is there a specific need for a proxy server if I wont have any users access office 365 from outside my network?Anonymous
October 07, 2011
Any idea if AD FS integrated with other federation providers will work with Office 365? If I follow Microsoft's AD FS 2.0 -> Oracle Identity Federation Identity guide, will this work with 365? technet.microsoft.com/.../ff849212%28WS.10%29.aspxAnonymous
October 07, 2011
The comment has been removedAnonymous
November 04, 2013
Thank you for the video. It was very helpful. I did notice that after all was complete that the existing O365 users did not have the double arrow for synchronization. Are they being synched or is the synch only for new users that are entered into AD?Anonymous
November 04, 2013
Yes - that's right. There is an "anchor" attribute and that is only discovered on provisioning the account in the first place. Therefore only the accounts that were provisioned by Dirsync will be synced.Anonymous
March 29, 2014
A great alternative to doing Office 365 federation this way, is using IAM Cloud. The service is a direct replacement/alternative to running ADFS and Dirsync on-premises. It is hosted wholly in Windows Azure and is highly scalable, available and cost effective. User experience is the same as an on-premises deployment but with a few nice extras, including Office 365 plan assignment, and the ability to federate other applications. Deployment is simple and quick, and you require no additional servers. For more information, see www.iamcloud.com/federate365.com.Anonymous
May 19, 2014
Planky, very well & descriptive video. Request if you can come up with ADFS 3.0 video that focus on 2 Factor Auth provided by Windows 2012 R2.Anonymous
May 19, 2014
Hi Dematri, Yes - it is something I will eventually get round to. Just sooo busy with hundreds of other things right at the moment. At least your comment indicates there is an interest.Anonymous
July 14, 2014
An Awesome video using which i was able to setup an environment at my end successfully in 1 day today thanks a lot Planky, i like this nameAnonymous
September 16, 2015
Really a useful video...well explained Thanks a lot