3.2.2.1.5.1 Search Requests
The CA SHOULD perform modify requests as demonstrated in the following figure.
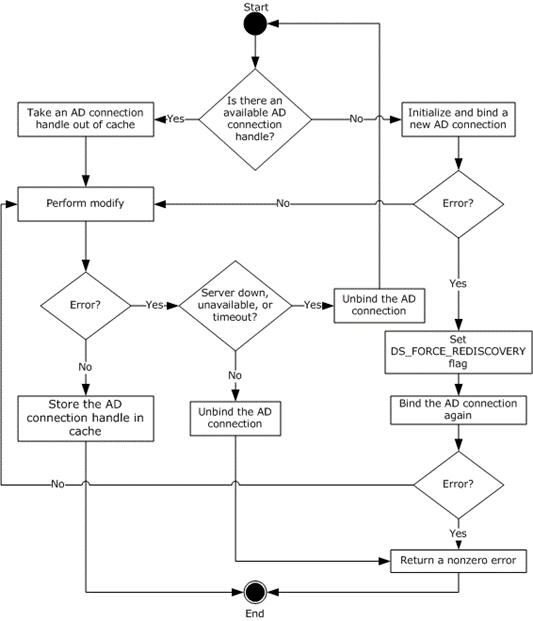
Figure 7: Retrieving an ADConnection handle for publishing issued certificates to a user or computer object
The following steps describe the flow of the preceding figure:
If the Collection_of_Certificates_Publication_AD_Connections ADM has no ADConnection element:
Invoke the "Initialize ADConnection" task ([MS-ADTS] section 7.6.1.1) to construct an ADConnection with the following parameters:
TaskInputTargetName: Domain Name System (DNS) of the end entity obtained from the distinguished name (DN) of the end entity passed in as input parameter EndEntityDistinguishedName.
TaskInputPortNumber: If the value of the Config_CA_LDAP_Flags datum has 0x0000001 (LDAPF_SSLENABLE) bit set, use port 636. Otherwise, use port 389.
Store the returned ADConnection handle in the ActiveDirectory_Connection variable.
Perform a bind request, as specified in section 3.2.2.1.5.2. Go to step 3.
If the Collection_of_Certificates_Publication_AD_Connections ADM has an ADConnection handle, remove it from the Collection_of_Certificates_Publication_AD_Connections ADM and use it as ActiveDirectory_Connection in the following steps.
Verify that the issued certificate, passed in as input parameter IssuedCertificate, does not already exist under the user object as specified in the following steps.
Invoke the "Perform an LDAP Operation on an ADConnection" task ([MS-ADTS] section 7.6.1.6) with the following parameters:
TaskInputADConnection: ActiveDirectory_Connection
TaskInputRequestMessage: LDAP SearchRequest message (see [RFC2251] section 4.5.1) as follows:
baseObject: EndEntityDistinguishedName
scope: baseObject
filter: NULL
attributes: userCertificate
sizeLimit: 10000
timeLimit: 120
derefAliases: neverDerefAliases
typesOnly: FALSE
TaskOutputResultMessage: Upon successful return from the task, this parameter will contain the results of the LDAP search.
Store the returned value for userCertificate attribute in the Set_Of_Certificates variable.
If the TaskReturnStatus returned is not 0, convert it to a 4-byte HRESULT value (errors are specified in [MS-ERREF] section 2.1) by performing the processing rules in section 3.2.2.1.7 with the following input parameters:
InputReturnStatus: TaskReturnStatus
InputResultMessage: TaskOutputResultMessages
Return the OutputHRESULT output parameter to the client and exit. Also, invoke the "Perform an LDAP Unbind on an ADConnection" task (see [MS-ADTS] section 7.6.1.5) with the TaskInputADConnection parameter set equal ActiveDirectory_Connection and then exit.
If the certificate in input parameter IssuedCertificate does not exist in the Set_Of_Certificates variable, add it to this set.
If any of the certificates in Set_Of_Certificates variable has expired for more than 24 hours, remove it from Set_Of_Certificates.
If Set_Of_Certificates is not changed as part of step 3.3 and 3.4, add the ActiveDirectory_Connection to the Collection_of_Certificates_Publication_AD_Connections ADM and then exit.
Invoke the "Perform an LDAP Operation on an ADConnection" task ([MS-ADTS] section 7.6.1.6) with the following parameters:
TaskInputADConnection: ActiveDirectory_Connection
TaskInputRequestMessage: An LDAP ModifyRequest (see [RFC2251] section 4.6) as follows:
Object: EndEntityDistinguishedName
The modification sequence has one entry, as follows:
operation: replace
modification:
type: userCertificate
vals: Set_Of_Certificates
TaskOutputResultMessage: Upon successful return from the task, this parameter will contain the results of the LDAP search.
If the LDAP modify is successful, add the ActiveDirectory_Connection to the Collection_of_Certificates_Publication_AD_Connections ADM and exit.
If an error is returned from the LDAP modify indicating that the LDAP server is down, unavailable, or that there is a timeout (that is, the error code LDAP_SERVER_DOWN, indicating the directory server is unreachable), the CA MUST do the following:
Invoke the "Perform an LDAP Unbind on an ADConnection" task (see [MS-ADTS] section 7.6.1.5) with the TaskInputADConnection parameter set to ActiveDirectory_Connection.
Go to step 1.
If an error is returned from the LDAP modify for reasons not covered in step 6, the CA MUST do the following:
Invoke the "Perform an LDAP Unbind on an ADConnection" task (see [MS-ADTS] section 7.6.1.5) with the TaskInputADConnection parameter set to ActiveDirectory_Connection.
Return a nonzero error to the client and then exit.