Dynamic Group Membership in Azure Active Directory (Part 2)
Dynamic Group Membership in Azure Active Directory (Part 2)
In Part 1 of this series, I covered Creating and Assigning Licenses and Applications to a Dynamic User Group - https://blogs.technet.microsoft.com/pauljones/2017/08/28/dynamic-group-membership-in-azure-active-directory-part-1/.
For Part 2 of the series, I will cover Creating Dynamic Device Groups.
One of my favorite new features in Azure Active Directory is Dynamic Group Membership. In these blog posts, I will describe the different types of Dynamic Groups that you can create, then assign these Groups (User and Device) to Applications and Licenses. If a user or device satisfies a rule on a group, they are added as a member of that group. If they no longer satisfy the rule, they are removed.
I will step through the process in this blog on creating a Dynamic Device Group:
The following options are available for Membership Type:
- Assigned
- Dynamic Device
- Dynamic User
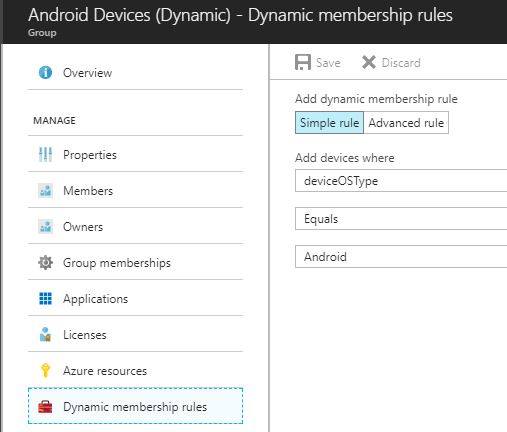
For this blog, I will create Dynamic Groups for the following: iOS Devices (iPad and iPhone), Android Devices and Windows Devices. For each one, I selected Dynamic Device under Membership Type. For my dynamic query, I selected the following:
Add devices where: deviceOSType equals Android
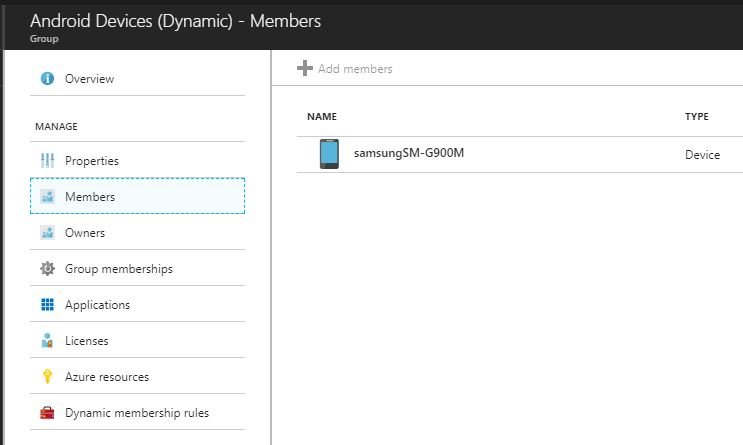
Now, all Devices in Azure Active Directory that are Android Devices will automatically be added to this group. I choose deviceOSType, but you can choose any of the attributes that are registered with each device.
I used Azure AD Graph Explorer to view the Device information:
- Goto https://graphexplorer.azurewebsites.net/
- Login with Tenant Account
- Run the following query https://graph.windows.net/myorganization/devices
- Results:
"deviceId": "37d6b344-0234-469f-967f-98c975e8d355",
"deviceMetadata": null,
"deviceObjectVersion": 2,
"deviceOSType": "Android" ,
"deviceOSVersion": "6.0.1",
"devicePhysicalIds": [],
"deviceTrustType": "Workplace",
"dirSyncEnabled": null,
"displayName": "samsungSM-G900M",
"isCompliant": null,
"isManaged": null,
"lastDirSyncTime": null
The information displayed will depend on if the device is Azure AD Joined, Workplace Joined, Intune MDM, etc...
Another way to find this information is to use PowerShell Command Get-MsolDevice. In this example, I pulled information on a Windows 10 Device.
PS C:\Users\Mike\Desktop>Install-Module MSOnline
PS C:\Users\Mike\Desktop> Connect-MSOLService
PS C:\Users\Mike\Desktop> Get-MsolDevice
cmdlet Get-MsolDevice at command pipeline position 1
Supply values for the following parameters:
Name: W10A
Enabled : True
ObjectId : e815d501-0806-43f2-a725-62823638010c
DeviceId : 008d51f8-7fc0-4e8e-95b7-7d0c35a015f1
DisplayName : W10A
DeviceObjectVersion : 2
DeviceOsType : Windows
DeviceOsVersion : 10.0.15063.540
DeviceTrustType : Azure AD Joined
DeviceTrustLevel : Compliant
DevicePhysicalIds : {}
ApproximateLastLogonTimestamp : 8/17/2017 6:36:22 PM
AlternativeSecurityIds :
DirSyncEnabled :
LastDirSyncTime :
RegisteredOwners : {Paul@XXXXXXX.onmicrosoft.com}
GraphDeviceObject : Microsoft.Azure.ActiveDirectory.GraphClient.Device
This is the full list of all possible device attributes that can be used:
accountEnabled
displayName
deviceOSType
deviceOSVersion
deviceCategory
deviceManufacturer
deviceModel
deviceOwnership
domainName
enrollmentProfileName
isRooted
managementType
organizationalUnit
deviceId
objectId
You can also use multiple attributes and operators:
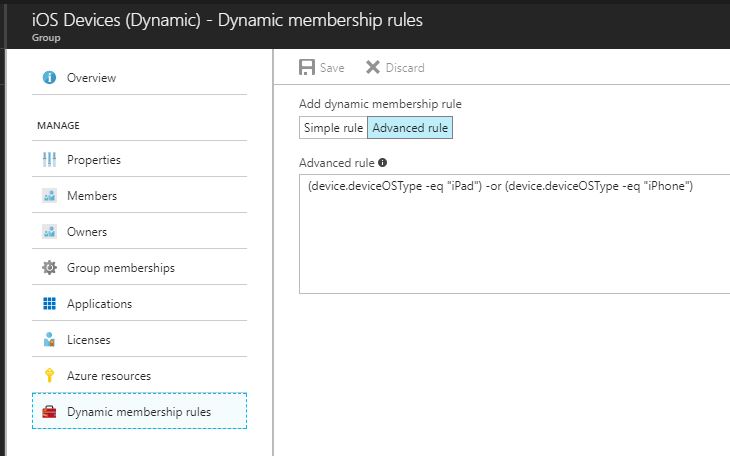
- (device.deviceOSType -eq "iPad") -or (device.deviceOSType -eq "iPhone") - this will include all iOS Devices (pictured below)
- (device.deviceOSType -eq "Windows") - this will include all Windows devices
- (device.deviceOSType -eq "Android") -and (device.deviceOSVersion -eq "6.0.1") - this will include all Android devices running version 6.0.1
- (device.deviceOSType -eq "Android") -and (device.isRooted -eq true) - this will include all Android devices that are Rooted
Now that we have created Dynamic Groups, we can use these groups with Azure Active Directory, Intune and Application Deployments.
You can create a dynamic group for devices or users, but you cannot create a rule that contains both user and device objects.
Device membership rules can only reference immediate attributes of device objects in the directory.