Investigating Suspicious Activity in a Hybrid Cloud with OMS Security
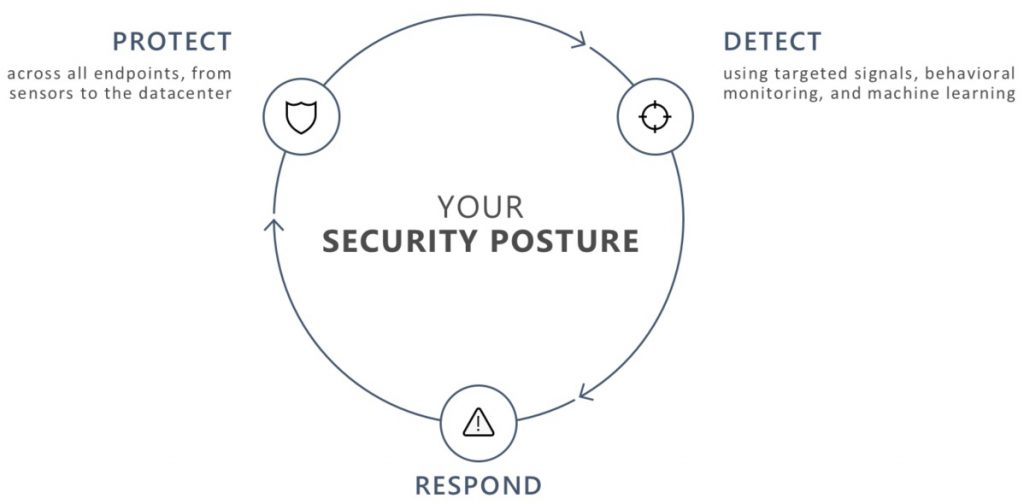
Monitoring devices in a hybrid environment is imperative to your secure posture. The intent of having a tight secure posture is to close the gap between discovering a threat and take an action to proper add countermeasures in place. Monitoring will play a big role in the detection phase of your secure posture as shown in the following diagram:
In a hybrid environment you can leverage OMS Security & Audit Solution detection capabilities to identify threats and use some of the guidelines provided by OMS to help you to proper respond to that threat. While there are some scenarios that the threat itself will be easily detected by OMS, in some others scenarios you may just receive an alert that a suspicious activity took place in a particular system. The intent of this post is to show you how to leverage some of the OMS Security & Audit capabilities to help you during this investigation.
Note: It is important to emphasize that you should always leverage your organization’s incident response process to proper handle case by case.
Following the warning sign
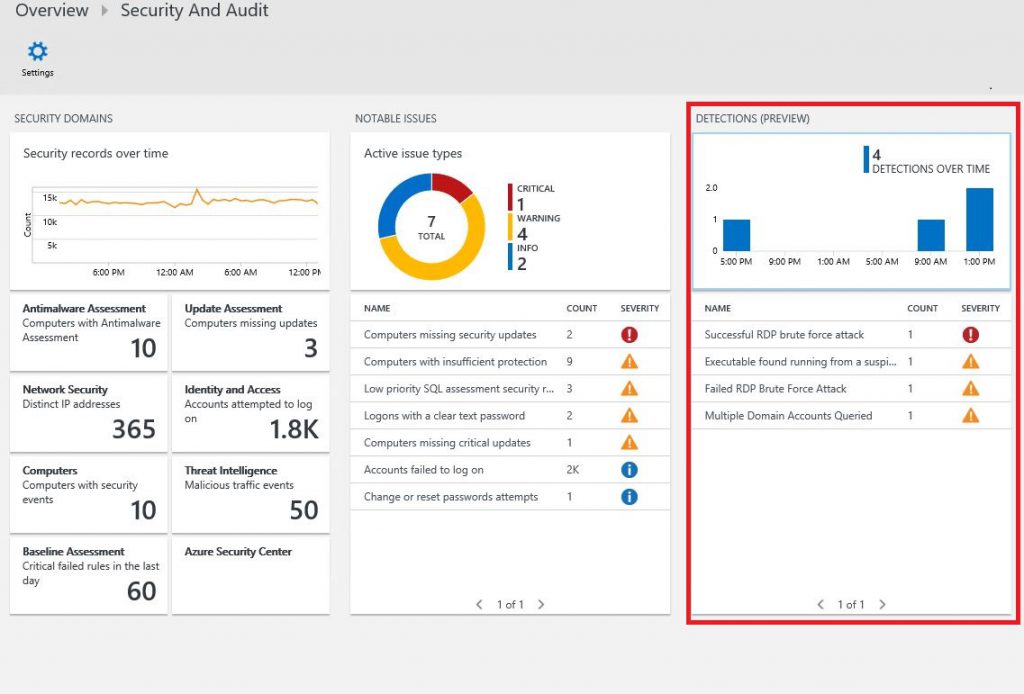
When trying to identify a suspicious activity, the first step is to open OMS Security & Audit dashboard, and in there look at the Detection (Preview) tile as shown below:
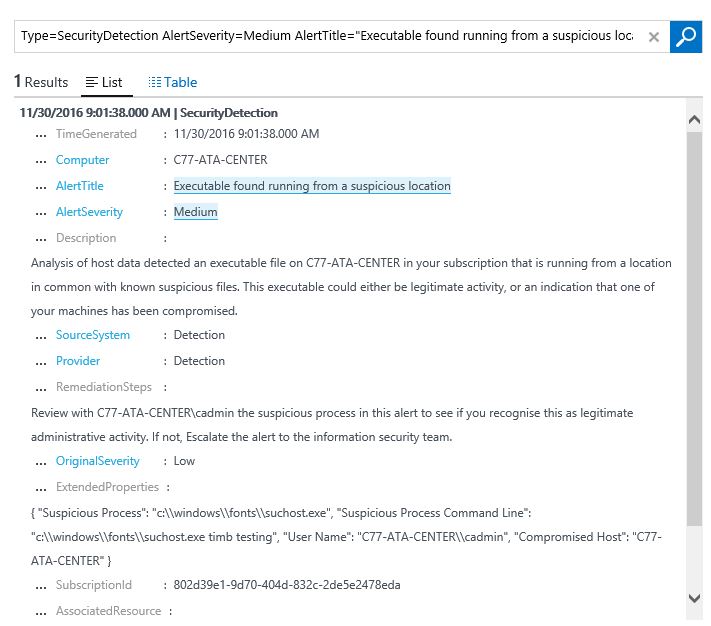
When reviewing the list of alerts, you should address the issues based on the severity, in other words, high (red) severity first. However, for the purpose of this example we will use the second detection, which is a medium (orange) alert. This detection says: “Executable found running from a suspicious location”. If you click on this alert you will see the search result for this query:
In this case there is a suspicious executable file (suchost.exe) located at c:\windows\fonts folder. The query result also shows the user that ran this executable, the time that was detected and the computer’s information. At this point you have enough information to perform your investigation at the target host and verify if this is a legitimate process or not.
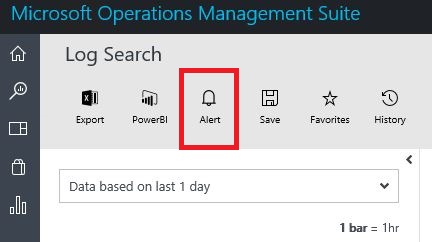
As a further measure, you can also configure OMS Security to send an email to you if this process is executed again, in any computer monitored by OMS. To do that click in the Alert button in the same search page that you found the suspicious activity.
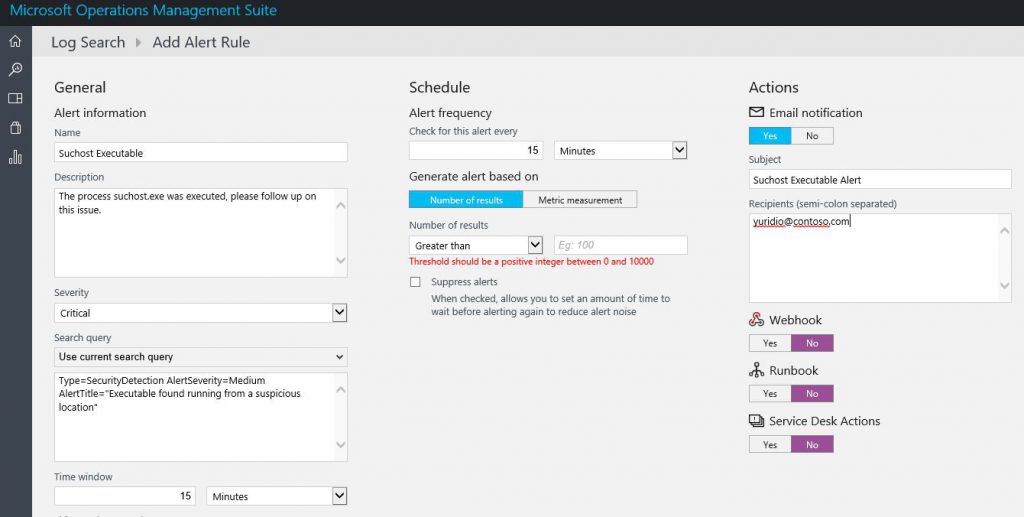
The Add Alert Rule page will open and you can customize the fields according to your need. Below you have an example of a rule for this suspicious process:
Once you finish customizing the options, click Save.
More information
For more information (and demonstration) about how to use OMS Security for Incident Response scenarios, watch this presentation from Ignite 2016:
[embed]https://youtu.be/QK3qxheUdBA[/embed]
Stay alert!
Yuri Diogenes
Senior Content Developer, CSI Enterprise Mobility + Security (Azure Security and OMS Security)
@yuridiogenes