Windows Right Management: Helping Organizations Safeguard Digital Information From Digital Use
Microsoft Windows Rights Management Services for Windows Server 2003
Helping Organizations Safeguard Digital Information from Unauthorized Use
Microsoft Corporation
Published: October 2003
Updated: April 2005
** **
Abstract
The dramatic rise in cyber crime and the emergence of related new legislative requirements point to the need for better means to protect digital information. While organizations such as financial institutions, government agencies, healthcare organizations, and professional services firms address many security concerns adequately, their strategies usually focus on access and delivery of information. To augment perimeter-based (firewalls, repositories) or transport-based (encrypted delivery) security technologies, there is a need to better protect information after it has been accessed by or delivered to an authorized individual, helping to prevent sensitive information from intentionally or accidentally getting into the wrong hands.
This paper discusses Microsoft® Windows® Rights Management Services (RMS) for Windows ServerTM 2003 with Service Pack 1 (SP1) and related technologies. RMS is information protection technology that works with RMS-enabled applications to help safeguard digital information from unauthorized use–both online and offline, inside and outside of the firewall.
This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein.
The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.
This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT.
Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred.
© 2005 Microsoft Corporation. All rights reserved.
Microsoft, Active Directory, SharePoint, Windows, the Windows logo, Windows Media, Windows NT, and Windows Server are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
*The names of actual companies and products mentioned herein may be the trademarks of their respective owners. *
Introduction: Safeguarding Digital Information in an Increasingly Connected World
Loss of confidential information is causing significant damage to organizations. In January 2003, The New York Times reported on the “exponential” increase in computer-related crimes, citing “a tightening economy, the increasing riches flowing through cyberspace, and the relative ease of such crimes” as some of the reasons computer-savvy outsiders as well as corporate employees make off with confidential information. Worldwide losses due to cyber crime (crime related to computers, technology, and the Internet) are estimated in the millions or even billions of dollars a year.1
All digital information is susceptible to attack. That includes everything from confidential meeting notes and customer-facing online content to military defense strategies and other classified government information.
In addition to the threat of computer-related crime, the finance, government, healthcare, and legal sectors are increasingly challenged by the need to tighten protections for digital information to comply with emerging legislative standards. The Healthcare Insurance Portability and Accessibility Act (HIPAA)2 and the Gramm-Leach-Bliley Act (GLBA)3 in the financial services industry are some relatively recent legislative measures that require enterprises to take specific steps to protect digital information.
Why Current Solutions Cannot Address This Growing Problem
The information technology industry has worked diligently to keep up with the increasing need to safeguard digital information. Network access can be limited with firewalls; access to certain digital information can be restricted with access control lists (ACLs). Such technologies meet important needs. Strategies that rely solely on such perimeter-based methods resemble an egg: If the network “shell” is cracked, digital information could be exposed. If someone does gain access to the network, there is currently no additional layer of protection.
Secure/Multipurpose Internet Mail Extensions (S/MIME), which is an Internet Engineering Task Force (IETF) standard based on X.509 certificates and a Public Key Infrastructure (PKI) implementation, provides digital signing, non-repudiation, and point-to-point encryption. S/MIME is a valuable and widely used application protocol to attest to the identity of the sender, to keep e-mail secure while in transit, and to validate the credentials of the recipient. However, recipients are still free to do whatever they want with any information that falls into their hands. For example, it could be forwarded to another person, copied to another computer, or posted online. Even accidental security breaches can cause serious harm to an organization. Sensitive e-mail or documents could be forwarded mistakenly to a recipient with potentially malicious intent.
In many cases, information is at risk within the firewall perimeter once employees transport that information from corporate servers to their own desktops, laptops, or when it is saved to some form of removable media such as CD-ROM or USB flash memory stick. The risk is magnified once employees transport information beyond the corporate firewall. The laptop or removable media could easily be lost, stolen, or given to an individual that is not authorized to view the information. Today’s perimeter-based solutions are unable to help protect information after it has been accessed or delivered to an authorized individual. For a more comprehensive solution, organizations need technology that will help them safeguard information--no matter where it goes.
Introducing RMS in the Windows Platform
More and more organizations are using and forwarding information digitally, which increases the risk of information leaks. Microsoft has heard from customers that they need new ways to help safeguard sensitive information such as customer data, financial reports, product specifications, and confidential e-mail messages from intentionally or accidentally getting into the wrong hands. RMS has been developed in response to that need and combines features of the Windows Server 2003 operating system with developer tools, and industry security technologies–including encryption, Extensible Rights Markup Language (XrML)-based certificates, and authentication–to help create reliable information protection solutions.
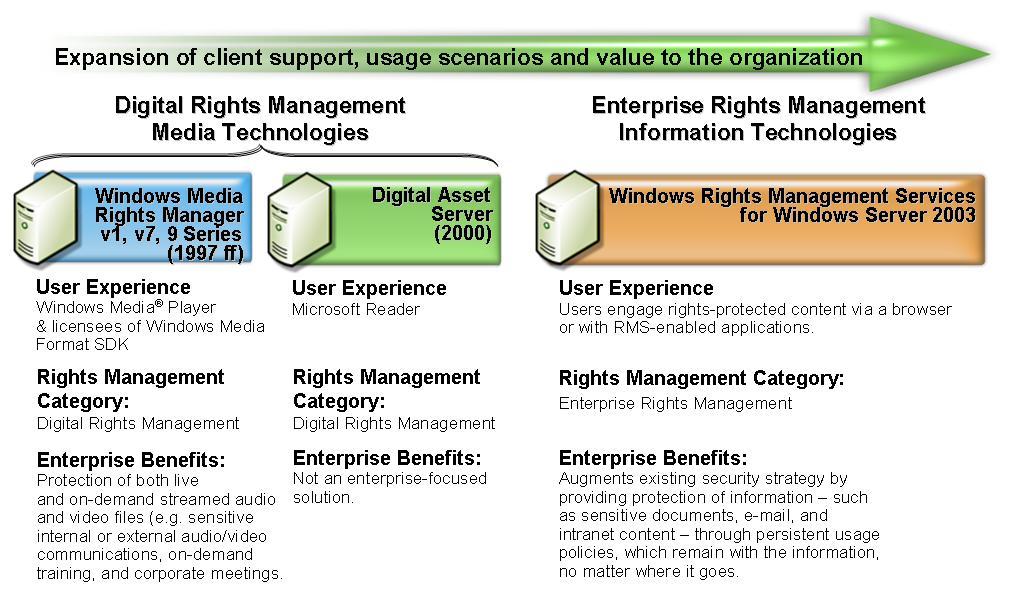
Windows RMS is the latest rights management technology to be released by Microsoft. Rights management is an industry category that represents the protection of various forms of digital assets. This category can be divided into digital rights management (DRM) and enterprise rights management. DRM is focused on protecting commercial media content and leverages Microsoft technologies such as Windows Media Rights Manager. Enterprise rights management is focused on protecting enterprise information and leverages the newly released Windows RMS to help organizations protect sensitive information from unauthorized use. Future sub-categories within rights management could include personal rights management to protect personal media such as family web sites and photos. Below is a diagram that shows how Windows RMS extends rights management scenarios beyond traditional media to help organizations protect sensitive information such as documents, emails, and intranet content.
Figure 1 Windows RMS extends digital rights protection beyond traditional media to help organizations protect information from unauthorized use.
RMS is information protection technology that works with RMS-enabled applications to help safeguard digital information from unauthorized use–both online and offline, inside and outside of the firewall. Information workers can define exactly how the recipient can use the information, such as who can open, modify, print, forward, and/or take other actions with the information. Organizations can create custom usage rights templates such as “Confidential - Read Only” that can be applied directly to information such as financial reports, product specifications, customer data, and e-mail messages. For example, RMS can help protect information in a wide range of situations, including the following:
- Intranet content. A manager within a large multinational pharmaceuticals company has been granted access to the online sales system. She navigates to the year-over-year sales information on the enterprise information portal, and the information is displayed on-screen within her RMS-enabled browser. Because the information is sensitive, specific usage restrictions have been applied to the report she sees. The manager gets the information she needs, conveniently, but because she does not have rights to print, copy, or paste the information on screen, the company’s sensitive sales data is better protected from inadvertent or deliberate sharing with an unauthorized individual.
- E-mail communications. A CEO needs to send an e-mail message that contains confidential information about an upcoming reorganization to his executive staff. In his RMS-enabled e-mail application, he selects a template to specify that recipients can only read the e-mail message, and that they cannot copy, paste, edit, or forward the information. The recipients receive the e-mail message and view it in an RMS-enabled e-mail application or browser, which transparently enforces the permissions. The CEO has a new level of confidence that this sensitive information will not be shared beyond his executive staff.
- Documents. Using a simple on-screen toolbar button or menu prompt built into her RMS-enabled word processor, a research manager at a manufacturing company rights-protects a new product research report to allow selected members of the product development team to preview and comment on the information for exactly one week. She sends the rights-protected document to multiple people via e-mail. When each person opens the document, their RMS-enabled word processor or browser enforces the rights assigned to the document, including the time-based conditions; after a week, the rights expire and these individuals can no longer open the document. The research manager then rights-protects and distributes the final version as company confidential read-only to the entire product development team. The research manager feels confident that the product development team only has access to the final information and that it is protected from unauthorized individuals, such as a competitor, viewing this information.
RMS protects through persistent usage policies that remain with information no matter where it goes. This helps organizations prevent sensitive information from intentionally or accidentally getting into the wrong hands. (The various RMS usage rights that can be applied to information are discussed in the section “The Benefits of RMS.”)
Windows RMS Components
Windows RMS technology includes client and server software along with SDKs.
- Windows RMS server software is a Web service for Windows Server 2003 that handles the XrML-based certification of trusted entities, licensing of rights-protected information, enrollment of servers and users, and administration functions.
- Windows Rights Management client software is a group of Windows APIs that facilitate the machine activation process and allow RMS-enabled applications to work with the RMS server to provide licenses for publishing and consuming rights-protected information.
- Software development kits (SDKs) for the server and client components include a set of tools, documentation, and sample code that enables software developers to customize their Windows RMS server environment and to create RMS-enabled applications.
For an end-to-end RMS solution, the following is necessary:
- Windows RMS for Windows Server 2003
- Windows Rights Management client software
- Windows RMS-enabled applications (such as Microsoft Office 2003 Editions) or an RMS-enabled browser (such as Microsoft Internet Explorer with the Rights Management Add-on) to create and/or view rights-protected information
Figure 2 illustrates the deployment of RMS server and client components.
Figure 2 Deployment of Windows RMS
- Server enrollment. An organization’s root Rights Management Services (RMS) server sends its public key along with the RMS version and URL information to the Server Enrollment Service to request an RMS Licensor Certificate.
- Client setup. Windows APIs that work with RMS-enabled applications are either installed by administrator as part of RMS rollout (via SMS or similar tool) or by downloading from Windows Update.
- Machine activation. As part of the client software instalation, each client machine connects to the organization’s RMS server for machine activation. The RMS server acts as a proxy for the client machine and acquires a unique lockbox and machine certificate from either the hosted Machine Activation Service or via a future hardware appliance that would live inside the organization’s network perimeter.
For added protection and interoperability, RMS uses the Extensible Rights Markup Language (XrML), an emerging rights expression language (REL) standard based on XML. XrML offers a common, simple-to-use means for applying rights and usage policies to digital information. It is a flexible, extensible, and interoperable standard equipped to meet any organization’s needs, regardless of industry, platform, format, media type, business model, or delivery architecture. (More information about XrML can be found in the appendix.)
RMS Workflow
Along with technology, people and processes are key ingredients in any security mix. By using tested and proven industry security technologies, including encryption, XrML-based certificates and authentication, RMS gives organizations the means to implement processes that empower people to better protect sensitive information.
RMS information protection is designed to be easy to use and transparent to users. To protect digital information with RMS, information workers simply follow the same logical and fundamentally interlinked workflow they already use with digital information.
- Creating rights-protected information. With RMS-enabled applications, users can easily create rights-protected information. The applications that people use every day—for example, computer-aided design (CAD) applications or Microsoft Office 2003 Editions—can incorporate Windows RMS functionality. Using common task management procedures within a familiar on-screen environment, users can easily assign usage policies to digital information, such as an e-mail message or document. Custom-built templates can be used to easily apply predefined organizational usage policies. Organizations can incorporate RMS into line-of-business applications which apply usage policies automatically, integrated into an existing workflow. And, through third-party solutions, organizations can also bring information protection to automated workflows.
- Licensing and distributing rights-protected information. After the user creates the document or file and defines the usage rights, the RMS system transparently issues a publishing license that contain the specified usage rights and conditions for the information. The information is then encrypted by the RMS-enabled application. After the information is encrypted or locked by this mechanism, only the trusted entities specified in the publishing licenses can unlock and use that information. The information can then be distributed using any standard method such as e-mail, a network share, a diskette, etc.
- Decrypting rights-protected information and usage policy enforcement. Recipients, who are named by the information author, can open or view rights-protected information by using trusted computers, which have the Windows Rights Management client software installed, along with an RMS-enabled application or browser. These applications enforce the usage rights which were defined by the author of the information. In a process that is transparent to the recipient, the RMS server validates the recipient and then issues a use license that contains the usage rights and conditions that were specified in the publishing license. The information is decrypted by the RMS-enabled application or browser and the usage rights and conditions are then enforced. The usage rights are persistent and enforced everywhere the information goes.
For a better understanding of the RMS workflow within an organization, see Figure 3.
Figure 3 RMS Workflow
- Authors receive a client licensor certificate from the RMS server the first time they rights-protect information. (This is a one-time step that enables offline publishing of rights-protected information in the future.)
- An author creates a file and defines a set of rights and rules. The RMS-enabled application in conjunction with the Windows Rights Management client software creates a “publishing license” and encrypts the file.
- The author can distribute the file in any preferred manner.
- The recipient clicks the file to open it. The RMS-enabled application calls to the RMS server, which validates the user and issues a use license.
- The application renders the file and enforces the rights defined in the use license.
The Benefits of RMS
RMS helps augment any organization’s security strategy and policies by providing information workers with a flexible, easy way to better protect digital information they commonly create and use everyday. For online information (such as information portals and/or database-backed dynamic content containing employee benefits and payroll information), as well as e-mail communications and documents, RMS will digitally help enforce policies such as restricting the ability to print, forward and edit data. Permissions can be set to expire at a specific point, such as a number of days after publishing. For highly sensitive information, permission can be set that require the user to be validated each time they open the information or at regular intervals. In addition, usage policies can be centrally defined and managed with RMS templates. Templates for policies such as “company confidential” or “attorney-client privilege” are easy to create and deploy, and ensure a consistent policy is exercised across an organization.
Information that is rights-protected using RMS technology is safer from being opened and used by unauthorized users. Rights-protected information is encrypted, and only users named in the publishing license will be able to open and use the rights-protected information. However, it is important to note that there is still a dependency on the authorized user to handle rights-protected information with appropriate sensitivity. While RMS can enforce an organization’s information usage policy, preventing the authorized user from inadvertently sharing the information, it cannot stop the authorized user from using analog methods to share the information, such as taking a photograph of their screen. The Windows print screen functionality is disabled when rights-protected information is open, but RMS technology does not stop third-party screen capture tools or products.
The RMS auditing feature provides an organization with the ability to view a comprehensive, internal log that tracks RMS licensing activity. If an organization utilizes the logging feature, a record will be made each time a use license (Figure 3, Step 4) is granted or denied. Should an information leak occur, the auditing feature can assist the organization in identifying where the breach occurred.
RMS can help organizations meet regulatory compliance requirements. RMS satisfies U.S. Federal Information Processing Standards (FIPS) compliance, using FIPS-certified cryptographic modules available in Windows. Through solutions developed by Microsoft technology partners, RMS enables e-mail archiving solutions to archive RMS-protected e-mail and facilitates information protection for the many organizations that must archive electronic communications in order to comply with the Sarbanes-Oxley Act or other regulations. Other third-party solutions make it possible to apply rights-protection policies to documents and records to protect intellectual property and sensitive information and, at the same time, meet compliance regulations.
Flexible and Customizable Technology
Organizations can manage digital information usage policies more effectively through centralized administration, custom usage policies, revocation and exclusion, and administrative override and decommissioning support. Through centrally defined and officially authorized rights policy templates, organizations can better manage confidentiality policies by providing information workers with a set of predefined usage templates. Administrators can centrally manage trust relationships via control of RMS credential issuance or revocation and exclusion policies. An organization can centrally maintain full control over all information that has been protected using their RMS server by designating administrative override rights to an individual or group of users or by decommissioning the RMS system.
RMS also offers flexible deployment options, from single-box deployments to global distributed topology, and provides the tools needed to deploy and use RMS in a wide variety of scenarios. RMS can easily scale up or out as needed and meet the needs of high-availability networks. Broad Windows client support, centralized Web-based administration, published client APIs, and Microsoft Active Directory® services integration work together to help make RMS flexible. Organizations can roll out RMS across networks with ease through Microsoft Systems Management Server or other software tools.
RMS delivers an extensive, scalable foundation for building RMS-enabled solutions. The RMS SDKs enable developers and organizations to RMS-enable their systems and applications. Support for XrML gives application developers the flexibility to provide a high level of granular rights and conditions for information protection. RMS technology can be seamlessly integrated into an application’s unique architecture, interface, and user experience. As a result, applications can present RMS usage policy options that are consistent with the user interface of the application.
Rights-protected information can be created and used while the user is either online or entirely offline. Protected information can be opened and used on multiple machines by the same user. To open rights-protected data, users simply click to open it. Credential and license management and the other technical considerations that help keep information safe are designed, for the most part, to be transparent to users.
Maintaining Existing Investments
RMS is designed to make the most of existing infrastructure investments. RMS integrates with Active Directory, which provides a unique identifier for each user. With the flexibility of Windows authentication, RMS can use smart card and biometric devices as well as other alternate authentication methods supported by Windows. With RMS SP1, third parties can integrate information protection with RMS into business critical applications for automation of workflows, central application of policy in records and document management systems, e-mail archiving, content inspection, and more. RMS also can integrate with content-inspection gateways, such as A/V scanners, so that organizations can consistently apply scanning and quarantine rules to RMS-protected content.
For recipients of rights-protected information who do not have a program that is RMS-enabled, the Rights Management Add-on (RMA) for Internet Explorer will add RMS features to the browser so Windows can be used to view rights-protected documents, including e-mail and other HTML information. The RMA for Internet Explorer will enable broad intranet scenarios by presenting rights-protected HTML to users.
The RMS SDKs are available to developers and ISVs to add RMS functionality to their programs so, in addition to Microsoft applications, non-Microsoft applications may incorporate RMS to help protect digital information. The resulting availability of enhanced RMS capabilities for both Microsoft and non-Microsoft applications enables diverse, multi-tiered solutions.
For organizations that maintain and operate customized internal programs and applications, the RMS SDKs provide the technology needed to help express, manage, and enforce information usage policies.
**Figure 4 ** RMS can help protect dynamically generated and distributed information
**(such as a web portal or database-driven applications). **
With these abilities, businesses as well as government agencies and not-for-profit organizations gain effective means to help safeguard digital information. In any market segment, RMS can be particularly effective in protecting the sensitive information used in complex collaborative processes. In many organizations, team collaboration involves heavy e-mail use, often combined with transfer of documents through instant messaging. Workers may include sensitive information in e-mails and exchange confidential files through instant messaging. For those organizations using a portal solution, such as Microsoft Office SharePoint® Portal Server 2003, RMS protects documents and information that reside on SharePoint sites, removing the need to create subwebs or intranets with special permissions just for certain documents. Types of sensitive documents and information in a number of industries include the following:
- inancial performance statistics, insurance claims and loan applications, cost forecasts, budgets, invoices, expense reports, and contracts.
- Operations. Quality control statistics, deployment plans and proposals, inventory data, benchmarking studies, production details, purchase orders, shipping reports, and enterprise resource planning (ERP) data.
- Sales. Responses to request-for-proposal (RFP) and request-for-information (RFI) documents, contracts, customer information, business plans, sales performance reports.
- medical records, employee and supplier performance analyses, employees’ personal information, and organizational announcements.
- Government. Outgoing RFPs and RFI documents as well as responses from vendors to RFPs and RFIs, staff performance evaluation information, and sensitive information related to public infrastructures.
- Legal organizations. Client communications and personal information pertaining to clients, court briefs and opinions, transcripts of hearings and testimony, contracts, and billing records.
- Manufacturing. Intellectual property in the form of product recipes or component specifics, proprietary process information, drawings and diagrams, costing information, test results, contracts and transactions with business partners and vendors.
- Not-for-profit organizations. Collaborative grant writing documents, grant management reports, financial documents, and member information.
- hite papers and official research reports, business development strategies, supplier information, cost-benefit analyses, production status reports, documentation and training manuals.
- Marketing and public relations. Brand strategy documents and brand assets, information about pricing and promotions, drafts of brochures and newsletters, presentations, press releases, testimonials, business plans, customer and constituent requirements and feedback.
Summary
More and more, the success of an organization depends on the ability to protect and manage digital information. Windows Rights Management Services (RMS) is information technology that works with any RMS-enabled application to help safeguard information from unauthorized use. Designed to make the most of existing infrastructure investments and to integrate easily with both Microsoft and non-Microsoft applications, along with other technology solutions, RMS fosters a new level of assurance that digital information will be better protected with persistent usage policies, which remain with the information—no matter where it goes.
Appendix: The Emerging Standard for RMS Interoperability
Microsoft is a strong believer in the benefits of industry standards and well-documented technical specifications, such as HTTP, TCP/IP and XML, which have been tested and reviewed by a standards organization. Industry standards must show technical competency. Therefore, standards organizations, such as the World Wide Web Consortium (W3C) and Moving Picture Experts Group (MPEG), review proposed standards to ensure that their developers have followed correct guidelines. In addition, standards organizations test proposed standards in numerous independent and networked scenarios.
Voluntary adherence to a standard rights expression language will develop critical enterprise rights management interoperability benefits that are currently latent. The emerging standard, XrML—which has been recognized by MPEG—offers many innate interoperability benefits. XrML provides digital properties with a simple-to-use, universal method for expressing rights linked to the use and protection of digital information, including Web services. Developers can integrate new and existing rights management systems easily with XrML. Moreover, XrML is currently the only rights expression language used in working rights management solutions. Microsoft, which has utilized XrML since its inception, looks forward to the many important benefits that enterprise rights management interoperability (based on the XrML standard) will bring to bear.
How XrML Works
XrML specifies a rights expression language that trusted systems within a trusted environment can use to express digital information policies. XrML licenses can be applied to trusted information in any format, such as e-mail, office productivity tools, database contents,
e-commerce downloads, line-of-business programs, and customer relationship management systems, to name a few. XrML licenses can then be enforced through any trusted rights management system that uses the XrML standard.
The rights to be managed are expressed in an XrML issuance license attached to the file. The issuance license is an expression of how the information owner wants their information to be used, protected, and shared. The issuance license and the user’s identity are passed to the rights management system, which builds a license.
These licenses are easily interpreted and managed by various interoperable rights management systems because they all use the XrML standard. Managing information online using licenses provides ease of access from any location. After the license is downloaded, the rights management is effective both online and offline because the rights persist with the file wherever it goes.
XrML supports an extensive list of rights, and applications can define additional rights to meet particular needs, which help ensure that organizations can build many business, usage, and workflow models to meet their specific requirements.
More information about XrML can be found at http://www.xrml.org.
Related Links
- Additional information about Microsoft Windows Rights Management Services is available online at http://microsoft.com/rms.
- Additional information about Microsoft products and security is available online at http://microsoft.com/security.
- Details about Microsoft products and privacy can be found at http://microsoft.com/privacy.
- Information about the Trustworthy Computing initiative can be found online at http://www.microsoft.com/mscorp/innovation/twc.
For the latest information about Windows Server 2003, see the Windows Server 2003 Web site at http://www.microsoft.com/windowsserver2003.
Windows Server System is the comprehensive, integrated
server software that simplifies the development, deployment, and operation of agile business solutions.
www.microsoft.com/windowsserversystem
1 “Crime Is Soaring in Cyberspace,” New York Times, Jan. 27, 2003, online edition.
2 Passed in 1996, HIPAA relates to healthcare coverage and, for example, how companies may use medical information.
3 Gramm-Leach-Bliley, also known as the Financial Services Modernization Act, was passed in 1999.
*