How to setup and collect network capture using Network Monitor tool
Network Monitoring is a Sniffing or Monitoring Program used to Identify and Isolate issues related to Networks or Applications communicating over a Network.
The Current Release for Network Monitor is 3.4 and can be downloaded here.
There are 3 versions available:
NM32_IA64_setup.exe 6.4 MB ---- Itanium Version.
NM32_x64_setup.exe 4.4 MB ---- 64bit Version.
NM32_x86_setup.exe 4.3 MB ---- 32bit Version.
Download the Version Compatible with the Server
Where the Sniffer is placed or which Computer Network Monitor is captured from is extremely vital in achieving the right diagnosis. In most scenarios, Capturing Network Monitor just from the 2 or more communicating Machines should be sufficient.
However, there may be a scenario for example, where one may wish to observe traffic from a machine whilst it is Booting. Obviously it is not possible to execute Network Monitor on that machine. To get around, the switch port to which the computer is connected is mirrored to another port on the switch.
We can now connect a laptop to the mirrored port and configure Network Monitor to run in a mode called Promiscuous on the laptop so as to now see packets from the Problem computer.
There may also be an intermittent issue which manifests once in a week or month for which the frequency/time of the issue cannot be predicted. It would be Resource Exhausting to execute Network Monitor on a computer for days waiting for an issue. In such cases, a light weight command line version of Network Monitor called nmcap can be leveraged to capture logs in a Circular or Chained format.
Let’s now look at how to Use the GUI version of Network Monitor:
- Once installed, launch Network Monitor.
The Launched GUI will have 3 screens: Recent Captures; Getting Started and Select Networks.
Let’s focus on the Select Networks Section:
Here we see a List of all the Network Cards from which traffic can be captured.
Notice the Highlighted P-Mode Button. Enabling it will Start Promiscuous Mode Captures.
Do Note that it is enabled per Network Interface and hence Care should be taken to enable it for the Correct Network Interface.

Once the Network Card has been Selected, Click New Capture to Create a New Capture Session:
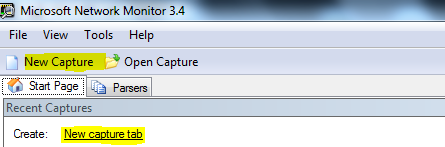
- That is basically it.
A Quick look at the Save Dialog Box:
Network Monitor files are saved in CAP format.
Either the all the Captured Packets can be saved or certain frames depending on what it is one is looking at and what filters have been applied.
We shall talk about Filters in another Post.

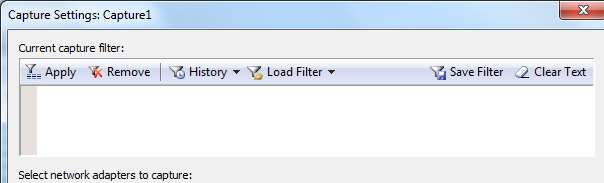
Before beginning a Capture, you may wish to set a Capture Filter in order to capture only certain kind of traffic based on protocols, IP Addresses etc. Below is a ScreenCap of the Capture Settings Window. Again we shall discuss filters in future posts.
Let’s now look at how to Use the NMCAP, the command line version of Network Monitor:
- First and foremost, launch a command prompt in Elevated Mode.
- Browse to C:\Program Files\Microsoft Network Monitor 3
- Executing the command nmcap will produce the below output:
C:\Program Files\Microsoft Network Monitor 3>nmcap
Network Monitor Command Line Capture (nmcap) 3.4.2350.0
NMCAP Version = 3.4.2350.0
Try using nmcap /Usage or nmcap /Examples for help.
*It will be useful to explore the output of nmcap /Usage and nmcap /Examples
For now let’s look at a few example commands to capture packets:
- nmcap /network * /capture /file c:\filename.cap:50M
The above command will capture packets from all Network Cards. The File will be limited to a size of 50MB and captured in a circular format.
- nmcap /network “Local Area Connection” /capture /file c:\filename.cap:50M
The above command will capture packets from the “Local Area Connection” network interface. The File will be limited to a size of 50MB and captured in a circular format.
- nmcap /network * /capture /file c:\filename.chn:50M
The above command will capture packets from all Network Cards. CHN specifies that the captures will be written to a chained series of files each limited to a size of 50MB each.
- nmcap /network * /capture “ipv4.address==1.1.1.1” /file c:\filename.cap:50M
In the above command a Capture filter has been specified. So only traffic that includes
the IP 1.1.1.1 as the Source or Destination for communication will be captured.
Cheers
Ajay Rodrigues