Blog Series: Get Familiar with the SDL-LOB Process, Introduction to Phase One: Requirements for LOB
Hello, Anmol here. For this blog series I’ll discuss the SDL-LOB process and cover all 5 phases as we go. In my last blog entry I provided an overview of this process, Blog Series: Get Familiar with the SDL-LOB Process . Today I’ll discuss Phase One: Requirements for LOB. As you read my blog series on the SDL-LOB process, I will try to share experiences and lessons learned from an information security group perspective.
Phase One: It’s is all about “Risk Assessment”
What we learned from our experiences working for more than 6 years now in securing Microsoft’s line of business applications is that effectively assessing risk is one of the stepping stones for managing a big portfolio of applications in an enterprise. We have an inventory of more than 3500 applications which have different security and privacy needs. As you can imagine, it would have been impossible to manage such a large number of applications without effective –
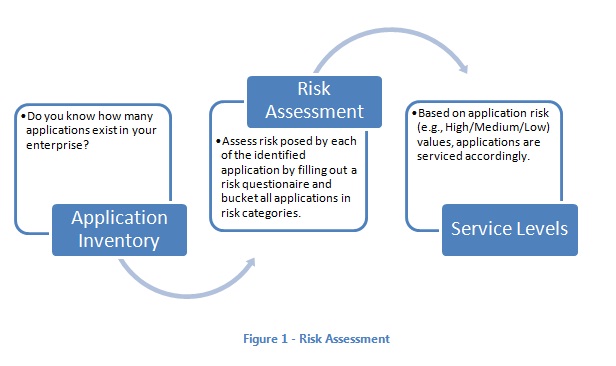
a) Application inventory
b) Risk Assessment
c) Service Levels
The following diagram summarizes key tasks in this phase:
Every organization is unique in how it measures and reacts to risk. However under the hood the basic principle for assessing risk remains consistent. When looking at application we first try to gather the following information.
a) Data: Type of data being handled by the application (is it sensitive, non sensitive, public, etc.)
b) Business: Business Unit being catered by the application (such as finance, HR, payroll or cafeteria)
c) Audience: Audience (users of the application) and hosting type (internal/external)
From a broader level, we are also trying to get a mind map of what will be the impact on the organization if the application got compromised.
a) Will this cause negative impact to the company’s reputation? (loss of customers, brand, etc.)
b) Will this cause negative business impact? (loss of revenue, sensitive data stolen, etc.)
As application data becomes more sensitive or the system becomes more critical to business, risk increases.
Whenever you’re working with risk, it’s most likely there will be a risk assessment in some form conducted. For the SDL-LOB process, a Risk Assessment questionnaire helps us capture general security and privacy ‘‘qualities” for the application. This allows us to determine the appropriate amount of “oversight” needed. Essentially we are trying to understand the potential risk the application poses for the enterprise. From a risk perspective, if an application is high risk, we’ll put forth more oversight and vice versa, if an application is low risk, it receives less oversight. Note that definition of what is “High” is also organization specific. You can create your own risk categories such as “Red/Orange/Green,” “High/Medium/Low,“ “Most Risky/Risky/Minimum Risk” - it’s all up to you. Identifying the most risky applications in an organization and spending the right resources, money and time to reduce the risk posed by them is the key here.
At Microsoft, risk assessment produces repeatable guidance on the type of oversight the application will receive in the SDL-LOB process. I encourage you to read the detailed requirements and recommendations for this Phase on Security Development Lifecycle 4.1 under SDL-LOB section.
Next time I'll talk about Phase Two: Design for LOB.
-Anmol Malhotra
Senior Security Engineer
ACE Team