Manage Application Control for Azure Local, version 23H2
Applies to: Azure Local, version 23H2
This article describes how to use Application Control to reduce the attack surface of Azure Local. For more information, see Manage baseline security settings on Azure Local, version 23H2.
Prerequisites
Before you begin, make sure that you have access to an Azure Local, version 23H2 instance that is deployed, registered, and connected to Azure.
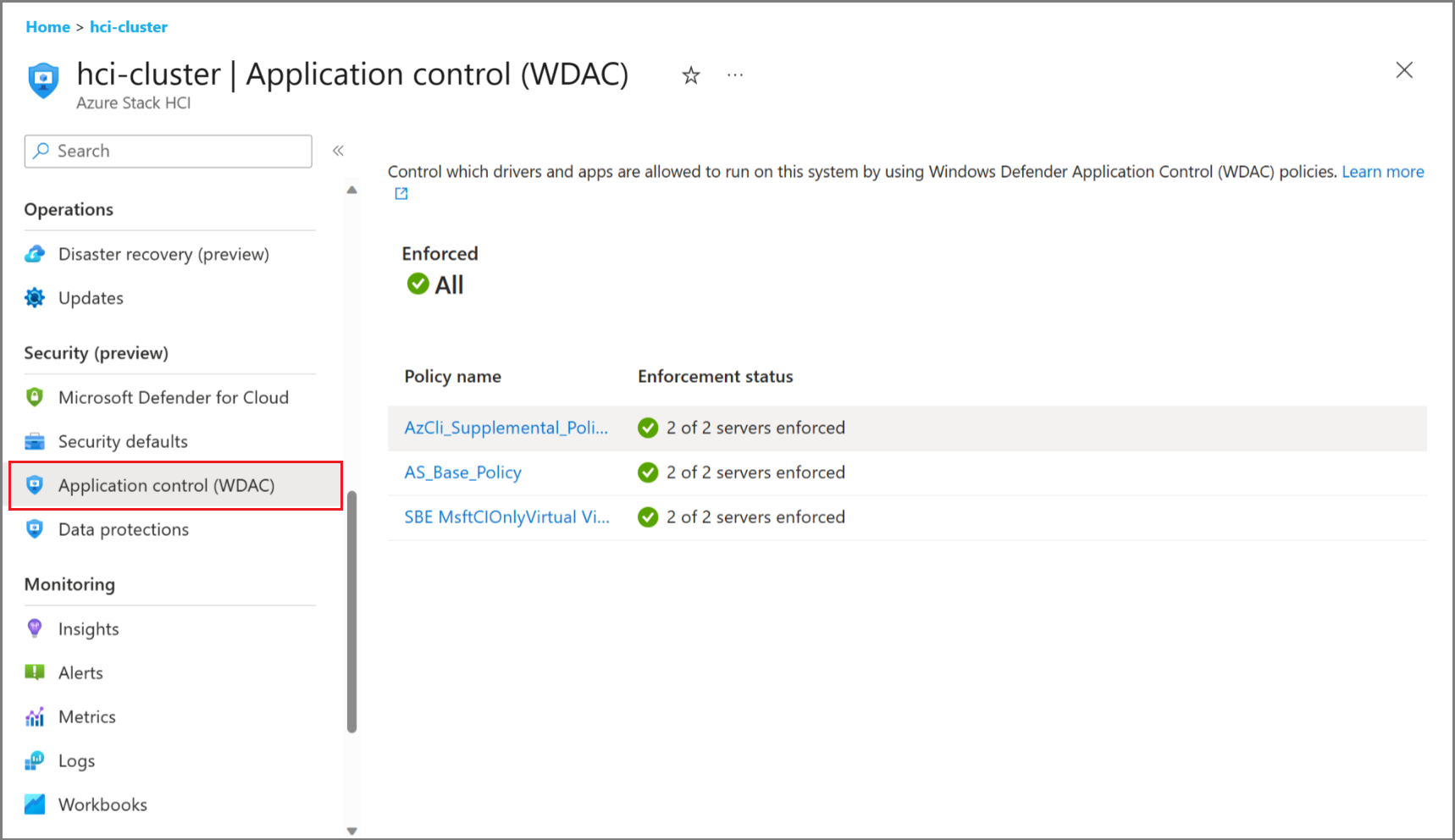
View Application Control settings via Azure portal
To view the Application Control settings in the Azure portal, make sure that you have applied the MCSB initiative. For more information, see Apply Microsoft Cloud Security Benchmark initiative.
You can use Application Control policies to manage which drivers and apps are allowed to run on your system. You can only view Application Control settings via Azure portal. To manage the settings, see Manage Application Control settings with PowerShell.
Manage Application Control settings with PowerShell
Enable Application Control policy modes
You can enable Application Control during or after deployment. Use PowerShell to enable or disable Application Control after deployment.
Connect to one of the machines and use the following cmdlets to enable the desired Application Control policy in "Audit" or "Enforced" mode.
In this build release there are two cmdlets:
Enable-AsWdacPolicy- Affects all cluster nodes.Enable-ASLocalWDACPolicy- Affects only the node on which the cmdlet is run.
Depending on your use case, you should run a global cluster change or a local node change.
This is useful when:
- You started with default, recommended settings.
- You must install or run new third party software. You can switch your policy modes to create a supplemental policy.
- You started with Application Control disabled during deployment and now you want to enable Application Control to increase security protection or to validate that your software runs properly.
- Your software or scripts are blocked by Application Control. In this case you can use audit mode to understand and troubleshoot the issue.
Note
When your application is blocked, Application Control creates a corresponding event. Review the Event log to understand details of the policy that's blocking your application. For more information, see the Application Control operational guide.
Switch Application Control policy modes
Follow these steps to switch between Application Control policy modes. These PowerShell commands interact with the Orchestrator to enable the selected modes.
Connect to your Azure Local machine.
Run the following PowerShell command using local administrator credentials or deployment user (AzureStackLCMUser) credentials.
Run the following cmdlet to check the Application Control policy mode that is currently enabled:
Get-AsWdacPolicyModeThis cmdlet returns Audit or Enforced Mode per Node.
Run the following cmdlet to switch the policy mode:
Enable-AsWdacPolicy -Mode <PolicyMode [Audit | Enforced]>For example, to switch the policy mode to audit, run:
Enable-AsWdacPolicy -Mode AuditWarning
The Orchestrator will take up to two to three minutes to switch to the selected mode.
Run
Get-ASWDACPolicyModeagain to confirm the policy mode is updated.Get-AsWdacPolicyModeHere's a sample output of these cmdlets:
PS C:\> Get-AsWdacPolicyMode VERBOSE: Getting Application Control Policy Mode on Node01. VERBOSE: Application Control Policy Mode on Node01 is Enforced. VERBOSE: Getting Application Control Policy Mode on Node01. VERBOSE: Application Control Policy Mode on Node01 is Enforced. NodeName PolicyMode -------- ---------- Node01 Enforced Node01 Enforced PS C:\> Enable-AsWdacPolicy -Mode Audit WARNING: Setting Application Control Policy to Audit Mode on all nodes. This will not protect your system against untrusted applications VERBOSE: Action plan instance ID specified: 6826fbf2-cb00-450e-ba08-ac24da6df4aa VERBOSE: Started an action plan 6826fbf2-cb00-450e-ba08-ac24da6df4aa to set Application Control Policy to Audit Mode. 6826fbf2-cb00-450e-ba08-ac24da6df4aa PS C:\> Get-AsWdacPolicyMode VERBOSE: Getting Application Control Policy Mode on Node01. VERBOSE: Application Control Policy Mode on Node01 is Audit. VERBOSE: Getting Application Control Policy Mode on Node01. VERBOSE: Application Control Policy Mode on Node01 is Audit. NodeName PolicyMode -------- ---------- Node01 Audit Node01 Audit
Create an Application Control policy to enable third party software
While using Application Control in enforcement mode, for your non-Microsoft signed software to run, build on the Microsoft-provided base policy by creating an Application Control supplemental policy. Additional information can be found in the public Application Control documentation.
Note
To run or install new software, you might need to switch Application Control to audit mode first (see steps above), install your software, test that it works correctly, create the new supplemental policy, and then switch Application Control back to enforced mode.
Create a new policy in the Multiple Policy Format as shown below. Then use Add-ASWDACSupplementalPolicy -Path Policy.xml to convert it to a supplemental policy and deploy it across nodes in the cluster.
Create an Application Control supplemental policy
Use the following steps to create a supplemental policy:
Before you begin, install the software that will be covered by the supplemental policy into its own directory. It's okay if there are subdirectories. When creating the supplemental policy, you must provide a directory to scan, and you don't want your supplemental policy to cover all code on the system. In our example, this directory is C:\software\codetoscan.
Once you have all your software in place, run the following command to create your supplemental policy. Use a unique policy name to help identify it.
New-CIPolicy -MultiplePolicyFormat -Level Publisher -FilePath c:\wdac\Contoso-policy.xml -UserPEs -Fallback Hash -ScanPath c:\software\codetoscanRun the following cmdlet to modify the metadata of your supplemental policy:
# Path of new created XML) $policyPath = "c:\wdac\Contoso-policy.xml" # Set Policy Version (VersionEx in the XML file) $policyVersion = "1.0.0.1" Set-CIPolicyVersion -FilePath $policyPath -Version $policyVersion # Set Policy Info (PolicyName, PolicyID in the XML file) Set-CIPolicyIdInfo -FilePath $policyPath -PolicyID "Contoso-Policy_$policyVersion" -PolicyName "Contoso-Policy"Run the following cmdlet to deploy the policy:
Add-ASWDACSupplementalPolicy -Path c:\wdac\Contoso-policy.xmlRun the following cmdlet to check the status of the new policy:
Get-ASLocalWDACPolicyInfoHere's a sample output of these cmdlets:
C:\> Get-ASLocalWDACPolicyInfo NodeName : Node01 PolicyMode : Enforced PolicyGuid : {A6368F66-E2C9-4AA2-AB79-8743F6597683} PolicyName : AS_Base_Policy PolicyVersion : AS_Base_Policy_1.1.4.0 PolicyScope : Kernel & User MicrosoftProvided : True LastTimeApplied : 10/26/2023 11:14:24 AM NodeName : Node01 PolicyMode : Enforced PolicyGuid : {2112036A-74E9-47DC-A016-F126297A3427} PolicyName : Contoso-Policy PolicyVersion : Contoso-Policy_1.0.0.1 PolicyScope : Kernel & User MicrosoftProvided : False LastTimeApplied : 10/26/2023 11:14:24 AM