Microsoft Entra deployment scenario - Secure internet access based on business needs
The Microsoft Entra deployment scenarios provide you with detailed guidance on how to combine and test these Microsoft Entra Suite products:
- Microsoft Entra ID Protection
- Microsoft Entra ID Governance
- Microsoft Entra Verified ID (premium capabilities)
- Microsoft Entra Internet Access
- Microsoft Entra Private Access
In these guides, we describe scenarios that show the value of the Microsoft Entra Suite and how its capabilities work together.
- Microsoft Entra deployment scenarios introduction
- Microsoft Entra deployment scenario - Workforce and guest onboarding, identity, and access lifecycle governance across all your apps
- Microsoft Entra deployment scenario - Modernize remote access to on-premises apps with MFA per app
Scenario overview
In this guide, we describe how to configure Microsoft Entra Suite products for a scenario in which the fictional organization, Contoso, has strict default internet access policies and wants to control internet access according to business requirements.
In an example scenario for which we describe how to configure its solution, a Marketing department user requires access to social networking sites that Contoso prohibits for all users. Users can request access in My Access. Upon approval, they become a member of a group that grants them access to social networking sites.
In another example scenario and corresponding solution, a SOC analyst needs to access a group of high-risk internet destinations for a specific time to investigate an incident. The SOC analyst can make that request in My Access. Upon approval, they become a member of a group that grants them access to high-risk internet destinations.
You can replicate these high-level steps for the Contoso solution as described in this scenario.
- Sign up for Microsoft Entra Suite. Enable and configure Microsoft Entra Internet Access for desired network and security settings.
- Deploy Microsoft Global Secure Access clients on users' devices. Enable Microsoft Entra Internet Access.
- Create a security profile and web content filtering policies with a restrictive baseline policy that blocks specific web categories and web destinations for all users.
- Create a security profile and web content filtering policies that allow access to social networking sites.
- Create a security profile that enables the Hacking web category.
- Use Microsoft Entra ID Governance to allow users requesting access to access packages such as:
- Marketing department users can request access to social networking sites with a quarterly access review.
- SOC team members can request access to high-risk internet destinations with a time limit of eight hours.
- Create and link two Conditional Access policies using the Global Secure Access security profile session control. Scope the policy to groups of users for enforcement.
- Confirm that traffic is appropriately granted with traffic logs in Global Secure Access. Ensure that Marketing department users can access the access package in the My Access portal.
These are the benefits of using these solutions together:
- Least privilege access to internet destinations. Reduce internet resource access to only what the user requires for their job role through the joiner/mover/leaver cycle. This approach reduces end user and device compromise risk.
- Simplified and unified management. Manage network and security functions from a single cloud-based console, reducing complexity and cost of maintaining multiple solutions and appliances.
- Enhanced security and visibility. Enforce granular and adaptive access policies based on user and device identity and context, as well as app and data sensitivity and location. Enriched logs and analytics provide gain insights into network and security posture to more quickly detect and respond to threats.
- Improved user experience and productivity. Provide fast and seamless access to necessary apps and resources without compromising security or performance.
Requirements
This section defines the requirements for the scenario solution.
Permissions
Administrators who interact with Global Secure Access features require the Global Secure Access Administrator and Application Administrator roles.
Conditional Access (CA) policy configuration requires the Conditional Access Administrator or Security Administrator role. Some features might require more roles.
Identity Governance configuration requires at least the Identity Governance Administrator role.
Licenses
To implement all the steps in this scenario, you need Global Secure Access and Microsoft Entra ID Governance licenses. You can purchase licenses or obtain trial licenses. To learn more about Global Secure Access licensing, see the licensing section of What is Global Secure Access.
Users and devices prerequisites
To successfully deploy and test this scenario, configure for these prerequisites:
- Microsoft Entra tenant with Microsoft Entra ID P1 license. Purchase licenses or obtain trial licenses.
- One user with at least Global Secure Access Administrator and Application Administrator roles to configure Microsoft's Security Service Edge
- At least one user as client test user in your tenant
- One Windows client device with this configuration:
- Windows 10/11 64-bit version
- Microsoft Entra joined or hybrid joined
- Internet connected
- Download and install Global Secure Access Client on client device. The Global Secure Access Client for Windows article describes prerequisites and installation.
Configure Global Secure Access
In this section, we activate Global Secure Access through the Microsoft Entra admin center. We then set up the required initial configurations for the scenario.
- Sign in to the Microsoft Entra admin center as a Global Administrator.
- Browse to Global Secure Access > Get started > Activate Global Secure Access in your tenant. Select Activate to enable SSE features.
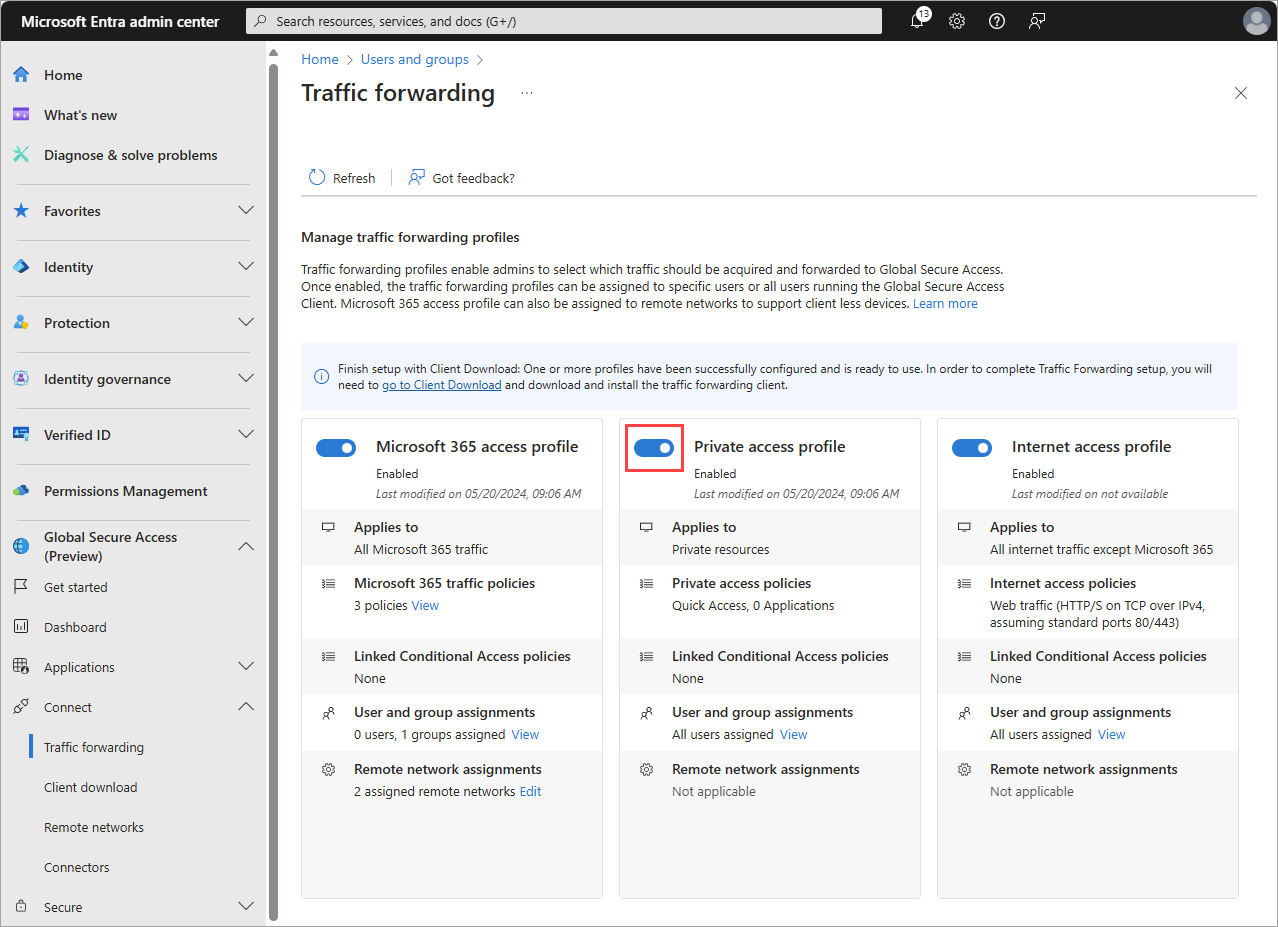
- Browse to Global Secure Access > Connect > Traffic forwarding. Toggle on Private access profile. Traffic forwarding enables you to configure the type of network traffic to tunnel through Microsoft's Security Service Edge Solution services. Set up traffic forwarding profiles to manage traffic types.
The Microsoft 365 access profile is for Microsoft Entra Internet Access for Microsoft 365.
The Private access profile is for Microsoft Entra Private Access.
The Internet access profile is for Microsoft Entra Internet Access. Microsoft's Security Service Edge solution only captures traffic on client devices with Global Secure Access Client installation.
Install Global Secure Access client
Microsoft Entra Internet Access for Microsoft 365 and Microsoft Entra Private Access use the Global Secure Access client on Windows devices. This client acquires and forwards network traffic to Microsoft's Security Service Edge solution. Perform these installation and configuration steps:
Ensure that the Windows device is Microsoft Entra joined or hybrid joined.
Sign in to the Windows device with a Microsoft Entra user with local admin privileges.
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
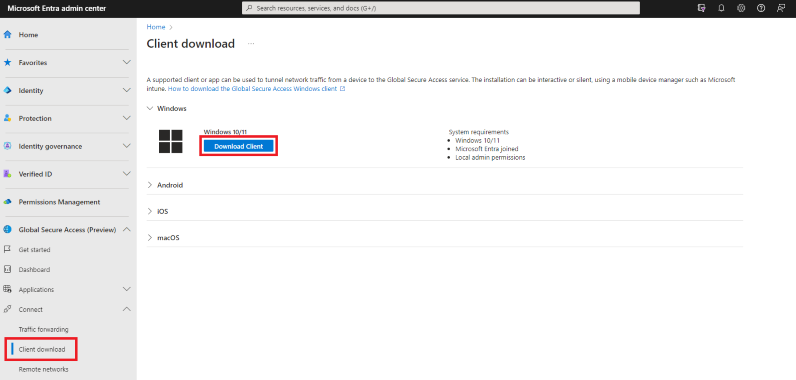
Browse to Global Secure Access > Connect > Client Download. Select Download client. Complete the installation.
In the Window taskbar, the Global Secure Access Client first appears as disconnected. After a few seconds, when prompted for credentials, enter test user's credentials.
In the Window taskbar, hover over the Global Secure Access Client icon and verify Connected status.
Create security groups
In this scenario, we use two security groups to assign security profiles using Conditional Access (CA) policies. In the Microsoft Entra admin center, create security groups with these names:
- Internet Access -- Allow Social Networking sites = Internet Access -- Allow Hacking sites
Don't add any members to these groups. Later in this article, we configure Identity Governance to add members on request.
Block access with baseline profile
In this section, we block access to inappropriate sites for all users in the organization with a baseline profile.
Create baseline web filtering policy
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Secure > Web content filtering policies > Create policy > Configure Global Secure Access content filtering.
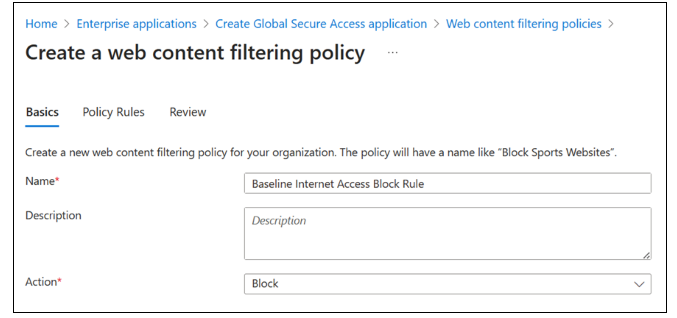
On Create a web content filtering policy > Basics, complete these fields:
Select Next.
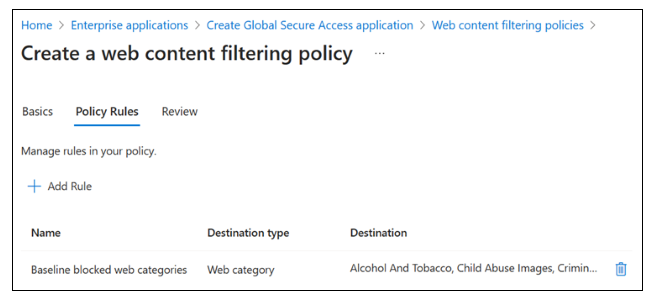
On Create a web content filtering policy > Policy Rules, select Add Rule.
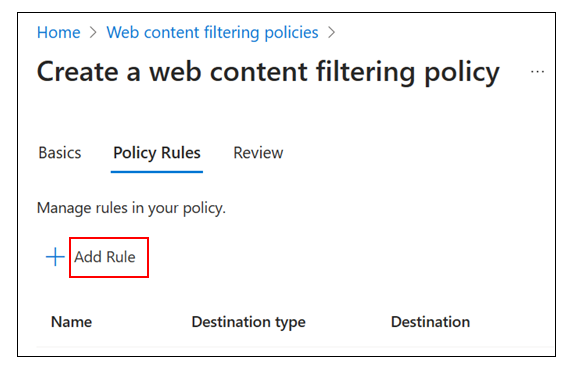
In Add Rule, complete these fields:
- Name: Baseline blocked web categories
- Destination type: webCategory
Search: Select the following categories. Confirm that they are in Selected items.
Alcohol and Tobacco
Criminal Activity
Gambling
Hacking
Illegal Software
Social Networking
Select Add.
On Create a web content filtering policy > Policy Rules, confirm your selections.
Select Next.
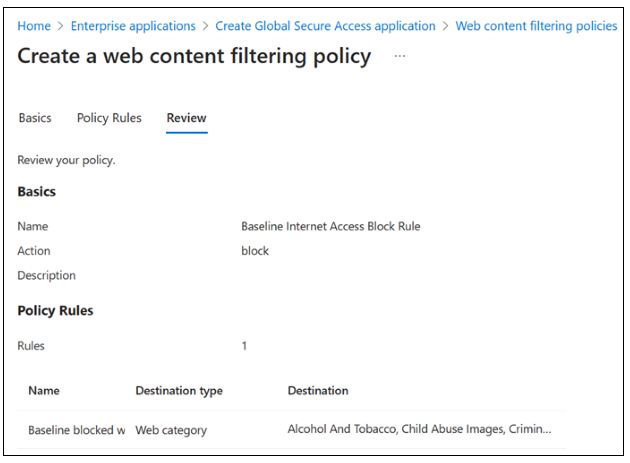
On Create a web content filtering policy > Review, confirm your policy configuration.
Select Create policy.
To confirm policy creation, view it in Manage web content filtering policies.
Configure baseline security profile
- Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
- Browse to Global Secure Access > Secure > Security profiles.
- Select Baseline Profile.
- On Basics, set State to enabled.
- Select Save.
- On Edit Baseline Profile, select Link policies. Select Link a policy. Select Existing policy. Complete these fields:
- Link a policy: Select Policy name and Baseline Internet Access Block Rule
- Priority: 100
- State: Enabled
- Select Add.
- On Create a profile > Link policies, confirm Baseline Internet Access Block Rule is listed.
- Close the baseline security profile.
Allow access to social networking sites
In this section, we create a security profile that allows access to social networking sites for users that request it.
Create social networking web filtering policy
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Secure > Web content filtering policies > Create policy > Configure Global Secure Access content filtering.
On Create a web content filtering policy > Basics, complete these fields:
- Name: Allow Social Networking sites
- Description: Add a description
- Action: Allow
Select Next.
On Create a web content filtering policy > Policy Rules, select Add Rule.
In Add Rule, complete these fields:
- Name: Social networking
- Destination type: webCategory
- Search: Social
Select Social Networking
Select Add.
On Create a web content filtering policy > Policy Rules, select Next.
On Create a web content filtering policy > Review, confirm your policy configuration.
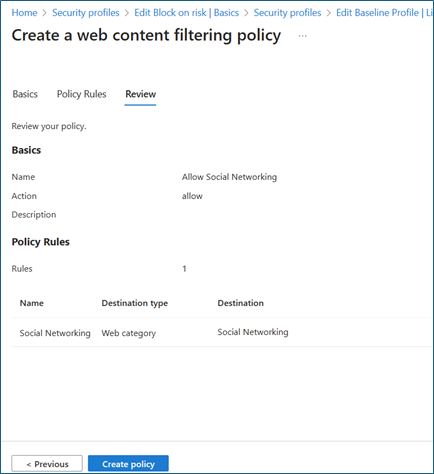
Select Create policy.
To confirm policy creation, view it in Manage web content filtering policies.
Create social networking security policy profile
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Secure > Security profiles. Select Create profile.
On Create a profile > Basics, complete these fields:
- Profile name: Allow Social Networking sites
- Description: Add a description
- State: Enabled
- Priority: 1000
Select Next.
On Create a profile > Link policies, select Link a policy.
Select Existing policy.
In Link a policy, complete these fields:
- Policy name: Allow Social Networking
- Priority: 1000
- State: Enabled
Select Add.
On Create a profile > Link policies, confirm Allow Social Networking is listed.
Select Next.
On Create a profile > Review, confirm your profile configuration.
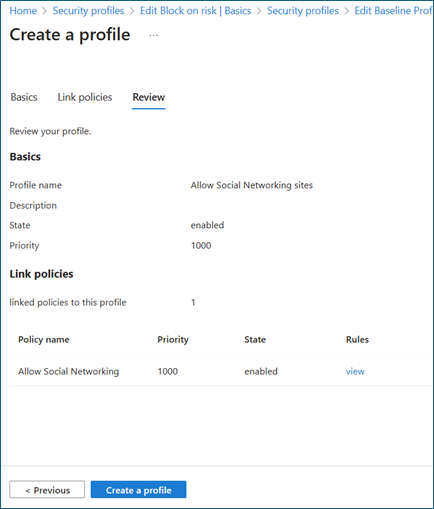
Select Create a profile.
Create social networking Conditional Access policy
In this section, we create a Conditional Access (CA) policy that enforces the Allow Social Networking security profile for users that request access.
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Protection > Conditional Access > Policies.
- Select New policy.
- In New Conditional Access Policy, complete these fields:
- Name: Internet Access -- Allow Social Networking sites
- Users or workload identities: Specific users included
- What does this policy apply to? Users and groups
- Include > Select users and groups > Users and groups
- Select your test group (such as Internet Access -- Allow Social Networking sites). Select Select.
- Target resources
- Select what this policy applies to > Global Secure Access
- Select the traffic profiles this policy applies to > Internet traffic
- Leave Grant at its default settings to grant access so that your defined security profile defines block functionality.
- In Session, select Use Global Secure Access security profile.
- Select Allow Social Networking sites.
- In Conditional Access Overview > Enable policy, select On.
- Select Create.
Allow access to hacking sites
In this section, we create a new security profile that allows access to hacking sites for users that request it. Users receive access for eight hours after which access is automatically removed.
Create hacking web filtering policy
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Secure > Web content filtering policies > Create policy > Configure Global Secure Access content filtering.
On Create a web content filtering policy > Basics, complete these fields:
- Name: Allow Hacking sites
- Description: Add a description
- Action: Allow
Select Next.
On Create a web content filtering policy > Policy Rules, select Add Rule.
In Add Rule, complete these fields:
- Name: Hacking
- Destination type: webCategory
- Search: Hacking, select Hacking
Select Add.
On Create a web content filtering policy > Policy Rules, select Next.
On Create a web content filtering policy > Review, confirm your policy configuration.
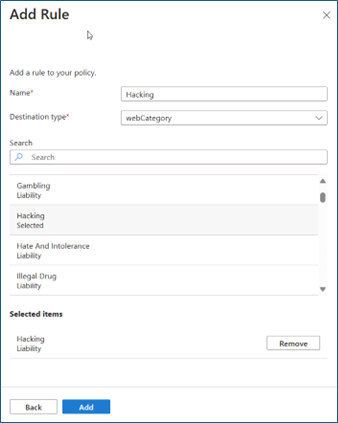
Select Create policy.
To confirm policy creation, view it in Manage web content filtering policies.
Create hacking security policy profile
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator.
Browse to Global Secure Access > Secure > Security profiles. Select Create profile.
On Create a profile > Basics, complete these fields:
- Profile name: Allow Hacking sites
- Description: Add a description
- State: Enabled
- Priority: 2000
Select Next.
On Create a profile > Link policies, select Link a policy.
Select Existing policy.
In the Link a policy dialog box, complete these fields:
- Policy name: Allow Hacking
- Priority: 2000
- State: Enabled
Select Add.
On Create a profile > Link policies, confirm Allow Hacking is listed.
Select Next.
On Create a profile > Review, confirm your profile configuration.

Select Create a profile.
Create hacking Conditional Access policy
In this section, we create a Conditional Access policy that enforces the Allow Hacking sites security profile for the users that request access.
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Protection > Conditional Access > Policies.
- Select New policy.
- In the New Conditional Access Policy dialog box, complete these fields:
- Name: Internet Access -- Allow Hacking sites
- Users or workload identities: Specific users included
- What does this policy apply to? Users and groups
- Include > Select users and groups > Users and groups
- Select your test group (such as Internet Access -- Allow Hacking sites) > select Select.
- Target resources
- Select what this policy applies to > Global Secure Access
- Select the traffic profiles this policy applies to > Internet traffic
- Leave Grant at its default settings to grant access so that your defined security profile defines block functionality.
- In the Session dialog box, select Use Global Secure Access security profile.
- Select Allow Hacking sites.
- In Conditional Access Overview > Enable policy, select On.
- Select Create.
Configure access governance
Follow these steps to create an entitlement management catalog:
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
Browse to Identity governance > Entitlement management > Catalogs.
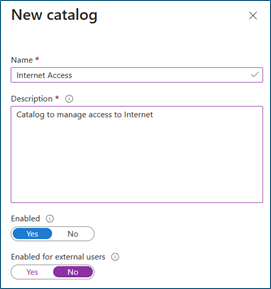
Select New catalog
Enter a unique name for the catalog and provide a description. Requestors see this information in an access package's details (for example, Internet Access).
For this scenario, we create access packages in the catalog for internal users. Set Enabled for external users to No.
To add the resources, go to Catalogs and open the catalog to which you want to add resources. Select Resources. Select Add resources.
Add the two security groups that you previously created earlier (such as Internet Access -- Allow Social Networking sites and Internet Access -- Allow Hacking sites).
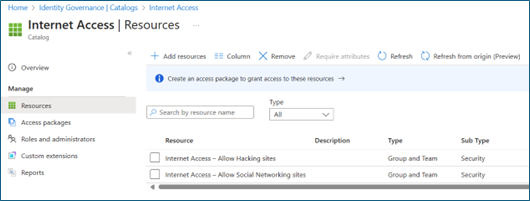
Create access packages
In this section, we create access packages that allow users to request access to the internet site categories that each security profile defines. Follow these steps to create an access package in Entitlement management:
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
Browse to Identity governance > Entitlement management > Access package.
Select New access package.
For Basics, give the access package a name (such as Internet Access -- Allow Social Networking sites). Specify the catalog that you previously created.
For Resource roles, select the security that you previously added (such as Internet Access -- Allow Social Networking sites).
In Role, select Member.
For Requests, select For users in your directory.
To scope the users that can request access to social networking sites, select Specific users and groups and add an appropriate group of users. Otherwise, select All members.
On Requests, select Yes for Enable new requests.
Optional: In Approval, specify whether approval is required when users request this access package.
For Lifecycle, specify when a user's assignment to the access package expires. Specify whether users can extend their assignments. For Expiration, set Access package assignments expiration to On date, Number of days, Number of hours, or Never.
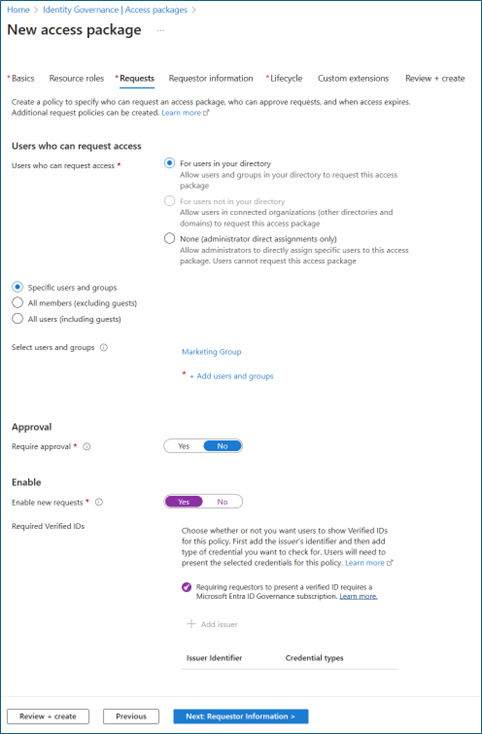
Repeat the steps to create a new access package that allows access to hacking sites. Configure these settings:
- Resource: Internet Access -- Allow Hacking sites
- Who can request: SOC team members
- Lifecycle: Set Number of hours to 8 hours
Test user access
In this section, we validate that the user can't access sites that the baseline profile blocks.
- Sign in to the device where you installed the Global Secure Access client.
- In a browser, go to sites that the baseline profile blocks and verify blocked access. For example:
hackthissite.orgis a free, safe, and legal training ground for security professionals to test and expand ethical hacking skills. This site is classified as Hacking.YouTube.comis a free video sharing platform. This site is classified as Social Networking.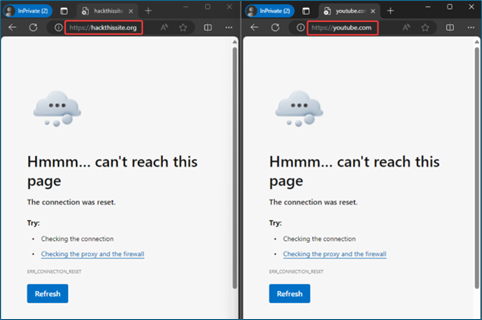
Request social networking access
In this section, we validate that a Marketing department user can request access to social networking sites.
Sign in to the device where you installed the Global Secure Access client with a user that is a member of the Marketing team (or a user that has authorization to request access to the example Internet Access -- Allow Social Networking sites access package).
In a browser, validate blocked access to a site in the Social Networking category that the baseline security profile blocks. For example, try accessing
youtube.com.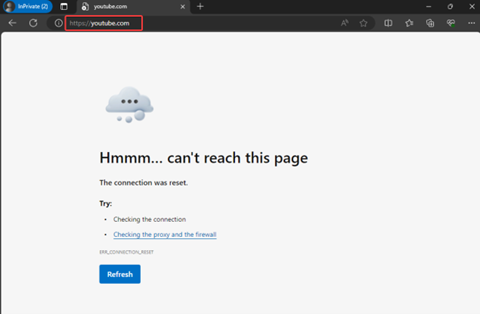
Browse to
myaccess.microsoft.com. Select Access packages. Select Request for the Internet Access -- Allow Social Networking sites access package.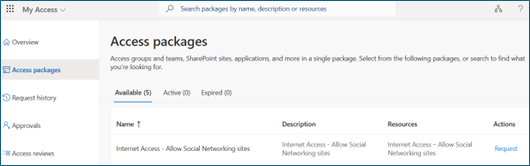
Select Continue. Select Request.
If you configured approval for the access package, sign in as an approver. Browse to
myaccess.microsoft.com. Approve the request.Sign in as a Marketing department user. Browse to
myaccess.microsoft.com. Select Request history. Validate your request status to Internet Access -- Allow Social Networking sites is Delivered.New settings might take a few minutes to apply. To speed up the process, right-click the Global Secure Access icon in the system tray. Select Log in as a different user. Sign in again.
Try accessing sites in the social networking category that the baseline security profile blocks. Validate that you can successfully browse them. For example, try browsing
youtube.com.
Request hacking site access
In this section, we validate that a SOC team user can request access to hacking sites.
Sign in to the device where you installed the Global Secure Access client with a user that is a member of the SOC team (or a user that has authorization to request access to the example Internet Access -- Allow Hacking sites access package).
In a browser, validate blocked access to a site in the hacking category that the baseline security profile blocks. For example,
hackthissite.org.
Browse to
myaccess.microsoft.com. Select Access packages. Select Request for the Internet Access -- Allow Hacking sites access package.Select Continue. Select Request.
If you configured approval for the access package, sign in as an approver. Browse to
myaccess.microsoft.com. Approve the request.Sign in as a SOC team user. Browse to
myaccess.microsoft.com. Select Request history. Validate your request status to Internet Access -- Allow Hacking sites is Delivered.New settings might take a few minutes to apply. To speed up the process, right-click the Global Secure Access icon in the system tray. Select Log in as a different user. Sign in again.
Try accessing sites in the hacking category that the baseline security profile blocks. Validate that you can successfully browse them. For example, try browsing
hackthissite.org.
If you configured hacking site access with Lifecycle > Number of hours set to 8 in previous steps, after eight hours elapses, verify blocked access to hacking sites.