Microsoft Entra deployment scenario - Modernize remote access to on-premises apps with MFA per app
The Microsoft Entra deployment scenarios provide you with detailed guidance on how to combine and test these Microsoft Entra Suite products:
- Microsoft Entra ID Protection
- Microsoft Entra ID Governance
- Microsoft Entra Verified ID (premium capabilities)
- Microsoft Entra Internet Access
- Microsoft Entra Private Access
In these guides, we describe scenarios that show the value of the Microsoft Entra Suite and how its capabilities work together.
- Microsoft Entra deployment scenarios introduction
- Microsoft Entra deployment scenario - Workforce and guest onboarding, identity, and access lifecycle governance across all your apps
- Microsoft Entra deployment scenario - Secure internet access based on business needs
Scenario: Modernize remote access with quick access
In this section, we describe how to configure Microsoft Entra Suite products for a scenario in which the fictional organization, Contoso, is upgrading their existing VPN solution. The new, scalable cloud-based solution helps them to move towards Secure Access Service Edge (SASE). To accomplish this objective, they deploy Microsoft Entra Internet Access, Microsoft Entra Private Access, and Microsoft Entra ID Protection.
Microsoft Entra Private Access provides users (whether in an office or working remotely) secure access to private corporate resources. Microsoft Entra Private Access builds on the Microsoft Entra application proxy to extend access to any private resource, independent of TCP/IP port and protocol.
Remote users can connect to private apps across hybrid and multicloud environments, private networks, and data centers from any device and network without requiring a VPN solution. The service offers per-app adaptive access based on Conditional Access (CA) policies for more granular security than a traditional VPN solution.
Microsoft Entra ID Protection cloud-based identity and access management (IAM) helps protect user identities and credentials from compromise.
You can replicate these high-level steps for the Contoso solution as described in this scenario.
- Sign up for Microsoft Entra Suite. Enable and configure Microsoft Entra Internet and Private Access to desired network and security settings.
- Deploy Microsoft Global Secure Access client on user devices and Microsoft Entra Private Access connectors on private networks. Include multicloud Internet-as-a-Service (IaaS)-based virtual networks to access apps and resources on Contoso networks.
- Set up private apps as Global Secure Access apps. Assign appropriate users and groups. Set up Conditional Access policies for those apps and users. With this setup, you can achieve minimum access by allowing access only to users and groups that require access.
- Enable Microsoft Entra ID Protection to allow administrators to investigate and remediate risks to keep organizations safe and secure. Risks can be fed into tools like Conditional Access to make access decisions and fed back to a security information and event management (SIEM) tool for investigation.
- Use enhanced logs and analytics from Microsoft Entra Internet Access, Microsoft Entra Private Access, and Microsoft Entra ID Protection to track and evaluate network and security status. This configuration helps your Security Operations Center (SOC) team to promptly detect and examine threats to prevent escalation.
Microsoft Entra Suite solutions offer these advantages over VPN:
- Easier and consolidated management
- Lower VPN costs
- Better security and visibility
- Smoother user experience and efficiency
- Preparedness for SASE
Requirements for remote access with quick access
This section defines the requirements for the scenario's solution.
Permissions for remote access with quick access
Administrators who interact with Global Secure Access features require the Global Secure Access Administrator and Application Administrator roles.
Conditional Access (CA) policy configuration requires the Conditional Access Administrator or Security Administrator role. Some features might require more roles.
Prerequisites for remote access with quick access
To successfully deploy and test this scenario, configure these prerequisites:
- Microsoft Entra tenant with Microsoft Entra ID P1 license. Configure Microsoft Entra ID to test Microsoft Entra ID Protection. Purchase licenses or obtain trial licenses.
- One user with at least Global Secure Access Administrator and Application Administrator roles to configure Microsoft's Security Service Edge
- At least one client test user in your tenant
- One Windows client device with this configuration:
- Windows 10/11 64-bit version
- Microsoft Entra joined or hybrid joined
- Internet connected and no corporate network access or VPN
- Download and install Global Secure Access Client on client device. The Global Secure Access Client for Windows article describes prerequisites and installation.
- To test Microsoft Entra Private Access, configure a Windows server to function as the resource server:
- Windows Server 2012 R2 or later
- A file share
- To test Microsoft Entra Private Access, configure a Windows server to function as the connector server:
- Windows Server 2012 R2 or later
- Network connectivity to Microsoft Entra service
- Ports 80 and 443 open to outbound traffic
- Allow access to required URLs
- Establish connectivity between connector server and application server. Confirm access to test application on the application server (for example, successful file share access).
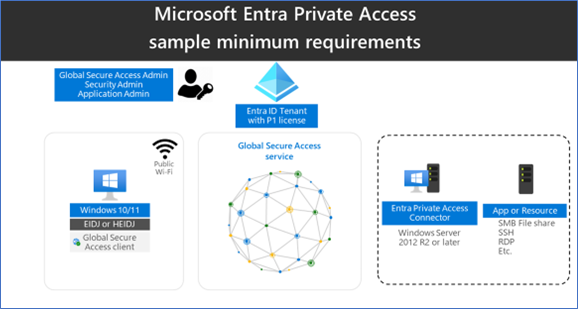
This diagram illustrates the minimum architecture requirements to deploy and test Microsoft Entra Private Access:
Configure Global Secure Access for remote access with quick access
In this section, we activate Global Secure Access through the Microsoft Entra admin center. We then set up initial configurations that this scenario requires.
- Sign in to the Microsoft Entra admin center as a Global Administrator.
- Browse to Global Secure Access > Get started > Activate Global Secure Access in your tenant. Select Activate to enable SSE features.
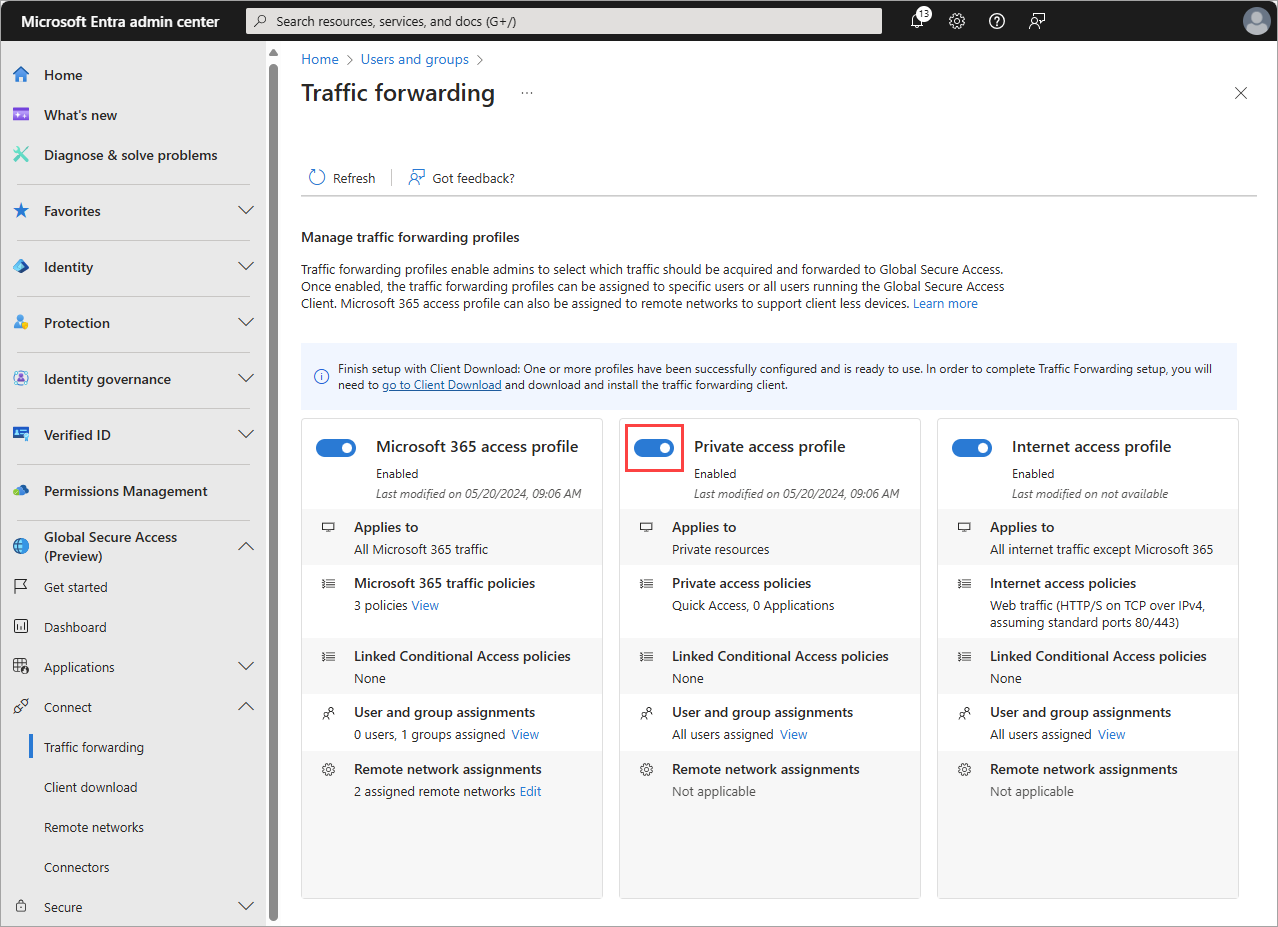
- Browse to Global Secure Access > Connect > Traffic forwarding. Toggle on Private access profile. Traffic forwarding enables you to configure the type of network traffic to tunnel through Microsoft's Security Service Edge Solution services. Set up traffic forwarding profiles to manage traffic types.
The Microsoft 365 access profile is for Microsoft Entra Internet Access for Microsoft 365.
The Private access profile is for Microsoft Entra Private Access.
The Internet access profile is for Microsoft Entra Internet Access. Microsoft's Security Service Edge solution only captures traffic on client devices with Global Secure Access Client installation.
Install Global Secure Access client for remote access with quick access
Microsoft Entra Internet Access for Microsoft 365 and Microsoft Entra Private Access use the Global Secure Access client on Windows devices. This client acquires and forwards network traffic to Microsoft's Security Service Edge Solution. Complete these installation and configuration steps:
Ensure that the Windows device is Microsoft Entra joined or hybrid joined.
Sign in to the Windows device with a Microsoft Entra user role with local admin privileges.
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
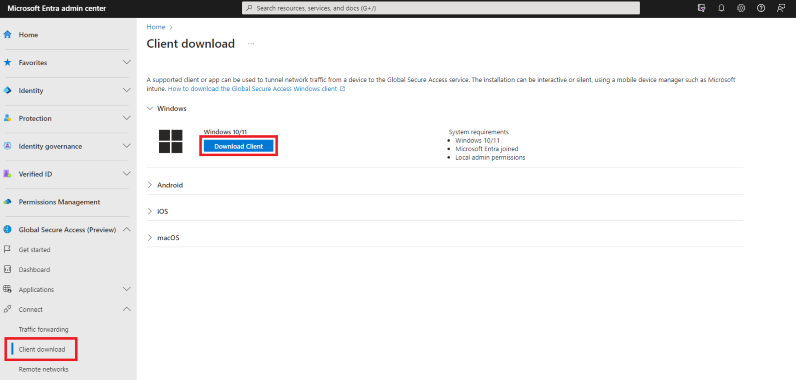
Browse to Global Secure Access > Connect > Client Download. Select Download client. Complete the installation.
In the Window taskbar, the Global Secure Access Client first appears as disconnected. After a few seconds, when prompted for credentials, enter test user's credentials.
In the Window taskbar, hover over the Global Secure Access Client icon and verify Connected status.
Set up connector server for remote access with quick access
The connector server communicates with Microsoft's Security Service Edge Solution as the gateway to the corporate network. It uses outbound connections through 80 and 443 and doesn't require inbound ports. Learn How to configure connectors for Microsoft Entra Private Access. Complete these configuration steps:
On the connector server, sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator.
Browse to Global Secure Access > Connect > Connectors. Select Enable Private Network connectors.
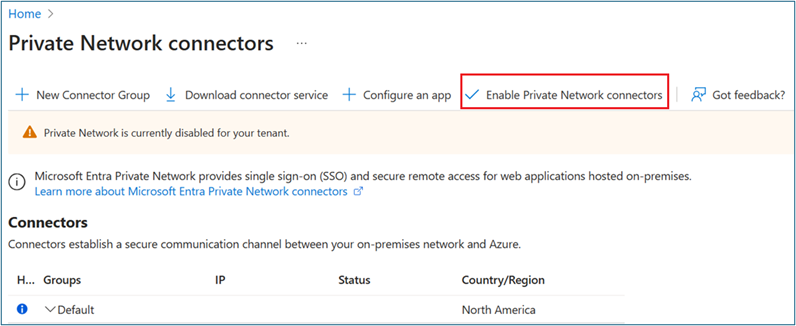
Select Download connector service.
Follow the installation wizard to install the connector service on the connector server. When prompted, enter tenant credentials to complete installation.
The connector server is installed when it appears in Connectors.
In this scenario, we use the default connector group with one connector server. In a production environment, create connector groups with multiple connector servers. See detailed guidance for publishing apps on separate networks by using connector groups.
Create security group for remote access with quick access
In this scenario, we use a security group to assign permissions to the Private Access application and to target Conditional Access policies.
- In the Microsoft Entra admin center, create a new cloud-only security group.
- Add test user as a member.
Determine private resource for remote access with quick access
In this scenario, we use file share services as a sample resource. You can use any private application or resource. You need to know which ports and protocols the application uses to publish it with Microsoft Entra Private Access.
Identify a server with a file share to publish and note its IP address. File share services use port 445/TCP.
Publish application for remote access with quick access
Microsoft Entra Private Access supports transmission control protocol (TCP) applications using any port. To connect to the file server (TCP port 445) over the internet, complete these steps:
From the connector server, verify that you can access a file share on the file server.
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Applications > Enterprise applications > + New Application.
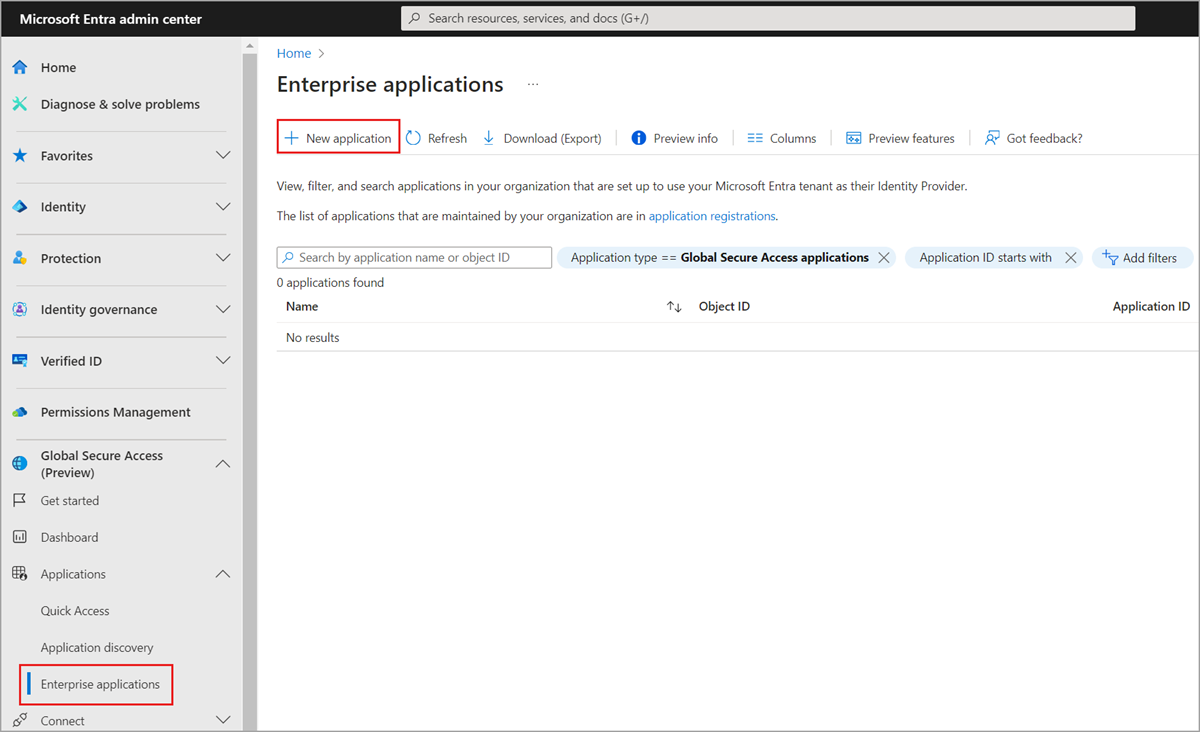
Enter a Name (such as FileServer1). Select the default connector group. Select +Add application segment. Enter the IP address of the application server and port 441.
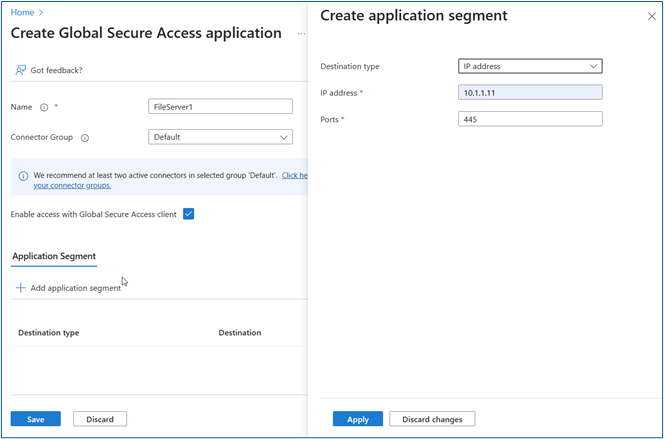
Select Apply > Save. Verify that the application is in Enterprise applications.
Go to Identity > Applications > Enterprise applications. Select the new application.
Select Users and groups. Add the security group that you created earlier with test users that access this file share from the internet.
Secure published application for remote access with quick access
In this section, we create a Conditional Access (CA) policy that blocks access to the new application when a user's risk is elevated.
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Protection > Conditional Access > Policies.
- Select New policy.
- Enter a name and select users. Select users and groups. Select the security group that you created earlier.
- Select Target resources > Apps and the application that you created earlier (such as FileServer1).
- Select Conditions > User risk > Configure > Yes. Select High and Medium risk levels. Select Done.
- Select Grant > Block access > Select.
- Toggle on Enable Policy.
- Review your settings.
- Select Create.
Validate access for remote access with quick access
In this section, we validate that the user can access the file server while there's no risk. Confirm that access is blocked when risk is detected.
Sign in to the device where you previously installed the Global Secure Access client.
Try to access the file server by running \
\\IP_addressand validate that you can browse the file share.
If desired, simulate user risk by following instructions in Simulating risk detections in Microsoft Entra ID Protection. You might need to try multiple times to raise user risk to medium or high.
Try accessing the file server to confirm that access is blocked. You might need to wait up to one hour for block enforcement.
Validate that the Conditional Access policy (that you created earlier using sign in logs) blocks access. Open non-interactive sign in logs from ZTNA Network Access Client -- Private application. View logs from the Private Access application name that you previously created as the Resource name.
Scenario: Modernize remote access per app
In this section, we describe how to configure Microsoft Entra Suite products for a scenario in which the fictional organization, Contoso, is transforming their cybersecurity practice. They adopt zero trust principles that verify explicitly, use least privilege, and assume breach across all applications and resources. In their discovery process, they identified multiple business applications that don't use modern authentication and rely on connectivity to the corporate network (either from their branch offices or remotely with VPN).
You can replicate these high-level steps for the Contoso solution as described in this scenario.
- To verify explicitly, configure Microsoft Entra ID Private Access to access the corporate network on a per-application basis. Use the unified set of access controls provided by Conditional Access and Microsoft Entra ID Protection to grant access to the corporate network based on identity, endpoint, and risk signal that they use with Microsoft 365 and other cloud applications.
- To enforce least privilege, use Microsoft Entra ID Governance to create access packages to include per-app network access alongside the applications that require it. This approach grants corporate network access to employees aligned with their job functions across their joiner/mover/leaver lifecycle.
As part of this transformation, SecOps teams achieve richer and more cohesive security analytics to better identify security threats. These are the benefits of using the solutions together:
- Enhanced security and visibility. Enforce granular and adaptive access policies based on identity and context of users and devices as well as application and data sensitivity and location. Use enriched logs and analytics to gain insights into network and security posture to detect and more quickly respond to threats.
- Least privilege access to on premises applications. Reduce access to corporate network only to what the applications require. Assign and govern access aligned with job function evolves through joiners/movers/leavers cycle. This approach reduces the risk of lateral movement attack vectors.
- Increase productivity. Cohesively enable access to applications and networks when users join the organization so they're ready to go on day one. Users have the correct access to information, group memberships, and applications that they need. Self-service capabilities for movers within the organization ensure access revocation when users leave the organization.
Requirements for remote access per app
This section defines the requirements for the scenario's solution.
Permissions for remote access per app
Administrators who interact with Global Secure Access features require the Global Secure Access Administrator and Application Administrator roles.
Identity Governance configuration requires at least the Identity Governance Administrator role.
Licenses for remote access per app
To implement all the steps in this scenario, you need Global Secure Access and Microsoft Entra ID Governance licenses. You can purchase licenses or obtain trial licenses. To learn more about Global Secure Access licensing, see the licensing section of What is Global Secure Access?.
Users for remote access per app
To configure and test the steps in this scenario, you need these users:
- Microsoft Entra administrator with the roles defined in Permissions
- On-premises Active Directory administrator to configure Cloud Sync and access to the sample resource (file server)
- A synchronized regular user to perform testing on a client device
Private Access prerequisites
To successfully deploy and test this scenario, configure these prerequisites.
- One Windows client device with this configuration:
- Windows 10/11 64-bit version
- Microsoft Entra joined or hybrid joined
- Internet connected and no corporate network access or VPN
- Download and install the Global Secure Access Client on the client device. The Global Secure Access Client for Windows article describes prerequisites and installation.
- To test Microsoft Entra Private Access, configure a Windows server to function as the resource server:
- Windows Server 2012 R2 or later
- A file share
- To test Microsoft Entra Private Access, configure a Windows server to function as the connector server:
- Windows Server 2012 R2 or later
- Network connectivity to Microsoft Entra service
- Ports 80 and 443 open to outbound traffic
- Allow access to required URLs
- Establish connectivity between the connector server and the application server. Confirm that you can access your test application on the application server (for example, successful file share access).
This diagram illustrates the minimum architecture requirements to deploy and test Microsoft Entra Private Access:

Determine private resource for remote access per app
In this scenario, we use file sharing services as a sample resource. You can use any private application or resource. You need to know which ports and protocols the application uses to publish it with Microsoft Entra Private Access.
Identify a server with a file share that you wish to publish and note its IP address. File share services use port 445/TCP.
Configure Global Secure Access for remote access per app
Activate Global Secure Access through the Microsoft Entra admin center and make required initial configurations for this scenario.
- Sign in to the Microsoft Entra admin center as a Global Administrator.
- Browse to Global Secure Access > Get started > Activate Global Secure Access in your tenant. Select Activate to enable SSE features in your tenant.
- Go to Global Secure Access > Connect > Traffic forwarding. Toggle on Private access profile. Traffic forwarding enables you to configure the type of network traffic to tunnel through Microsoft's Security Service Edge Solution services. Set up traffic forwarding profiles to manage traffic types.
The Microsoft 365 access profile is for Microsoft Entra Internet Access for Microsoft 365.
The Private access profile is for Microsoft Entra Private Access.
The Internet access profile is for Microsoft Entra Internet Access. Microsoft's Security Service Edge solution only captures traffic on client devices with Global Secure Access Client installation.
Install Global Secure Access client for remote access per app
Microsoft Entra Internet Access for Microsoft 365 and Microsoft Entra Private Access use the Global Secure Access client on Windows devices. This client acquires and forwards network traffic to Microsoft's Security Service Edge solution. Complete these installation and configuration steps:
Ensure that the Windows device is Microsoft Entra ID joined or hybrid joined.
Sign in to the Windows device with a Microsoft Entra ID user role with local admin privileges.
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator
Browse to Global Secure Access > Connect > Client Download. Select Download client. Complete the installation.
In the Window taskbar, the Global Secure Access Client first appears as disconnected. After a few seconds, when prompted for credentials, enter test user's credentials.
In the Window taskbar, hover over the Global Secure Access Client icon and verify Connected status.
Set up connector server for remote access per app
The connector server communicates with Microsoft's Security Service Edge solution as the gateway to the corporate network. It uses outbound connections through 80 and 443 and doesn't require inbound ports. Learn how to configure connectors for Microsoft Entra Private Access. Complete these configuration steps:
On the connector server, sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator.
Browse to Global Secure Access > Connect > Connectors. Select Enable Private Network connectors.

Select Download connector service.
Follow the installation wizard to install the connector service on the connector server. When prompted, enter tenant credentials to complete installation.
The connector server is installed when it appears in Connectors.
In this scenario, we use the default connector group with one connector server. In a production environment, create connector groups with multiple connector servers. See detailed guidance for publishing apps on separate networks by using connector groups.
Create Private Access application security group
In this scenario, we use a security group to assign permissions to the Private Access application and to target Conditional Access policies.
- In the Microsoft Entra admin center, create a new cloud-only security group.
- Add test user as a member.
Publish application for remote access per app
Microsoft Entra Private Access supports transmission control protocol (TCP) applications using any port. To connect to the file server (TCP port 445) over the internet, complete these steps:
From the connector server, verify that you can access a file share on the file server.
Sign in to the Microsoft Entra admin center as at least a Global Secure Access Administrator.
Browse to Global Secure Access > Applications > Enterprise applications > + New Application.

Enter a Name (such as FileServer1). Select the default connector group. Select +Add application segment. Enter the IP address of the application server and port 441.

Select Apply > Save. Verify that the application is in Enterprise applications.
Go to Identity > Applications > Enterprise applications. Select the new application.
Select Users and groups. Add the security group that you created earlier with test users that access this file share from the internet.
Configure access governance for remote access per app
In this section, we describe the configuration steps for this solution.
Create Entitlement management catalog
Follow these steps to create an Entitlement management catalog:
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
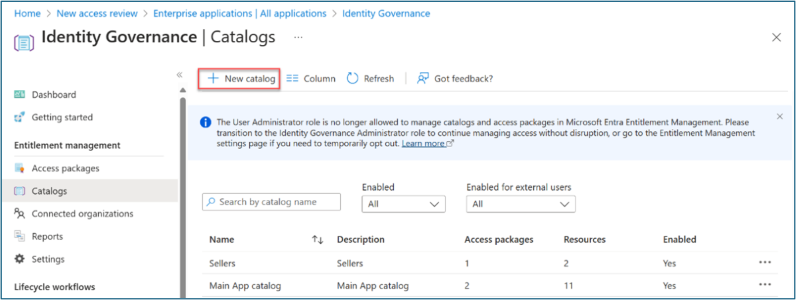
Browse to Identity governance > Entitlement management > Catalogs.
Select +New catalog.
Enter a unique name for the catalog and provide a description. Requestors see this information in the access package's details.
To create access packages in this catalog for internal users, select Enabled for external users > No.
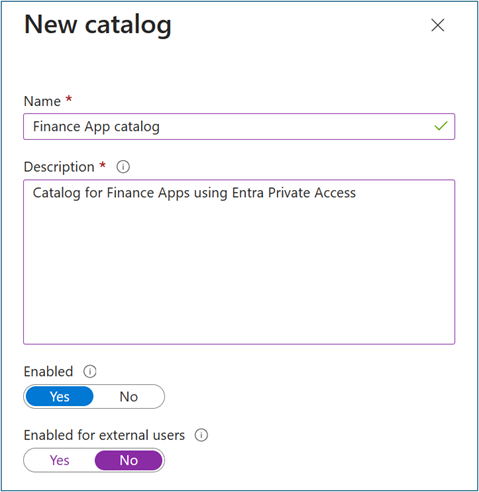
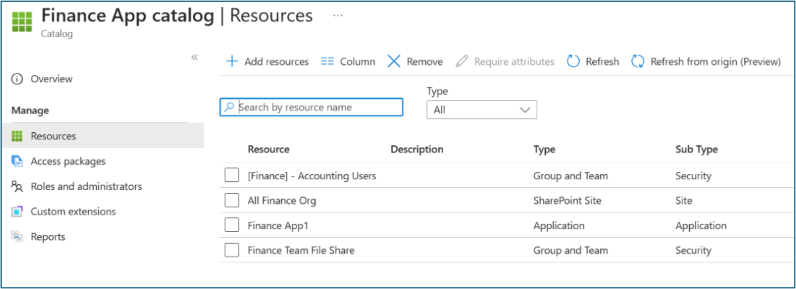
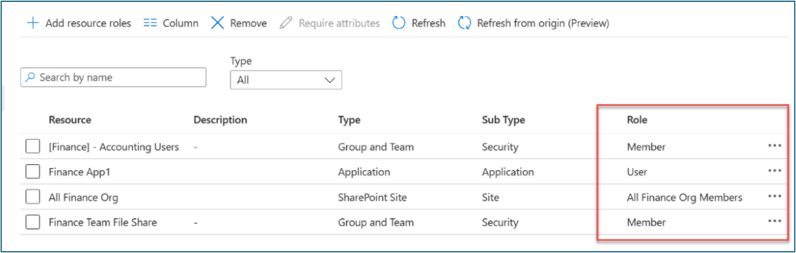
On Catalog, open the catalog to which you want to add resources. Select Resources > +Add resources.
Select Type, then Groups and Teams, Applications, or SharePoint sites.
Select and add the application (such as FileServer1) and security group (such as Finance Team File Share) that you previously created. Select Add.
Provision groups to Active Directory
We recommend group provisioning to Active Directory with Microsoft Entra Cloud Sync. If you use Connect Sync, switch your configuration to Cloud Sync. The Prerequisites for Microsoft Entra Cloud Sync in Microsoft Entra ID and How to install the Microsoft Entra provisioning agent articles provide detailed instructions. Group Writeback v2 in Microsoft Entra Connect Sync will no longer be available after June 30, 2024.
Follow these steps to configure Microsoft Entra Cloud sync:
Sign in to the Microsoft Entra admin center as at least a Hybrid Identity Administrator.
Browse to Identity > Hybrid management > Microsoft Entra Connect > Cloud sync.
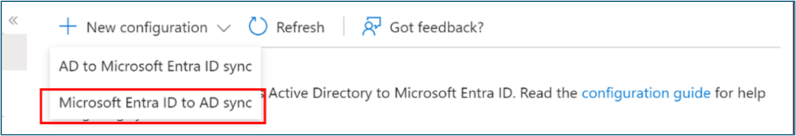
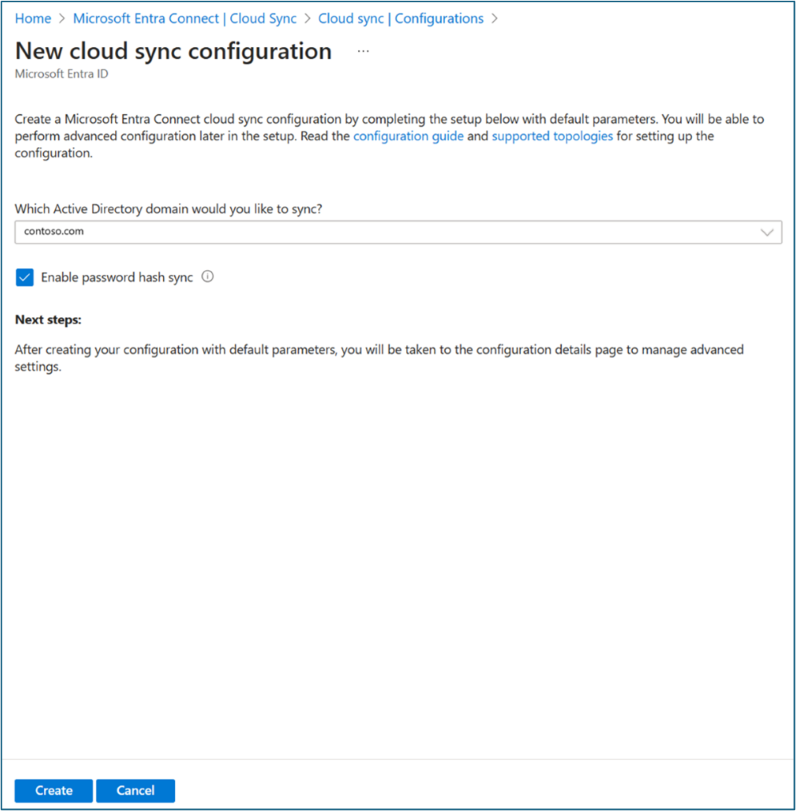
Select New configuration.
Select Microsoft Entra ID to AD sync.
On Configurations, select your domain. Optionally, select Enable password hash sync.
Select Create.
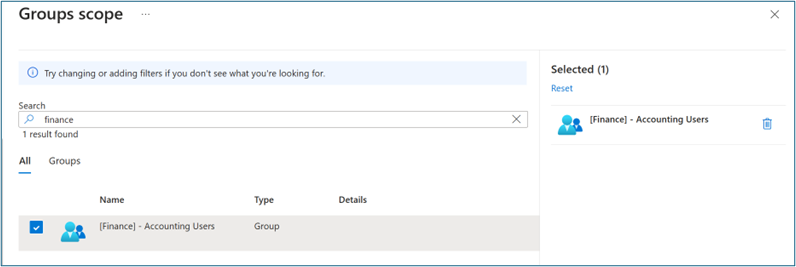
For Getting started configuration, select Add scoping filters (next to the Add scoping filters icon) or Scoping filters (under Manage).
Select Selected security groups in the Select group(s) option. Select Edit Objects. Add the Microsoft Entra ID security group that you previously created (such as Finance Team File Share). We use this group to manage access to on-premises applications using lifecycle workflows and access packages in later steps.
Assign access to on-premises file server
- Create a file share on the selected file server.
- Assign read permissions to the Microsoft Entra ID security group (such as Finance Team File Share) that you provisioned to Active Directory.
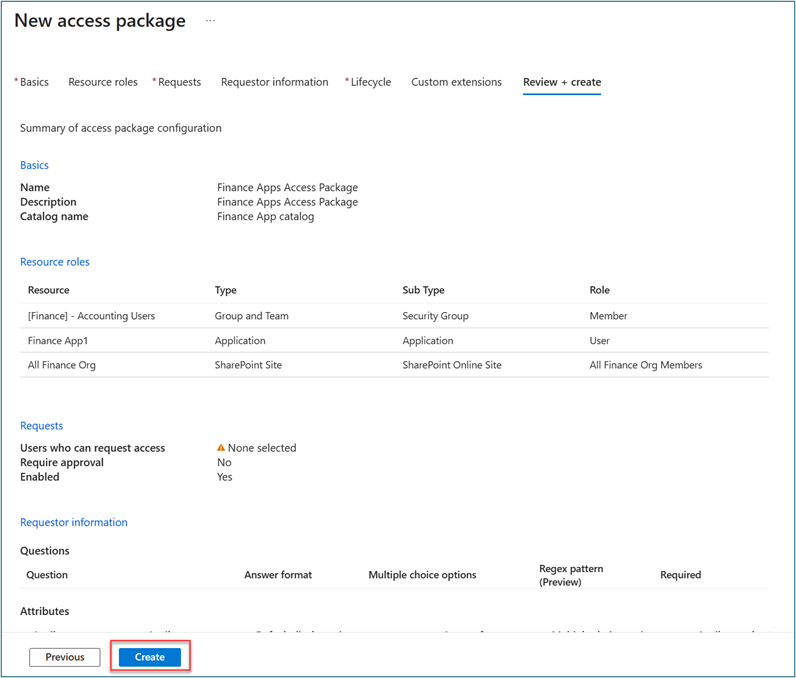
Create access package for remote access per app
Follow these steps to create an access package in Entitlement management:
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
Browse to Identity governance > Entitlement management > Access package.
Select New access package.
For Basics, give the access package a name (such as Finance Apps Access Package). Specify the catalog that you previously created.
For Resource roles, select the resources that you previously added (such as FileServer1 app and Finance Team File Share security group).
In Role, select Member for Finance Team File Share and User for FileServer1 app.
For Requests, select For users in your directory. Alternatively, enable the access package for Guest Users (to be discussed on a separate scenario).
If you selected Specific users and groups, select Add users and groups.
Don't select a user on Select users and groups. We test a user requesting access later.
Optional: In Approval, specify whether approval is required when users request this access package.
Optional: In Requestor information, select Questions. Enter a question that you want to ask the requestor. This question is known as the display string. To add localization options, select Add localization.
For Lifecycle, specify when a user's assignment to the access package expires. Specify whether users can extend their assignments. For Expiration, set Access package assignments expiration to On date, Number of days, Number of hours, or Never.
Select Create.
Create lifecycle workflows
In this section, we describe how to create joiner and leaver workflows and run workflows on demand.
Create joiner workflow
To create a joiner workflow, follow these steps.
Sign in to the Microsoft Entra admin center as at least a Lifecycle Workflows Administrator.
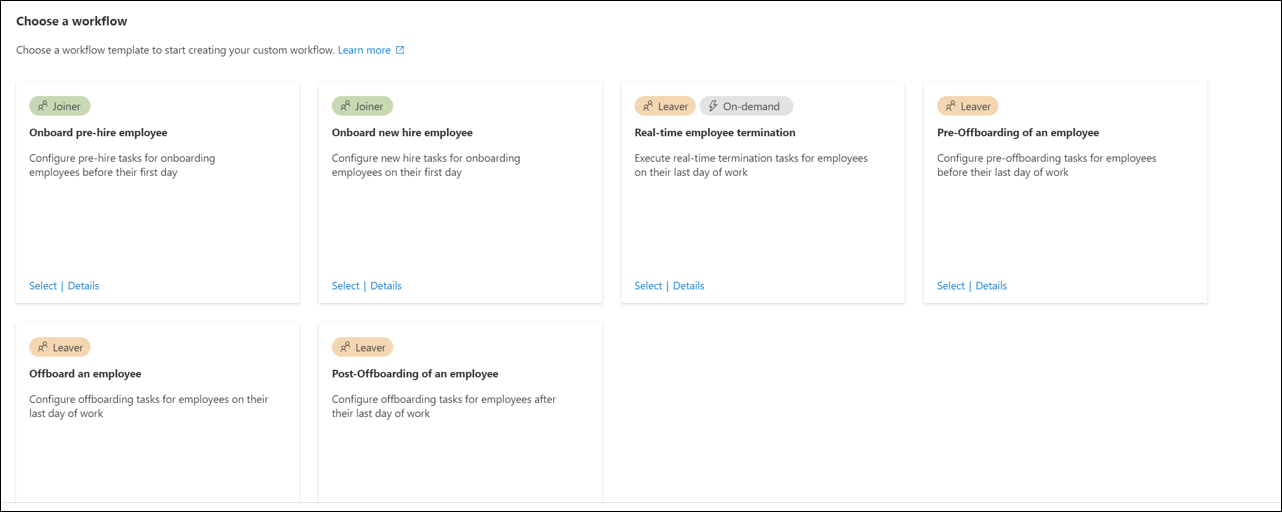
Browse to Identity governance > Lifecycle workflows > Create a workflow.
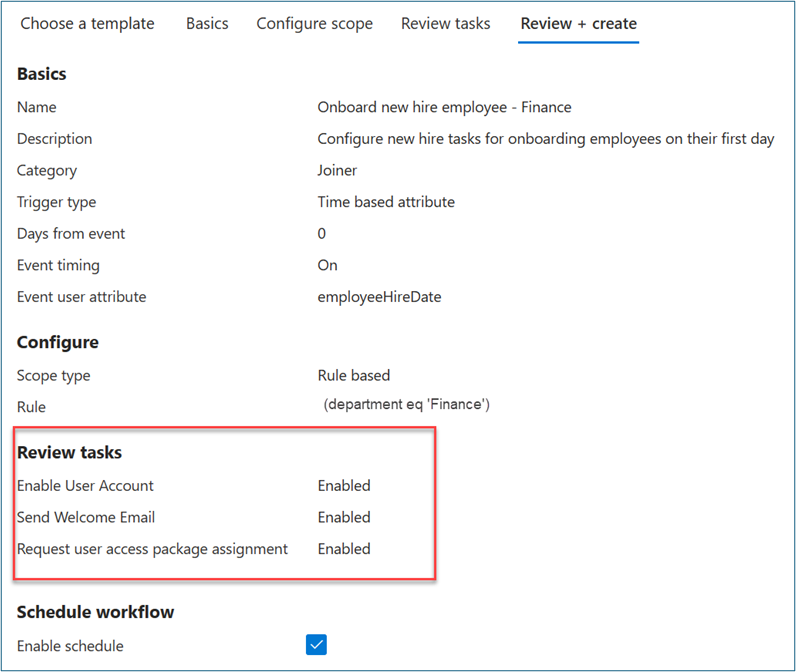
For Choose a workflow, select Onboard new hire employee.
For Basics, enter Onboard New hire employee -- Finance for the workflow display name and description. Select Next.
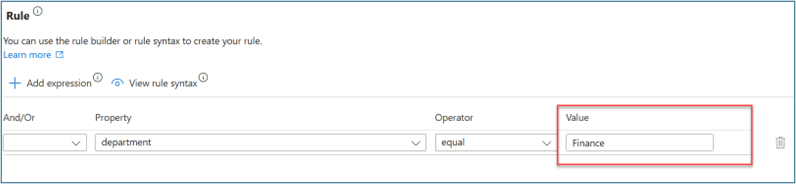
For Configure scope > Rule, enter values for Property, Operator, and Value. Change the expression of the scope to only users where Property > department has a Value of Finance. Ensure that your test user populates Property with the Finance string so that it's in the workflow scope.
On Review tasks, select Add task to add a task to the template. For this scenario, we add Request user access package assignment.
For Basics, select Request user access package assignment. Assign a name to this task (such as Assign Finance Access Package). Select a policy.
In Configure, select the access package that you previously created.
Optional: Add other joiner tasks as follows. For some of these tasks, ensure that important attributes such as Manager and Email are properly mapped to users as described in automate employee onboarding tasks before their first day of work using Lifecycle Workflows APIs.
- Enable User Account
- Add user to groups or teams
- Send Welcome Email
- Generate TAP and Send Email
Select Enable Schedule.
Select Review + create.
Create leaver workflow
To create a leaver workflow, follow these steps.
Sign in to the Microsoft Entra admin center as at least a Lifecycle Workflows Administrator.
Browse to Identity governance > Lifecycle workflows > Create a workflow.
On Choose a workflow, select Offboard an employee.
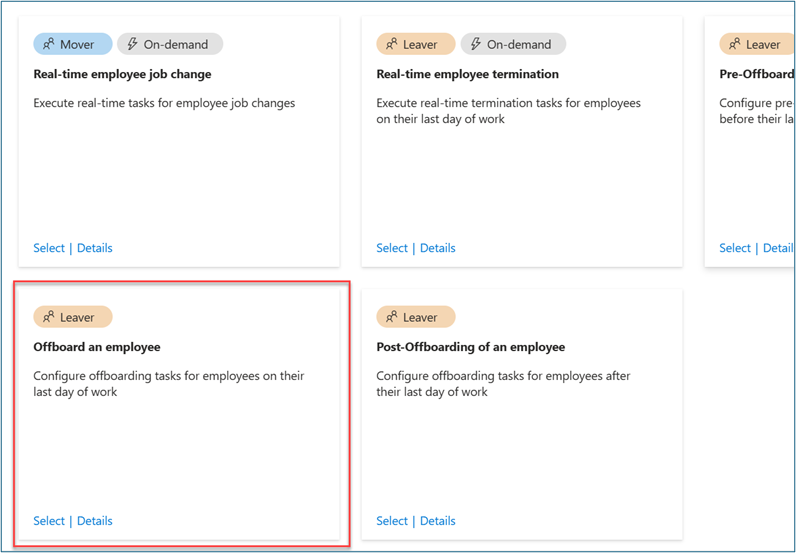
On Basics, enter Offboard an employee -- Finance as display name and description for the workflow. Select Next.
On Configure scope > Rule, enter values for Property, Operator, and Value. Change the expression of the scope to only users where Property > department has a Value of Finance. Ensure that your test user populates Property with the Finance string so that it's in the workflow scope.

On Review tasks, select Add task to add a task to the template. For this scenario, we add Request user access package assignment.
Optional: Add other leaver tasks such as:
- Disable User Account
- Remove user from all groups
- Remove user from all Teams
Toggle on Enable schedule.
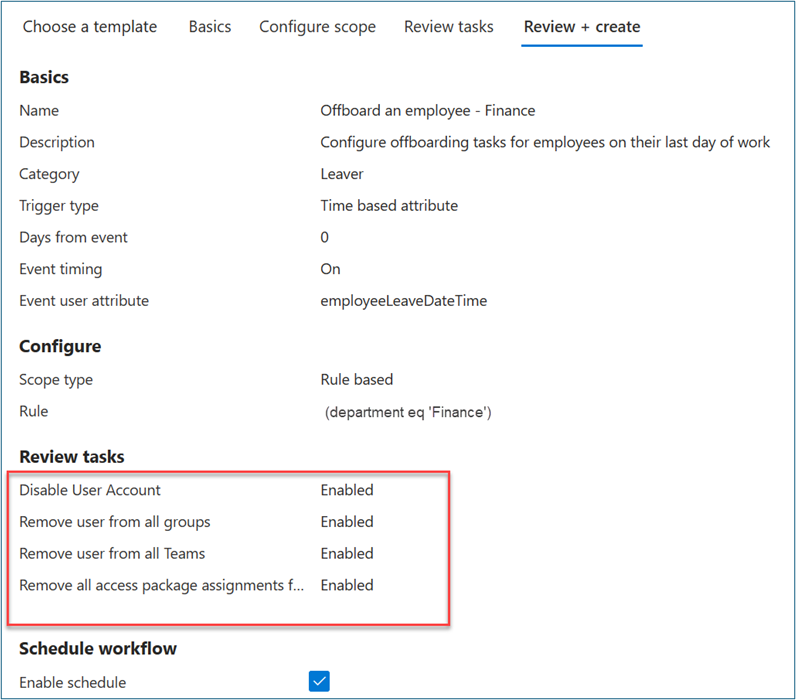
Select Review + Create.
Note
Lifecycle workflows run automatically based on defined triggers that combine time-based attributes and an offset value. For example, if the attribute is employeeHireDate and offsetInDays is -1, then the workflow should trigger one day before the employee hire date. The value can range between -180 and 180 days. The values employeeHireDate and employeeLeaveDateTime must be set within Microsoft Entra ID for users. How to synchronize attributes for Lifecycle workflows provides more information on attributes and processes.
Run joiner workflow on demand
To test this scenario without waiting for the automated schedule, run on-demand lifecycle workflows.
Initiate the previously created joiner workflow.
Sign in to the Microsoft Entra admin center as at least a Lifecycle Workflows Administrator.
Browse to Identity governance > Lifecycle workflows > Workflows.
On Workflow, select Onboard New hire employee -- Finance that you previously created.
Select Run on-demand.
On Select users, select Add users.
On Add users, select the users for which you want to run the on-demand workflow.
Select Add.
Confirm your choices. Select Run workflow.
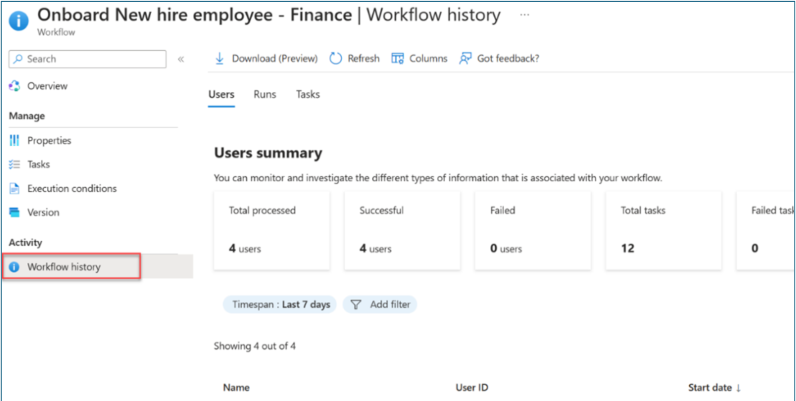
Select Workflow history to verify task status.
After all tasks are completed, verify that the user has access to the applications that you selected in the access package. This step completes the joiner scenario for the user to access necessary apps on day one.
Validate access for remote access per app
In this section, we simulate a new member of the Finance team joining the organization. We automatically assign the user access to the Finance Team file share and remote access to the file server with Microsoft Entra Private Access.
This section describes the options to verify access to assigned resources.
Verify access package assignment
To verify access package assignment status, follow these steps:
As the user, sign in to
myaccess.microsoft.com.Select Access packages, Active to see the access package (such as Finance Access Package) that you previously requested.
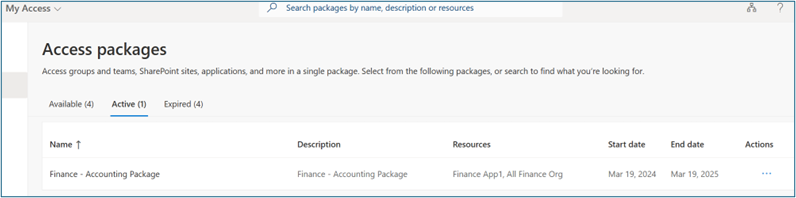
Verify app access
To verify app access, follow these steps:
As the user, sign in to
myaccess.microsoft.com.In the list of apps, find and access the app that you previously created (such as Finance App).
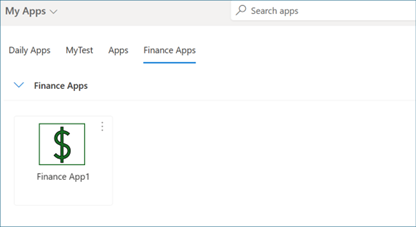
Verify group membership
To verify group membership, follow these steps:
As the user, sign in to
myaccess.microsoft.com.Select Groups I am in. Verify membership in the group that you previously created (such as Finance Accounting).
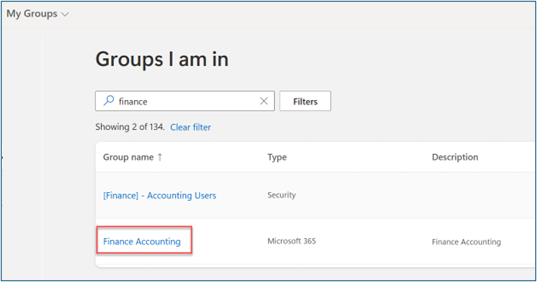
Verify Teams membership
To verify Teams membership, follow these steps:
As the user, sign in to Teams.
Verify membership in the Team that you previously created (such as Finance Accounting).
Verify remote access
To verify user access to the file server, follow these steps:
Sign in to the device where you installed the Global Secure Access client.
Run \
\\IP_addressand validate access to the file share.
Run leaver workflow on demand
Sign in to the Microsoft Entra admin center as at least a Lifecycle Workflows Administrator.
Browse to Identity governance > Lifecycle workflows > Workflows.
On Workflows, select the Offboard an employee - Finance workflow that you created in the leaver steps.
Select Run on-demand.
On Select users, select Add users.
On Add users, select the users for which you want to run the on-demand workflow.
Select Add.
Confirm your choices and select Run workflow.
Select Workflow history to verify task status.
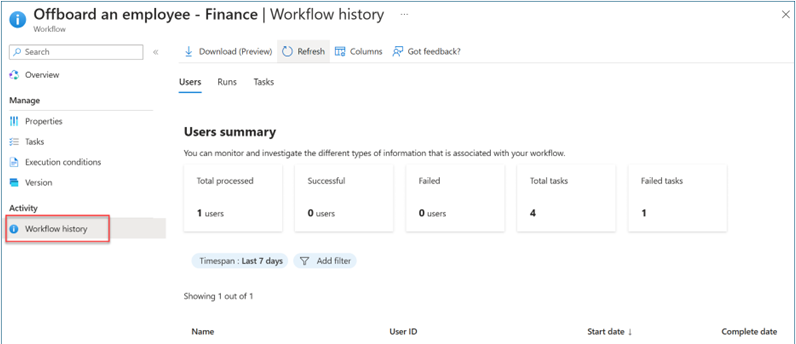
After all tasks are complete, validate that the user is removed from all access to the applications selected in the access package.
Validate access removal
After executing the leaver workflow, confirm the removal of user access to finance applications, the finance team, SharePoint sites, and file shares by repeating the steps in the Verify app access and Verify remote access sections. This step ensures thorough verification of the user being prevented from accessing these resources.
Related content
- Learn about Microsoft Entra ID Governance
- What is Microsoft Entra ID Protection?
- Plan a Microsoft Entra ID Protection deployment
- Get started with Global Secure Access
- Learn about the Global Secure Access clients for Microsoft Entra Private Access and Microsoft Entra Internet Access
- Learn about Microsoft Entra Private Access
- Learn about Microsoft Entra Internet Access